Tor Privacy settings coming to Firefox
Mozilla works on uplifting privacy settings of the Tor browser project to the Firefox web browser to provide privacy conscious users with additional privacy-related options.
While the Tor browser is based on Firefox ESR, it is modified with additional privacy and security settings to protect users of the browser while using the program.
Considering that Tor browser is used by some in critical situations, whistleblowing, publishing news or communication, it is only natural that a stronger focus on privacy and security is necessary.
Mozilla acknowledges these modifications, and plans to integrate some of them in Firefox natively. In fact, the company has already begun to integrate some in Firefox, and plans to integrate others in the future.
Up until now, add-ons added some of the privacy features to Firefox to protect against plugin enumeration or webRTC IP leaks when using Firefox.
Tor Privacy settings coming to Firefox
Three Tor-specific options landed in Firefox 50 already. Firefox 50 is currently available on the Nightly channel, and it looks as if it is the target milestone right now. As is the case with these improvements, they may be postponed.
- The first patch blocks enumeration of plugins and mimeTypes. Sites may retrieve the information from the browser, and use it in fingerprinting. With the patch in place, Firefox returns no information to the site blocking the requests effectively.
- The second patch works in a similar manner. Firefox returns 0 for screen.orientation.angle and "landscape-primary" for screen.orientation.type when sites or applications request the information.
- The third and final patch removes the "open with" option in the download dialog.
Tor-specific privacy settings are often not suitable for Firefox's mainstream audience. That's why you need to enable these settings manually in Firefox before they become available.
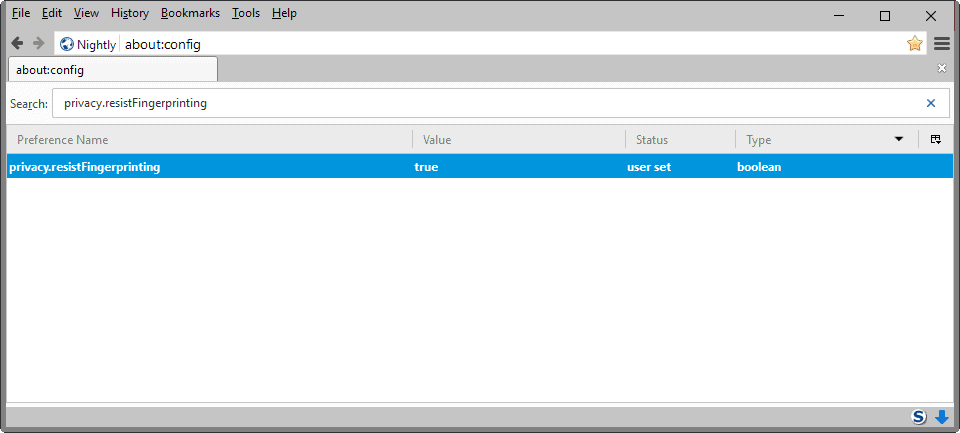
A core preference is privacy.resistFingerprinting. Originally introduced in Firefox 41, it is the central preference for Tor-related settings. While it covers most Tor settings that are implemented in the Firefox browser, some are available under other preferences.
Enable Tor-related privacy settings in Firefox

Instructions below are for Firefox 50 Nightly.
- Type about:config in the Firefox address bar.
- Confirm you will be careful.
- The privacy.resistFingerprinting preference does not exist by default.
- Right-click in the main area, and select New > Boolean from the context menu.
- Name the preference privacy.resistFingerprinting.
- Set its value to True to enable it.
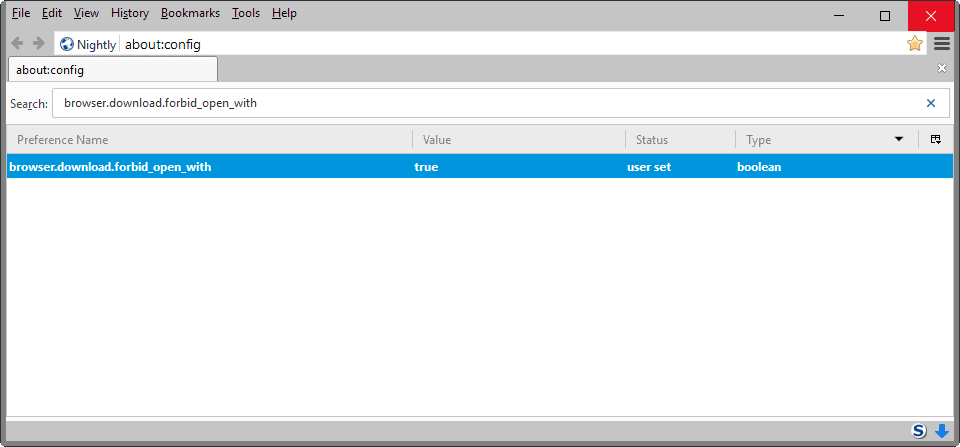
To block the "open with" option when downloading files, do the following instead
- While still on about:config, search for browser.download.forbid_open_with.
- Double-click the preference to set it to true and enable it.
The future
The Tor Uplifting entry on Mozilla Wiki highlights some of the improvements that Mozilla plans to integrate in the future.
Many bugs are not assigned yet, but those that are will protect against system font enumeration or make WebGL fingerprint resistant.
The Tor meta bug lists eight patches that are currently being worked on, and four that are already integrated in Firefox.
Closing Words
Integration of Tor-specific privacy settings and features in Firefox is welcome. These features won't be enabled by default, but they provide privacy-conscious users with better options to harden the browser against browser fingerprinting and identification. (via Sören)
Now Read: The most comprehensive Firefox user.js privacy and security information





















yeah
Are you saying that setting privacy.resistFingerprinting to true stops user scripts from working? If so, my experience has not been the same as yours. I have the pref set to true, and both of my scripts (using Greasemonkey) are still working fine on FF 56.
privacy.resistFingerprinting:true makes Grease-, Tamper- & Violentmonkey stopping the scripts included. They are still there, but don’t work any longer. Firefox 56.
Also, starting from Firefox 51 the WebAudio API (used in audio fingerprinting) can be disabled via dom.webaudio.enabled according to https://bugzilla.mozilla.org/show_bug.cgi?id=1288359
I don’t quite get it, those 3 settings will be default or you’ll have to manually enable them? I use the “open with” option with downloads a lot (with torrent files for example).
You have to enable them, they are not turned on by default.
Privacy is the one thing Firefox can defeat Chrome, Edge, and Safari on.
I already get “undefined” for Browser Plugin Details with Firefox 47:
imgur com/Jqdz0wI
Added these privacy settings in Firefox’s profile but the Panopticlick tool (https://panopticlick.eff.org/) was still able to fingerprint my browser.
Thanks for the tip about the Panopticlick tool: I wasn’t aware of that.
Like you though, the privacy.resistFingerprinting setting didn’t do anything in FF48 and I eventually looked for an extension to fix the problem. This one helps a little bit: https://addons.mozilla.org/en-US/firefox/addon/stop-fingerprinting/?src=api
After installing that, I still get a warning that FF has a unique fingerprint, but the Stop Fingerprinting extension hides all my extensions. So now I can go to Reuters.com and not get a warning to disable ABP because it’s no longer visible.
Panopticlick v2.0 is useless because they factor the canvas fingerprint into your uniqueness. If you don’t spoof it, your value is unique. If you do spoof it with a random unique value every time, your value is unique. Cogito ergo sum … you are always unique.
Also, you need to realize that privacy.resistFingerprinting is a pref that only covers a couple of things so far (in FF47) – namely windows/screen measurements. It will report all dimensions as your inner window (that’s the bit that holds the web page content), and it’s highly likely that you have a high entropy figure there (you can see the results here: http://browserspy.dk/screen.php ). You would need to resize your browser to allow for toolbars and side panels and so on.
To set a size, open a XUL (chrome) page (such as about:config) which is at 100% zoom, hit Shift+F4 to open the scratchpad, type window.resizeTo(1280,800), hit Ctrl+R to run. Test your window size (link above), do some math, flick back to the XUL window, go back to your scratchpad, resize to allow for all the non inner window elements.
“privacy.resistFingerprinting … will report all dimensions as your inner window … and it’s highly likely that you have a high entropy figure there”
Very true: With the pref set to false, my screen dimensions are quite common – browserprint.info reports that 1 in 16 browsers have the same value. If I set the pref to true and run the same test, that changes to 1 in 41,000 :-(
This is one thing I don’t understand concerning the privacy.resistFingerprinting setting (hidden, added and set to true) : I go to http://browserspy.dk/screen.php and notice that my screen’s Width, Height, AvailHeight and AvailWidth are all read and correct. Am I missing something?
I should have mentioned this in ‘The most comprehensive Firefox user.js’ has been updated (https://www.ghacks.net/2016/07/03/comprehensive-firefox-user-js/) but forgot to … Firefox 47.0.1 here.
Adopting TOR’s privacy settings, TOR’s commitment to privacy, focusing on privacy will always set a browser apart when speed and new functions (some of which considered by some/many as gadgets) are not the only concerns of users, are less as privacy’s importance is increasing even among the average users. Competitors to Firefox don’t really consider privacy as an important factor, security yes but privacy less or not at all (an advertisement company’s browser is not naturally inclined to its users’ privacy).
So, if Firefox advantages this topic, which has always been one of its characteristic but perhaps not sufficiently recalled, especially since the Australis turn, then it will be for the good of us all and for the good of Mozilla as well.
Once they get e10s (as a per tab, not just two processes), they should be marketing the hell out of the difference between chrome and firefox (no point targeting anyone else, just go for the market leader) in regards to privacy/fingerprinting/tracking. How hard can it be to show that chrome don’t give a sh*t and deliberately “bake out” or limit any solutions, while mozilla bake them in (and for now also have more addon scope). No other browser offers anything remotely close to what mozilla does. And I’m hoping e10s will boost FF’s results in the-browser-war tests (although to be fair, the differences are pretty much negligible for humans, I think).
All those naysayers who moaned about Australis – I understand the anger at removing some customization, but that has been brought back via an extension. And I agree/wish they had left it in. Not enough for me to turn my back on them though. And as for cloning chrome – how stupid. Building a unified, larger for fat fingers, touch friendly, stream-lined and simplified interface to cater for all devices is a natural progression. And TBH, my desktop version is nothing like an android one.
Anyway .. a lot of these preferences from the tor uplift are already in the v10 ghacks user.js – some have already landed in FF46 (or earlier) such as the one mentioned by Martin: privacy.resistFingerprinting. It’s already active. It will also gain new powers as they stack more tor tickets onto it. A lot of the rest are listed under the “to investigate” section. You can all thank me later :)
We thank you already, Pants! Same here regarding Firefox, and if I do moan (less now) after a few innovations I considered as gadgets, the main point as you remind it is that indeed the user has the ability at his finger-tips to modify settings, except for the hidden ones which you detail in the now famous so-called ‘Ghacks user.js’ (though ‘Pants user.js’ in fact), and which is most appreciated alongside your work and the concatenation result with sources you moreover have the elegance to detail.
So : Go Firefox, Go TOR, and let’s all go for the Magical Privacy Tour :)
“Simpsons did it first” – https://www.ghacks.net/2016/07/03/comprehensive-firefox-user-js/ :)
That’s why I like FF. Mozilla should go this way and forget about cloning chrome.