Take control of WebRTC IP leaks with Statutory for Firefox
In recent years, new technologies have found their way into modern web browsers. Designed to improve or add functionality to the browser to support web applications making use of them, they sometimes have side-effects that can affect a user's privacy on the Internet.
It became known only recently for instance that the two browser features HTTP Strict Transport and HTTP Public Key Pinning can be abused for tracking purposes while they have been designed to make user connections to HTTPS more secure.
The same is true for WebRTC which sites may use to detect the local IP address of the system connecting to it.
You can test if your browser leaks the information by visiting IP Leak. Check whether your IP address is revealed under the WebRTC detection section on the page.
We have reviewed methods in the past to disable WebRTC spying in Chrome and Firefox, and if you don't use WebRTC at all, they may serve their purpose.
If you do use web applications or services that make use of WebRTC, then you may not want to disable the feature completely, as it would mean to toggle it whenever you use these apps or services.
Note: Statutory is no longer available. Firefox users can install add-ons like Disable WebRTC which provide similar functionality.
WebRTC IP Leaks
Statutory is a free browser add-on for the Firefox web browser that puts you in control. Instead of disabling WebRTC outright, it displays notifications on pages where it is being used.
You may accept or deny the request then and there depending on whether the request was initiated by you or by the site.
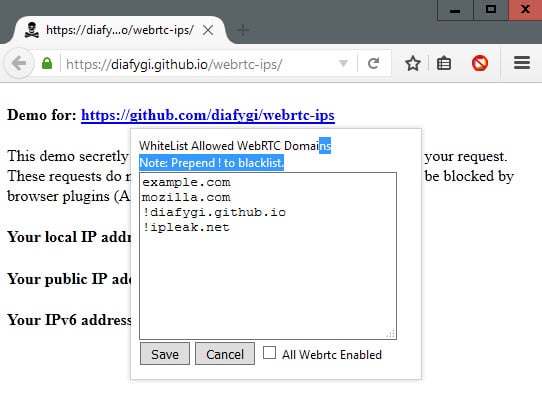
The extension ships with a whitelist and blacklist on top of that to define permanent rules for sites. If you use WebRTC on a site for example, you may want to add it to the whitelist to allow it automatically.
The same is true in reverse for sites that make use of WebRTC even though you don't use it on those sites. Instead of receiving prompts each time you visit the site, you simply add it to the blacklist to deny the request automatically.
Blacklisted and whitelisted sites are mixed into a single list by the extension. To whitelist a site simply adds its domain name in a new row, and to blacklist a site do the same but prepend "!" in front of the domain name.
The add-on's options enable you to disable notifications, and to disable WebRTC permanently. If you select the latter all WebRTC functions are disabled so that it cannot be used anymore in the browser until revoked.
There is an easier way to disable WebRTC in Firefox though as you can set the preference media.peerconnection.enabled to false on the about:config page to block it as well.


























It appears this software no longer is being offered. There are other similar tools, however.
Tony, thanks for letting me know. I have updated the review to reflect that, and added a link to a suitable alternative.
Doesnt work, i tried it and visited the ipleak link and my I.P was shown. gues i’ll just disable it in about.config
Yes I noticed this as well. FF offers the allow/deny drop down, and only when deny its clicked will it block. But on first page load is was not blocked.
https://ipleak.net/
Current version of Ublock Origin has a privacy option to prevent WebRTC from leaking local IP addresses. It is not enabled by default. When enabled in Firefox, Hello doesn’t work properly. In Chrome, Google Hangout and Facebook messenger do not work properly when this setting is enabled.
IP Leak states and confirms “No leak, RTCPeerConnection not available.”.
Always a pleasure to notice the blindness of a thief.
So true as the article clearly points it out that what is given by one hand has a counterpart taken by the other hand. Business in worse when business is known as an exchange (win-win is seldom the outcome) and therefore leads to no surprise. Surprise! is the lot of an increasing number of so called “tools”, “enhancements” to a browser where the technically uneducated user may not even be aware of the price to pay, especially that the price here is that of privacy.
My surprise is not that one but rather this one : why do browser developers not rather focus on improving (when not creating) the basic requirements for a secure and private browsing experience. For example the cookie management which could (should) be far more sophisticated than it is, even that of Firefox. Many other examples are available. I’m wondering if the reason, besides a commercial odyssey requiring an increase in tracking, is not the very natural excitement of the techie side of all those who participate to a browser’s development which is provided by a greater thrill to innovate than to improve : are we not all the same? When it comes to developers I believe they should put aside their thrills once in a while and think at the user rather than dive into their ego.
Great post, Tom. Agreed.