Another Fix For Unauthorized Google Redirects
We posted a solution for one of the causes of unauthorized Google redirects yesterday. These redirects can happen in one browser or multiple ones, and are usually related to searches that the user performs in search engines such as Google.
Yesterday's redirect we reported about was caused by a plugin that got installed on the host computer without the user's consent. This plugin did not appear in the list of installed plugins and the fix was to run the program Gooredfix to remove it from the computer system.
Today's reason for an unauthorized redirect is a rootkit that is commonly known as Rootkit.Win32.TDSS. The problem with a rootkit is that many security applications do not detect it even if they are updated with the latest virus definitions.
Security software that can detect the rootkit are for example Dr. Web's CureIT or Kaspersky Internet Security.
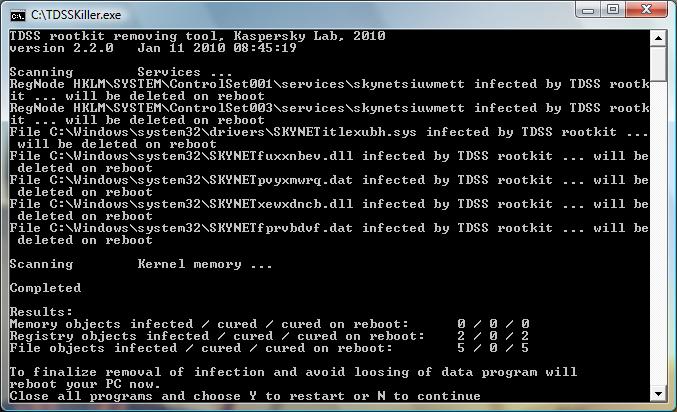
TDSS Killer
From Kaspersky comes a tool that can be used to remove the TDSS rootkit right away. That's the simplest solution if the cause of the unauthorized Google redirects is indeed the rootkit.
The program TDSSKiller can be downloaded from a Kaspersky support page. It will scan the system for traces of the rootkit and clean it if any are found.
All you need to do is run the program with elevated rights and wait for it to complete the scan and disinfection. To do that, download the program from Kaspersky, extract the archive to the local system, and right-click on it afterwards to select the "run as administrator" option from the context menu.
# The registry is scanned for hidden services. The utility will remove the services identified as belonging to TDSS. Otherwise, the user is prompted to eliminate the service. The services are eliminated upon a reboot.
#System drivers are scanned for infection. In case an infection has been detected, the utility will search for an available backup copy of an infected file. If an available backup copy of an infected file has been detected, the utility will restore the file from it. Otherwise, the utility will attempt to disinfect the file.
# By default, the utility outputs runtime log into the system disk root directory (the disk where the operating system is installed, C:\ as a rule). The log is like UtilityName.Version_Date_Time_log.txt. for example, C:\TDSSKiller.2.2.0_20.12.2009_15.31.43_log.txt.
# When its work is over, the utility prompts for a reboot to complete the disinfection.
The driver will execute all scheduled operations and kill itself upon the next system reboot.
Another possible solution has been posted at the Remove Malware website. It is a thorough way that takes longer than just running the Kaspersky removal tool but it ensures that no rootkit or malware traces are left on the computer system.


















@Frank,
You had TDL3 version 3.22 or earlier on your PC.
Regards
Simon
This worked for me. It tried the Goored.exe fix from the first article, with no luck. I then tried the TDDSKiller from the link just below the screenshot. The log file noted two problems, one of which required a reboot. The problem files were “atapi.something”, I can’t remember exactly what. Anyway., problem solved. I’m running XP Service Pack 3.
“Internet security 2010” IS malware. My PC was attacked by this company demanding I purchase their anti-malware program and I’ve spent the better part of 3 days trying to get rid it’s “security threat” pop-ups.
Hi,
TDSS infections which are either not detected or very difficult to remove are basically NOT TDSS.
The latest rootkit is called TDL3 and is rapidly updating to make is difficult detect and remove.
Calling it the same as TDSS is NOT helpful as folks are then missing this when checking for malware infections.
Few if any of the mainstream AV tools will detect it or remove it so special tools are needed.
There is info on the tools you can use and a summary of the issues here:
http://www.podnutz.com/forums/viewtopic.php?f=26&t=1633
Some versions of TDL3 patch ATAPI.SYS or other low level mass storage drivers to create their own pseudo filling system on unused storage space. TDL3 v 3.23 has a watchdog service which prevents it removal from the registry.
Regards
Simon
Does not work with x64 systems :(