We read it in the news everyday. The major music industry players like Sony BMG or EMI are reporting losses all over the place and blame it solely on internet pirates. Internet pirates are actually a very good excuse for bad times. Hard facts do not exist and no one is able to check on the numbers the MI provides for losses due to internet pirates.
They don´t seem to realize that they criminalize their own customers with measures like copy protected cd´s and rootkit software installed on customers pc.

The news spread like fire last week: Sony has a installer on some of their music cd´s that might install a rootkit on customers pc´s if they put them into their personal computer. The rootkit software could not be uninstalled by normal means and has already been used by hackers to hide World of Warcraft cheat scripts from being detected by Blizzards Warden client.
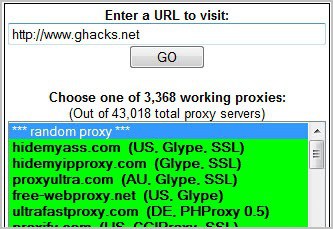
Here is another of those online proxy sites that allow you to surf without revealing your ip at the destination site. Its available at xanproxy.be
Cd´s and Dvd´s have the nasty habit to become unreadable due to data loss or aging at the very moment when one needs them most. Dvdisaster creates error correction codes to compensate read errors which are not correctable in the CD/DVD drive.
If you ever sold or bought a used hard disk you probably know about this already. For all others, even if you use delete and format to clear the hard disk before selling it there are possibilities to recover most and possibly all data that was once on the hard disk.
There have been numerous cases in the news where people bought used hard disk and found confidential files on them using tools to recover deleted data. Enter Darik's Boot and Nuke.
I´ve been using spamihilator for the last two years and can only say that this is the best free anti spam software that I ever used. And believe me, I tried a lot. Before i used the software I recieved approximatly 500 spam mails per day, mainly due to published emails on websites that I own.
I searched desperately for a good anti spam software and tried many. Most did not work to well in reducing spam, some worked to well and even stopped my normal mail from arriving. Then, finally after a long evaluation time I found the spam software that I´am still using today. It reduced my daily spam dosis of 500 to 4 in just two days.

Yesterday I´ve written a short tutorial about streamripping and one of the questions that occured was if its possible to rip real audio music as well. Today i present a guide on how to rip the real audio format.
Rapid leech is a fine server script that is able to download files from sites like rapidshare using a server instead of your home connection which speeds up the download process. You need of course a server to install the script and run it from there.

Streamripping means saving mp3 files from internet radio streams to your hard drive. All you need is the right tool that does the work for you and your favorite radio station that broadcasts on the internet and uses a format supported.
This article will give you a tutorial on how to start streamripping and legally download all the latest mp3 files to your computer. I can´t speak for all countries though so you better check out if recording music from radio is legal in your country.
Picostick is only 6K in size, making it one of the smallest windows applications ever. It is a small post-it-note utility in your Windows(tm) taskbar icon tray. It is easy to use, come with striking color, and will not clutter your computer screen at all.
This one is pretty useful, its called SilentNight Micro CD/DVD/ISO/AUDIO Burner. The tool is just above 1 Mb in size and fits easily on and can be run from a single floppy disk. There is no installation required, just unpack and run the tool, makes it ideal for mobile usage as well.

It has come to our attention that World of Warcraft Hackers already are using Sonys Rootkit Software to hide their hacking from Blizzards Warden Client.
We reported earlier this week that some Music Cds by Sony labeled "Content enhanced & protected" would bring up an installation program when the music cd was put into a personal computer.
If you ever had the problem that you needed a good graphics suite and always thought the Adobe Photoshop line of products was far to expensive then GIMP might be the right software for your. The biggest advantage, its completely free, you don´t pay a dime for it.

And another player joins the rangs of the companies that might install spyware with their Music Cds when you put them into your pc drives. "Fontana Distribution, part of Universal Music Group and distributors for Upstairs Records Inc., are encouraging the independent records labels they distribute to use content protection on their CDs. "Twelve Eighteen", featuring the hit song "Summer Nights", carries the same content protection currently being used by Sony BMG.
John Lopez of Upstairs Records commented: "we are very pleased with the seamless production of the album. The media player on the CD has a good user experience and we intend using the technology on more new releases."
Most banks in Europe offer a new service on their internet pages. When a user has to enter his login data he has the option to enter the password using a keypad that is displayed on the screen using a java applet. The user then clicks on the numbers and they appear in the password field. This is done to prevent the keylogging of the password.
The Anti-Keylogger does the same thing, only difference is, that its a tool that is started like every other windows program. After the tool is started you simply use the displayed keys to enter your passwords or other data on websites or even local programs.

Lets start with a quick link in the morning. The online proxy Poxy can be configured in many ways, you can chose to accept cookies, enable javascript, show images and have a small form above the website that you want to surf anonymously with poxys configuration available.
The great advantage of Poxy is that the site itself has no ads, no popups and all those other nasty stuff that most online proxies seem to have these days.

A few minutes ago I read a news article written by Brian Krebs who described how some Sony Music Cds try to install a software on pcs that could be labeled as spyware.
It seems that we have reached a new level in the fight between the record companies and its consumers. If you put a music cd in question into your drive a installer will popup. If you agree to install the software you won´t find a uninstall feature anywhere on your pc.
Apparently all Music Cds labeled "Content enhanced & protected" have the installer on the CD, make sure you check this before you buy a cd you would want to hear using your pc.

The guys at neowin.net posted an article on how to find out if a recovery cd is in fact a normal windows xp version labeled recovery version.
The process involves a total of eleven steps, starting with the creation of the cd structure and the movement of the files needed to later burn them to a new cd.
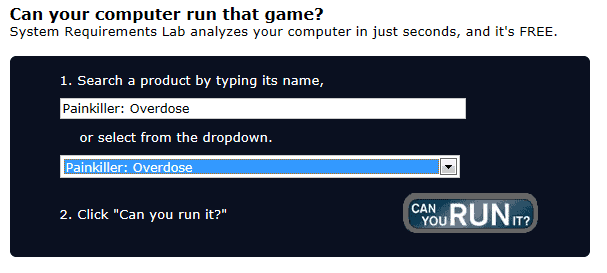
I found a website that tests the ability of your pc to run a certain game. They have most newly released and soon to be released games in their list, e.g. Age of Empires III and Civilization IV.

The National Security Agency offers Operating System Guides on their websites. These guides are currently being used throughout the government and by numerous entities as a security baseline their systems.

Everything you do on the net transmitts your Ip Address. If you chat with someone he could easily find it out, if you write an email the information will be transmitted with the email.
The article describes what the IP reveals about the user behind.
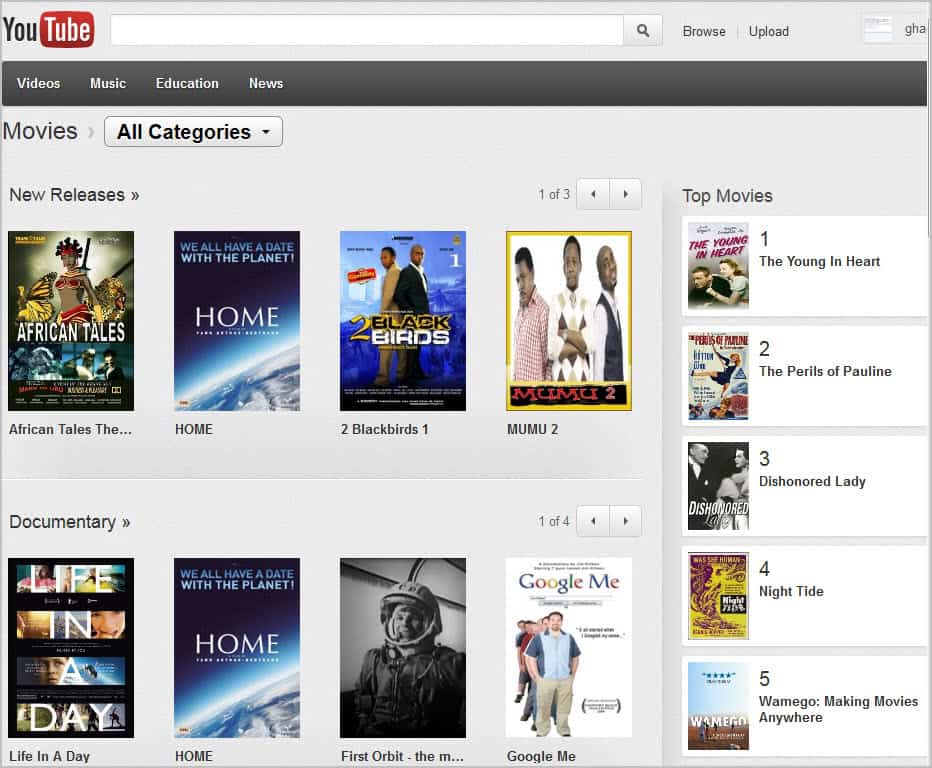
I thought this would be of interest to some of you. Watchfilms.com are offering more than 300 movies on their website that you can watch for free.
The movies are divided into six categories: Movies, Cartoons, Documentaries, Newsreels, Commercials and Short Films. Most films are black and white movies from 1930-1950.

This article describes how search engines work, how the data is processed, how search results are generated. It also describes most of the advanced search operators available today.
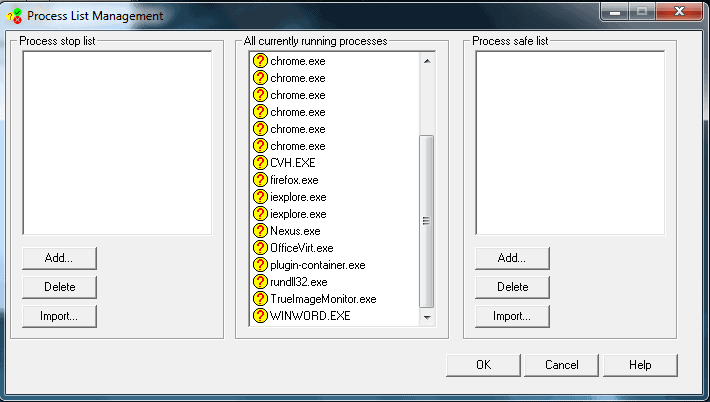
Process Patrol allows you to manage the Windows processes on your computer. You can set stop lists for spyware, adware, and virus programs that will be automatically killed. Program files are renamed to prevent restarts.

Greg Hoglund with some time at his hands performed a long reversing session on a game most of us played or have at least heard of: World of Warcraft.

Just a quick news this time. A new free online proxy site opened up its gate. You can use it to bypass restrictions at school or work for example. (e.g. filtered sites)

Richi posted a nice introduction on how spammers actually send the millions of spam mails every day. He begins by describing two ways of sending spam mails: traditional and viral.
Have you ever recieved on of the following ...
OpenOffice 2.0 is finally available for eve...
This short guide has the intention to provide even new users with an easy way to enjoy the internet. A big problem that stands between the enjoyment is mail spam or simply spam.
Have you ever wondered how many and which files...

A warm welcome to everyone! gHacks.net is the direct result of a thread posted @ www.deny.de about some advanced search options with the google search engine.

Shortcode with all attributes Shortcode with no attributes Shortcode with link but no title Shortcode with title but no link Shortcode with link and title Shortcode with link and subtitle Shortcode with […]