Your browser stores passwords and sensitive data in clear text in memory
Your web browser may store sensitive data, including usernames, passwords and session cookies in clear text in memory according to CyberArk security researcher Zeev Ben Porat.

Most Chromium-based web browsers appear to be affected, including Google Chrome. Microsoft Edge was tested for the weakness and it was affected by it, too. A quick test on a local Windows 11 system confirmed that browsers such as Brave and Mozilla's Firefox web browser are affected by the issue as well.
Physical access to the target machine is not required, as remote access or access to software that is running on the target machine is sufficient to extract the data. Extracting can be done from any non-elevated process that runs on the same machine.
While it is necessary for the user to enter credential data such as usernames and passwords before they can be extracted, Zeev Ben Porat notes that it is possible to "load into memory all the passwords that are stored in the password manager".
Two-factor authentication security may not be sufficient to protect user accounts either, if session cookie data is also present in memory; extraction of the data may lead to session hijacking attacks using the data.
The security researcher describes several different types of clear-text credential data that can be extracted from the browser's memory.
- Username + password used when signing into a targeted web application
- URL + Username + Password automatically loaded into memory during browser’s startup
- All URL + username + password records stored in Login Data
- All cookies belonging to a specific web application (including session cookies)Testing your browsers
The issue was reported to Google and it received the "wont fix" status quickly. The reason given is that Chromium won't fix any issues that are related to physical local access attacks.
Zeev Ben Porat published a follow-up article on the CyberArk blog, which describes mitigation options and different types of attacks to exploit the issue.
How to test your browsers
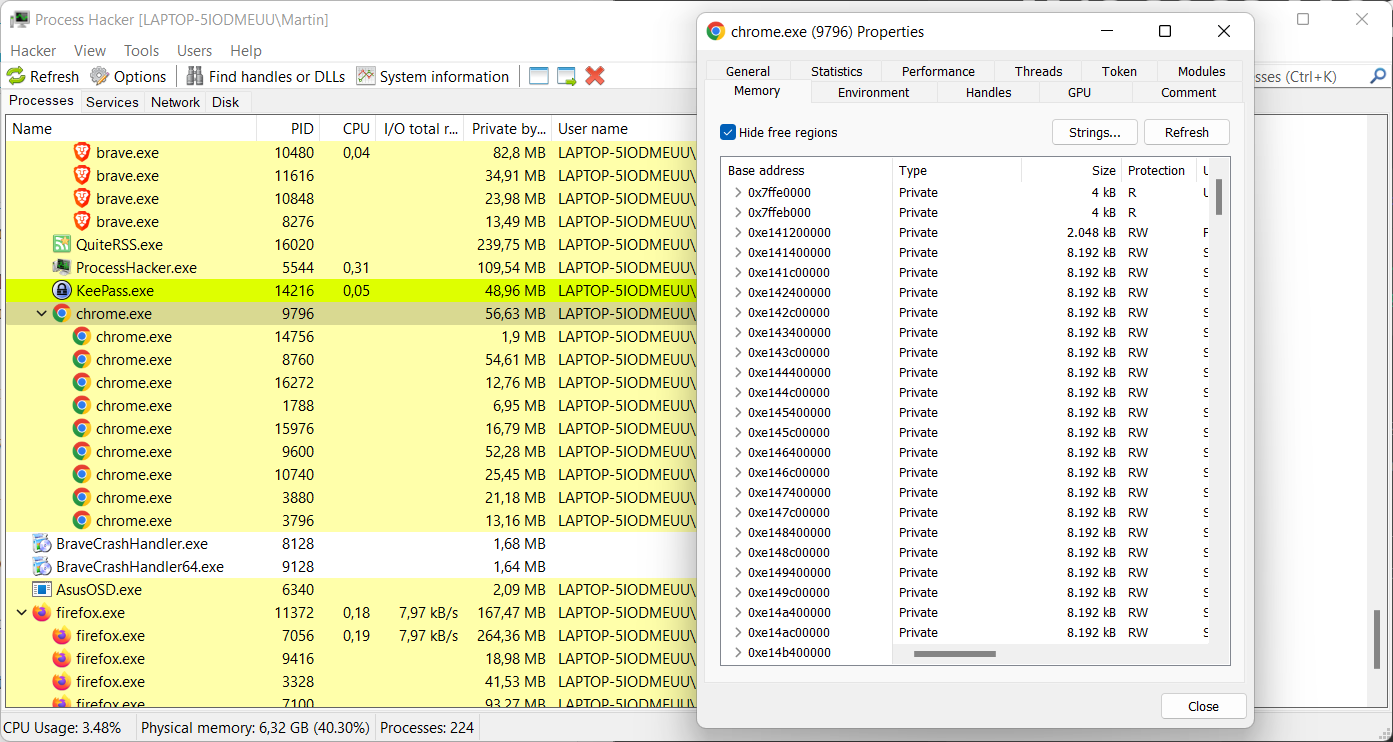
Windows users may use the free tool Process Hacker to test their browsers. Just download the portable version of the program, extract its archive and run the Process Hacker executable to get started.
Enter a username, password or other sensitive data in the browser that you want to test.
- Double-click on the main browser process in the process listing to display details.
- Switch to the Memory tab.
- Activate the Strings button on the page.
- Select OK on the page.
- Activate the Filter button in the window that opens, and select "contains" from the context menu.
- Type the password or other sensitive information in the "Enter the filter pattern" field and select ok.
- Process Hacker returns the data if it is found in process memory.
Now You: is your browser affected by this? What is your take on the issue? (via Born)


















just would like to say that when you use tools such as virus total etc,you should consider what kind of software that it is that your having scanned. If its a password cracker or a android root device for mobile phones or a keygen…..it is these types of programs that are going to make the virus total return a false positive because of the nature of the software that is being scanned which in this case would be the “process hacker” software portable version on windows. I havent actually myself looked at it bcuz at the moment im writing this on my hackintosh CFL UHD 630 13.0 VENTURA BETA , which is nice by the way macOS 13.0,anyway ill go ahead and look and see what it is thats goin on bcuz i seriously doubt the author of this article put up a link that has malware in it! So if im wrong im wrong my apologies but i think just by the nature of the software “process hacker” i think it is causing false positive from the virus total. Because of ther things that it does such as displays your passwords and such i mean thats a feature that would set any anti virus anything thourgh the roof!
Yeah, and look how ram consuming are browsers without encrypting data tha doesn’t even matter. Who save important password in browser or store session cookies?
One of the stupid clickbait article. ????
Does the author understand how a computer work?
I actually fell victim to a similar attack a few years ago. 2017 or so maybe. There is a freeware developer that uploads his projects on his own website Nirsoft. I think my machine was compromised via some P2P media I downloaded online if you catch my drift.
One day I catch a glance of some icon in my task bar that I did not recognize. When I go to click it, it disappears. That’s odd I thought but after some quick checks I didn’t see anything and got back to gaming. Eventually I got off for the night but left my computer on. The next morning I woke up to multiple notifications on my phone showing unusual activity with PayPal, Ebay, and Amazon. I freak out after over $1500 in Twitch donations/gift cards were charged under my accounts. After calling my banks and various sites, I finally get to my computer. I see the icon again at the bottom of the screen and so I click it and all of a sudden I am staring at a list of all my usernames, emails, passwords, etc.
Since that day I have never saved a password in my browser. Unless it’s some one time website I’m setting up and the password is just random.
damn brother! thats some serious stuff right there man! wow
To clarify, the attacker utilized this Nirsoft developer’s freeware to perform the attack. I realized I never mentioned the connection. The odd icon I noticed was from this developer’s software. When I found this connection I tried to reach out to this developer but never received a reply. Not that there would be much for him to say besides suck to suck, but I remember being upset that he never responded to how his software was used haha
Steve99 – Could you give us clear, simple advice of how to lessen leaked data from Brave browser? Thanks for your explanation.
You use it to scan, sorry your weak password is revealed by this scanning process, you knew it, someone knows for sure.
Well duh, if you have autofill enabled, even webpages or extensions can steal passwords
Zeev Ben Porat, the person who raised this issue, has stated that this issue is caused by a peculiarity of “Chromium-based web browsers”, which does not applicable to Firefox. Just to be sure, we in the community (forums.mozillazine.jp) have also re-tested the issue and confirm Zeev Ben Porat’s opinion.
https://www.ghacks.net/2022/06/12/your-browser-stores-passwords-and-sensitive-data-in-clear-text-in-memory/#comment-4523612
In short, this is something that users of Chromium-based web browsers (and Vivaldi Mail) should consider.
Everything is explained in his blog.
Best of all, check out his blog!: Go BLUE! A Protection Plan for Credentials in Chromium-based Browsers | Zeev Ben Porat
https://www.cyberark.com/resources/threat-research-blog/go-blue-a-protection-plan-for-credentials-in-chromium-based-browsers
How about 2 factor auth and don’t worry at all? – I mean do what you want, but don’t get crazy about it.
This is the kind of thing that is near impossible to fix. Your password has to exist in memory, in the clear, at some point to actually use it. And there are MULTIPLE layers of software likely not written by the browser devs but used by them like Open SSL that are probably copying that password from buffer to buffer in the process of transforming, encrypting data before transmitting it over the web.
Code scanning software once recommended at my job to address a C# application having a password in the clear in memory and we basically protested because even Microsoft .NET engineers admitted there was no way to keep that data safe in memory. C# is even worse because you don’t even have enough access to clear memory. It’s up to the framework.
By the way. This is a good reason to use 2 factor authentication.
There’s no way to enter a password and not have it stored in ram, how is this a security concern? For a password to function at all the program has to have access to it in plain text. There’s literally no way around this.
Time to go back to carrying a pocket diary full of passwords…
Why Martin Why… why you must put fear with such news? I pretty much have all my passwords stored on Edge :(
Bitdefender came up with a new password manager; all for a little extra fee. How quaint. What’s the point of Total Security Solution when you’re going to sell crucial services as an add-on?
I just love Windows Firewall Control. When you’re doing using the internet; set it to high filter mode. No data in, no data out. PC runs buttery smooth. :)
It’s still going to be in memory when you type it. This isn’t a security concern, it’s literally how a computer program works.
I think what could be considered a concern here is that it’s stored in memory in such a way that any other process (even an unelevated one) can read it.
I tested this on firefox logging into O365, and it kept the credentials around until I closed the WINDOW, even after navigating away from that site and closing the tab I logged in from.
Seems like some more could be done to clean up and/or protect sensitive data than is currently in place.
Run the browser in a virtual machine?
VM doesn’t solve this particular issue, but your suggestion is excellent advice. VMs abstract your physical HW from your browser processes and thus gives many benefits. The main benefit is if you get an infection, you simply click the [x] for immediate shutdown, restore from snapshot, and you’re back to a pristine machine. It also protects your HW RAM from the browser, as long as you have a healthy machine (the OS is supposed to do this via memory randomization and protections, but as history shows, those processes and mechanisms have been breached quite a few times ).
VMs also allow you to completely wipe your [ LOCAL ] VM computing history if you care to, via the same method of “click [x] / restore snapshot”. Residue exist and can be retrieved at great expense, but unless a user has a SA after them, they have nothing to worry about. If you re-import your bookmarks after restore, you bring back allot of that history (which I always do). The paranoid run their VMs on encrypted partitions and wipe the partition before they hear creaks on the floorboards.
VMs also allow you to create a pure inet browsing machine, with unnecessary ports and services shutdown. For instance, intelligent folks do not want ports 135-139/445/5355/1900/etc open at all on an inet browsing machine. In fact, those types don’t want anything at all responding on those ports. Thus, they completely disable SMB both via the registry, shut down the svr/wks services, and block at those ports at the firewall (belts and suspenders). While fiddling with services, disable printing service and most of the network chaff, especially on Windows. Give the VM a static IP and then disable DHCP. The more chaff disabled, the harder it is to infect the VM.
Host firewall
Because it is an inet VM and folks can make & easily recover from mistakes, advanced users delete all incoming and outgoing default firewall rules. They then block ALL incoming and block outgoing by default. Then, specific rules are put in place to allow out the only ports required are dns (53 or *443 via dnscrypt*), 20-21 if needed, 80, 443 (, and 8080 if needed). If properly setup, that VM should not issue more than a few packets an hour while at rest and it should reject every packet went to it.
So your suggestion to use a VM is excellent advice. Doesn’t stop the browser from being a leaking sieve of your personal data, but if config’d right, it does prevent massive leakage of your personal files and data.
You have no idea what youre talking about, VM or NO VM wont mitigate any security issues like this.
Clearly you have no clue how any of this works. Or are just posting stupidity on purpose.
Imagine suggesting using a ‘password manager extension’ to workaround this.
first, I don’t even think it will going to work when the browser is loading to memory everything on plain text, not just passwords but cookies, urls, anything you do in a browser and it doesn’t get cleared because you can open the browser for 24 hours, and you will still find the same info.
Second, how can saving your passwords in an external server you have no control of be better?
I mean, I always wonder about it, you literally have to create an ACCOUNT with your personal email and your password to use those extension password manager, there is no password manager that doesn’t require to be logging in, unless it is like a Keepass that has to be installed/running in the local computer.
You even have to pay for some password managers, you know, now you have to provide your billing information.
I mean, when you log in to your password manager… will the password shows in memory just like the email?
If it does, then the whole “use password manager” will not work, because if someone has Physical access to the computer, they can use your password manager extension, if people have physical access to your computer, they can steal whatever information.
And if you log out, it will be protected until you log in again and the email and password shows.
But let’s be honest, how many people keep they accounts logged in anyway? the person accessing your computer physically or remotely with Anydesk or teamviewer or whatever (because some people install those things and never realize someone is controlling their computer). Then that means the person can just access your emails, change passwords and do whatever they want.
I mean, that’s why Google doesn’t even care to fix this, if you let someone use your computer and you didn’t have any protection like an account password, firewalls and anything to stop someone from accessing your computer so easily locally and remotely, then it is your fault.
Microsoft might do something about this and Edge, since they care more about that, but I mean, when even Firefox does this, that means it was meant to do these by all these Browser makers.
So, now I wonder if IE, netscape, old opera, old Edge also did that.
It would be safer to have an encrypted file with all your passwords locally and hide it somewhere, than trusting a password manager like lastpass or 1password or bitwarden, but some people I guess believe they are cooler by using those services after giving your personal information like email, so you are now identifiable just like with anything else in computing.
For the paranoid people, maybe it is time to stop using your technology, it is not like Windows and Process Hacker is the only way they can get your information anyway, especially in the age of dumb technology where you can’t even easily have firewalls or adblockers or good browsers with good features like happens with Phones and Tablets, which all of your probably have and have it on 24/7.
I would actually worry more about the tracking phones do than some ‘plain text memory information’ this article suggest. Just look how easily is for anyone to track you around if you use your phone 24/7… while this? well, someone literally needs to be in your computer to really do anything and we know, they will use other ways to get your info easier than checking memory.
For example, if you have your computer with no login password, and Chrome or Firefox don’t have a way to lock the browser with a master password, how will you protect the information? by unicorn dust mixed with an elf’s pee?.
If a person can get in your computer EVEN if you had a password, then your browser is still unprotected, and there is no way to protect it unless you do workaround about it.
This memory issue is just the least of the problems, and it was obvious that’s how it worked all along. Now, it is funny how people will try to take advantage of this now it is known, because I am sure (even if it was obvious) nobody ever tried to use this method to hack anything because while they can get the info, they don’t know where it belongs to, which means, they are useless. Unless it is an obvious password or email which means… well, it sucks.
I tested on Twitch and used a false information and then it showed it as “{username: password:”}, so… some websites will be worst than others.
You know technology is meant to spy you, stop pretending ‘rights for internet privacy’ or some bullshit like that, that’s only the marketing scheme they use to sell you products and then sell your information when they get your info while pretending they protect your data and never track you.
You are using technology which have many layers of people watching what you do, when you use extensions, VPNs, and all that, well, you are making it worst since you are really trusting some people really making money the same way the others ‘bad guys’ did.
They are and there will always be companies that openly state “we will give law enforcement your data” and that’s how it works, they have access to it, they can do whatever they want, especially if you are using their service with their servers and then it is their rules.
Nobody is going to exploit this, let’s be honest, and if people get to do it, it is because the device’s owner didn’t do anything to prevent it, like having a simple firewall should be enough to stop any unauthorized remote access, because if someone has access to your computer then there is nothing Big tech and Silicon Valley can do to protect you, I mean, they are the first one working with governments so I doubt they would do anything in the first place, just wash their hands and be like “well, it is what it is”
Hmmmm
“Internet Users Discover how Computers Work!”
or
“Everything old is new again.”
It seems to me all right with Firefox after checking with the steps outlined with Process Hacker.
I also tried with KeePass and I seem to have noticed that if I use Kee Password Manager (only in this case) I can see the related login password in Keepass memory (not in Firefox too). But I’m not good at these things.
Hi Shiva,
Exactly the same here…Firefox shows up no passwords.
However, I can see the passwords in cleartext only when Keepass is open, if you don’t login to Keepass, then no passwords.
So it appears from the results the least secure is to have Keepass running continuously, which is what you are going to have to do if you don’t let your browser remember passwords !
Go figure.
This could be easily fixed by storing sensitive data in protected memory. And to make this bug worse, once a password is used to gain website account access, that protected memory allocation should be securely wiped from RAM by the browser. Secure programming 101. And, passwords could easily be encrypted while in protected memory for a proper belts and suspenders approach.
Note netizen friends, browsers are leaking sieves of your personal data in ways that are not immediately apparent. By default, firefox and chrome browsers allow websites to access many of your machine’s private, hardware/software resources. This goes beyond fingerprinting and into your highly sensitive data. You have to hunt a group of settings down to alter them because it is not simple to locate them. But, take a few minutes and locate the dangerous settings listed further below. Note, I use brave so if you use chrome, change the protocol token to whatever that spy browser uses. Back when firefox was firefox, it allowed hot linking to these settings so it was simple matter to locate them. But no longer, you have to go through just as much bs to locate them as in chrome. Of all of them, clipboard should be disabled because there is no legitimate reason a website should ever have access to this extremely private data (think ssn, bank account #, CC#s, pwds, and even website urls, etc).
brave://settings/?search=clipboard
brave://settings/content?search=usb
brave://settings/content?search=File+editing
brave://settings/content?search=camera
brave://settings/?search=Microphone
There are quite a few more settings folks should change while they hunt in advanced settings. The browser is supposed to ask for permission to allow websites to gain access to these resources. However, users are often several keystrokes ahead of the browser and frequently press enter into the KB buffer… then one of these dialogue boxes unexpectedly pops up consuming that buffered enter key press – accidentally giving access. This type of buffer issue happens to me all the time, esp while doing file maint. Also, there will eventually be browser bugs (or knowing google, intended features) that give sites unconfirmed access to HW resources.
Firefox for the win.
@pHROZEN gHOST,
> Just a thought…. what if […]
It’s those “just a thought”, “what if” that differentiate paranoia from awareness : the former asserts, the latter wonders.
This said, “Avec des si on mettrait Paris en bouteille” as we say in French (“With ifs we could bottle up Paris”). Eiffel tower included :=)
@Tom Hawack
“Avec des si on mettrait Paris en bouteille”
Hadn’t seen this expression for a long while. Do you speak French?
@Martin P., I am French. As I don’t remember who (was it Charles Quint?), “I speak to men in French, to women in Italian, to horses in German” … sorry Martin! (the other one, the site admin). Two out of three are false, not that I wouldn’t practice such a natural behavior but rather because I speak neither Italian nor German. Horses don’t care, women might … Romanella, la piu bella del mondo ….
Anyway, I happen indeed to squeeze in a comment one or two words in French… pour le bien de la patrie :=)
I’d rather be a bit more concerned and safe.
It’s complacency that causes many of the security issues.
… and what if, the reason Google won’t fix this any time soon is because they are also stealing this data?
Or passing it to 3 letter agencies and per their agreements.
Just a thought…. what if Process Hacker is uploading that data?
@pHROZEN gHOST:
Then you have no idea how process hacker works and has always worked. When in doubt use the process hacker to hack itself and reveal any such code, you will find none.
@pHROZEN gHOST
wow… your questions are really….
1. ProcessHacker is open source.
2. if you are not using a firewall already, then, you have problems… do you know what a firewall is and what a firewall can do for you? well, that means that Process Hacker can’t do anything.
The only time Process Hacker connects to the internet (anyway) is when it searches for an update, obviously if you never check it and you disable automatic updates, then it will not connect to anything.
so your “what if” is really dumb because it is obvious they don’t. I mean, if you are going to start with questions like that, you could say “what if Linux, what if Microsoft, what if Apple, what if notepad, what if….
You can literally verify that and also use the brain.
Google is not going to care about passwords, they care about building profiles for advertising which works in conjunction with tracking data, but stealing passwords? that really is far fetched dumb thinking.
@pHROZEN gHOST: That was MY first thought, as well! What if Process Hacker is the bluestriped fangblenny* of security utilities? ;-) But more seriously, it looks like Process Hacker is open-source, so I figure someone with modest coding chops would probably have spotted any untoward phoning-home code by now.
*The bluestriped fangblenny is an aggressive mimic of the juvenile bluestreak cleaner wrasse. Client fish welcome it, thinking they’re going to get the usual cleansing of parasites and dead tissue, but instead, the bluestriped fangblenny takes a nice, juicy bite of living client flesh and swims off. Oh, and it injects a little opioid compound, so the client doesn’t realize what’s happened right away. Not a bad analogy for a rogue software package!
I have not “verified” this topic (Your browser stores passwords and sensitive data in clear text in memory), but in the interest of breaking news (given the seriousness of the issue), I quoted the ghacks article and reported the following:
https://forums.mozillazine.jp/viewtopic.php?t=19815&p=72065#p72065
The community (forums.mozillazine.jp) has verified that:
In Firefox,
we could not confirm that the data stored in the password manager is always stored in memory in plain text, but it seems that while the “about:logins” page is open, the login information is expanded in memory in plain text, and when the tab is closed, the login information in memory When the tab is closed, the login information in memory seems to be erased.
Therefore, it may be necessary to be careful not to leave the about:logins page open in situations where you need to be vigilant against malicious programs attempting to steal process memory.
In Chrome,
we confirmed plain text login information from a Chrome process that only had a new tab open.
As far as Chrome is concerned, it sure is awful.
We additionally verified Thunderbird (which shares a platform with Firefox ESR).
It is the same as Firefox.
As long as the “about:logins” page is open, the login information is expanded in memory in plain text, but it disappears and does not remain once the page is closed.
As for Firefox and Thunderbird, I don’t think we should make too much noise about this. I think it is only natural that when you use data, it should be in memory.
However, I think it would be better to make sure that the time period is as short as necessary.
However, I do agree that a method such as Chrome (Chromium-based web browsers and Vivaldi Mail), where “the browser always has decrypted confidential data deployed in memory” is risky.
Japan’s “National Police Agency @Police” is issuing a warning on June 9, 2022, naming “Google Chrome”.
https://www.npa.go.jp/cyberpolice/important/2020/202012111.html
The malware “Emotet” has the added ability to steal credit card numbers, name of the holder, and card expiration date stored in the web browser “Google Chrome” and transmit them to external parties, a National Police Agency investigation found.
Because Emotet’s new feature also steals the key to restore encrypted data at the same time, an Emotet infection could reveal your credit card information to a third party.
@Marv, with an external application it is not the browser that transmits the credentials but the the extension or the external application. Bitwarden as far as it is concerned has the option to “Automatically clear copied values from your clipboard.” but IMO this applies to manually copied : not sure that when those values (user + password) are directly transmitted from Bitwarden to the corresponding input box on a browser’s page, these values are ever registered in RAM.
Nevertheless your remark is worth being dug, I’m not an expert.
P.S. this comment is an answer to @Marv yet won’t be located in his comment’s tree but at the end of the Comments because presently scripts are disabled.
As far as I am concerned the browser will have the PW from Bitwarden clipboard in the clear in RAM, then hash it if the forms requires the PW to be hashed before sending it to the server, then encrypt the HTTP POST with TLS1.3 and send it to the server.
I’m sure Bitwarden cannot make its own HTTPS POST requests. The description is very specific:
>Selecting the login inside the browser extension will auto-fill your username and password in the detected input fields.
If security of RAM is the scope of the threat model you need Intel SGX, AMD SEV/SME, Apple’s secure enclave or Android KeyStore. And even then security is dubious at best if the attack has admin on your system.
Which is why I find this “””security researcher””” hilarious. It’s like saying people can look into your underwear drawer if they are unnoticed in your home. His threat model was what again here?
Another fallacy, assumes any of these solutions are any more secure, they are not… NEWS flash
I literally implied they cannot be trusted *whoosh*
I use the Bitwarden extension for confidential data including logins (except for bank credentials).
One of the reasons I had disabled Firefox’s native Password manager is that it requires the “security.nocertdb” pref to be “false” (default). This pref concerns Firefox’s intermediate certificate caching :
“this is not a fingerprinting issue but a first party isolation and super cookie problem” [https://bugzilla.mozilla.org/show_bug.cgi?id=1334485#a6198890_474980]
Creating (it’s a hidden pref) / setting “security.nocertdb” to “true” affects login/cert/key dbs. The effect is all credentials are session-only. Saved logins and passwords are not available. Hence implies an external password manager, local or on the cloud. @Henk above emphasizes on local, he may be right, for my part I trust the Bitwarden extension.
“I trust the Bitwarden extension.” LOL imagine… did you even test to see if anything about extensions showed to memory? did you even did that or you are just talking nonsense you haven’t even tested?
Extensions are part of the browser, why would it act any different? like… if you try to log in, it should show the email you typed to log in Memory, what about anything else? Like if you use uBlock you can easily find stuff there in ‘plain text on memory’ so it doesn’t make much sense to ‘trust’ but don’t check since text is text, and when you log in to a website using bitwarden, it could still display the email/username or password.
How does that change that the browser needs the password in cleartext in RAM before even being able to transmit it? I think the issue in the article was that it is not being deleted from RAM until you close the entire browser.
Extension or password manager or no cert DB will not change how HTTPS requests to a server are made. Before you hit send on the login form, all the data is in RAM.
I am confused. The article says that the attack can be carried out by remote access, then the article says that Google won’t fix the problem because it is a “physical local access attack{s}”. Which is it?
It is a local normal debug process how Windows has always been. The scare tactics are implying if a remote execution bug exists in the future then that could be used to run code locally and this is one thing they could read from your PC.
When I wrote password managers I’d decrypt in RAM only for the time needed to fill in the blanks and then fill that variable with garbage but a good debugger would’ve seen my variables. If something is running on your PC in general it has access to too many things.
It’s a terrible article which describes a local “attack” as if it can be remotely executed. The attack is simply that a user reads his _own_ password from a process started by _himself_. This is completely expected and not a problem.
Shocking discovery, shocking! My heart is racing. It is basically that passwords in use must be loaded into RAM! Just like the only attacks on DMcrypt/LUKS and Vera-/TrueCrypt!
Next thing the “””security researchers””” tell us is, that a local attack with admin rights can directly log the passwords from our brains as we type them into the machine!
/s
(hope I wasn’t too heavy on the sarcasm this time)
No need for reading your thoughts, that’s what keyloggers are for.
That was directly implied *whoosh*
Do not store any passwords in your browser, but instead set it to never save any of them — and do use an external (but not cloud-connected) passwords manager. Also, do never save complete browser sessions, but instead set your browser to always delete all session data on exit (so there is nothing left to automatically reload at the next start). Also, do use an extension such as Cookie Autodelete to ensure that all tab-related cookies are deleted right after that browser tab has been closed (so no unnecessary data will keep lingering around during your entire browser session).
This is what I’ve been doing for years, and will keep doing. Of course it doesn’t garantuee that pasted-in passwords won’t land in your RAM. But it least it will (somewhat) minimize the risk of keeping them in memory for a longer period of time.
I wrote my own password and bookmark manager, save database in a complex folder structure (/drive/p/a/s/s/d/r/o/d/!/!/abcxyz.123) and load to clipboard through local HTTPS request using WinHttpApi, so far no security concerns.
Thank you, I needed the laugh!
Password managers? Wait, only if not cloud connected? What? Show me anything that is secure and I’ll give you a gold bar.
password-store and keeping your keys on an encrypted usb drive. I’ll store that gold bar with the other definite-not-stolen-ones I already have.
“…and do use an external (but not cloud-connected) passwords manager.”
I’m not sure how that will prevent local attacks any more than the method described in the article. If you’re running Keepass for example, malicious software running locally can wait for the user to launch keepass.exe and enter their master password – it can then just export the entire Keepass database to a plain text file using Keepass’ own export feature. Alternatively, software running locally can make a copy of the Keepass database file and then log keystrokes to capture the master password when the user enters it – as entering the master password on Secure Desktop isn’t a default setting.
Really, the entire password system needs to move away from using usernames and passwords and on to using private/public keypairs such as FIDO2/WebAuthn; with the private key being stored on a secure hardware chip such as TPM/Secure Enclave, that cannot be accessed by either the user or software running on the local machine.
The main stumbling block with FIDO UTF and FIDO2 has always been end user usability, however with “Multi-device FIDO credentials” (Passkeys) coming to all major operating systems later this year, hopefully it will gain more widespread adoption.
https://media.fidoalliance.org/wp-content/uploads/2022/03/How-FIDO-Addresses-a-Full-Range-of-Use-Cases.pdf
This will not only alleviate passwords being dumped on a local machine, phishing attacks, etc., but will also make server password database breaches a thing of the past, as companies will only need to store public keys of users in their databases rather than passwords – so there is nothing of value to steal.
Using a password manager locally is my preferred option too, but if you are after maximum security make sure the database locks down after some period of inactivity or event, like minimizing it or at least after suspend. Password mangers like KeePass (at least KeePassXC) also have the option of clearing your clipboard after a few seconds to prevent attacks on it, which if far easier for other programs to access it.
I am using Internet Explorer with JavaScript disabled so I have no worries.
https://death-to-ie11.com/
Bill, Internet Explorer goes End of Life on 15 June.
I have just switched yesterday from Internet Explorer to Opera browser. And Wow this thing is fast! The pages are more responsive and I can block ads right away.
I will try Firefox browser next, is there any other browser recommendations? I don’t want to use Chrome at all.
You should try Vivaldi it is from ex Opera developers
Yeah, Vivaldi is cool for it is very customizable.
Oh yea Internet Explorer will save you. NOT. If not a problem for this, its a problem everywhere else, its a shit browser filled with many vulnerabilities many of them not public and so unpatched and should have been put to death the moment it came out to the public.
Well, until they don’t show how to ‘extract the data remotely’ then, it is just speculation. Of course, in the time where people give random ‘support’ people access to their computers, this is the least of the problems.
I mean, if someone has physical access then, nothing matters, and saying how ‘loads in memory’ it’s really irrelevant if most people will save their passwords in their browser anyway, so that means, instead of lookin in memory, the person can just look in the password manager. As far as I know, only Yandex offers a feature to create a master password to protect the passwords.
the thing about this is how the person has to even know your password, yeah, it is on plain text, but the person won’t know much about where it belongs to, that means that if people don’t use familiar names or numbers that can be searched and used like a password generator, then it will make it harder for people to access the info.
I mean, it is not even hard to get a lot of sensitive information with the unsecured profile data of a browser. If someone has physical access to a computer. I remember trying popOS and used the same profile I had on windows, and the browser didn’t even complain about how it wasn’t the same OS installation or anything, so it was even more insecure.
So while this looks wrong, let’s be realistic, it will be like not something people are going to really use to get information or will not be the best. Of course, memory has everything, urls, passwords, cookies info, everything… but it sounds really unrealistic to think a random person will see it and know where things belong to.
It says right in the article that url and cookie data can be extracted with the username and password data. The bad actor would know exactly where to use the credentials.
“Until they don’t show…” or “until they show…?”
How can I test this on Linux?
Shouldn’t memory be owned and locked by the process that allocated the memory?
With elevated rights you can read and modify other processes memory, that’s how the Cheat Engine works.
But the article says “non-elevated process”, that’s sounds indeed impossible.
You not needed to be elevated to debug (read memory) of another non-elevated process, as long, as your user have this privilege (granted by default for non-elevated admin). And there is nothing wrong with this.
PS: Also as long user can decrypt own data (without additional actions) stored in profile (cookies) – other processes surely can do same silently.
The download off the portable version gets blocked by Bitdefender, saying that the website from Sourceforce is infected. This happens after the countdown for the download itself.
ESE IS = Process Hacker containe malware
I was instantly weary when that app was linked in the article
Wow, that really tuckered you out, huh?
Virus Total found 17 Malicious Viruses on the portable version. WOW!