0Patch has a patch for Windows "InstallerFileTakeOver" 0-day vulnerability, Microsoft has none

There is a 0-day vulnerability for Windows, called InstallerFileTakeOver, which Microsoft has yet to address. The vulnerability was discovered by Abdelhamid Naceri, a security researcher, who discovered two other 0-day vulnerabilities in Windows this year already.
We mentioned the vulnerability in late November 2021 already here on this site. The issue was unpatched back then and Microsoft has yet to release a security update that addresses the vulnerability.
Micro-patching company 0Patch released a free patch for the issue this week that is available to all users. The micropatch that 0Patch released is available for the following operating systems:
- Windows 10 version 1709 to 21H1.
- Windows 7 ESU
- Windows Server 2012, 2012 R2, 2016, 2019.
- Windows Server 2008 R2 ESU
0Patch notes that non-ESU Windows 7 and Windows Server 2012 installations are not affected by the vulnerability. Windows Server 2022 and Windows 11 are likely also affected, but not officially supported by the company yet (hence no patch). Windows 8.1 was not analyzed because of low interest in the particular version of Windows.
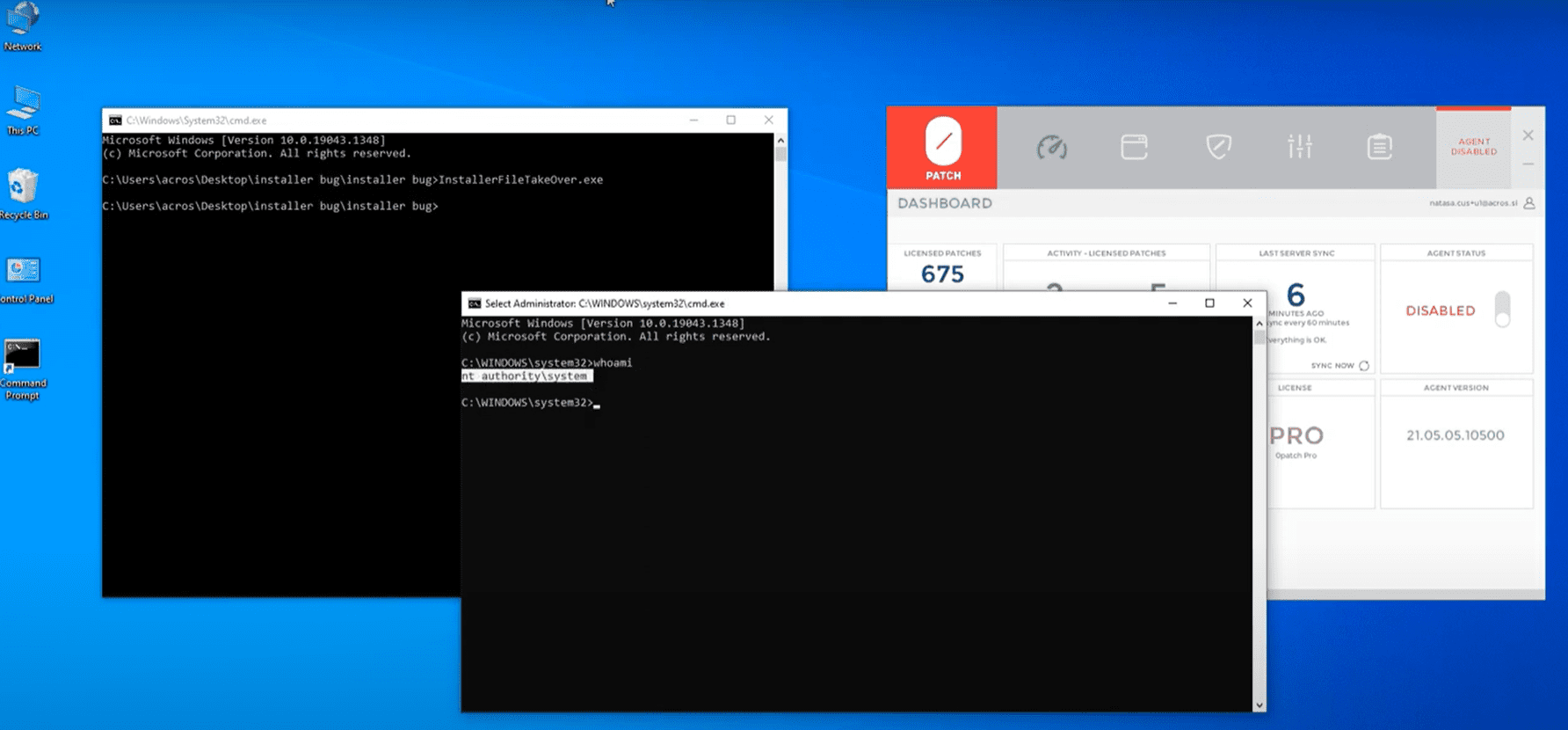
The vulnerability takes advantage of rollback files that Windows Installer creates during installation. It stores files that are deleted or modified during the installation process, to allow rollbacks. The rollback file is created in system directories and then moved to a temp folder in the user's directory.
Naceri discovered that a symbolic link can be placed in the location, so that the RBF file is moved to another location. The symbolic link points to a file on the system that is then made accessible to the user, provided that Local System has write access to it.
Since Windows Installer is running as Local System, any file writable by Local System can be overwritten and made writable by the local user.
The micropatch that 0Patch has created checks if the destination for the rollback file operation contains junctions or links. The operation is blocked if that is the case, or allowed otherwise.
Patching systems with 0Patch micropatches requires a free account at 0Patch Central and the installation and registration of 0Patch Agent from the company. The patch is applied automatically, a reboot is not required.
Here is a demo video that 0Patch published on YouTube:
Here is the video of our micropatch in action. Without the micropatch, exploit works and a command line window is launched as Local System; with the micropatch, the code we correct in msi.dll determines that destination path contains a symbolic link, aborts the file move operation and triggers an "Exploit blocked" event.
Check out the 0Patch blog for additional details.
Now You: how do you handle unpatched vulnerabilities?

















Disappointed to note that 0Patch won’t be supporting Windows 8.1 once MS support ends in just over a year’s time. Too little interest according to their blog.
So as far as I can tell it takes a non-elevated local user to install a nefarious .msi? As usual be careful what you install I guess. I’m glad there are white-hats out there looking for exploits and putting pressure on MS.
All these security 0 day vulnerabilities risk are just a farse, another way to make propaganda and brainwash people to fear, just like the lies that you will ever get privacy online, and you will stay anonymous and life on the internet will be perfect because you harden Firefox (because it is the only one you can truly do that, not because I think it is any good) or you use 30 adblockers and 90 antitrackers, or you use ungoogled chromium instead of Opera, etc etc, or using Signal which is funded by US and other governments or Session, or Jami or any P2P, onion routing which is controlled and centralized in the end, even if they tell you decentralization is the future.
It is like the lies about “security suites” and all the antimalware and antivirus, 0days Heuristic analysis and “we will protect you”.
Microsoft is not more secured or dangerous than any other OS, understand it. Linux will not protect you, MacOS is not going to protect you… or people forgot how the boogeyman spectre and meltdown appeared, and the way to “protect you” is to slow down your computer you?
What’s my point? well, all this BS talk about “vulnerabilities” is just dumb because to make a symbolic link you will have either physical access to a system and you need rights, you need admin rights today to make a symbolic link, you know, right click, start as admin blabla.
So how is this a so critical “0 day vulnerability”? (yes, it is just propaganda), you literally need to allow other person to do it, and even if there was 1 small change 1 in two trillion that this can be done by another person in another galaxy, it is not going to affect ANYBODY, this just another boogeyman to make you believe system can be “patched” and be “secured” so you can have a better life on the internet.
You literally need to move it to “users directory”…. do people think these things happen often?
This is not going to affect anyone even if Microsoft doesn’t patch it in 10 years. And if this vulnerability is already patched, if someone somehow has access to another person’s computer, I doubt a symbolic link would be the worst of problems.
People today already open random attachments and emails, people fall for the phishing more than any other “attack” why? because phishing is the easier way to get money from ignorant people who think they will get money for opening an email from a random person in the spam folder.
I mean, I know humans are dumb and fall for any propaganda but come on… this goes way beyond ridiculous reporting, not your fault Martin, but accept it, this will not affect anyone, they are just bugs that will not affect anyone who has more than 2 braincells, and it is not the “attack” someone will ever do, when they can do easier things since most people barely have any braincells
“I know humans are dumb and fall for any propaganda”
Well, based on your rather voluminous post, I have to agree with you.
KDE Plasma.
CLW Type A
Tuborg
MS only uses security as a pretext to take away user control and force users to buy subscription based licenses. And they forcibly bundle their security patches with spyware and adware via windows update. Win 10-11 consistently has more critical security issues each month than 7-8, meaning newer versions of Windows are less secure at the core system level. It goes to show how low of a priority security is for them.
0Patch uses micropatches. Microsoft seems hell-bent on making patches larger (and it follow, more complex). Also, 0Patch cherry-picks what they patch. Quote from 0Patch
“The goal of 0patch is not to micropatch every vulnerability but the important ones, such as those exploited in the wild or those without official vendor patches.”
It would be surprising if the patches 0Patch release were not well ahead of Microsoft.
Microsoft has become a joke of a company since 2014. Its run by unskilled fools.