Firefox 93.0 release: here is what is new and changed

Firefox 93.0 will be released later today, if you are reading this on October 5, 2021. The new stable version of Mozilla's Firefox web browser is a feature update that includes security and stability fixes as well.
All other Firefox channels are updated around the same time. Firefox Developer and Beta versions are upgraded to version 94, Firefox Nightly to version 95, and Firefox for Android will also be updated to version 93.
The last Firefox 78.x ESR version is released today. Mozilla released Firefox 91.0 ESR in August, and it will become the only supported ESR channel when Firefox 94.0 is released next month.
You can check out Firefox 92.0 release information, in case you missed it or want to read it again.
Executive Summary
- Firefox 78.15 ESR is the last release of the branch, and the only supported version of Firefox to support Adobe Flash and Mac OS X versions 10.11 and older.
- Firefox supports the AVIF image format by default
- WebRender should be enabled on all systems now.
- Firefox 93.0 includes security updates.
Firefox 93.0 download and update

Firefox installations will be updated automatically on most systems, as Firefox checks for updates automatically in intervals to download new updates automatically.
To check the installed version, go to Menu > Help > About Firefox. Note that this will also run a manual check for updates and will install new versions that are found during the scan.
Manual downloads are also available. The following pages list direct downloads for supported Firefox channels.
- Firefox Stable download
- Firefox Beta download
- Nightly download
- Firefox ESR download
- Firefox for Android on Google Play
New features and improvements
AVIF format support is enabled by default
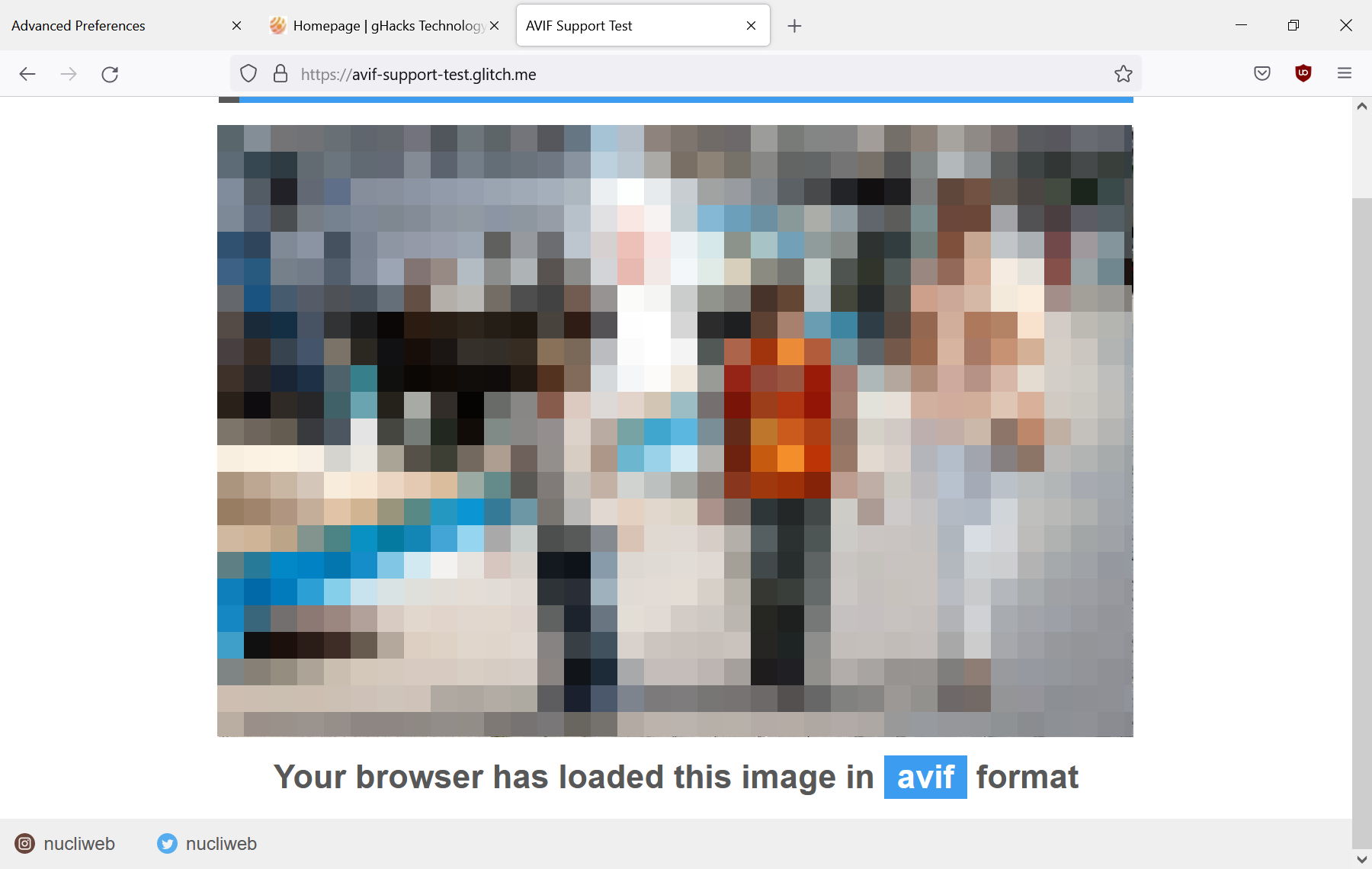
Mozilla planned to enable AVIF support in Firefox 92, but postponed the release. AVIF support is enabled by default in Firefox 93. It is an open format that offers "excellent compression" and has no patent restrictions.
The Firefox implementation supports still images, "with colorspace support for both full and limited range colors, and image transforms for mirroring and rotation", but no animated images.
Tip: open this test site in your browser to see if it supports AVIF.
Unload tabs on Windows when memory is critically low
Firefox includes a new tab unloading feature on Windows. It is an automated feature that will unload tabs if available "system memory is critically low".
Tabs are unloaded based on last access time, memory usage and other attributes.
Mozilla hopes that the feature will reduce the number of memory-related crashes that users of Firefox experience.
See our full coverage of Firefox's new tab unloading feature here..
Insecure downloads are blocked by default
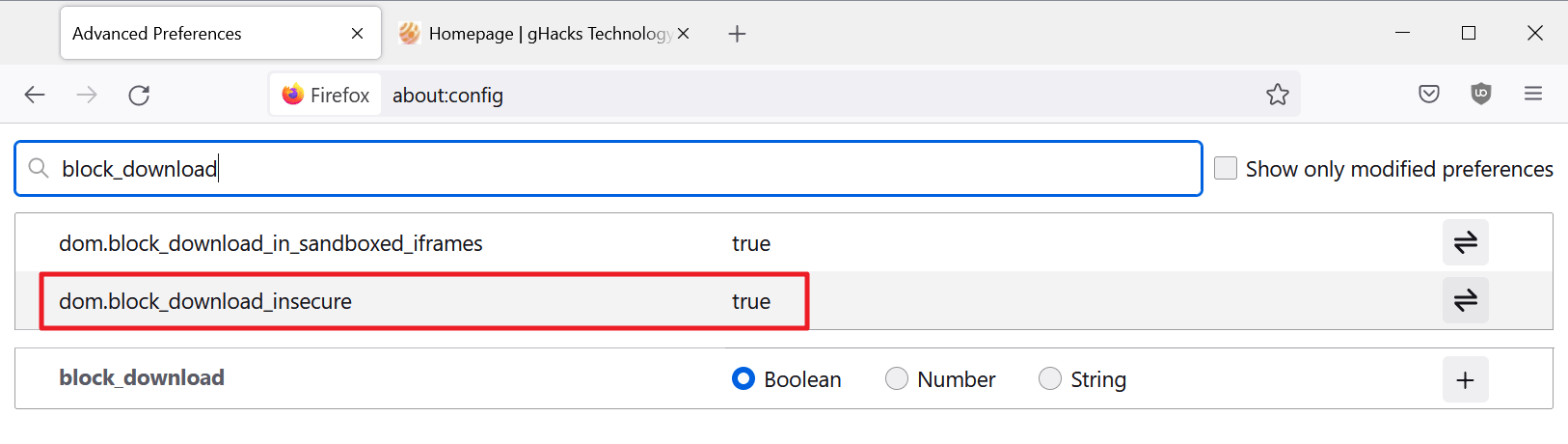
Firefox blocks insecure downloads by default now (non-secure downloads on secure webpages).
The preference dom.block_download_insecure can be toggled to allow insecure downloads again, by setting it to False.
- Load about:config in the Firefox address bar.
- Confirm that you will be careful if the warning prompt is displayed.
- Search for dom.block_download_insecure.
- Set the preference to FALSE.
See our full coverage of the new insecure downloads blocking feature of Firefox here.
Other changes
- Firefox's PDF Viewer supports filling out XFA-based forms, which some governments and banks use.
- Firefox users on Mac OS are prompted to finish installation if they run the browser from a mounted .dmg file to prevent session loss.
- Web compatibility improvements for Firefox's SmartBlock feature.
- New referrer tracking protection when Strict Tracking Protection is enabled, and in Private Browsing.
- VoiceOver screen reader reports checkable items are checked or unchecked.
- Orca screen reader works correctly with Firefox now. Users don't have to switch to another application anymore after starting Firefox.
- Download panel "follows the Firefox visual styles" now.
Developer Changes
- The SHA-256 algorithm is now supported for HTTP Authentication using digests. "This allows much more secure authentication than previously available using the MD5 algorithm" according to Mozilla.
- The default HTTP ACCEPT header for images changed to: image/avif,image/webp,*/* (following addition of support for the AVIF image format).
Enterprise changes
- TLS ciphersuites that use 3DES have been disabled. They can be re-enabled only when deprecated versions of TLS are enabled.
Known Issues
None listed.
Security updates / fixes
Security updates are revealed after the official release of the web browser. You find the information published here after release.
Outlook
Firefox 94.0 will be released on November 2, 2021. Firefox 91.4 will be released alongside it, and it will be the only ESR version that Mozilla will release, as Firefox 78.x ESR will no longer be supported as of November 2, 2021.
Recently Reviewed Firefox extensions
- Don't track me Google for Firefox blocks links manipulations by Google when clicking or copying
- JavaScript Restrictor: improve privacy by limiting web browser APIs
Recent Firefox news and tips
- Firefox 93 for Android becomes system-wide password manager
- Mozilla VPN boosted with multi-hop, blocking and custom DNS features
- Firefox Experiment is testing Bing as the default search engine
- Mozilla reverse engineers Microsoft Edge's default browser setting behavior
- How to disable Firefox Suggest
Additional information / sources
- Firefox 93 release notes
- Firefox 93 for Developers
- Firefox for Enterprise 93 - release notes
- Firefox Security Advisories
- Firefox Release Schedule






















@Martin Brinkmann
There is sonatype.com *pop-up* window, maybe from smartadserver.com. I had to block all your ads.
Can you fix that and I can unblock ads?
Years… literally years. Iron Heart is still in every single Firefox article with his autistic arguments that practically add nothing to the discussion. You’re infamous here dude, Congrats on the lifes achievement.
“smallppman”
I don’t even know who you are.
Martin. how to turn off firefox nightly telemetry
@jennie
Here might be some prefs:
https://github.com/arkenfox/user.js/blob/master/user.js
How about Webrender in Firefox. It is still possible to turn it off?
My friends and I, have stopped updating Firefox since version 91.It messed up with the bookmark drop down menu spacing. We fixed the issue using the followings:
about:config toolkit.legacyUserProfileCustomizations.stylesheets true
Create folder and file C:\Users\XXX\AppData\Roaming\Mozilla\Firefox\Profiles\XXX.default-release\chrome\userChrome.css and copy the following 2 lines. Restart Firefox.
menupopup > menuitem, menupopup > menu {padding-block: 0px !important;}
:root {–arrowpanel-menuitem-padding: 0px 0px !important;}
My question is when Mozilla will fix ?
@Eddy, in about:config, set (create this boolean pref if it doesn’t exist) :
browser.uidensity = 1
// 0=normal mode, 1=compact mode, 2=touch mode
Firefox 93 now includes bringing back menus’ padding to a reasonable value when uidensity is set to compact.
EDIT : “create this boolean pref if it doesn’t exist” : integer, not boolean
SEE : https://www.reddit.com/r/firefox/comments/q228mf/make_the_bookmarks_smaller/
Since 92 release I noticed that with privacy.resistFingerprinting enabled Cloudflare browser checking goes into an infinite loop.
@Shiva
Talk about getting locked out like Tor without enjoying the benefits of Tor, LOL.
that’s a cloudflare change, not a Firefox one
Since the Firefox 92.0 version the drop down menus from the personal bookmarks
bar don’t have anymore borders and thus are less comfortable to differentiate from
the general background.
These borders were a thin grey line at the top and left sides of each menu and a
grey shadow at the bottom and right sides as one can see on the context menus
where they still are present.
These borders are really missing.
Maybe some css lines could bring them back ?
Would someone know a solution ?
Thanks.
Add the following userChrome.css
/* MENUS – BORDER */
menupopup {border:1px solid #000 !important;}
Thanks. I was able to add the borders with your line I changed the color to a grey one.
I have almost recovered the popup menus as they were in the versions before the 92
one.
I wonder why they have changed the pop-up menu as every other menus have kept the original design ; a thin line for the top and left borders and a shadow for the bottom
and right ones. It makes them really more separated from their environment.
Here is my code :
#personal-bookmarks menupopup {
max-width: 350px !important;
–arrowpanel-background:#F0F0F0 !important;
border:1px solid #979797 !important;
background-color: #F5F5F5 !important;
}
The “background-color” adds the shadow on the right and bottom sides, but it creates a different color in a little space that is between the borders and the “arrowpanel-background”
(the color #F5F5F5). Actually I made a screen shot of that space and once it is enlarged it present three strips of a gradient grey color. None of them is #F5F5F5. ??
@Ygerad, your CSS code applies only to #personal-bookmarks menupopup whilst mine applies to all poups. Your quest was for #personal-bookmarks so I should have limited my solution to that.
I don’t quite understand why Firefox devs apply so apparently complicated design algorithms for this #personal-bookmarks menupopup. On the other hand if the corrections users apply fit their visual comfort then brain-storming on the why of the why when zooming in a graphics display is maybe interesting in theory but, as far as I’m concerned, deserves attention only for theorists, which I am not.
One thing seems sure, IMO : whatever the qualities of Firefox, design has never been its first one. The browser designers who understand — feel — what harmony is, its imperative nature when it comes to colors, proportions, overall rendering, seem to be unqualified. And this deserves more than considering design as extra superfluous little flowers (as a techy once told me). It’s a balance : excessive design is indeed a bother, lack as well; it’s all in harmony. Ask an interior designer (after all a GUI is a 2D environment) and you’ll see that his/her answer will always be led by the notion of harmony. Firefox’s GUI lacks harmony, and it’s not the only app/software to de-consider aesthetics even if one has to admit things have progressed since the old times.
@Tom Hawack
I agree that aesthetic in a browser isn’t about “extra superfluous little flowers”. Aestetic
has a real usefull function, as for the popup menus on which I spent much time ; I think
the reading of these menus is incomparable when they have borders and shadows.
I think that the Firefox team has modified their software in the right direction but it shouldn’t be oversimplified. Though I think it is the best browser I couldn’t use it in its default configuration.
I have found the solution for the menus. It was on this web page :
https://www.reddit.com/r/FirefoxCSS/comments/k0u9rk/how_to_style_all_menu_popups_in_firefox/
I tweaked a little that script and was able to recover the popup menus exactly as they were before the 92 version. Here are the lines :
menupopup:not(#BMB_bookmarksPopup) {
appearance: none !important;
border: 10px solid transparent !important;
background-origin: border-box !important;
background-clip: content-box, border-box !important;
margin: -10px !important;
}
.menupopup-arrowscrollbox:not([part=”arrowscrollbox”]),
.menupopup-arrowscrollbox[exportparts=”scrollbox: arrowscrollbox-scrollbox”] {
appearance: none !important;
background-color: #f5f5f5 !important;
box-shadow: 5px 5px 5px -5px #000000 !important;
border-radius: 0px !important;
border: 1px solid #979797 !important;
overflow: hidden !important;
}
(plus the lines that already were in my css file :)
menupopup > menuitem, menupopup > menu {padding-block: 0px !important;}
#personal-bookmarks menupopup {
max-width: 350px !important;
}
There are several lines that I don’t understand at all, but it works (eureka !).
Here is a link to a web page which help to understand and create box shadows :
https://cssgenerator.org/box-shadow-css-generator.html
Thanks for your answers.
@Ygerad, thank *you* for two things : 1- for digging, 2- for sharing your discoveries. I know what digging means, that determination to bypass surrender in order to achieve a quest. I copy your code and the link. All this has as you say a real useful function, that of an easier approach to the modules of a browser and therefor, for those concerned, improved “productivity” (I dislike the word, for my part i’ll consider “experience”). The beat goes on :)
https://github.com/black7375/Firefox-UI-Fix
See if this can help, shared by other readers before in another article.
I haven’t dived into this as I use default design but you’re welcome to check if it can help you.
That github page is too complicated. It has hundreds of options which I don’t understand.
I don’t really know the css code. I created the userChrome.css file and added lines that
I had found here and there on the web and that solved the modifications I needed.
These past days I have tested different css lines about the menu borders that I have found
on the web but none of them worked.
Thanks.
martin is arkenfox enough enough for firefox configuration
brave fingerprint test looks more unique
@milton
> martin is arkenfox enough enough for firefox configuration
The belief that you can reduce your uniqueness by changing a few settings here and there is illusory. If you want to use something Firefox-based, try the Tor Browser Bundle.
> brave fingerprint test looks more unique
It is supposed to. Brave randomizes certain values, meaning that you are unique per site and per session – you are again unique to the same site in a new session, but not with the same values. You are unique but never statically so.
firefox is said to be better for privacy
Brave looks more unique in tests
what is your opinion
my opinion is that brave sucks and firefox is great and wonderful because both depend on google, but baker seems to more successful than eich, maybe its the big p***y energy.
> The belief that you can reduce your uniqueness by changing a few settings here and there is illusory.
> Brave randomizes certain values, meaning that you are unique per site and per session – you are again unique to the same site in a new session, but not with the same values.
Eh, doesn’t arken fox do the same thing as brave then?
Source (comments in this thread) : https://www.reddit.com/r/privacytoolsIO/comments/ovqwyn/how_to_get_rid_of_your_browser_has_a_nearlyunique/
A while back I read the above thread and put a stop to my pseudo-privacy obsession. I was lazy to do the tests mentioned in the comments myself, so I took their word for it. Hence you can do the tests yourself and be sure about it.
If I was wrong then feel free to burn the houses of those 50 redditors.
the incessant falsidical paradoxes of iron heart are becoming tedious
arkenfox uses RFP which randomizes canvas which almost every script has so it is the equivalent of raising entropy for naive scripts same as brave. A naive script is one that falls for the random value. You do not need a crowd to hide in as iron heart keeps claiming.
brave is not “more unique” than RFP. coveryourtracks has hard-coded a bias that if there is more than one randomized value, then they give top marks, which is brave. Their point is that if something is randomized then it makes you unique and fools naive scripts, but they never give Tor Browser or RFP this distinction, only brave – and it’s hypocritical given they detect the randomness
Advanced scripts (meaning they do not fall for the randomizing) return a lowered entropy like coveryourtracks which shows “randomized”. This affects both brave and firefox. Somehow brave gets extra credit for randomness but is not pinged for all the unprotected items. RFP however covers enough items to make fingerprinting very hard, whereas brave doesn’t cover enough (think fonts, screen, timezone, languages, chromium only APIs like keyboard and many more). Brave is years behind and struggling to even patch it’s own leaks after years: canvas leaks, audio leaks, plugins can be bypassed, and other randomizing can be undone. Brave does have an advantage in that it’s shields are on by default (like Tor Browser) because with advanced scripts you need a crowd
coveryourtracks and similar sites providing entropy are a load of shite, they are only good for seeing what you return
So who will get there first – brave adding enough protection and fixing all their leaks, or firefox making RFP front facing and/or a default in Private Windows and perhaps getting around to finishing webgl protection. This is ignoring that fact that an IP is part of a fingerprint, such as ISP, gateway, VPN provider – and the damage from that is immense and affects both browsers
Only Tor Browser can protect you properly
thank you gustav, I will use arkenfox and firefox as it is superior to brave
@gustav olafsson
> arkenfox uses RFP which randomizes canvas which almost every script has so it is the equivalent of raising entropy for naive scripts same as brave. A naive script is one that falls for the random value. You do not need a crowd to hide in as iron heart keeps claiming.
That’s not an argument to use Firefox over Brave. Don’t know why you are attacking me.
> coveryourtracks
Who mentioned that crap? I didn’t. You did.
> a bias
Proof or bust.
> and it’s hypocritical given they detect the randomness
Where Firefox does randomize, e.g. Canvas, the randomization can also be detected. That the randomization can be detected is irrelevant because it doesn’t help the tracker one bit. It still doesn’t get the hand on the real values, no canonical fingerprint emerges.
> RFP however covers enough items to make fingerprinting very hard, whereas brave doesn’t cover enough (think fonts, screen, timezone, languages, chromium only APIs like keyboard and many more).
Do you know how long Tor has been doing what they are doing? Mozilla got what they got from Tor. Brave’s defenses are still in their infancy and when they do something, web compatibility has to be kept in mind because the defenses are supposed to be enabled by default in Brave. RFP may cover “enough” metrics (and hopefully the user.js users don’t further modify things, breaking through RFP in the process, lol) but it comes at a price, the experience is horrid (and only acceptable for Tor, where it belongs).
> Brave is years behind and struggling to even patch it’s own leaks after years: canvas leaks, audio leaks, plugins can be bypassed, and other randomizing can be undone.
They are currently the FP defenses. Firefox also still has leaks after years and years, notably WebGL and extension leaks.
> So who will get there first – brave adding enough protection and fixing all their leaks, or firefox making RFP front facing and/or a default in Private Windows and perhaps getting around to finishing webgl protection.
Brave, because Firefox won’t exist in five years time if the current trend is anything to go by.
> Only Tor Browser can protect you properly
“If you want to use something Firefox-based, try the Tor Browser Bundle.” – Me, a few comments before.
> Firefox also still has leaks after years and years
Where are these leaks then, please do enlighten us. Don’t list items they do not protect, otherwise I could list at least a hundred items Brave fails at. A leak is when they didn’t fully patch the protection, not a list of all possible items.
> Mozilla got what they got from Tor
RFP was written and improved from scratch by Mozilla, some based on ideas from Tor Project, but the majority of it was rethought and completely changed and added over five releases, call it six months. They have been solid ever since. They certainly didn’t implement protections and ignore service workers for two years, or add methods that could be completely bypassed or waste time on amateur gimmicks like random spacing in strings, and they added far more protections in that small time frame that the tiny amount that brave has. And at the same time they added first party isolation.
There was a dedicated Tor Uplift team and resources and time was spent on it. You make it sound like Mozilla didn’t do anything and it was all gifted to them by tor project.
stop making excuses. just admit that brave is not trying to defeat fingerprinting except naive scripts, and that is all they ever will do. To brave, allowing massive holes a dump truck could drive through is not a problem, because naive scripts aren’t that advanced. They don’t care, it’s low priority. This is a brave half-assed gimmick like most else they do. The only robust fingerprinting is RFP, and yet you claim that all hope lies with brave – you are deluded. Only Firefox is engineering real solutions by tackling the actual causes, not the symptoms
> Proof or bust
Assuming you can read, go look at the source and issues at github – it’s right there
@Anon
Admit that most of the code comes from the Tor project and only exists in Firefox to make the maintenance of Tor easier (by shifting the maintenance burden from the Tor Project to Mozilla). It can and will never work in Firefox because custom Firefox setups tend to be unique, RFP is meant for preconfigured browsers like Tor that tackle values outside of RFP in a specific way. Firefox users endanger themselves by coming up with custom setups, sometimes even breaking RFP in the process by modifying values actually covered by it.
Brave fights what you call “naive” scripts, i.e. most fingerprinting scripts. It also outright blocks a great deal of them natively, without the need for extensions, and does a great deal more than RFP with the weak ass Disconnect list here. I don’t feel insecure or “unprotected” by using Brave. I also want to maintain reasonable web compatibility and not break things left and right like Firefox user.js scripts that are poor imitations of Tor. I also don’t believe that Firefox will be a thing anymore in five years so there is that as well, and that is not even considering its worse web compatibility / security / performance etc. all of which are good arguments against using it. You act as if the FP defenses are the only reason to use the browser, while having a horrible browsing experience that doesn’t get you much further than what Brave does.
Last time I checked, vanilla Firefox + vanilla arkenshit user.js, I got font leaks, navigator object leaks, buildID leak, actual version number leaks via feature detection despite the sorry ass fake user agent with RFP, DRM leaks, and if I followed the arkenshit wiki, I would probably also get extension-related leaks like uBlock Origin leaking its lists etc. It’s horse shit.
And that’s not even talking about elements that are not yet tackled like WebGL, or protections that can hardly be upheld because they break things left and right, like Canvas, but you don’t want to hear about those, right?
@Iron Heart
1. “great deal more than RFP with the weak ass Disconnect list here”
2. “Last time I checked, vanilla Firefox + vanilla arkenshit user.js, I got font leaks, navigator object leaks, buildID leak, actual version number leaks via feature detection despite the sorry ass fake user agent with RFP, DRM leaks, and if I followed the arkenshit wiki, I would probably also get extension-related leaks like uBlock Origin leaking its lists etc.”
1. I suggest you put that bottle of wine or whatever you’re having, RFP is different.
2. Do bottle thing again.
uBO leaking its lists – so does any other adblocker including Brave, enjoy.
Various leaks – First that is totally false, so good job there. To prove it otherwise, why don’t you elaborate your point further, if you can? Of course that might save you 5 quid.
@Yash
1. RFP and ETP (fingerprinting script blocking) are both part of the fingerprinting defense. I have never said that ETP is a part of, or identical with, RFP. You made that up.
2. Brave, if unchanged, runs with a few (already powerful) lists and the leak would be the same one for every Brave user unless you enable more lists.
* [Editor: removed. Stay polite, and your answers stay. Continue being impolite, e.g. by altering usernames or other names, and your replies won’t show up]
1. I actually didn’t made anything up. I highlighted your quotes. In your comment you mixed RFP and Disconnect.
That’s it.
Fingerprinting is different than adblocking. Tor Browser doesn’t have an adblocker, yet still a champ in avoiding fingerprinting. RFP is different than Disconnect. So next time be careful what you’re writing.
Finally RFP helps in avoiding fingerprinting. ETP’s main job is to stop trackers, and now dFPI is part of it too. I know this already.
2. “Brave, if unchanged, runs with a few (already powerful) lists and the leak would be the same one for every Brave user unless you enable more lists.”
First thanks for deflecting the main point which was about various leaks when using user.js file.
Second about what you wrote in last comment – That’s definitely not the case with various metrics leaking real values which in itself doesn’t allow Brave users to form a crowd. So this point is moot.
@Yash
> I actually didn’t made anything up. I highlighted your quotes. In your comment you mixed RFP and Disconnect. That’s it.
OK. If you say so. I think the entire thread here, including my comments, make it abundantly clear already that RFP and ETP are not the same thing. But whatever.
> Second about what you wrote in last comment – That’s definitely not the case with various metrics leaking real values which in itself doesn’t allow Brave users to form a crowd. So this point is moot.
The idea is for Brave users to form a behavioral crowd. You seem to think “Crowd = all users look the same, exact same values” but this is not the case. It is actually sufficient when “Crowd = all users behave the same”, i.e. all Brave users randomize and this behavior is consistent across installations. That Brave does not yet cover all metrics was repeated ad nauseam in this thread already – it will be tackled, but the basic idea is a behavioral crowd even though the implementation is not yet complete obviously.
> First thanks for deflecting
* [Editor: removed. It is really simple. Stay polite, and your comments (meaning everyone’s comments) are published. Be impolite, and they are not published. Impolite includes changing usernames or project names. It is not difficult. If you spot something that you consider a violation, let me know, and I take a look at it.]
> I got font leaks, navigator object leaks, buildID leak, actual version number leaks via feature detection despite the sorry ass fake user agent with RFP, DRM leaks
None of those leak. And if that is all you can come up, then I stand vindicated that you couldn’t find anything, especially considering that RFP protects many more items than brave, and yet brave leaks everything
DRM is not RFP protected, so invalid. And clearly you do not understand the rest: that the lowered entropy is per criteria. Your ignorance knows no bounds.
There are no fonts leaks. Font protection is enabled for windows, mac and some linux distros. When used, it does not leak. Prove otherwise, because robust testing says you are a liar. If your claim is that some platforms differ, that is by design. The protection is per platform, including allowing differences in windows 7 vs windows 8/10. Look up the word equivalency, and that this is not a leak
Navigator object does not leak. The object itself is protected. What objects are protected?
– buildID, productSub, appCodeName, appName, product are the same for ALL Firefox users
– platform is the same for each OS, RFP does not lie about this so it can’t leak
– that leaves appVersion, oscpu and userAgent which combines the others and adds a version
– hardwareConcurrency
– these do not leak in JS using the navigator object – not in iframes or via any workers in any way shape or form
So flat out caught you making up more LIES and you trying to pad your pathetic list by listed non-items e.g. DRM and listing items twice – e.g. buildID is already listed under your navigator item, and it does not leak – it is the same for ALL USERS
What you fail to realize is the reason navigator was added as it is. It is not trying to fully protect these as this is impossible – it’s not even trying to hide the platform. It is to make it harder for scripts, especially when JS is disabled such as safest in Tor Browser. If users are up to date, then any leaks are the same for everyone. If you knew anything about fingerprinting, which you clearly do not, then you would understand that this is equivalency and is not being protected
> Brave fights what you call “naive” scripts, i.e. most fingerprinting scripts. It also outright blocks a great deal of them natively, without the need for extensions, and does a great deal more than RFP with the weak ass Disconnect list here
reality: RFP in firefox fights what you call “naive” scripts, i.e most fingerprinting scripts. It also outright blocks a great deal of them natively, without the need for extensions
iron heart: brave works and is good, firefox with exact same method, not working , no good.
reality: iron heart can’t logic
iron heart: disconnect is weak
reality: iron heart making up alternative facts and confusing tracker/fingerprint blocking with adblocking. disconnect’s fingerprinter’s list comes from openWPM which is world class, Also dFPI makes this moot – real solutions from real engineers
iron heart: brave randomizes and is in a crowd
reality: there is no crowd because it’s randomized
iron heart: leaks come from compat
iron heart: blah blah blah
iron heart is deliberately being obtuse and ignorant
Here’s a tiny snippet of iron hearts lack of knowledge on the subject
– https://www.ghacks.net/2021/07/31/how-firefoxs-new-smartblock-feature-works/#comment-4501396
– https://www.ghacks.net/2021/07/31/how-firefoxs-new-smartblock-feature-works/#comment-4501361
I don’t know why you’re still ranting about some arkenfox user.js or compat. These have nothing to do with the effectiveness of protecting real values. Your noise levels are stupendously loud, and clearly arkenfox or the fact that firefox can tweak hundreds of settings via this methods triggers you – seek some help
> You act as if the FP defenses are the only reason to use the browser
I’m not acting like anything. Where did I say that? More lies.
I use Firefox because it is the best browser for privacy, hands down – FPI/dFPI, full proper network isolation, and many other options other browsers only wish they could add. Real solutions. Not shitty half baked gimmicks like Brave’s sevn days cookie lifetime, which didn’t cover all cookies, let alone all storage methods, and is bypassed with prolongation attacks.
Brave pales in comparison. Brave is a browser run by an advertising company, which uses privacy as a gimmick to suck in gullible users. Enjoy your shilled shitty bat-shady crypto client which doesn’t build anything except useless and incomplete wonky patches on top of google’s wet dream
@Anon
You are so, so right. I was so, so terribly wrong. The leaks only existed in my imagination, since you assured me that they don’t actually exist, I instantly regained peace of mind. All the science and robust testing is against me, how could I have been so foolish to report my findings? Must have been hallucinations, clearly.
I am also happy that people like you, with all of your immense coding experience, are shining down on little ignorants like me with your light and brightness. I feel so unworthy now, your knowledge outright blinds me. In response to your great comment, I have installed Firefox again and I have applied arkenfox right away because why the hell not. I have also donated $5 to Mitchell Baker’s Foundation since she is so poor. I hope that I can also donate a great sum to arkenfox, to make up for the time the maintainer wasted discussing topics with me, the ignorant.
I can already feel it, my browsing experience is so much better now, absolutely nothing breaks, I get no recaptchas ever, and I can rest assured that, with this decision, I have outwitted both Google and the NSA!!! I feel so secure and private now, thank you for that massive revelation of yours. No FP script or any other form of tracking can touch me anymore! What is Tor even? They can end their project right now, for arkenfox already exists, which is giving Tor all of the necessary info and definitely not the other way around. Even the Tor devs are but fools compared to the sacred knowledge of this project’s most illuminated maintainer. All of us can only profit from talking to her, and that she has been overlooked so far is a shame.
And you are right of course, Brave Software is total scum, a sinister ad company the likes of which the world has never seen before. We knew Facebook and Google (which, gracefully, has seen the light and now funds Mozilla), but Brave is way, waaaay worse. The privacy of the browser is a joke against mighty Firefox and BAT is the worst of the worst of course. Here, again, your light shone forth to me, the ignorant, and has illuminated my darkness. Thank you a thousand times.
Shut up and take my money.
> The leaks only existed in my imagination
Noted: iron heat failed to provide proof of any leaks
Thanks Gustav, you make way more sense than that Iron Heart. Seems like Iron Heart is just a Brave shill who doesn’t know how it works
@a different anonymous
If I am a Brave shill, then I don’t know what the people writing these Firefox advertisements all the time are. If you try to be accusatory, perhaps you shouldn’t also be hypocritical about it.
gustav, brave forgot to cover randomizing in all workers, so leak is an understatement
https://github.com/brave/brave-browser/issues/18251
@Anon
“Forgot to cover”… More like, the defenses are still young, and they have to work with third party code where NOTHING is protected by default. They have to get there one by one, it takes time. The issue you’ve pointed to does not prove negligence.
That Brave is always accused of being bad, sometimes via very creative reasoning, is tiresome.
> the defenses are still young
over two years and counting
> and they have to work with third party code where NOTHING is protected by default
oh no, do they have to write their patches from scratch every release? seems like you’re admitting that brave isn’t a browser, just a fork with some dodgy shady gimmicks and that brave couldn’t engineer themselves out of a wet paper bag
stop being an apologist
@Anon
Two years is hardly anything, how long has Tor improved their defenses? Answer: For over a decade.
And yes, working with third party code where nothing is protected by default means that they have to write the defense for each value from scratch. I never said that they have to rewrite it for every single release, you absolute tard. You accuse them of incompetence without proof, it’s just trollish agitation.
> That Brave is always accused of being bad, sometimes via very creative reasoning, is tiresome.
This and other recent comments by you indicates clearly a fatique. Lack of deboonk. Why not take a break?
@Irrelevant self-importance
Why should I take a break? I am pointing out YOUR captain obvious trolling, it is you who should take a break.
where does arkenfox say it reduces uniqueness? you made that up
if anyone is wondering here is arkenfox https://github.com/arkenfox/user.js
They have also reinforced the new recent referrer policy that sends only the domain instead of the full URL for cross-origin requests, by no longer allowing sites to override it. But this reinforcement was added only in private browsing or strict tracking protection mode, not for default settings.
With Mozilla’s lack of transparency, only the future will say if it’s a transition before making it a default or if sites will still have the possibility to receive full URL referrers across domains for a long time. The actual power struggles and real motives behind those Google driven decisions (and the very fact that they are Google decisions) are also absent from their public communications, as usual.
One may also wish that all third-parties and target sites of clicks stop all receiving even the domain we’re browsing but in GoogleZilla land that would sound like something too utopian to request.
@Anonymous
Mozilla doesn’t give a shit, as with many other settings that have horrible defaults in Firefox. This is usually excused by the existence of about:config, which users can use to “fix” or “harden” Firefox (while in reality just fingerprinting themselves in the process). This is then said to prove that Firefox is pro-privacy.
That browsers like Brave or Bromite provide superior privacy by default (without the FP risk) seen as a sign of their respective users being uneducated and being unable to flip some preferences from “true” to “false” (and vice versa). The world of the FF fanboys on here in a nutshell.
Yikes, saw your comments on a different thread. Thought you were a just-critic who was enthusiastic about brave and had my respect for 300 seconds. In the end, you were a toxic brave shill all along.
> This is usually excused by the existence of about:config, which users can use to “fix” or “harden” Firefox (while in reality just fingerprinting themselves in the process).
Last time I checked, you can easily get away with this using an extension called “NoScript” which disables javascript (which is used for fingerprinting in the majority of cases).
[A source I dug up in 120 seconds : https://stackoverflow.com/questions/44996014/how-to-reduce-your-fingerprint-in-browser-for-privacy-and-for-web-scraping ]
I personally use no script and in my use case, I can usually use websites without toggling the js sources in no script. (Although the sites might not look pretty)
On rare occasions, I have to toggle one or two js sources.
On VERY VERY rare occasions, I have to boil my head to figure out which js source I have to toggle (without enabling js which is also an option in the extension menu if you are fed up with toggling multiple source)[Happened to me ~ 10 times in a period of 6 months]
Also, I am a firefox enthusiast who thinks that brave is also cool but despises toxic brave shills and english is not my native language incase you are about to point out my lack of expertise in english grammar. [Leaving this in here so that you can predict my responses in case you wish to leave any replies]
@Anonymous
You can call me a “toxic Brave shill” for pointing out that some browsers fight fingerprinting by default, thus allowing for crowd building, but it doesn’t mean that I am. If you don’t like the fact that Firefox does nothing to fight fingerprinting by default, leaving it to users to fingerprint themselves by meddling with about:config settings, complain to the Mozilla devs, not to me.
Disabling JavaScript is not the perfect fix you think it is, because JavaScript being disabled is in itself also detectable: https://old.reddit.com/r/TOR/comments/9zhiey/disabling_javascript_vs_browser_fingerprint/ea9pi5k/
I think fingerprinting defenses are implemented and used under the assumption that JavaScript remains enabled for web compatibility reasons. Not everybody can and should handle a browser with JS disabled and you have to allow some scripts at times anyway to alleviate breakage.
a different anonymous here
> You can call me a “toxic Brave shill” for pointing out that some browsers fight fingerprinting by default, thus allowing for crowd building, but it doesn’t mean that I am. If you don’t like the fact that Firefox does nothing to fight fingerprinting by default
brave doesn’t have a crowd because it randomizes. with advanced scripts it lacks the ability to create a crowd
firefox does fight fingerprinting by default. firefox blocks known fingerprinters. saying firefox does NOTHING is another of your lies
I’m going to call you an ” ignorant alternate-facts toxic Brave shill”
> Disabling JavaScript is not the perfect fix
more nonsense. disabling js removes far more entropy than it creates. try searching for some basic facts, it will astound you and open your biased eyes
@Anonymous
> brave doesn’t have a crowd because it randomizes. with advanced scripts it lacks the ability to create a crowd
Advanced scripts don’t take the randomization because they check for a broad range of items, negating the poison pill even if it can’t be normalized. Considering that Brave’s defenses are still in their infancy, and considering that I’ve never claimed that they can beat advanced scripts, I don’t even know what you want from me here. Firefox doesn’t beat advanced scripts either, neither by default nor modified.
> firefox does fight fingerprinting by default. firefox blocks known fingerprinters. saying firefox does NOTHING is another of your lies
I’ve already acknowledged the joke that is their tracking protection, which uses the weak Disconnect list, in another comment:
“FF’s tracking protection doesn’t do anything against fingerprinting aside from blocking a low number of scripts (total joke).”
It blocks a VERY low number of fingerprinting scripts by default. You can call that “doing something” as a most flimsy pretense, but we both know exactly that it is a joke, a non-starter even and is nowhere near sufficient. Even installing Privacy Badger potentially does more than this joke.
> I’m going to call you an ” ignorant alternate-facts toxic Brave shill”
You can also call me Father Christmas, it’s not like I care.
> more nonsense. disabling js removes far more entropy than it creates. try searching for some basic facts, it will astound you and open your biased eyes
Dude, nobody does this for web compat reasons but IF it is done it IS another reference point. I didn’t attempt a risk / benefit analysis here, I just pointed out that JS being off is detectable of course. Fingerprinting can be done partially at the networking level or via CSS. You are the ignorant here. Ever wondered why no browser disables JS by default, since it is apparently so easy a fix? Something, something, web compatibility.
Some users disable it, so what. It’s a non-starter for most. You know it, and I know it.
You can also use uBO and/or uMatrix instead of NoScript. Won’t be missing out on anything as those two works better and are easier to use IMHO.
uBO works best in firefox – https://github.com/gorhill/uBlock/wiki/uBlock-Origin-works-best-on-Firefox
> uBO works best in firefox
That link doesn’t say anything. It just describes extension API limitations of Chromium, which uBlock Origin has to operate under since it’s an extension. Native adblockers like the one in brave are not extensions and are not under those limitations. For example, extensions on Chromium can’t do CNAME uncloaking but Brave’s native adblocker can.
gorhill also believes that Chromium should retain the webRequest API that has been adbused all the time by malware intercepting and redirecting connections, just because his own extension also uses the API. Yeah, let various malware extensions roam free just so that uBlock Origin can continue to exist. *facepalm*
> It just describes extension API limitations of Chromium
limitations that firefox doesn’t have, hence it backs up what gorhill said, that uBlockOrigin works best in Firefox
do you really have to try and argue and bitch and whine and fucking act like a baby in every post? have you ever considered taking a break, or seeing a therapist
@gorhill has spoken
> limitations that firefox doesn’t have, hence it backs up what gorhill said, that uBlockOrigin works best in Firefox
The limitations only concern extensions. Native adblockers don’t have these limitations. I don’t care what gorhill has to say. According to him, the webRequest API which gives way too much privilege to extensions (allowing them to monitor everything basically) and is frequently used by malware should be retained, because… uBlock. Give me a break, LOL.
> have you ever considered taking a break, or seeing a therapist
Have you ever considered not being a troll?
> The limitations only concern extensions
and uBO is an extension and the limitation is not in firefox, and because of that uBO works best in Firefox
what are you trying to argue about?
have you ever considered that no one cares about your rants and constant dissing of Firefox, and just want to know that uBO WORKS BEST IN FIREFOX
@gorhill has spoken
uBlock Origin works “best” in Firefox due to an API that is to be removed from Chromium due to the high incidence of malware using it. Enjoy, until Mozilla removes it as well.
The browser having a native adblocker is much preferable.
@Anonymous: Iron Heart has been, and always be, a Brave shill. Arguing with him is like arguing with a loudspeaker.
@Unknown person
If my comments qualify for the word “shilling” (lol, in this case I just describe the necessity of browsers doing something against fingerprinting by default – which Brave, but also the Tor Browser Bundle fall under), then I don’t know how you would describe all the Firefox advertisements on this very blog, even within comment sections that are unrelated to Firefox. Your hypocrisy here is massive.
> This is usually excused by the existence of about:config
Last time I check you could just go to the privacy settings and change ETP to Strict mode. This gives you Tor Browser levels of site isolation which no other browser comes close to. Who mentioned anything about user.js
@Anonymous
FF’s tracking protection doesn’t do anything against fingerprinting aside from blocking a low number of scripts (total joke). Isolation of local data (which is not the same as site isolation, by the way) doesn’t help against tracking techniques that can be performed entirely server-side, like fingerprinting. And user.js scripts don’t fix your uniqueness, this is the biggest joke ever. If you want to fight fingerprinting you won’t get around using a browser that comes preconfigured by default (so that crowd building becomes possible), like the Tor Browser Bundle, Bromite, or Brave.
My browser is better than your.
> FF’s tracking protection doesn’t do anything against fingerprinting
no one said it does. you’re just twisting words, making shit up, conflating things and moving the goal posts
– ironheart: ranted about something about a user.js to change defaults
– reply : you could just go to settings and change ETP
And now you are downplay the network partitioning and dFPI work of mozilla, which far exceeds anything else anyone else has, except Tor Browser, which removes the ability for 3rd parties to link uuids cross-domain. What are servers going to do when the client no longer supports their tried and trusted long-time methods of linking traffic
This is tor browser level protection touching almost every aspect of the browser, even brave have acknowledged how great it is. But iron heart, oh no, not good enough because let’s add something completely outside of what it’s purview is, and bitch about it – i.e now you’re ranting about server side tracking, which no one was arguing about
> by default (so that crowd building becomes possible), like … Brave
iron heart is still totally ignorant. There is no crowd in brave, it only fools naive scripts and is years away from getting even close to protecting enough values, let alone stopping all the leaks of the current patches, after years of trying
@Anonymous
user.js changes don’t reduce your uniqueness. Reducing uniqueness is done to fight fingerprinting. Fingerprinting can be done entirely server side and usually is, therefore partitioning local data has no effect on it. I don’t know what is inconsistent about my argument.
> And now you are downplay the network partitioning and dFPI work of mozilla, which far exceeds anything else anyone else has, except Tor Browser, which removes the ability for 3rd parties to link uuids cross-domain.
Fingerprinting needs no local data, partitioned or not.
> This is tor browser level protection touching almost every aspect of the browser, even brave have acknowledged how great it is
Who gives a shit? It’s not like Firefox will be around in 5 years. You should be happy that it is acknowledged at all considering that it’s a dying project.
> But iron heart, oh no, not good enough because let’s add something completely outside of what it’s purview is, and bitch about it – i.e now you’re ranting about server side tracking, which no one was arguing about
You make it sound like setting FF’s tracking protection to “Strict” is a final fix to fingerprinting. No, it’s not.
> iron heart is still totally ignorant. There is no crowd in brave, it only fools naive scripts and is years away from getting even close to protecting enough values, let alone stopping all the leaks of the current patches, after years of trying
You tell me, hahahaha. Don’t you think I am aware of the values Brave protects or doesn’t protect. I am totally aware of it. The fact of the matter is, its protections are still young and when they do something, they have to keep web compat issues in mind. It is not because of their incompetence (alleged by you) when nothing is done, it is because the breakage it causes must be considered, since Brave aims to keep fingerprinting defenses on by default, and aims to form a crowd. Firefox will never have fingerprinting defenses on by default, they let users fingerprint themselves by modifying about:config values, a totally ridiculous concept that can and will never work. Firefox has to live with Tor’s defenses but the breakage these cause is only acceptable for Tor, not for a general use browser like Firefox. If Firefox did something by default, it would be along the lines of Brave. Deal with it.
No idea why you are hating on Brave Software, it is the best hope we have in the fight against fingerprinting, as Firefox won’t survive due to its engine dying. Firefox users promote a faulty concept of fighting fingerprinting (“modifying a few values here and there will fix it”) here, maybe you should reconsider what you are doing.
still ranting about fingerprinting. still ranting about a user.js
no one said changing defaults needs a user.js, except you. no one said changing defaults can’t impact an fingerprint. no one said ETP has anything to do with fingerprinting
by your logic all of brave’s privacy efforts mean nothing, because lets see, they didn’t protect your IP address
> You make it sound like setting FF’s tracking protection to “Strict” is a final fix to fingerprinting. No, it’s not
I never said that. If you could read, I said that ETP has nothing to do with fingerprinting
you never discuss anything in good faith, you just rant and make illogical arguments and contradict yourself
example: what does conjecture about firefox being around in the future have to do with the discussion.. more goal post shifting, shit spreading and noise
> they have to keep web compat issues in mind
you really are super ignorant, the leaks have nothing to with compat
@Anonymous
> no one said changing defaults needs a user.js, except you
LOL, OK? You realize that if you don’t apply a uniform user.js, but modify settings yourself here and there according to what you believe is best, that this makes it even worse, right? The people using these obscure user.js files are already minuscule in number and don’t fix their uniqueness, how about doing your very own setup instead? Ahahahahahaha…
> no one said changing defaults can’t impact an fingerprint
Then don’t promote bandaid fixes that do not reduce your uniqueness at all.
> no one said ETP has anything to do with fingerprinting
I merely pointed out that Firefox’s so called “enhanced” tracking protection fails to cover server-side tracking which is bound to become more prevalent as cookies die out. This is a legitimate argument despite you doing your utmost to avoid interacting with it.
> by your logic all of brave’s privacy efforts mean nothing, because lets see, they didn’t protect your IP address
…because that is not the job of the browser. That is what VPNs or Tor are for.
> I never said that. If you could read, I said that ETP has nothing to do with fingerprinting
So you are admitting that ETP only tackles tracking techniques that will go extinct anyway, OK.
> what does conjecture about firefox being around in the future have to do with the discussion.. more goal post shifting, shit spreading and noise
That has something to do with your attitude, not mine. Why are you advertising a product that will go the way of the dodo? Why bash Brave Software, who are trying to implement FP defenses in Blink, the engine that will survive? You are doing more harm than good here, advertising Firefox, an insecure, irrelevant browser that is obviously moribund.
> you really are super ignorant, the leaks have nothing to with compat
Weren’t you accusing me of not arguing in good faith? Well, what you wrote there is not a bona fide argument either. I said that they have to evaluate every single value for its web compat implications should they decide to tackle it. I never said that this had anything to do with leaks of already existing defenses. You said they don’t cover XYZ yet and the reason why something is not covered yet more often than not has something to do with web compat.
That test site is shit. This is a better AVIF test website: https://libre-software.net/avif-test/
Mozilla might want to re-consider that “tab unloading” bit ’cause the preview of opened tabs on Windows taskbar doesn’t seem to be as good as before. Have some opened tabs with spinning icons instead of image preview.
Just file a bug on bugzilla.
[NB:]***We blocked this phishing page for your protection:
https://cdn.glitch.me/ ***[Bitdefender Security!]
||me^ and it is blocked.
Probably because of recent phishing attempts w/ link connections to glitch.me sites
Same here with Avast (Web Shield).
i deleted bitdefender cause it was slowing down everything