Tox is a peer-to-peer instant messaging protocol with end-to-end encryption, voice calls, video calls and file transfers
Instant Messaging is one of the most popular forms of electronic communication. You don't have to pay extra fees (not counting data charges) for chatting with family members, friends or colleagues regardless of their location.
But, there has been a rising concern about the privacy of such services. State-sponsored attacks and mass surveillance are some major examples.
Tox is a peer-to-peer instant messaging protocol with end-to-end encryption for Windows, Linux, macOS, Android and iOS.
What is a decentralized messenger?
Let me explain what a centralized messaging service is. Any instant messaging protocol that uses a cloud-based connection, aka a server, is a centralized service. Examples for this would be Skype, Hangouts, Facebook Messenger, Viber or Telegram. When you send a message through a centralized service, it is transmitted (passes through) a server, where it may or may not be stored before it is delivered to the recipient. This could potentially result in data being stolen, or the user being spied on.
A decentralized messenger is one that cuts out the middleman, i.e., there is no server in between you and your contact. The message that you send is delivered directly to the recipient, as in Peer-to-Peer (P2P). Combined with end-to-end encryption; this is better for privacy when compared to a centralized service.
Tox encryption and Security
Tox uses NaCl encryption for cryptography and the developers have labelled this as experimental. The encryption happens on a per-message basis. Also, worth mentioning is that messages are metadata free, which is important because metadata is used as a way to trace users. Your data is only stored on your device.
Is Tox secure?
The main concern with Tox is that despite being open source, its encryption protocol has not been audited. The developers don't hide this though and have clearly mentioned this on the official website, which is a good sign. Does Tox expose the IP address? Any P2P service will, that's how they work. Tox does by using your IP and your contact's to help you communicate with one another directly. You could try using it with Tor or a VPN to prevent this.
Note: Your IP address is only visible to people whom you add as contacts, other users can't see it. I strongly advise you to read the service's documentation before using it.
Tox clients
There are many clients available for Tox. The most popular desktop applications are uTox and qTox. The official mobile apps while outdated still work. I also tested Tok Lite (doesn't support calls), which is a fork of the official Antox Android app.
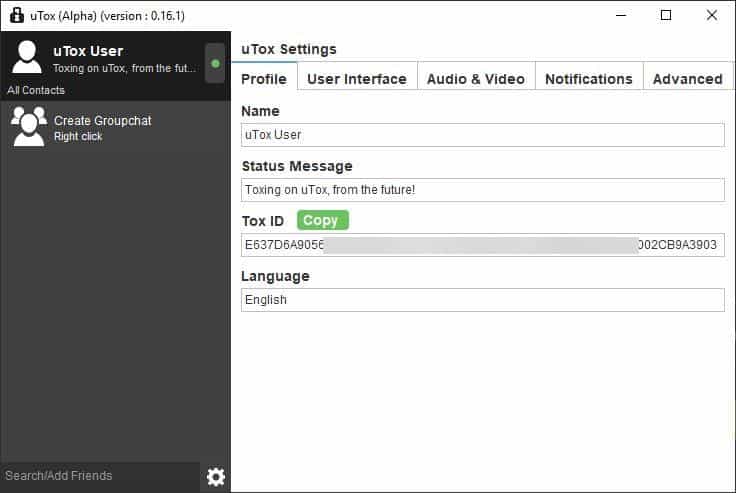
Signing up for Tox
There is no registration required as there is no account. When you install a Tox client and run it, you will see that it has a Tox ID (long alphanumerical ID) that's ready to use. You can change your name to whatever you want to. One of the biggest advantages of Tox is that you don't need to provide a phone number or an email address.
I installed uTox on my computer (set it up) and then installed qTox; it automatically picked up my Tox profile. That's because Tox saves a profile to the \AppData\Roaming\Tox folder. You will see a .Tox file here, this is your Tox profile. You can use it to export your profile to other devices, for e.g. if you want to import it to the mobile app.
Adding Contacts
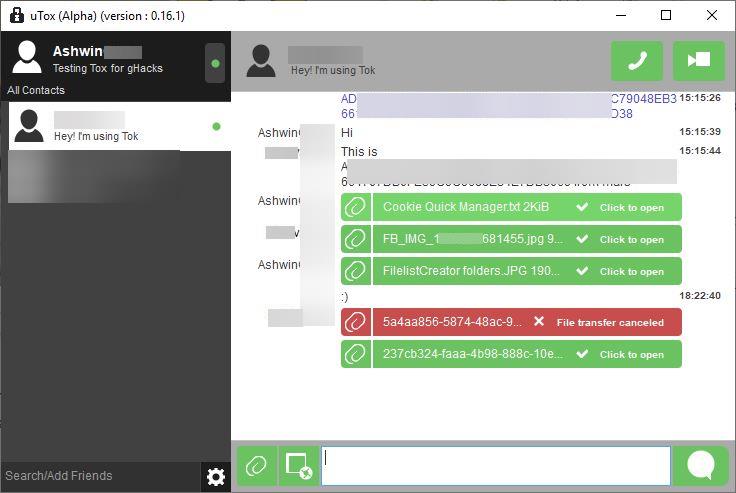
There are a couple of ways to do this. You can send your Tox ID to someone to invite them to chat. They have to accept your request and optionally add you as a contact. Or you can send your QR code that they can scan to accept your invite (only on mobile apps). Some clients have additional functionality such as an option to send voice messages, capture a screenshot of a selected region on the screen and send it to the contact.
Messages, Voice Calls and Video Calls
Tox allows you to send instant messages to your contacts, but can also be used to make audio calls, and video calls. All communication made through Tox is end-to-end encrypted. The Mobile clients display notifications and function just like most IM apps.

File Transfers
You can send files to your contact and depending on the client that you're using, you'll be able to choose whether to accept the incoming transfer or reject it. This option can also be useful to save data, if you're on a mobile network.
Connectivity
Since everything is peer-to-peer based, the connection speed depends on the network quality of you and your contact. It worked flawlessly on local networks, mobile networks, and long-distance peer-to-peer communication as well. I used IPv6, but it also works with IPv4 networks.
The main issue with the service is probably getting people to use it.
Before I wrote this post, I was using Jami (formerly Ring) for a few days. It had way too many connectivity issues (couldn't deliver messages, unjoinable peer, etc), that I had to ditch it. Maybe you will have better luck with it. Wire used to be good, until it was acquired quietly (went from a Luxembourg based ownership to a US one). It has been criticized by Edward Snowden. Riot is another option, though it uses Matrix (which has been hacked twice iirc). Signal still seems to be the best secure messaging app, but it requires a phone number. Android users can try Briar, which uses Tor (for internet) or Bluetooth/Wi-Fi.
























Thanks for this article.
I recently installed the latest qTox at a client site to see how well it works on internal LAN and over Internet for their Manager at home. Still playing around…
However, one issue — unless I’m totally blind! HOW the heck do you DELETE a message or multiple messages?? It’s quite logical for a user to want to delete a message in the Outbox queue that hasn’t yet been sent since the user is offline.
If this program can’t do this, I haven’t a clue why TF its sooo popular.
Frankly speaking there are even more good messengers, maybe not so worldwide known and popular, but very secure. I will advice to choose Utopia p2p https://utopia-ecosystem.com/. For me very important point is when it doesn’t require my phone number, email or any other personal info.
Is this just a utopian sales person? We do get that a lot, even messaged from builders themselves promoting their crap.
Thank you for your information, very helpful. I’m looking for a free independent alternative to whatsapp. I am on Signal, but think they are going to get squeezed out too, they are not independent. When using TOX, must you use VPN for it to be safe?
Definitely interesting, months ago I tried out Tox once again. It’s basic features work in practice, though there is sadly a major drawback which is also its strength: Peer to peer connections. The more contacts you have, the more power and connections are needed. It doesn’t matter much on a computer, but it absolutely does on phones. And since these days most Internet users are mobile, Tox would be impractical for mobile use. Especially since Google begun enforcing aggressive battery savings on Android since version 6. Where the only reliable way to work around out is to use a push notification via Google Play Services.
Wasn’t signal in the Vault7 dump among a list of compromised messaging apps?
Beyond chatting and such, I imagine TOX may become popular for sharing pirated media, via their Group feature.
Furthermore, if you trust all the users in your TOX group, then you potentially wouldn’t need a VPN for such, that is if your ISP doesn’t thwart such P2P traffic, and you trust TOX’s security.
Yet being that the encryption is still “experimental”, I guess many users as me will wait and see how TOX evolves.
Also, my VPN bans P2P traffic, thus TOX is not much of an option for me right now.
But thanks for this tip Ashwin. I’ve bookmarked TOX under “promising freeware”.
When I ran qTox for the first time, having TCPView turned on, I saw a connection, among three or four others, to “unassigned.quadranet.com” . I wonder what this domain – organization is about. A quick search shows it is based in the US.
Good article.
Also in February was released new Messenger – Session. Please review it if possible.
Based on Signal protocol, have E2EE, not need to have an e-mail or telephone number.
WASTE:
https://en.wikipedia.org/wiki/WASTE
?
Wow, found that it is still live forks like “BlackBelt WASTE”.
Interesting.
BlackBelt WASTE: Supports Tor and i2p out of the box.
As IT admin for a 300-odd seat business its really difficult finding a good, usable IM software that’s secure from snooping US tech companies, governments, and the users want to use it. I like these business-centric reviews. More please.
Tox is great but its best feature is also its worst feature.
I used to use Wire a lot but the company moved from Switzerland to the USA at the end of last year and forgot to mention it to the customers. Very annoying as Wire is the best I’ve found so far.
Nice Ashwin, the first software in ages you’ve reviewed that has potential.
However…
How can this be given a 5 star rating when the software is so immature?
Even the developers say you could run into bugs – that’s not good for a supposedly secure messaging system.
It’s main selling point is secure communication, but with unverified protocols etc it really shouldn’t be recommanded for any users than those that wish to test and aid development.
The 5 star rating needs revision.
Nice to see Tox getting some news, it’s been a good few years, I was worried it was all but abandoned. Of antox, utox, poison etc, qtox was the best client for general desktop use last I used it.
It still has untapped potential.
Yeah, I have been checking some messaging applications and I wanted to try this one but how?
The problem is not about if it works or not in my case, but how it’s not a good ecosystem. iOS app ‘antidote’ is dead and there is no way to use it on iOS anymore, so what is the point of using this type of application if you can’t use it on a popular mobile platform like iOS? Android app is pretty much old and not updated much anymore either, and the others android apps are not much better either, even if they are updated recently they miss essential features like video calls and stuff like that.
That is the main problem about this Tox ecosystem, it is open source but with really limited userbase so and if someone doesn’t work on it, it dies like happened with iOS app.
After Tox, the other interesting app I found was Jami, still havent had time to tried it, but seems like it could be better than tox. And supposedly just like Tox, your information, not even 1 byte is store in a server, like happens with Signal or Riot, where you need to provide your phone number or have an account and username and all that and then Riot/Matrix accounts can’t even be deleted, they can only be ‘disabled’, so I find that pretty bad.
Is tok a company? How can I trust it over sthg like Antox? I see using the Tok app that there is sthg called Tok coins, what is it? Tok seems to be much more than a simple Tox client?
Thank you for more info.
It rhymes on some malware released by saudis. The website looks sh1t, no useful information or source.
I would not touch that software.
Yes, that’s what I thought. But why do you involve saudis? :-)
Is it possible to use Tok Lite with an already existent tox profile. I tried to add my tox profile in Tok but couldn’t figure out how…
Also what is the difference between the two versions of Tok, the full and the lite?
I set up my tox profile a few years ago but never had the chance to use it because couldn’t find anybody using tox. So if sbdy wants to try with me here is my tox ID:
51C0245B40EFC536D8EFAE8F21D8829C9FF5125EC5B772EB83BCDEE7B9AA387AE8818196AA0D
QR code containing my tox ID: https://i.imgur.com/3KMgQIh.png
You can use whatever client you wish on the TOX network from memory. I wouldnt advertise your TOX ID as you may get undesirables adding you.
As the article mentioned using Jami – I used to use it – and really hung in with it but after a few months but got nothing but frustration. TOX was great except mobile phone clients used to go offline when they were put to the background, only coming back online when opening the client. An additional client TOX notify seems to have fixed the problem so constantly now showing as online and works fantastic. Still early testing days yet but looking promising – just hope it doesnt suck the battery dry.
Threema is popular in Europe (Germany, Austria, Switzerland). Anynymous sign up. Very stable – even behing the GFC.
Does tox now support asynchronous (fully implemented offline) messaging? If not then it’s still a waste of time IMO.
It’s called email with pgp.
JFK!
I never thought that i will see anything other than facebook’s cr@p on a popular site!
You should also mention Ricochet (Text only over Tor) or some XMPP client/server too (they work over Tor too).
I don’t like Signal because its file size limitation, their desktop client that will never implement Audio/Video Call and it is not federated so if i want to send something BIG (or call someone) i use a Jabber client (files can be big as the free Hard Drive space of the server if configured) or as you mentioned Tox.
Ricochet is outdated, so not secure at all. XMPP is good and secure with OMEMO.
What do you mean by outdated?
I built it with latest Tor 0.4.2.7 that was built with latest OpenSSL 1.1.1d.
It will never be outdated.
Yeah, you can expect anyone to fully support, and promote what they built, to the highest degree, though it may be total crap, with the builder knowing. No different from a China AliExpress seller sending me Russian phones in America, with China Trade Assurance supporting them, no matter how much proof I sent showing I literally ask for Global phones. It’s because they’re Chinese, and support each other no matter how wrong they know they are.
“It will never be outdated.”
The latest version is 1.1.4 (November 5, 2016), so, it is outdated. Am I wrong?
I’d like to see some more reviews about services like this. I’ve always been curious about Riot / Matrix chat, but don’t know enough about them to know if they’re good to use or not.
Definitely worth to try. Available on desktop and cell phones too. Every feature did work as described not like in Jami or Tox.
For a start just register and test it then later try to setup an own server to see how it works.Very well documented and explained.
A Matrix server isn’t hard to setup you grab a Let’s Encrypt cert to it, set a user and you are basically ready. It also supports TURN (REST) so works with stun and turn servers (coturn and such) just like Jami or a few XMPP client.