How to remove DarkMatter Certificates from Firefox
Cyber-security company DarkMatter, based in the United Arab Emirates, applied to become a top-level certificate authority in Mozilla's root certificate program recently.
Certificates are a cornerstone of today's Internet; HTTPS ensures that communication is encrypted. A company in control of a root CA could potentially decrypt traffic that it has access to.
A Reuter's article links DarkMatter to the United Arab Emirates government and surveillance operations. One such operation, called Karma, saw the team hack iPhones of "hundreds of activists, political leaders, and suspected terrorists" according to Reuters.
The EFF notes that DarkMatter's "business objectives directly depend on intercepting end-user traffic on behalf of snooping governments".
DarkMatter has an intermediary certificate already issued by QuoVadis. QuoVadis is owned by DigiCert which means that there is some oversight in place currently but that it would be lost if DarkMatter would get the root certificate.
So, the chain is DigiCert > QuoVadis > DarkMatter currently. It is possible to remove root certificates in Firefox. Note that doing so would impact any certificate issues by QuoVadis. In other words, any site you visit that uses such a certificate won't load anymore.
Note: As some readers have pointed out, certificates get restored with every update. You may also need to clear a site's cache if you run into loading issues. See this guide.
Removing the certificates

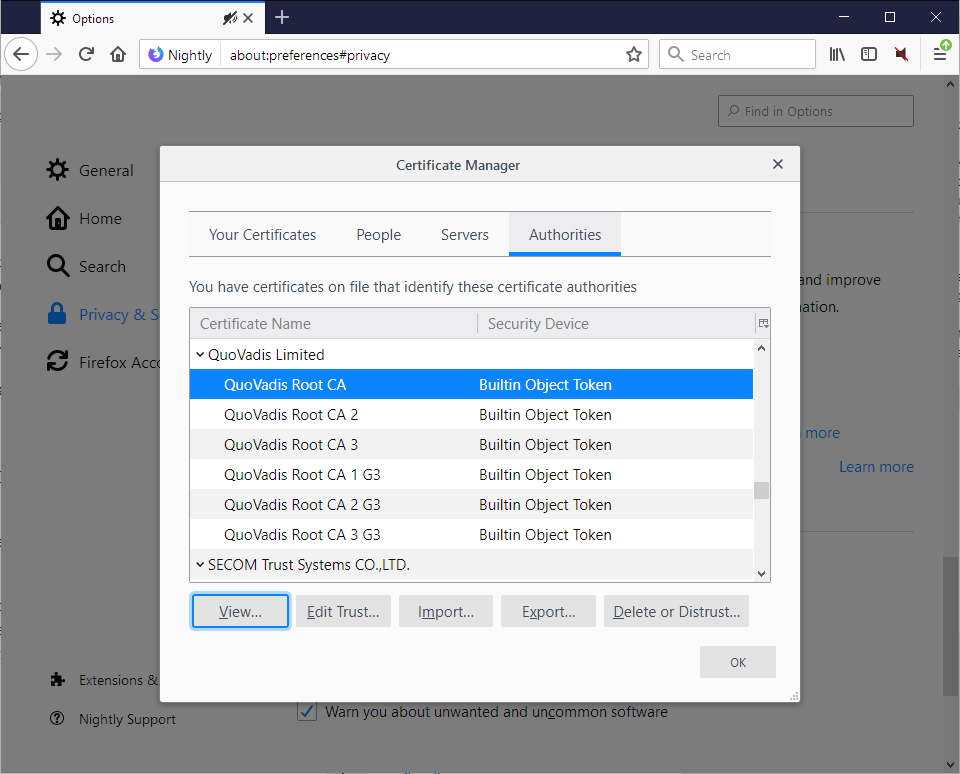
Here is how you can remove certificates from Firefox:
- Load about:preferences#privacy in the Firefox address bar to open the Privacy & Security settings.
- Scroll down to the Certificates section on the page.
- Click on the View Certificates button.
- Firefox lists all authorities in an overlay. Scroll down until you find the QuoVadis Limited listing (or any other listing you want to remove).
- Select a certificate, it does not matter which. Tip: Hold down Shift to select multiple certificates.
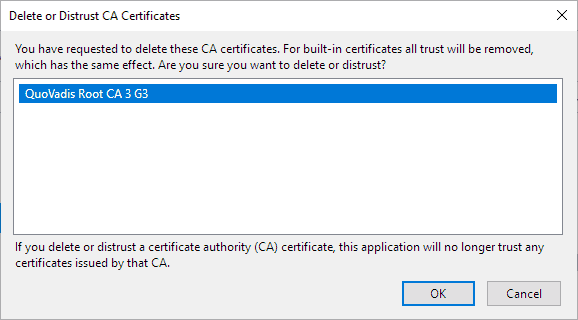
- Click on "delete or distrust".
- Select ok to remove the certificate from Firefox.
- Repeat steps 5-7 for all other certificates that you want to remove. until the QuoVadis Limited listing is no longer there.
You can follow the discussion and integration of the root certificate on Mozilla's Bugzilla website and the Firefox Dev Security Policy group on Google Groups.






















Looks like the problems many users experienced with Quovadis is about to erupt again since according to bleepingcomputer.com Mozilla has decided to blacklist DarkMatter as a root CA together with the Quovadis intermediary certs used by them: https://www.bleepingcomputer.com/news/security/mozilla-blocks-darkmatter-from-becoming-a-trusted-ca-in-firefox/
Is that going to affect sites like PostNL.nl and Protonmail I wonder?
I removed Quo Vadis on FF and rename SiteSecurityServiceState, so that it creates a new file.
Despite all these changes, Quo Vadis certificates comes back. What’s wrong ? How to fix this ?
Martin,
Thank you for what is an admirable yet uncommon attitude of service to others without agenda.
I have ceased business with PayPal over philosophical divergences. Upon reaching Patreon’s website I am presented with more “must trust” JavaScript than I can shake a stick at.
I have decades of painfully verified cynicism since my first & only check from the 5,000 lb. horse’s ass more commonly known as (censored) for contract programming bounced and is still in motion ~31 years later. Try as I might, I cannot convince myself all of that inquisitiveness is needed to forward you a donation less “processing fee”.
All of that being said, if you are comfortable that using Patreon is reasonably safe from malware, personal info theft/exploitation and other nefarious acts, i will cheerfully accept responsibility for my own well reasoned decision to proceed. In other words; my decisions that beget gain aren’t shared with you and those that beget pain aren’t shared with you.
Sorry for the verbosity. Engineering forensics taught one immutable lesson: the one detail communicated in a fashion as to leave room for interpretation is the one that will line up all other holes in the lurking hunk of Swiss cheese.
Best Regards,
fop&vaaty
Dudes, I’m setting up my android phone and -alas- the certificates in that google os are too many, TOO MANY.
Hmmm… have just come across a problem after having configured distrust in Quovadis. I’m expecting a parcel delivery for which I’ve been supplied with a tracking code. However, when trying to use it distrust in Quovadis means the tracking site can’t be accessed: http://imgbox.com/cAbioqdE
I thought I might be able to add an exception, but that’s not possible either it would appear: http://imgbox.com/bGUhOCTE
Fortunately IE11 still works so I’ll have to use that in future I guess. In that respect I’m loathe to reinstate the default in Waterfox by re-importing the QV certificates.
On this article I found this:
“A company in control of a root CA could potentially decrypt traffic that it has access to.”
CA (in this case DarkMatter) can not encrypt the traffic. But DarkMatter can mark trusted the malicious servers(web sites).
Am I right?
Oh yes I see, deleting them disables the trust of the certs even when they reappear. Nothing to worry about.
I tried this but they keep on reappearing in Firefox and Thunderbird; upon closing and reloading the browser they never go away. Whats up with that Ghacks?
Thanks Ghacks! I found a pair of these in my Windows 10 certificate authority list, and disabled them there as well!
UNtrusting them is the CORRECT WAY to do it. You need to leave them listed and use the “edit trust” button for each. Remove the checkmarks. That’s it. They are as good as gone as they are no longer trusted and you will get a popup from Fx if you try to visit a site that uses one of these certs. You can then simply not visit that site or you can make an exception to trust the cert for that site. However, if the site in question uses HSTS then Fx will not allow you to make an exception.
Years ago (beginning on Dec 24 2008) this was discussed extensively in mozilla.dev.tech.crypto newsgroup when Eddy Nigg (Startcom) bought a cert for mozilla.com from a Comodo reseller. Some of the Mozilla devs even wrote blogs about it and said the above is the correct way to disable a cert.
So, they keep reappearing. Mine too.
When your looking at them on the list, select one, then click the “edit” button.
After deleteding them and they appear the next time you open FF, both boxes are unchecked, aka untrusted.
I took a look at them in TOR because I hadn’t touched them there yet. All them little boxes (almost all) where checked.
So, you can’t get rid of them, they are “built in” you can only untrust it seems. For whatever good that does…
This article is spreading false info about this and should be removed. Total fail internet journalism.
The DarkMatter CAs were previously hosted and operated by QuoVadis, and included in the QuoVadis WebTrust audits through 2017. In November 2017, the CAs were transitioned to DarkMatter’s own control following disclosure to browser root programs. The CAs have been continuously audited per Mozilla requirements. The migration was audited by DarkMatter’s auditors KPMG, and QuoVadis auditors EY were also present for the Bermuda aspects of the migration. DarkMatter had a point-in-time and an initial period-of-time WebTrust in place for their environment, and the CAs are now in scope for DarkMatter’s ongoing WebTrust audits. **DarkMatter have been logging all SSL issuance to CT since the transfer.**
How come that someone’s able to delete them and others not?
I’ve followed your steps, but as soon as I open FF again, or view certificates after deletion, they are still there, not even unthrusted.
I’m using FF Quantum v.65.0.1 x64, my SiteSecurityServiceState.txt are emty and read only.
I have deleted two QuoVadis thrusted certificates from certmgr though.
They are in Thunderbird as well.
Martin, you should watermark your images and screen caps. Too many sites like techadminlab stealing your work. Would make it more obvious where the source material is from.
Tried to remove offending certificates : broke too many sites to list.
Makes me wonder what the point of both this certificate mess and this article are. The world wide web as it was intended has been broken by infantile greed and public sleepiness. That any form of authority should be given to those issuing so called certificates is just another fool’s game and we are the fools for playing it.
Give me back my pre-palladium internet please.
Name two other sites this breaks other then Proton Mail.
I received a report of another site not working after deleting/distrusting the certs: Synchrony Bank. After following Martin’s steps above to rename cert9.db and restore the certs the user said he could access the site again.
Ah yes, the other site mentioned above besides Sparda-Bank West is QuoVadisGlobal.
I followed the directions Martin gave above to restore certs so I can’t do any more testing.
One was already mentioned above: Sparda-Bank West
Chromium and Chromium based browsers use the operating system’s certificate store. On Windows you’d have to distrust this certificate from Windows’ own certificate manager. It should affect IE, and Edge, as well.
ADD: I know, by default, today’s modern devices trust an unreasonable amount of certiticate authorities. I tried looking online for an article or something about which auhorities I can safely distrust but did not find anything, I guess it would be fairly difficult to write such an article, and it might have different impacts depending on one’s region. Still, would like such an article. I personally don’t mind messing around with the cert. store, I do my backups well and regularily, I can always rollback.
Statement from Proton Mail (of course I had to read it in another browser):
https://protonmail.com/blog/dark-matter-quo-vadis/
Finally some clarity in a sea of mischief.
+1
I removed the Quo Vadis Certificates and now i can’t enter the “Sparda-Bank West” website. Not a good idea removing certificates without knowing if you need them.
Malte, close Firefox, open the Firefox profile folder, remove the cert file there, and restart Firefox. The cert file is re-created on start.
Here is a detailed article on that: https://support.mozilla.org/en-US/questions/1230877
Quo Vadis translates to “Where are you going” in latin. Now THAT is an amazing name choice for a security company that has been accused of spying on and outing dissidents and journalists.
For Proton Mail (a “Secure” and “private” email service) to be associated with Quo Vadis is just icing on the cake.
Proton Mail had better be scrambling ATM. If they say nothing I hope ppl flee like rats off a ship.
The EFF article said: “DarkMatter was already given an ‘intermediate’ certificate by another company, called QuoVadis, now owned by DigiCert.”
This doesn’t make every certificate from QuoVadis unsafe.
If you read the Firefox bug report, DarkMatter is not yet approved by Firefox, and I doubt it ever will be based on latest reader comments.
>DarkMatter is not yet approved by Firefox
It doesn’t matter if approved or not, some ghacks folks like to hear fleas cough and the grass grow.
>This doesn’t make every certificate from QuoVadis unsafe.
This whole debate is a illustrious example of hysterical and blind overzealousness. It may be a lesson to some readers not to uncritically follow every ghacks recommendation next time – especially for the Proton users.
I can’t do homebanking now because i didn’t know my bank uses QuoVadis Certificates. I have to re-enable them. This article was a fail. Many legitimate sites rely on these certificates.
Why are you guys saying that it “A company in control of a root CA could potentially decrypt traffic that it has access to?” It is not reasonable to make this assumption. To decrypt HTTPS traffic, the CA needs the private key of it’s client key pair, but the it does not have access to the private key for the certificates they issue. All they do is sign their client’s public key with their own private key (by so assuring that the signed public key indeed belongs to the subject of the certificate – usually a website).
If a CA could decrypt their client’s traffic, the CA of your bank’s website would be able to watch or even transfer money from your bank account. Would that be reasonable?
Is there something I’m missing here?
I cannot get rid of these! They respawn instantly after closing the View Certificates window. Multiple attempts with the same result. Tried deleting the cert9.db, restarting FF and deleting again but they’re still there, laughing at me probably.
Anyone know why? I just want them go away and stop mocking me.
Wondering how many readers actually read the Reuter’s article. Here’s a delicious quote from a Lead Analyst: “Stroud said it all happened so quickly she was unable to recall the names of the three U.S. journalists or other Americans she came across in the files.”
Anyone who has been involved with surveilling and is as skilled as Stroud makes herself out to be doesn’t forget names; anyone involved with “hacking” doesn’t forget. Period.
The article smells of a rotting attempt [the story goes back by nearly a decade] by Reuter’s to twist a legitimate counter-terroism program led by US cyber-spy mercenaries hired by the UAE into a program that targets the NSA and all Americans . . . but no one can “recall the names of the three” U.S. journalists or the other three somebody’s in the files.
Karma on the iPhone sounds intriguing.
Rather absurd . . . roll my eyes.
So if they are doing something bad wouldn’t Mozilla just kill it off in Firefox themselves anyway? They are all about user privacy and security. I don’t think having users mess with their browser like this is good. After reading the comments it seems manually messing with it breaks a lot of things. Can’t we just let Mozilla do it?
Answering my own question: How to remove these certificates from windows.
1) Search > MMC > Right click and Run as Admin> File > add/remove snap-in > select certificates > click add > Select ‘Computer account’ > Click Next > Select local computer > Click Finish > Click OK
2) Expand Certificates, expand Trusted Root Certification Authorities, Select ‘Certificates’
3) Right click the certificate you’d like to remove and click delete
4) When you exit MMC don’t save the settings.
How do I remove it in here?
Windows > Control Panel (not settings) > Internet Options > Content > Certificates > Trusted Root Certification Authorities
On Linux one can distrust QuoVadis system-wide, which should work for all web browsers and any other internet facing application that using ca-certificates (which is most if not all).
On Debian based distro’s this needs editing /etc/ca-certificates.conf and prepending QuoVadis lines with a “!”.
Other distro’s use /etc/ca-certificates/trust-source/blacklist. Each certificate placed in there will be treated as distrusted for all purposes.
Both methods guarantee these CA’s stay distrusted after upgrades of ca-certificates.
@glitsj16: many thanks for that. I have 2 questions:
1. Prepending the ! presumably means leaving a gap between it and the next word on each line?
2. Usually when a line is “commented out” a # is used. Not in this case?
If my questions appear basic, if not stupid, please forgive me, I am a Linux noob.
Forgot to mention that after making those edits in /etc/ca-certificates.conf you’ll need to update the certs store via
$ sudo update-ca-certificates –fresh
This is all documented in ‘man update-ca-certificates’.
Likewise, on distro’s using the blacklist dir, one needs to update the list once by running
$ sudo update-ca-trust
@glitsj16: thanks, done.
Lines that begin with “#” are comment lines and thus ignored. Lines that begin with “!” are deselected.
@99: thanks.
No gap. This is explained inside /etc/ca-certificates.conf at the very beginning:
# line begins with # is comment.
# line begins with ! is certificate filename to be deselected.
So use it like this:
!mozilla/QuoVadis_Root_CA.crt
…
No need to apologize, this is indeed one of those exceptions.
@glitsj16: many thanks !!!
Did Hong Kong Post as well, as suggested by someone else above.
https://web.archive.org/web/20190224173955/https://www.quovadisglobal.com/QVRepository/Compatibility.aspx
Yup, it all over folks
It is a wrap
yeah james, in the end, i’m happy about this – for the first time in a long time. most of the people deserve their restrictions. what a yammering when their supposedly safe page is no longer displayed *lol*. who is willing to make sacrifices? because without sacrifice, no freedom. stallman’s words. he may be a paradox and control freak, but he is still a visionary. good thing, this bad thing. more please. this is not enough.
It is the US foreign strategy of nations and governments white listing them or not. The whole certificate system is a hirarchy in the hands of the US seeing that most people on this planet use US controlled key technology like algorithms, key industries like CPU development and most the operating systems and hence all programs based on that and all this protected by legal systems as well… so it wont be easy to escape and it wont be easy to circumvent.
Chrome has QuoVadis under Trusted Root Certifications Authorities that can’t be removed.
I suppose that Windows 10… has the certificate as trusted, too.
At least untrusting a certificate on a mobile device is easy
Anyone know (any)thing about trusted certificate authority root programs?
QuoVadis shows up in Microsoft Operating Systems
http://aka.ms/trustcertpartners
Google Chrome uses the OS for certificates
do other Chromium browsers do the same?
I guess for Edge and Internet Explorer a user could revoke certificates?
> “I guess for Edge and Internet Explorer a user could revoke certificates?”
That’s what I did, I even removed them (mistake). As I mentioned far above they can be downloaded from https://www.quovadisglobal.com/QVRepository/DownloadRootsAndCRL.aspx which I did in case of : all 7 available for Firefox can be downloaded from there then re-installed for Windows… but you’ll need a browser handling the Quovadis certs because https://www.quovadisglobal.com requires … Quovadis certs!
DarkMatter: the network is bigger than meets the eye in the UAE – here is an interesting anlysis that puts it in context https://www.moonofalabama.org/2019/01/when-former-spies-run-wild-bad-things-happen.html
Deleted QV certificates then deleted SiteSecurityServiceState in profile with FF closed. Restarted and QV certificates were restored but FF is now much faster and more responsive. I guess from restore of SiteSecurityServiceState file but why? Is there a limit to the number of ways browsers can defeat themselves?
Has QuoVadis been accepted as a certificate for long in Firefox?
https://ccadb-public.secure.force.com/mozilla/CACertificatesInFirefoxReport
By the way, the Reuters article which you linked to Martin is a fascinating tale. Lori Stroud who, having worked for the NSA, but who was villified for persuading them to hire Edward Snowdon subsequently relocated to the UAE and proceeded to hack anyone that country’s intelligence services instructed her to.
The woman has no morals it seems and only became uncomfortable when she discovered that US citizens were also targets. It was OK to hack journalists, peace activists and similar individuals from other countries; just not Americans.
@TelV that former NSA employee, Lori Stroud, did mention that she left her job for the UAE when she found out the program would concern spying U.S. citizens. True or not, no idea, but she may have believed that only the Mid-East would be concerned.
EDIT, I read your comment too quickly, you do mention what I added…
“Interestingly”, in Opera Quo Vadis is in the list of Trusted Root Authorities, and the “remove” button is greyed out. Using the “Delete” button on the keyboard results in a “you have no authority to delete this entry”.
i really have enough. but a good and important article.
and yesterday also a little quarrel with stubborn fedora – silverblue developers/users who still rely on mozilla/firefox as a standard – without any criticism. internally they build a lot of brand new really amazing things (ostree et cetera). a near perfect, stable, non-overleaded, freedom respecting (freedom without detours) linux-os like no other.
but everything that comes from “outside” (like a like a verifiable “ungoogled” brave-browser) leads to one thing among most linux developers/users: fear/angst. we already had that “angst” with systemd.
+ a built-in vaapi – support in the in-house fedora chromium fork, but the idea of freeing chromium from google – like brave – seems to be be ignored. whenever you think it doesn’t get any worse, it gets worse.
not to speak of the overleaded spy-os ubuntu and their malicious “snapstore” (in cooperation with: amazon, spotify, microsoft and yes .. not better anymore .. mozilla).
so, what’s wrong. what. i know it. people. like always. and as mentioned in the last 2 posts. this will be the last time.
Sorry about this tiny question, but why Firefox includes it by default then? 😑
> “[…]why Firefox includes it by default then?””
Because the Web moves faster than time. This DarkMatter/Quovadis certificates issue is waking up only now. And in fact the possible issue is still under investigation even if EFF and others declare in a no-doubt tone that Quovadis certificates are unhealthy.
I’ve finally removed them (again) from FF and IE. But if I needed a site which uses Quovadis certificates such as Protonmail I certainly would think once again.
.. well, they fight for your privacy *lol*.
https://twitter.com/mozilla/status/1098959902268182528
CTRL + mouse click, select all certs and delete.
can this be done in Google Chrome?
Chrome uses MS’s cert mgr, you have to do it via the OS.
PS: I prefer Firefox’s method, there are allot of benefits to the way mozilla does it. For instance, it used to be that curl’s ssl cert list was derived from Firefox’s certs (not sure if that is the case anymore). Stand alone certs also abstract your important stuff like security away from MS – which, given what this article is about, is currently hard to see anymore.
Just a heads up, you can make this process much easier by doing the following:
1) While inside the certificates window, press ‘Q’ to quickly navigate to QuoVadis
2) Click on the first listing, and while holding shift, click on the last listing
3) Press the Delete key on the keyboard, you will get a popup warning that you are removing the certificates, simply press OK and you are done!
Great article again Martin. More and more it seems that everybody starting to need eyes not only in the front but also in the back of his head. Just like old Jonesey!
https://www.sciencedaily.com/releases/2018/05/180510115056.htm
How to reinstall certificates deleted as this article suggested:
C:\Users\USERNAME\AppData\Roaming\Mozilla\Firefox\Profiles\YOURPROFILE
Delete cert9.db and cert8.db to restore all builtin certificate.
Done.
I’ve reinstalled QuoVadis certificates as well (cert9.db deletion, caches cleaned, FF restart) after checking myself above comment stating that ProtonMail was inaccessible.
Maybe a word of caution reminding that the scheme at this time is investigation rather than conclusion could have accompanied this article. Martin is always very precise; maybe the idea was that it’s always possible to revert easily edited/removed certificates within Firefox (deleting cert8.db and/or cert9.db files).
My opinion at this time from what I’ve read a bit everywhere is that it’s too early to delete QuoVadis certificates.
@Tom Hawack: the issue has evolved into one of the user having the choice to delete or not to delete (sorry for the pun).
With Quo Vadis it appears that choice has been taken away, or, to put it more precisely, was never there in the 1st place. And that is not acceptable.
@Klaas Vaak, I’d like to be sure. Mozilla devs are debating about it, nothing s decided. Meanwhile Protonmail is inaccessible (its certificates are QuoVadis), and Protonmail focuses on security.
You know how it is nowadays : any discrediting information meets great success within a tornado of hatred. That means I won’t follow systematically but rather wait to know what Mozilla’s position is. Hey! : Protonmail and others cannot ce accessed!
I found “QuoVadis” in my Vivaldi too. Not possible to delete only disable.
Twitter doesn’t work after this. Total fail article, this will destroy your browsers completely.
You may need to clear the cache after this operation, see https://www.thesslstore.com/blog/clear-hsts-settings-chrome-firefox/
You don’t need to repeat every single certificate, you can just click Shift and select all of the QuoVadis certificates then distrust them all at one.
ProtonMail dead after doing this.
“For HTTPS, each website has a SSL certificate that is verified by a trusted certificate authority. The certificate authority that vouches for ProtonMail is QuoVadis Trustlink Schweiz AG. A modern browser should automatically check the validity of the certificate of a HTTPS protected website and alert you if it detects something untrustworthy. For the uber security conscious users who want to manually check, the fingerprints of our certificate are:”
You can use this url
https://dev.protonmail.com/login
You could use ProtonMail’s onion address instead (https://protonirockerxow.onion/), which still works as that one uses Proton Technologies AG Verified by: DigiCert Inc
quote: “quovadis is owned by digicert”. consequence?
@ Artim,
> “ProtonMail dead after doing this.”
Indeed. Caches cleaned, Firefox resarted, Protonmail inaccessible .
On one hand one of the most secure sites I know : protonmail,
On the other a recommendation detailed by Reuters, confirmed by EFF, to remove Darkmatter (QuoVadis) certificates.
I had proceeded this morning to QuoVadis certificates removal in Firefox as well as in IE.
I have a doubt. Until Mozilla’s decision, I’m …
reinstalling QuoVadis certificates in Firefox by deleting the cert9.db file in my FF profile;
reinstalling QuoVadis certificates in Windows 7 IE :
Control Panel / Internet Options / Content / Certificats / Import
Imported same QuoVadis as those presently in Firefox by downloading them from:
https://www.quovadisglobal.com/QVRepository/DownloadRootsAndCRL.aspx
Wait and see.
Interesting. Did you try clearing the cache as Martin suggested?
That won’t work, protonmail.com uses a certificate issued by quovaldis: https://urlscan.io/result/f853f7a8-ffd9-4df0-987d-1e49608f548d (click Certificates)
Follow these instructions to restore the certificates: https://support.mozilla.org/en-US/kb/what-does-your-connection-is-not-secure-mean#w_corrupted-certificate-store
Wouldn’t Firefox restore them after next update?
Yes, they’re present in Waterfox: http://imgbox.com/rRq6lKw0
I shall go do some digital spring cleaning now.
DarkMatter seems an odd name to use though. I immediately thought of the Dark Web when I started to read the article and considering its association with hacking and fraud, it seemed a bit odd at first that something like that would appear on Ghacks.
Thanks for the tip Martin.
Oh dear, I deleted them all as mentioned above, but after closing and then reopening the menu, they’re all back again.
Anyone else have this problem?
Possible answer to this conundrum on the FF forum which states that Firefox will remove the trust bits from questionable certificates so that they can’t be used anymore while the certificates themselves will remain in place. I assume it will apply to Waterfox / Pale moon etc., as well. https://support.mozilla.org/en-US/questions/952512#answer-414361
Protonmail users are advised to switch to https://dev.protonmail.com/ since it uses a different CA. See: https://www.reddit.com/r/firefox/comments/au7zcz/how_to_remove_darkmatter_certificates_from/eh87vrl/
Close Firefox, delete the SiteSecurityServiceState.txt in your Firefox profile, restart Firefox.
@Tom Hawack: nope, that does not work for me.
TelV said:
“I deleted them all as mentioned above, but after closing and then reopening the menu, they’re all back again.
Anyone else have this problem?”
Same here. Anyone know of a more permanent solution to getting rid of them?
Double check, they may still show but no longer be trusted (You can tell if this is the case because if they are no longer trusted all buttons except for the “Import” button will be greyed out.)
@Wolfie0827,
That’s the case for every CA. But if you click any certificate belonging to a particular CA all the buttons will become available again.
Also, I’m not encouraged by a post by Scott Rea (a Mozilla dev) on the Google Groups forum which reads, quote: “In response to your post overnight (included below), I want to assure you that DarkMatter’s work is solely focused on defensive cyber security, secure communications and digital transformation. We have never, nor will we ever, operate or manage non-defensive cyber activities against any nationality.”
It’s the 7th post down in the link here: https://groups.google.com/forum/#!msg/mozilla.dev.security.policy/nnLVNfqgz7g/YiybcXciBQAJ
Just an correction: Scott Rea is not a Mozilla dev; he works for DarkMatter
@Curtis K,
Yes, I see that that’s correct. I didn’t notice it before I’m afraid. Apologies for the error.
Some background info on him: https://www.rsaconference.com/speakers/scott-rea
You might not have hit OK which is to say, save. Might also want to kill the Hong Kong Post office too (unless you work there ; ). Used to be, there was only a few certs way back, now everyone and their dog catcher is in our business.
@TeIV: yes, I have the same.
We can also select all sub-certificates with the shift key (select the first, press & hold shift and select the last), then delete all at once.
Unfortunately this manipulation breaks some sites, but to reset the certificates, you have to leave FF, go to your profile folder, and delete the file cert9.db then restart FF
Certificate gets reinstalled on every update.
but not trusted
“Releat steps 5-7 for all other certificates that you want to remove. until the QuoVadis Limited listing is no longer there.”
[CTRL] + [A] and you can remove the DarkMatter-crap altogether. 😉
You can select multiple certificates, no need to delete one by one.
This certificate is in TOR browser also.
Done.
Anything concerning Certificates is top priority.
The whole certificate authority model is a joke if it can be abused so easily.
@asd:
I agree completely. The commercial CA method of ensuring trust is entirely broken, and cannot actually ensure the trustworthiness of certificates. This has been true for years now, but people outside of the security business continue to pretend otherwise.
If a cert is signed by a commercial CA, I consider that only slightly better than a self-signed cert and don’t place much faith in it at all.
This. You would have to remove each and every certificate from a Five-Eyes country because the United Arab Emirates is only a small head of the whole hydra.