Privacy-Oriented Origin Policy for Firefox
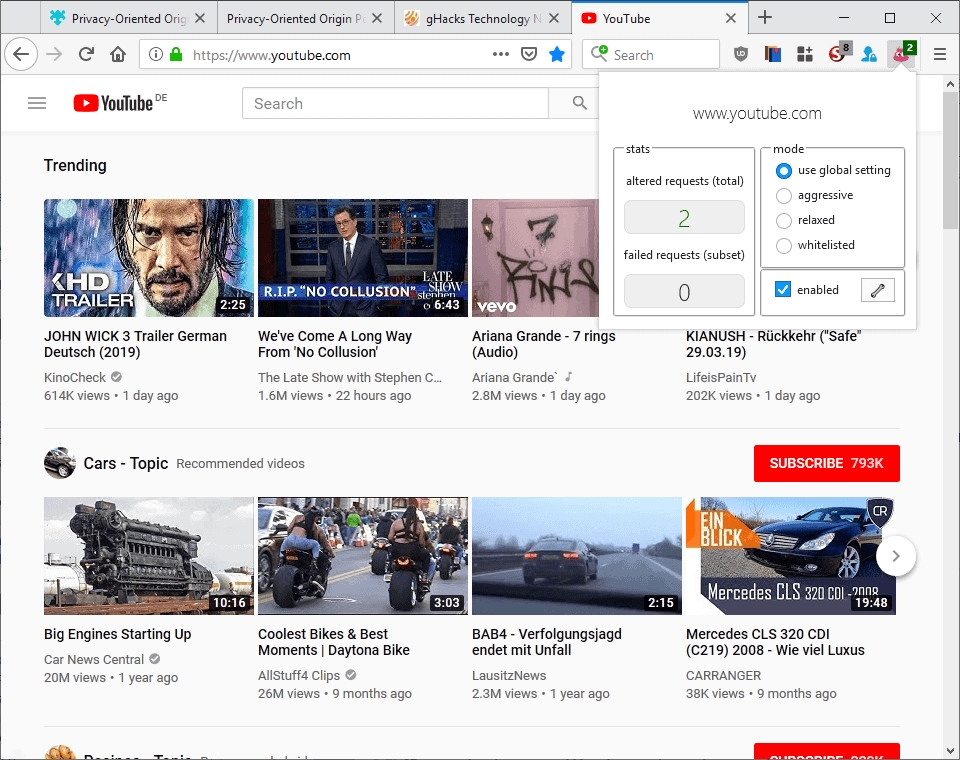
Privacy-Oriented Origin Policy is anew browser extension for the Firefox web browser that blocks Firefox from sending Origin headers under certain circumstances.
To understand what Privacy-Oriented Origin Policy does, it is necessary to understand how the same-origin policy and cross-origin resource sharing works.
The same-origin policy is a security model that restricts access to resources, e.g. JavaScript scripts, based on the origin (made up of scheme, hostname, and port); this is done to prevent cross-site scripting and cross-site request forgery attacks.
Cross-Origin Resource Sharing bypasses the same-origin policy so that other sites may request resources protected by the same-origin policy.
When a browser makes a cross-origin resource request, it adds a reference to the HTTP header that includes the origin that triggered the request. In other words: it tells the server the request is made to that you came from a certain domain, e.g. https://www.example.com:8080.
Privacy-Oriented Origin Policy may modify these requests to block the information from being revealed to the site the CORS request is made to.
The extension comes with several modes of operation; the default mode, relaxed, relies on heuristics to determine whether it is save to strip the origin header. Aggressive mode on the other hand strips all origin headers. Both modes work on GET requests only.
Relaxed mode won't remove the origin header if the request includes cookies, authorization header, or username, password, query, or hash data in the URL.
Some sites, often those that use cross-origin resource requests for legitimate purposes, may break when the extension is used as requests may fail if the origin header is not sent with requests.
Privacy-Oriented Origin Policy comes with options to whitelist domains. If you notice breakage, e.g. some site functionality is not available when the extension strips the Origin header, then you may add it to the whitelist to allow requests on that domain.
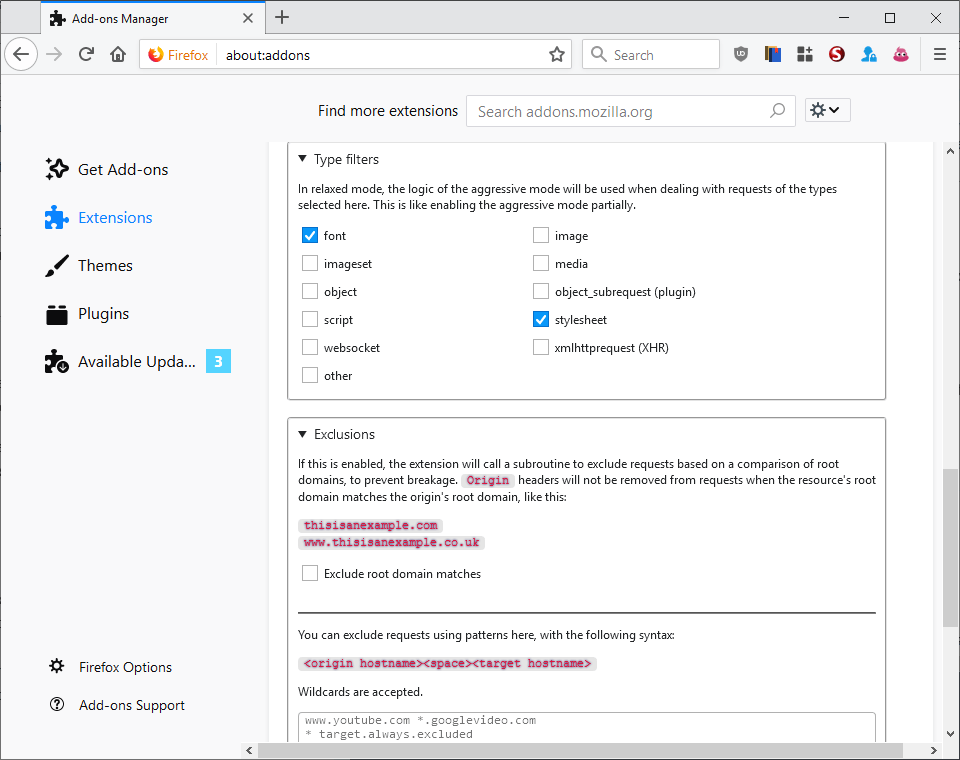
The settings give you even more control over the process:
- Change the global mode (aggressive or relaxed).
- Enable overrides, e.g. using aggressive on certain sites or whitelisting sites.
- Select types of requests, e.g. font or stylesheet, that you want handled in relaxed mode like in aggressive mode.
- Exclude root domain matches, to allow requests between non-www and www domains that share the same root, e.g. example.com and www.examplec.om
- Exclude requests using patterns.
Closing words and verdict
Privacy-Oriented Origin Policy is another browser extension that attempts to improve user privacy by restricting built-in functionality. It requires a bit of trial and error to make sure that essential features don't break because of it.
Firefox users who use uMatrix, uBlock Origin, NoScript or other content blockers that can block third-party requests offer an alternative.
Now You: Do you use privacy extensions?


























There’s a post on Reddit about this extension – https://www.reddit.com/r/firefox/comments/abk98u/i_found_this_new_privacy_addon_and_i_have_some/
The comment at the bottom caught my attention,
“So the extension removes the origin header from the request (website A), and injects a CORS allow * in the response (website B). This way website B won’t know the origin of the request, yet you’re still able to make the request to website B due to the CORS injection. That seems dangerous.
If for instance, website A is a malicious site and you give it the authority (through CORS injection) to make calls to website B, say an email API service, then website A can make requests to website B and send emails on your behalf, without your permission. And this is just one example. CORS is there to prevent this from happening.”
Don’t know if i should install it, Pants, i need some advice, lol.
So, if I already use Ublock origin, noscript, decentral eyes, and privacy badger…do I need to add this tool ?
I use Referer Control for this: really powerful, you can set rules From sites, To sites, using regular expressions…
But because of that, it may not be the most user-friendly of the bunch.
https://addons.mozilla.org/en-US/firefox/addon/referercontrol/
There is no need to set into aggressive mode.
Set to relax is a better option.
Additional to default you can check the scripts and XHR type filters.
Exclusions:
Check the “Exclude root domain matches” and:
*.youtube.com *
*.google*.* *
Cheers
As Joe mentioned, “I’m learning about new privacy concerns” on a daily basis, so I had to read a bit more about CORS: “Cross-Origin Resource Sharing (CORS) is a W3C spec that allows cross-domain communication from the browser. By building on top of the XMLHttpRequest object, CORS allows developers to work with the same idioms as same-domain requests.”
Everybody knows this, I guess, and it’s, as one post worded it, “an interesting thing with developers. Since the same origin policy is designed for the security of the users and not the developers, it should be made possible to allow the scripts from the given site to go across the restrictions.”
In other words, in HTML5, CORS is really a “good thing” when used by the right people for the right reasons and lets developers “stitch together a rich web experience.”
I also read that it was quite simple for a developer to code a site that would easily disable any CORS related functions. Period. CORS add-ons would be pointless for such a site and nefarious developer.
After installing the reviewed add-on, I wasn’t entirely sure what adjustments it was making, so I went the manual route:
For instance, the following items need to be tweaked in Firefox in about:config–
security.fileuri.strict_origin_policy [this seems to be the biggie, and it’s already set to ‘true’]
network.http.refere.XOriginPolicy
network.http.sendRefererHeader [guess this is an old setting and needs to be 0]
And these from Mozilla:
https://wiki.mozilla.org/Security/Referrer
Definitely a bit out of my space, but I feel much more comfortable making changes that I can see and somewhat understand. POOP probably does a much better job.
Anyway, fascinating topic. Wondering if my browser will still work!
Thanks, Gerard, For thinking of me. I was referring to the landing page. I had already visited the two by you mentioned website pages and I have already installed the extension and right now I am trying to learn about the WebExtension. I am trying to figure out right now or like Martin mentioned how to get with Ublock and Noscript the same functions.
I have already installed: NoScript, decentraleys, UBlock origin, smart referer, skip redirect, chameleon, canvas defender, Forget me not, I don’t care about cookies, privacy badger, https everywhere,
Suggestions are already welcome.
Martin, Thanks for this article. I noticed that your link in the summary section is directed to the review, not to the WebExtension page https://addons.mozilla.org/en-US/firefox/addon/privacy-oriented-origin-policy/
@Paul(us). The addons.mozilla link is in the summary block.
The extension can also be downloaded and installed manually here:
https://github.com/claustromaniac/poop/releases
Home page with documentation:
https://github.com/claustromaniac/poop/
Note that, even more important than the Origin header, the Referer header should be hidden/spoofed too for privacy, as it gives the full URL and not just the domain name. The Smart Referer extension helps with that problem :
https://addons.mozilla.org/firefox/addon/smart-referer/
About the Origin header itself, the Decentraleyes extension has an option to remove it for some CDN in addition to the Referer header (“cut the sensitive metadata from authorized requests”) :
https://addons.mozilla.org/firefox/addon/decentraleyes/
and the possibility for Smart Referer to hide the Origin header too is being discussed :
https://gitlab.com/smart-referer/smart-referer/issues/118
So it’s almost like Decentraleyes?
No.
Its seems like every week i’m learning about new privacy concerns. I hope Librefox can address this for me because It’s getting a bit too much to keep on top of all these and just enjoy getting use from my computer.
Thank you Martin,
I have been using Poop for a few days now without any problems. Maybe it slow down a little bit my download speed, I think.
Aggressive mode by default and I switch to relaxed mode if a site is broken instead of whitelisting it; for the moment, only youtube.com & deepl .com are in relaxed mode, reddit.com works with aggressive mode for example.
here is the only reddit discussion about:
https://www.reddit.com/r/firefox/comments/abk98u/i_found_this_new_privacy_addon_and_i_have_some/
“I have been using Poop for a few days now without any problems.”
lol
If there is a problem, there is a solution.
If there is no solution, there is no problem.
I’ve no problems since the extension provides solutions
Quite the same as @sangheeta, Global mode set to Aggressive and switched to per-site Relaxed if issues, then only whitelist should issues remain (unlikely).
Relaxed mode itself is configurable : I’ve set default (font & stylesheet) + xmlhttprequest (XHR)
Exclusions (whitelisted sites) : none at this time.
Exclude Root domains is checked (default) : I believe almost everyone will keep it that way.
Exclusions (request patterns) : 1 only at this time = http://www.youtube.com *.googlevideo.com
Other : Spoof cross-origin Referer is checked (default) — This means, as mentioned in the options, that *only* requests already altered by POOF will have their Referer headers spoofed.
—
Works nicely. Of course POOF will be far less active when access to 3rd-party site is filtered by an extension such as uBlock Origin but when those accesses occur POOF will show its jaws and bit when applicable.
I read and understand many users who express their exasperation about new settings, new extensions and one’s attention to check and set all that accordingly.
I’d just like to remind that if we may protest against browsers’ new features should we consider them as gadgets and/or as privacy invading (and that is a debate and those debates occur here on Ghacks!) on the other hand the multitude of settings and the multitude of dedicated extensions devoted to enhancing our privacy is not the browsers’ developers fault but their reaction (for our good) to the everlasting and ever increasing brain-storming developed by companies in order to peek all they can about us, users.
I won’t complain about the multitude of browsers’ settings, I’m happy they’re made available and you won’t find more than in Firefox, and I’m happy add-on developers contribute to enhancing what exists and/or adding their work-around for what lacks.
@Tom Hawack: if a site is broken how do you know it is due to POOP and not due to uBO, or the other way round? This could end slowing one’s workflow and costing time. Am I right?
That’s
Exclusions (request patterns) : 1 only at this time =www[dot]youtube.com *.googlevideo.com
www[dot]youtube.com (with the dot) is modified here to http://www.youtube.com
-> Don’t set the http:// in POOP’s settings
Thanks for the tips, Tom, I appreciate