Restore files that were encrypted by Thanatos malware
Thanatos is a ransomware variant that has been distributed using malware campaigns over the past few months.
Attack vectors include distribution through chat rooms on the Discord chat platform but also through other channels. Users need to execute specifically prepared files on Windows PCs to initiate the ransomware infection process.
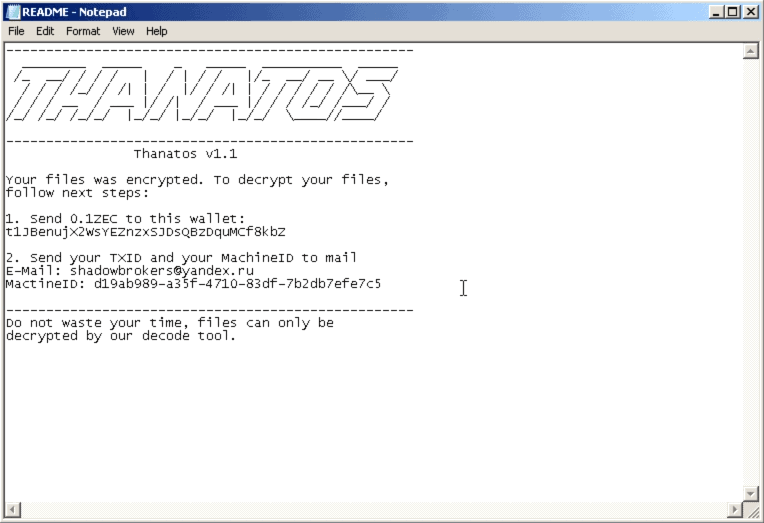
Different versions of the malware were distributed with Thanatos 1.1 being the most recent version of the ransomware and the likelihood that newer versions will become available.
The name Thanatos comes from the readme file that attackers plant on the user system. It includes instructions to users to pay a ransom using electronic currency to gain access to a decrypting tool to decrypt files that the ransomware encrypted on the user's device.
Thanatos places its files in the %APPDATA%/Roaming directory using random directory and executable names that it generates using the system's uptime. Thanotos scans important directories such as documents, pictures, OneDrive, or desktop to and encrypts files in those directories using AES encryption.
Cisco's Talos group analyzed Thanatos and managed to create a decryption tool that affected users may run to attempt to decrypt files and regain access to these files if the operation is successful.
ThanatosDecryptor has been released as open source. The program is said to work against version 1.0 and 1.1 of Thanatos and should be run against the encrypted files (that have the .THANATOS extension) on the infected machine.
The program attempts the decryption of some file types, docx, xlsx, pptx, zip, and about twenty more at the time. In other words: if Thanatos encrypted unsupported file types, ThanatosDecryptor won't be able to decrypt those at this point in time.
ThanatosDecryptor scans directories that Thanatos malware targets for files with the .THANATOS extension. Each encrypted file includes reference to the original file type and the decryptor application uses the information to determine whether it should attempt to decrypt the file.
The developers describe the decryption process in the following way:
ThanatosDecryptor also parses the Windows Event Log for the daily uptime messages and uses the encrypted file time metadata to determine a starting value for decryption. This value is used to derive an encryption key, an AES decryption operation is done against the file contents, and the resulting byte are compared against values known to be at the beginning of those file types. If the comparison is unsuccessful, increments the seed and tries this process again. Otherwise, the file is decrypted and written out with the original file name.
Finally, once one file has been successfully encrypted, ThanatosDecryptor uses the SEED value from that decryption attempt as a starting point for decryption attempts against follow-on files (since they are all likely to be very similar).
The developers note that the program could be improved, for example by adding support for additional file types or by using multi-threading to speed things up.
Windows users who are affected by the Thanatos ransomware should give ThanatosDecryptor a go as it may decrypt encrypted files.
The Talos researchers note that affected users and businesses should not pay the ransom as "the malware authors are unable to return the data to the victim" due to "issues present within the encryption process leveraged by this ransomware".
Additional information is available on the Talos Intelligence blog.


















If you have any System Restore points, you might try using Nirsoft’s ShadowCopyView to restore files.
That being said, the best defense against malware/ransomware is frequent backups.
Thanks for posting this Martin. I suspect that the page will be pulled up when files get encrypted by thanatos, and they look for a way to undo the damage.