Find out if your Intel system is vulnerable to Intel Manageability Engine vulnerabilities
Intel published a security advisory yesterday detailing security vulnerabilities in the firmware of the company's Management Engine, Server Platform Services, and Trusted Execution Engine.
A wide range of Intel processor families and products are affected by these issues, including 6th, 7th and 8th generation Intel Core processors, Intel Xeon processors, Intel Atom processors, Apollo Lake processors and Intel Celeron processors.
Basically, systems using Management Engine firmware versions 11.0, 11.5, 11.7, 11.10, and 11.20, Server Platform Engine firmware version 4.0, and Trusted Execution Engine version 3.0 are impacted by the vulnerabilities.
Attackers may exploit security vulnerabilities to gain unauthorized access to affected systems. Potential scenarios include running code outside the visibility of the operating system or user context, causing system instabilities or crashes, or impacting local security feature attestation validity.
Find out if a system is vulnerable

Intel released a detection tool which you may download from this web page. It is available for Windows 7 and newer versions of Windows, and for Linux.
The program runs a quick scan and returns its findings afterwards. It highlights whether the system is vulnerable, and displays the Intel product and its firmware version as well.
What to do if the system is vulnerable
There is nothing that users can do to the system directly to fix the vulnerability. Intel notes that it is up to OEMs and manufacturers to release updates for their products to fix the security issues.
What that means is the following: If you have bought a PC from a manufacturer like Dell, Lenovo, HP or any other PC manufacturer, you need to wait for them to release updates that address the issue.
Intel lists links to support information on this support article. The company will update links to manufacturers when updates are released by them. Currently, links are available for Dell and Lenovo customers.
Update: Now includes links to Acer, Fujitsu, HPE, and Panasonic as well.
Users who built a PC by themselves, changed the motherboard, or bought a pre-assembled PC using custom parts, need to consult the motherboard manufacturer instead.
Closing Words
Judging from past vulnerabilities and patching activity, it seems very likely that manufacturers won't release updates for some systems and motherboards. Since Intel prevents direct access to affected features, these systems will remain vulnerable throughout their lifetime.
This is not the first issue that affected Intel's Management Engine. The EFF published a detailed account on that back in May 2017 for instance, urging Intel to provide the means to give administrators and users options to disable or limit the Management Engine.
Now You: Is your system affected?


















So why is this thingie running on my AMD-processor machine? Do AMD processor have a similar problem?
related info for all uefi/intel curious! very technical but a scary eyeopener non the less!
https://www.youtube.com/watch?v=iffTJ1vPCSo&feature=youtu.be
Between this and the Ryzen stability problems, older hardware is looking more attractive every day. Old hardware just works, it is more secure because it lacks features like that which are outlined in the article, it is “fast enough”, and it is a fraction of the price!
MSI Z170A Gaming M5 with a 6600K is vulnerable. MSI hurry the fuck up! Other vendors already released updates.
Not an MSI issue, please contact Intel(TM)
My Win 8.1, Intel i5 laptop not vulnerable.
Thanks martin for the article.
HP has released the firmware update for their notebooks (I don’t know if they released them for all of the affected ones, but my laptop has the update on the driver downloads). The date of release (according to the Support Site) is October 17, 2017. This comes with firmware version 11.8.50.3390 (SVN 3) and the ME driver version 11.7.0.1043. There’s also an update to Intel’s Trusted Execution Technology as well.
Good news here : This system is not vulnerable. :-)
I got a very useful “maybe.”
UPDATE: An updated version of Intel’s Detection Tool (which SUMo alerted me to in a somewhat roundabout way*) now tells me my ThinkPad T510 is in fact vulnerable. Unfortunately, no updated BIOS is showing up in Lenovo System Update and I’m not confident one ever will, since the T510 is nearly 8 years old. Still, it would be a concrete demonstration of Lenovo’s confidence in the durability of T-series ThinkPads and of commitment to long-term security if they were to produce one. (Hint, hint, Lenovo.)
*SUMo flagged the Detection Tool’s MEInfoWin.exe component (two copies) as being out of date. SUMo’s built-in search function accordingly set up a search string for the component instead of for the Detection Tool itself and yielded the wrong utility (the Intel Manageability Engine Verification Utility) in the top search results. What you want is the Intel-SA-00086 Detection Tool. For updating, the best thing is to just make a shortcut to https://downloadcenter.intel.com/download/27150 and remember to use that instead of SUMo … which incidentally is still flagging the Detection Tool’s MEInfoWin.exe component as being out of date. I’m guessing that SUMo is at least partially crowd-sourced, so even though the Detection Tool is probably not a commonly “installed” portable app, maybe it will start showing up directly in SUMo’s update scans, eventually.
Lenovo states that they will be shipping a firmware upgrade as early as Nov 23. They have a full list of all the Lenovo systems that are affected/not affected on their website.
https://support.lenovo.com/ca/en/product_security/len-17297
The computers I look after not on the affected list. Very glad of that. Firmware updates are not my favorite thing to do.
I’ve got a Lenovo ThinkPad T510. I’m not going to reboot now to look, but I kind of recall that in the BIOS there was something pertaining to the Intel Management Engine and that I did my best to disable it and avoid downloading firmware for it. The Intel “discovery” tool tells me it couldn’t determine what version of IME I have and that I “may” be vulnerable, and Lenovo’s listing doesn’t go back as far as the T510. As I implied below, not terribly useful.
Can anyone tell me how to start the scan on a Linux machine?
Navigate to wherever you saved the file with your file manager. Right click on it, then click “Extract here.” Open a terminal and use cd to navigate to the SA00086_Linux folder that you just unzipped. Type ./intel_sa00086.py and press Enter. That should do it.
I did not have to make any of those files executable, they already were when I unzipped them. If you have any problems, inside that SA00086_Linux is another folder called ‘documents.’ The .pdf file has instructions if you need them.
(source: Linux Mint forums ; by jimallyn)
It doesn’t matter because, in reality, there is nothing to do even if the current system in use is vulnerable.
Much like going for a physical exam; my doctor always listens to the carotid arteries in the neck, but laughs–seriously, every year. And I always ask why. “Because we don’t know what to do even if we hear something odd.”
“Vulnerability” is a fear tactic-term; we are vulnerable in so many ways that if one were to list the ways, one would be enlisted in an asylum within hours.
Here Hear – besides it won’t work on my Windows 8 box. I was going to try booting from a Q4OS live CD I have and try the Linux build. But even then, so what can I do if I’m vulnerable? Is this just Intel trying to appear as being responsible?
Seems, you need Ubuntu 16.04 LTS to run the Intel detection tool.
It would be much better if you post instructions how to remove Minix/IME from PC. It’s a backdoor OS to gain full remote access that shouldn’t even exist in the first.
It’s impossible to completely remove Minix/IME, at most you can neuter it by removing parts of it like the webserver, networking stack, and other modules that are not strictly needed.
@ dark
https://www.howtogeek.com/56538/how-to-remotely-control-your-pc-even-when-it-crashes/
The above link shows the step-by-step instructions on how to configure both computers for Intel MEBx/AMT/vPro. From it, you can also see how to disable it in BIOS.
… So, most affected computers should be safe from hackers even if unpatched by a BIOS firmware update, unless the computers have already been configured for it, eg by business IT Admins.
Someone has already posted a link to me_cleaner but i’ll post it again if you like
https://github.com/corna/me_cleaner
However IMO it should only be attempted if you know what you’re doing and/or don’t mind taking the chance that you may have to buy a new motherboard as the possibility of being left with a bricked system are extremely high,
That would be good. At least that way Minix/IME, it will be probably impossible for anyone to remotely access Minix/IME.
Step by step instructions would be nice.
@ dark
You can only disable Intel ME/AMT/vPro in BIOS …
https://software.intel.com/en-us/forums/intel-business-client-software-development/topic/563988
You just turn it off. Everything still stay and may return active at Intel will.
@aaabbbccc
Could be placebo as Minix/IME likely can bypass bios.
(The “test” took less then 3 seconds)
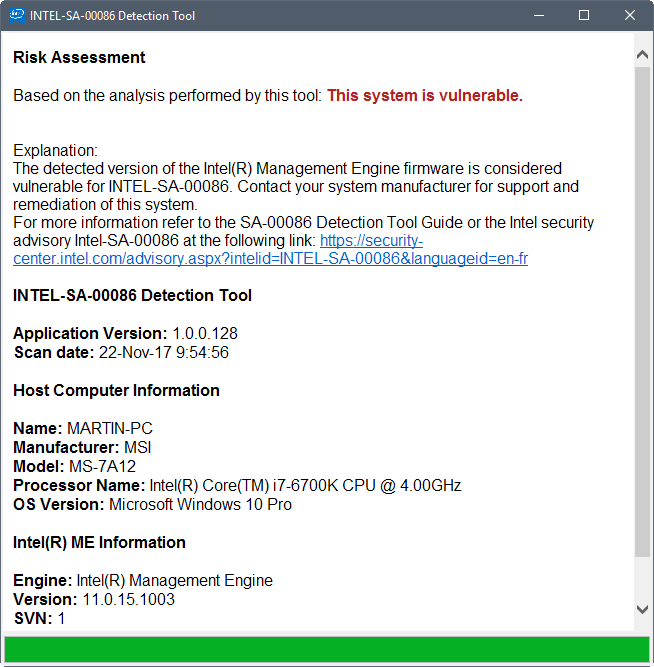
Risk Assessment
Based on the analysis performed by this tool: This system is not vulnerable.
For more information refer to the SA-00086 Detection Tool Guide or the Intel security advisory Intel-SA-00086 at the following link: https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00086&languageid=en-fr
INTEL-SA-00086 Detection Tool
Application Version: 1.0.0.128
Scan date: 11/22/2017 8:10:31 AM
Host Computer Information
Name: ******
Manufacturer: MSI
Model: MS-7845
Processor Name: Intel(R) Core(TM) i7-4790K CPU @ 4.00GHz
OS Version: Microsoft Windows 10 Pro
Intel(R) ME Information
Engine: Intel(R) Management Engine
Version: 9.0.30.1482
SVN: 1
Copyright(C) 2017, Intel Corporation, All rights reserved.
Correct me if I am wrong, but local access or remote access such as in remote desktop, are required to exploit the vulnerability. A PC in a bedroom or a home made router with no remote access and no unprotected open ports are safe.
Wrong, as remote desktop is an OS feature. This Intel ME is behind the OS. No OS Firewall can get its connections, but external hardware can (they need to block I2C Protocol).
@ cdr
Intel ME/AMT/vPro is enabled by default in most high-end Business PCs. Why is it enabled by default and not disabled by default.?
… There may be a possibility that hackers or the NSA can remotely access such computers, even if they have been switched off, as long as they are still connected to the AC wall outlet and the router.
This feature is supposedly for businesses to remotely manage their off-base computers/servers at the BIOS level, eg can even remotely reinstall the OS on a “sleeping” computer or borked server.
ME Analyzer tool, so you know what you have.
https://github.com/platomav/MEAnalyzer
For advanced users,
https://www.win-raid.com/t2540f39-ME-cleaner.html
I am beginning to think that OEMs suck at entering into agreements with their ‘business partners’. Intel is punting its responsibility and the OEM is on the nut for it? The alliance is a strange one. Intel created the problem and as the EFF has suggested, should offer options to users and sysadmins to disable or limit the Management Engine.
Alliance? Intel delivers to OEM. OEM has to agree, otherwise they are FIRED !!
Based on the analysis performed by this tool: This system is not vulnerable.
Processor Name: Intel(R) Core(TM) i5-4590 CPU @ 3.30GHz
OS Version: Microsoft Windows 7 Professional
Lucky me :)
4790K not guilty, but I have to wonder how many more secrets our betters keeping from us.
Clean bill of health :)
Not particularly good news for you though Martin judging by your screenshot.
Also, according to https://securitytracker.com/id/1039852 The Intel Trusted Execution Engine (TXE) and Intel Server Platform Services (SPS) products are affected by separate vulnerabilities.
We have to wait for OEMs and manufacturers to fix the issue? So I need to call Dell about my non-Linux laptop and ask them to provide a Linux update for it? I doubt they’re going to do that. So how is this going to work for Linux users? I mean: Intel did release a version of this tool for Linux, why would they do that when OEMs aren’t going to push updates to us anyway?
As far as I can tell, these are BIOS / motherboard updates, not programs you run on any particular operating system to patch the issue.
The total ignorance of the common customer is appalling.
This issue has ZERO involvement of OEM, as Intel delivers a closed-source
system complete with CPU and Network capabilities based on MINIX.
Most people doesn’t even realize how bad is this Intel botnetting.
imgur.com/8zbx2Nc
Is this sending a request to the NSA, adding me to aqueue list for them to try and get into my PC, and if they are able to do so I’ll get some text telling me that my PC is vulnerable? I guess so, It’s been half an hour already and nothing happens, so I guess I’m quite low on their queue list.
Seriously, why can’t Intel just release a list of affected processors? Why do I have to resort to cr.p like this that is refusing to work? Are they affraid that people are going to laugh (or cry) at the amount of affected CPUs?
On a quick google search I found that all K CPU’s were not affected until 8700/8600K, but that’s contradicted by the fact that 6700k is affected, so..
@Yuliya
I totally, completely subscribe to your perspective, in all things, computers these days.
i3-6100 @ 2.30 GHz, Skylake-U/Y 14nm Tech
The Analyzer: still needed a file (claiming missing in my system) to properly execute.
Virus Total: Awards green lights aplenty for the file.
But still, this is the reason I create a restore point, formally once a week…I would refer to that day as, “Sunday restore.” But with M$ft doing so much sneaky back-ground crap…I create a system restore point very couple of days, or before I download any system file. Also, in my system, there is a history of previous restore points magically disappearing. Again, M$sft is doing their part for planned err…..forced obsolesce. I trust very few companies these days, most focus on pleasing shareholders, not users.
INTEL-SA-00086 Detection Tool stuck at “System analysis running – please wait…” with no result. Win8.1/64, CPU DualCore Intel Core 2 Duo E6400, 2133 MHz (8 x 267), Conroe-2M
Still no result here either. I wonder if it’s because we’re running Windows 8 (as in the original build)
I have dual Xeon CPUs (the old Netburst style), so it’s ancient hardware.
2 September, 2015 – Intel Introduced its 6th Generation Intel Core
http://news.techtime.co.il/2015/09/02/intel-4/
Your CPU is much older.
Negative thankfully.
They even left a blank password bug so anyone could use it.
Makes me wonder if this is influenced by a desire to hobble security,
or just complete incompetence.
Everyone should ask for a refund if affected.
Band together and sue.