Nvidia GeForce Experience Node.js security vulnerability
Sec Consult security researchers discovered a vulnerability in Nvidia's GeForce Experience software that allows attackers to bypass Windows application whitelisting.
Nvidia's GeForce Experience is a program that Nvidia installs by default in its driver packages. The program, initially designed to provide users with good configurations for computer games so that they run better on user systems, has been blown up since then by Nvidia.
The software checks for driver updates now, and may install those, and it enforces registration before its other functionality becomes available.
What's interesting about it is that it is not needed for making use of the graphics card, and that the video card works equally fine without it.
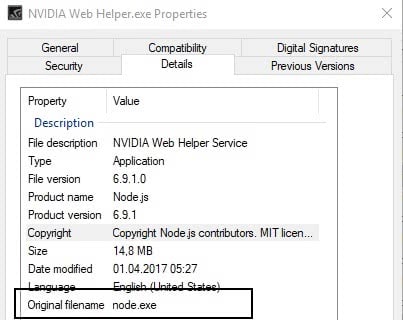
Nvidia GeForce Experience installs a node.js server on the system when it is installed. The file is not called node.js, but NVIDIA Web Helper.exe, and it is located under %ProgramFiles(x86)%\NVIDIA Corporation\NvNode\ by default.
Nvidia renamed Node.js to NVIDIA Web Helper.exe and signed it. What this means is that Node.js is installed on the majority of systems with Nvidia graphics cards, considering that drivers are installed automatically and not using the custom install option.
Tip: Only install the Nvidia driver components that you need, and disable Nvidia Streamer Services and other Nvidia processes,
Whitelisting allows administrators to define programs and processes that may run on an operating system. Microsoft AppLocker is a popular whitelisting solution to improve security on Windows PCs.
Administrators may improve security further by using signatures to enforce code and script integrity. The latter is supported by Windows 10 and windows Server 2016 with Microsoft Device Guard for instance.
The security researchers found two possibilities to exploit Nvidia's NVIDIA Web Helper.exe application:
- Use Node.js directly to interact with Windows APIs.
- Load executable code "into the node.js process" to run malicious code.
Since the process is signed, it will bypass any reputation-based checks by default.
From attacker perspective, this opens two possibilities. Either use node.js to directly interact with the Windows API (e.g. to disable application whitelisting or reflectively load an executable into the node.js process to run the malicious binary on behalf of the signed process) or to write the complete malware with node.js. Both options have the advantage, that the running process is signed and therefore bypasses anti-virus systems (reputation-based algorithms) per default.
How to resolve the issue
Probably the best option right now is to uninstall the Nvidia GeForce Experience client from the operating system.
First thing you may want to do is make sure that a system is vulnerable. Open the folder %ProgramFiles(x86)%\NVIDIA Corporation\ on the Windows PC and check if the directory NvNode exists.
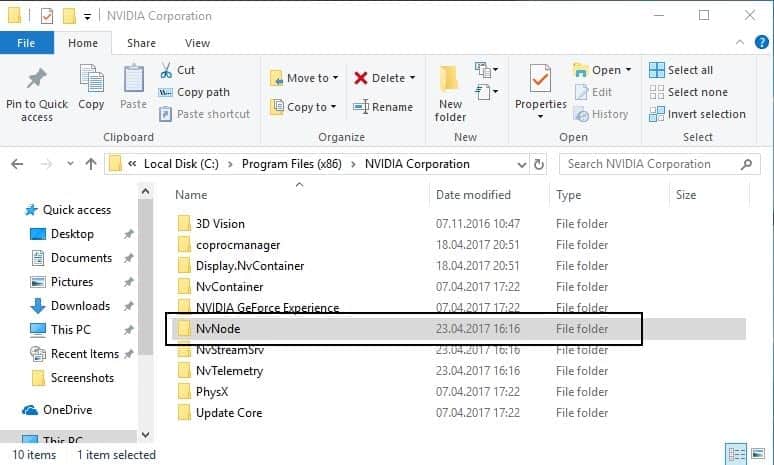
If it does, open the directory. Find the file Nvidia Web Helper.exe in the directory.
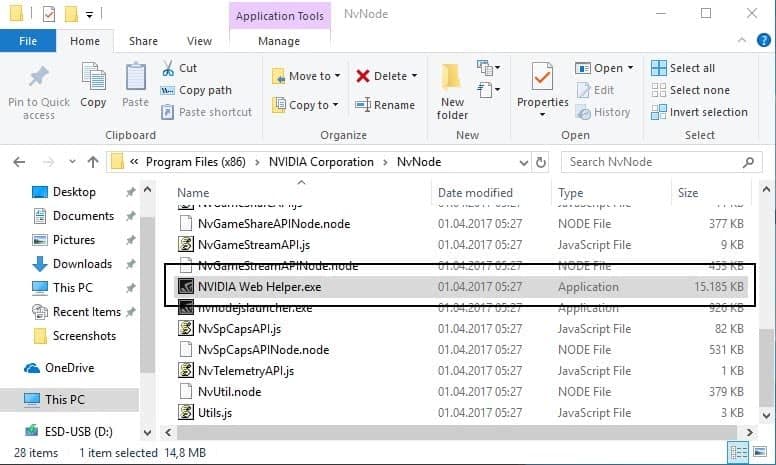
Right-click on the file afterwards, and select properties. When the properties window opens, switch to details. There you should see the original file name and product name.
Once you have established that a Node.js server is indeed on the machine, it is time to remove it provided that Nvidia GeForce Experience is not required.
- You may use the Control Panel > Uninstall a Program applet for that, or if you use Windows 10 Settings > Apps > Apps & features.
- Either way, Nvidia GeForce Experience is listed as a separate program installed on the system.
- Uninstall the Nvidia GeForce Experience program from your system.
If you check the program folder afterwards again, you will notice that the entire NvNode folder is no longer on the system.
Now Read: Block Nvidia Telemetry Tracking on Windows PCs


















It’s definitely still around for people like me who don’t know that much about PCs . Just had to spend 3 hours sorting it out.
http://nvidia.custhelp.com/app/answers/detail/a_id/4459
“First version that includes the fix
GFE 3.5.0.76”
Thanks, that is good news.
Wow, as a smaller SSD user, I just spent an hour clearing out all the old installer files Nvidia GeForce Experience left behind. (20+ GB!) After seeing this, I’m thinking I’ll just uninstall it and not bother reinstalling it. It bugs me that it asks me to login to update my drivers anyway.
Nvidia GeForce Experience Login = super cookie
yeah it is here
I am still using the old, pre registration required version, and not only does it still do shadowplay, it also does not seem to have this vulnerability in the first place!
+1
Already fixed in upcoming nVidia driver. Same like ICC color profile bug.
Do you have a proof for that?
Thanks, that is good news.