Punycode Phishing Attack fools even die-hard Internet veterans
There are only a handful of rules that you need to know to counter any phishing attack that you may be exposed to on the Internet, right?
Check the web address and make sure it is the right one. Also, make sure you don't follow any links on pages or in messages that you don't trust 100%.
While that is sound advise, and will help you identify the bulk of phishing attacks, Chinese security researcher Xudong Zheng just demonstrated that things may not always be that easy.
Punycode Phishing Attack
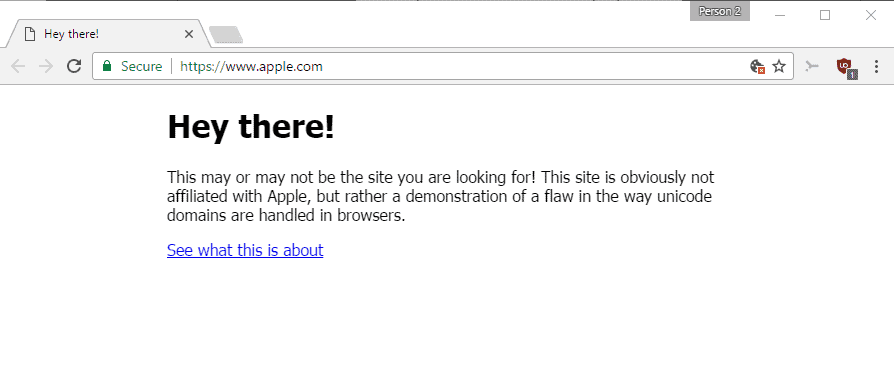
He set up a special domain to demonstrate how this works. Point your browser to https://www.аррÓе.com/ and watch what happens.

Somehow, you did not end up on Apple's website, but on a site that uses the correct URL, seemingly, and has a security certificate. If an attacker would have replicated Apple's website, and not displayed the "hey there" message, would you have noticed that you are not on Apple's site?
You wonder probably how this works. The technique uses something that is called Punycode. Broken down to the essentials, Punycode enables you to register domain names with characters that are not native to a language.
A basic example would be the German city of München. The letter ü is not available in English for instance, and that is where Punycode comes into play. The Punycode version of München is xn--mnchen-3ya. You can convert text on a site like Punycoder to see how other names are converted.
One of the main issues from a security perspective is that some characters are not easily distinguishable. Compare the ASCII "a" with the Cyrillic "а" and tell me if you see the difference.
An attack that makes use of these similarities are called homograph attack. Modern browsers come with security features that protect users from these kind of attacks.
If you open this аpple.com domain name for instance, you will notice that most browsers displays the Punycode version of it (http://xn--pple-43d.com/) instead automatically.
The security researcher discovered however that the protection in Chrome or Firefox fail if every single character is replaced with a foreign one. This is why this аррÓе.com domain name displays as if it is the real deal, even though it is actually xn--80ak6aa92e.com.
Good news is that some browsers protect you against the attack already. If you use Internet Explorer, Microsoft Edge, Safari or Vivaldi, you will notice that the Punycode address is displayed automatically.
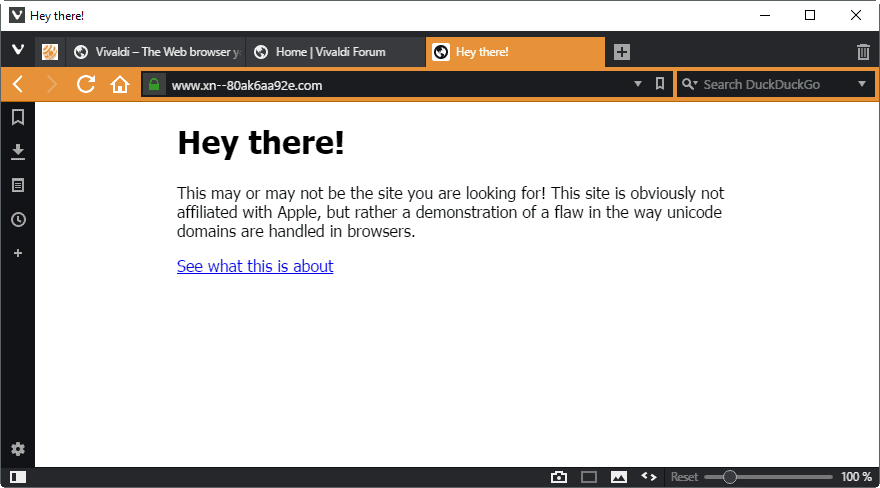
If you open the same domain name in Chrome, Firefox or Opera however, apple.com is displayed instead.
That's a big problem obviously, as that address is not distinguishable from Apple's real domain name.
The researcher disclosed the vulnerability to Google and Mozilla on January 20, 2017. Google created a patch for the issue which the company plans to roll out later this month in Chrome 58.
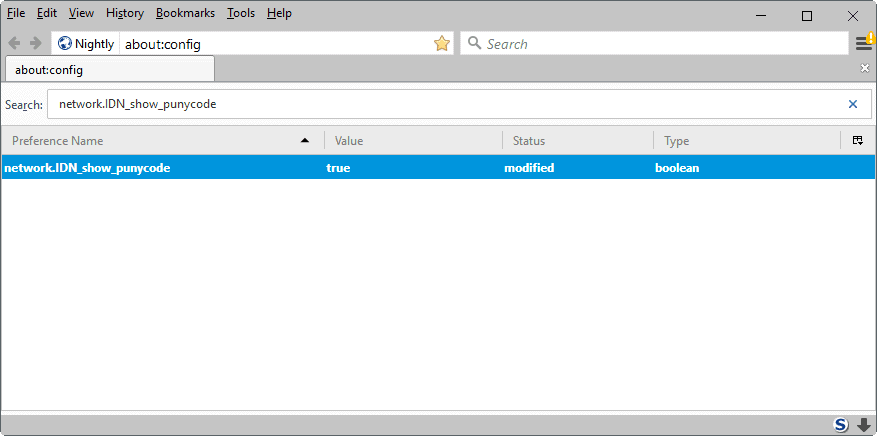
Mozilla filed a bug on Bugzilla, but no consensus appears to have been reached yet. Firefox users who want to be on the safe side of things need to make a change in the configuration:
- Type about:config in the Firefox address bar and hit the Enter-key.
- Confirm that you will be careful.
- Search for network.IDN_show_punycode.
- Double-click the preference to set it to true.
This forces Firefox to show Punycode when it is used.
Chrome users on the other hand need to wait until Google releases a fix for the browser.
Update: Chrome users can install Punycode Alert that warns users when a Punycode containing URL is loaded.
Now You: would you have fallen for the attack?


















I’m paranoid about email, and my brain anti-spam flags many false positives, including genuine warnings from Microsoft and such.
I wasn’t aware of the Punycode trick, though.
Latest Pale Moon 27.3.0 update provides additional security options on this:
https://forum.palemoon.org/viewtopic.php?f=26&t=15583
Outlook Mail Client and Gmail is vulnerable as well. Our PoC and article: https://ciberseguridad.lamula.pe/2017/04/22/ataque-de-phishing-imperceptible-con-unicode-tambien-afecta-clientes-de-correo-electronico/delphins/
“Good news is that some browsers protect you against the attack already. If you use Internet Explorer, Microsoft Edge, Safari or Vivaldi, you will notice that the Punycode address is displayed automatically.”
Pale Moon protects people against this as well now. The punycode address is displayed in the blue security certificate area that’s visible without clicking.
FYI the firefox addon privacy settings enables network.IDN_show_punycode if set to Privacy and security.
Thanks to Firefox addon Privacy Settings by Jeremy Schomery, I became aware of this great “feature” a while ago and disabled it.
Surprisingly, Edge with default settings does not fall for this phishing attack.
I use FF 52.02 just like @Andy. same thing: network.IDN_show_punycode does not exist.
Try searching for “Puny”
Wow! Good find Martin! I just changed the setting in about:config and the punycode version now shows at the foot of the page when I hover the mouse over your link. Resetting it to it’s default again just shows it as it’s written in your article.
I’m using Firefox 43.0.1 portable version. I don’t see apple.com in the url box but its punnycode translation.
I used Firefox 45.8.0 ESR and I got the https://www.apple.com URL.
I run Windows 10 x64 Home CU, and latest released beta for Chrome x64: Version 58.0.3029.68 beta (64-bit). The problem cited in the Apple example is already fixed.
I too use Chrome x64: Version 58.0.3029.68 beta (64-bit) and the site display secure: http://www.apple.com. So it is not fixed.
If you have the Edge browser, bring up this Ghacks URL and click on the same demo link you used in Chrome. Do you see the same image Martin shows now?
@chesscanoe
I use the link in “Point your browser to https://www.аррÓе.com/ and watch what happens.”
The test Apple URL in Martin’s article does in fact get stopped in Chrome Version 58.0.3029.68 beta (64-bit) . I suspect you are not using the test example Martin provides near the top of his article. Do not type what you see; click on Martin’s link instead.
First of all I’ll start by saying that I don’t use any robust real-time protection on my computers. I use MSE and the older free versions of Malwarebyte’s Anti-Malware and Malwarebyte’s Anti-Exploit. That’s all I need for myself. Haven’t seen a virus or malware object in many years.
Anyway… out of all the browsers I have installed the Only browser that did Not connect to the demo page was IE 11, same results on my desktop and laptop, both running Win7 x64. Pale Moon, Firefox, Vivaldi, Chrome, and Comodo Dragon, ALL connected to the demo page. Vivaldi did not display “apple” in the address bar. Pale Moon and every other browser DID show “apple” in the address bar, at least Pale Moon shows the correct name in the security area of the address bar (far left end). I’ve always looked to see where a link goes to and I have yet to see a link try to do what the demo page does. ;)
https://s12.postimg.org/3mmg2b3ul/Pale_Moon.png
https://s24.postimg.org/bs93dwzhh/Firefox.png
https://s16.postimg.org/4f276qfmd/Vivaldi.png
Have pale moon have not touched about:config
clicked your link
this what i got
Server not found
Pale Moon can’t find the server at http://www.аррÓе.com.
A sad part about a web address is there is usually so much more than just the main domain. I know a lot of people who either click links from emails, or other websites, and never even look at the URL. Even if they wanted to go to Apple.com, and it showed the special characters, I know of a few who would think that was normal (If they even looked at it at all.). :-(
I did that setting in FIreFox, great. I also tried Chromium 59 and the addressbar shows xn--80ak6aa92e, so Chrome users should expect this soon-ish? (Idk at which version is Chrome)
Anyway, I usually expect what I should find when I visit a page, and I’m not going to do anything other than just visit (not create an account, purchase stuff, etc) unless I visit the said site for a while, if something’s shady it usually comes up after a while if not sooner. Also I’ve been replacing а, е, Ñ, Ñ…, итд for years to bypass word filters ;) So..
I use pale moon and it refused to go to the phishing site without touching the about:config setting.
On Waterfox this was set to false by default, changed it to true, asked the dev is he could make this true by default. Thanks!
hi, opera shows this for me
prntscr.com/exigzc
In Firefox, network.IDN_show_punycode was set to false.
However, xn--pple-43d.com is blocked automatically by Emsisoft Internet Security (EIS) :)
FYI – I am running the EIS subscription version with automatic real time protection.
I dont have this in Firefox 52.02?
I have Pale Moon as my default browser, Firefox as my backup. In both the about:config shows as false, yet in both I was unable to connect to either of the links referrenced in your article.
The first link resolved to the following for both browsers:
“Welcome to nginx!
If you see this page, the nginx web server is successfully installed and working. Further configuration is required.
For online documentation and support please refer to nginx.org.
Commercial support is available at nginx.com.
Thank you for using nginx.”
For the second link I got Server Not Found for both.
This is the best article on the web about this problem!
In Edge while showing the real address if you click on the security lock the information says that:
DST Root CA X3 identified the site as http://www.apple.com and the connection is secure…
But in Firefox and Chrome it’s way much worst..
Palemoon, network.IDN_show_punycode FALSE, default.
So much for Chrome being more secure. They’ve know about this vulnerability for 2 1/2 months. As of now, a patch needs to be released quickly. Waiting for the next version sounds like a Microsoft-level excuse for allowing vulnerabilities to exist longer than they should.