KB4012218, KB4012219: Windows Update processor generation detection
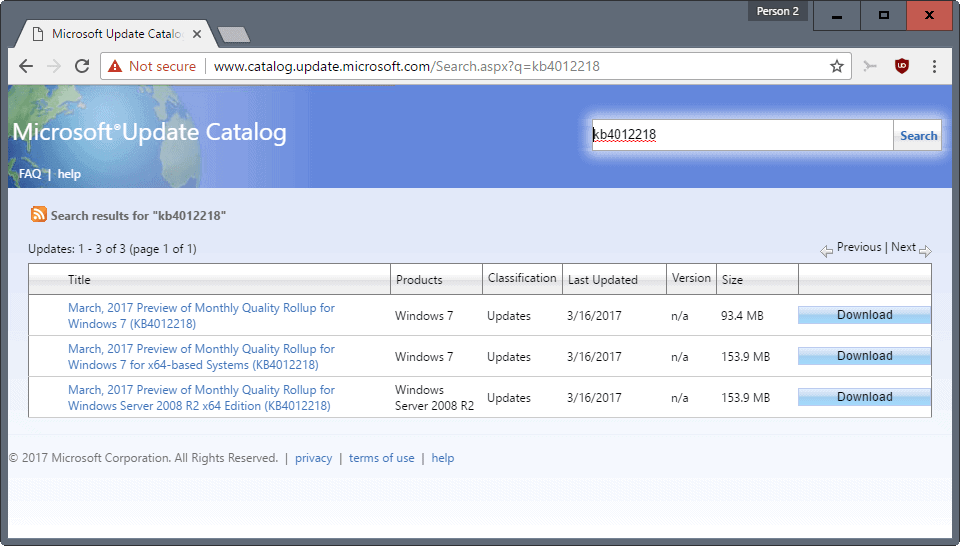
The March 2017 preview updates for Windows 7 and Windows 8.1 introduce Windows Update processor generation and hardware support detection.
Microsoft published KB4012218 for Windows 7 and Windows Server 2008 R2, and KB4012219 for Windows 8.1 and Windows Server 2012 and 2012 R2 yesterday evening.
These previews are only available through the Microsoft Update Catalog, and only include non-security updates.
They are designed to give system administrators, and interested home users, time to test cumulative updates for the operating systems they are released for before they are pushed out through Windows Update on the next Patch Day.
What's particularly interesting about these two preview updates is that they introduce the detection of the device's processor generation and hardware support.
Both include the following entry:
Enabled detection of processor generation and hardware support when PC tries to scan or download updates through Windows Update.
As you may know, Microsoft announced some time ago that it would not support the latest generation of processors on older versions of Windows. To hammer this home even more, Microsoft revealed that it will block updates on older versions of Windows if the device was powered by a processor of the latest generation.
Test showed that this was not the case at the time of revelation. It appears now though, that the updates KB4012218 and KB4012219 introduce that functionality on Windows 7 and Windows 8.1 (and the server versions).
Tests need to be conducted to find out whether this is indeed the case when the release updates are made available though.
For now though, it seems like a good idea to avoid these patches if your Windows device uses a cpu of the latest generation, or if you plan to equip it with one in the future.
KB4012218
- List of changes: On Windows 7 and Windows Server 2008 R2 update history page.
- Direct downloads: on Microsoft Update Catalog.
- KB4012218: support article.
Changelog:
- Enabled detection of processor generation and hardware support when PC tries to scan or download updates through Windows Update.
- Simplified listing of Approved Servers in the Point and Print group policies by allowing wildcards in the server name.
- Addressed issue that produces corrupt output when using fread() to read data from a pipe. The runtime will sometimes drop the newlines between lines.
- Addressed issue to update time zone information.
- Addressed issue with the Local Security Authority Subsystem Service process that crashes on the domain controller when making certain Lightweight Directory Access Protocol requests.
KB4012219
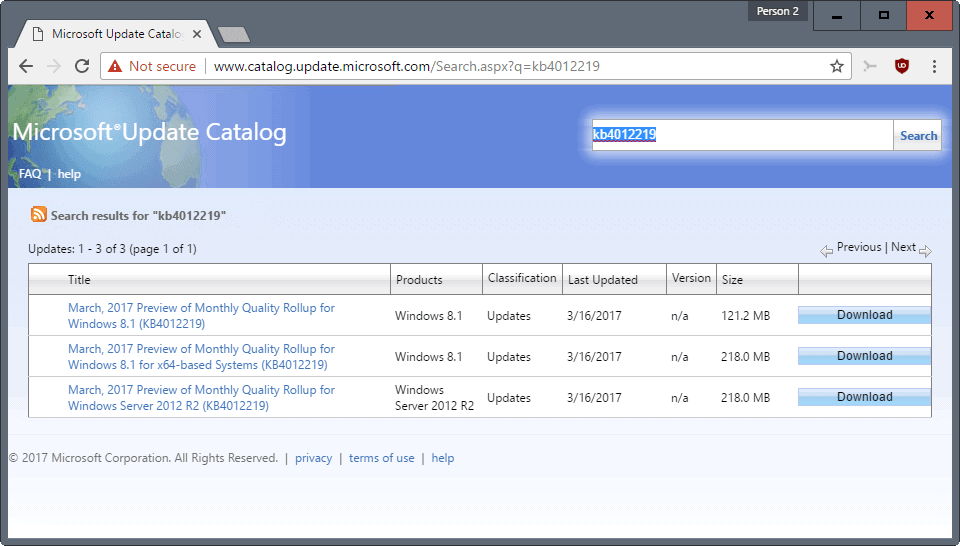
- List of changes: On Windows 8.1 and Windows Server 2012 / 2012 R2 update history page.
- Direct downloads: on Microsoft Update Catalog.
- KB4012219: support article.
Changelog:
- Enabled a warning message in Group Policy Management Console (GPMC) to alert administrators of a design change that may prevent the processing of a User Group after installing security update MS16-072.
- Addressed issue that prevents a smart card module from pairing with a contactless smart card reader.
- Addressed issue where a Scale-Out File Server that uses dual parity disks loses access to a disk if a disk fails while the parity log is being written.
- Addressed issue with the Spaceport driver that causes disks to detach after a hard restart.
- Addressed issue in multipath I/O when Driver Verifier is enabled.
- Addressed issue that causes workload disruption in Azure StorSimple appliances after installing KB3169982. Installation occurs using the KB3172614 rollup (released 2016.07).
- Addressed issue that causes crashes in a customer’s data path management software because of a regression in multipath I/O after installing KB3185279, KB3185331, or KB3192404.
- Addressed issue where installation of KB3121261 on a third-party, thinly provisioned Storage Area Network causes multipath I/O Event ID 48. This is in response to Small Computer System Interface status - 0X28 - SCSISTAT_QUEUE_FULL (SRB Status - 0X4 - SRB_STATUS_ERROR).
- Addressed issue to provide PowerShell cmdlets that enable and gather diagnostics for storage spaces.
- Addressed issue with multipath I/O failure that can lead to data corruption or application failures.
- Addressed issue that causes File Explorer to hang when performing a search on a network drive while connected using the Remote Desktop Protocol.
- Addressed issue that causes a crash when the user tries to connect to the server using WinShare and Remote Desktop Services. Stop error 0x50 at win32k!pDCIAdjClr+0x4f.
- Enabled detection of processor generation and hardware support when PC tries to scan or download updates through Windows Update.
- Improved support for networks by adding new entries to the Access Point Name (APN) database.
- Simplified listing of Approved Servers in the Point and Print group policies by allowing wildcards in the server name.
- Addressed issue to update Windows Defender on Windows 8.1.
- Addressed issue that prevents clients from accessing a file server when using Server Message Block 1.0 and NT LAN Manager authentication after installing MS16-110/KB3187754.
- Addressed issue that produces corrupted output when you use the fread() function to read data from a pipe.
- Addressed issue to set and persist the Quality of Service settings on a per-host basis.
- Addressed issue that breaks high-availability and fail over of a clustered virtual machine (VM). This occurs when the default data store settings for the VMs are configured inconsistently across the nodes in the cluster. For example, some data store settings are in %ProgramData%, while others use shared storage.
- Addressed issue where, under high load, the background tasks threads are blocked. None of the clusters that use Virtual Hard Disk Sharing can access their disks. This results in unresponsive virtual machines.
- Addressed issue (error 0x800b) that causes System Center Virtual Machine Manager to fail after live migrating a virtual machine between two Hyper-V clusters.
- Addressed issue where false file conflicts occur when Windows Server Work Folders is reinstalled after installing Azure Hybrid File Services.
- Addressed issue where share contents go offline if remote clients connect over slow links when encryption is enabled and offline caching is disabled for a server share.
- Addressed issue to generate Remote Desktop Services self-signed certificates to use SHA-2 instead of SHA-1. After this update, any existing self-signed certs in RD Session Host should be updated with SHA-2 certs. However, existing self-signed certs (if any) in Connection Broker and Gateway should be regenerated using the Remote Desktop Management Services (RDMS) UI.
- Addressed issue to allow a user to set the password for a virtual account.
- Addressed issue where IIS Automatic Certificate Rebind feature breaks client certificate mapping with active directory by disabling DS Mapper upon renewal of the server certificate. As a result, no user will be able to access the site unless an administrator manually remakes the binding and enables the DS Mapper.
- Addressed issue where Active Directory returns incorrect active thread count numbers for Lightweight Directory Access Protocol requests. Incorrect thread counts prevent Office 365 from load balancing correctly.
- Addressed issue to update time zone information.
- Addressed issue with random crashes on Hyper-V servers when users access Virtual Hard Disk files on Cluster Shared Volumes.
- Addressed issue that causes file share witnesses stored on a Scale-Out File Server cluster 2012R2 to fail. Event ID for this Error is 1562 and you will get an Error 64 in the Cluster Log for the failed Healthcheck (from RFC 7205769).
- Addressed issue where, after installing security update MS16-123, administrators cannot access some network drives that are mapped using the Distributed File System Namespace. This lack of accessibility occurs even though User Account Control and EnableLinkedConnections are enabled.
- Addressed issue where virtual Network File System (NFS) server shares intermittently fail to mount when another NFS share is assigned the same ID in a clustered environment.
- Addressed issue to add the LiveDump capture feature that will trigger a live kernel dump if requests are stuck for an extended period.
- Addressed issue where Failover Cluster Manager crashes when connecting to a cluster with a long name (15+ characters). This occurs after .NET 4.6.1 is installed.
- Addressed issue that crashes Exchange servers whenever a customer installs an Exchange cumulative or security update. Error code: STOP 0x3B
- Addressed issue that prevents the capture of network traffic when Microsoft Advanced Threat Analytics starts and stops the session that monitors traffic in promiscuous mode.
- Addressed issue where users cannot connect to wireless, proxy, and VPN authentication. The Online Certificate Status Protocol responder service intermittently returns an IIS 500 error when processing client requests. This causes the clients to fail revocation checking and fail authentication to the required service.
- Addressed issue to provide a maintenance mode for Active Directory domain controllers.
- Addressed issue where Active Directory Federation Services (AD FS) fails to authenticate external users because the ADFS proxy servers time out.


















When you are the 800lb gorilla you think you can do anything you want. Reminds me of how patients and a different mindset can drop the gorilla. For decades Sun Microsystems waited for the gorilla to ask permission to include Java in Windows. The gorilla never did and one day Sun decided that a court would determine how much millions of copies of stolen intellectual property was worth. With the settlement check in hand, Sun decided that the gorilla needed a competitor to their highly used Office product. Sun hired a slew of programmers and developed “open” office and gave it away to anyone for free. The gorilla was furious and demanded they cease and desist. The Judge decided there was no infringement and Sun could give away a product that was 100% file compatible with the gorilla’s because they did not infringe in any way on the gorilla’s copyright of the “office” program. The moral is quite simple – don’t be an 800 pound gorilla mindset when others have an 8000 pound elephant mindset.
Thank you… The moment i saw KB2952664 I was suspicious. I have always been a Microsoft person, but w8, and w10, and these suspicious ass updates are beyond forgiveness. Anyhow, I am happy that I’m not the only one that feels somewhat the same. Tyranny bullshit.
One of my PCs: unsupported hardware, i3 550 (clarkdale). A fuckin 7 years old CPU.
How idiotic is this? Off with KB4012218, fuckin imbeciles!
MS doing best to alienate/piss off everybody yet again.
I can imagine that office meeting meme:
– What should we do with Windows to make it better?
– Add ads, spyware, forced updates
– Yeah, and also piss off everybody, including Win7/8 users
– (guy near window) Maybe just make a great OS that will not piss off everyone and without stuff you proposed? (gets thrown out of the window)
Thanks I’ve included those 2 KB to my Exclusion list of MS-Spyware Malware with WSusOffline:
Here’s where are the file in WSUS: http://i.imgur.com/rIQL8EU.png
Here’s the whole list if someone need it:
kb971033
kb2952664
kb2976978
kb2990214
kb3021917
kb3022345
kb3035583
kb3044374
kb3068708
kb3075249
kb3080149
kb3123862
KB4012218
KB4012219
Why hasn’t the EU sued Microsoft for blatant discrimination against Win 7 / 8.1 users who paid for ALL Windows updates not just the updates Microsoft wants Win 7 / 8.1 users with Ryzen and later Intel CPUs to have? Microsoft’s actions are totally unreasonable, illegal and unacceptable and the EU, UK and USA should all be filing massive lawsuits against Microsoft for their violations of law which include discrimination, extortion and consumer fraud as Microsoft is NOT informing Win 7 / 8.1 users that they are being discriminated against and denied ALL Windows updates like Win 7 / 8.1 users not using the latest Ryzen and Intel CPUs are allowed to receive.
My seven year old home built dual boot computer runs Linux Mint just fine from a USB external hard drive. The last time I booted into Windows, I just felt kinda dirty.
It’s true that Microsoft has turned the Windoze O/Ss into scumware with their evil agendas. This is why consumer rights should be protected and Microsoft fined billions for their devious, unscrupulous customer abuse.
Good for you, why are you here again?
Isn’t this “ILLEGAL” purposely sabotaging a LEGALLY Bought OS specifically Windows 7/8? Here I thought the CPU’s themselves won’t work but instead Microsoft needs to patch the OS for it not to work…
Where’s the logic in that announcing latest CPU’s ain’t gonna work on Win 7/8 but still requires them to be patched thru Windows Update.
It could be (INAL) but by the time we found out through the legal system it would probably be to late, it took over 10 years for Microsoft to be found guilty of unfair practices concerning the packaging of IE into Windows and even then they got fined years later for non compliance.
By the time a court rules on whether this is legal or not Windows 7 & 8 will be distant memories.
Yes in the past but considering how technology has advanced and most people have become more tech oriented specially when it comes to debunking Windows. I think if given a number of people do push such case then it would push. But then again M$ having lots of $$$ would probably just bribe it’s way out.
I see that a few users have taken to installing these preview monthly rollups. It is disconcerting that average users do this.
On some sites, users have complained that they have compatible processors that have been snagged by the CPU checker. These being a few 2015 AMD systems and one guy on a 2015 Sky Lake processor. These systems are not the new gen systems in Microsoft’s announcement, so MS has a bit of house cleaning to do before the April cums get released. None the less, those you do not read MS announcements are in for a big surprise in April.
@ LD
Likely, M$ will pretend ignorance about the problem and just carry on as usual since M$ want to push as many Win 7/8.1 users as possible onto Win 10, ie by hook or by crook.
Welp, that’s that. Just turned off Windows Update completely. If they don’t like my inevitably becoming part of a botnet, they can stop being assholes about their updates.
@ S
Even with Windows Update turned off, users won’t automatically become part of a botnet if they practice safe-browsing(= eg no torrent downloads) and have installed an antivirus program.
Woo.! ……. M$ is now using Windows Update to stop providing updating support to certain Win 7/8.1 users.
= M$’s Windows Update is very much like a malware and/or ransomware.
Win 10 is very likely an NSA spyware.
Win 10 is already an adware.
Windows is likely going to become crapware like the < 2% market-share Win 10 Mobile in Nokia/Lumia smartphones.
.
.
.
P S – On 29 July 2015, M$ launched Win 10 and the 1-year free Win 10 upgrade offer to Win 7/8.1 users and soon after, Win 7/8.1 users began to experience very slow updating thru Windows Update, esp for those doing a fresh install.
In April 2016, many Win 7/8.1 users experienced a completely broken Windows Update. Hence, the famous fix of KB3020369 and KB3172605.
In Oct 2016, M$ introduced mandatory monthly Patch Rollups for Win 7/8.1.
In Jan 2017, Windows Update got "miraculously fixed" by M$, ie no more slow or broken updating for Win 7/8.1 users.
IOW, M$ is not your friend, esp for Win 7/8.1 users.
Blocking this won’t make any effect, this is just a preview update.
However, next cumulative update will contain this and you won’t be able to block it without blocking all the other stuff in it.
I hope this update shall not be embedded within cumulative in security only patch.
One more update to block and hide. ;)
Damn M$, it’s not AMD/INTEL whose killing Windows but you!!! Purposely patching the OS not to work on 7th Gen/above or Ryzen CPU’s!!!
any updates for KB3178690 ? causing excel 2010 to crash..
Thanks for the very comprehensive explanation of this KB’s contents, Martin.
It appeared in my Win Updates today. Although I clicked on all the support links, I found nothing but generalization and obfuscation. There was no in depth explanation of the KB that I could find AND the links just took me round in circles.
Mind you, that does not really matter because I will not be installing it.
Pretty un user friendly, I would almost say that at this point Microshaft is user hostile. Not sure where they are going with this.
step 1. change a great ui and force people to be wary of updates
step 2. piss everyone off in every way imaginable continuously
step 3 ?
step 4 profit
What does a generator have to do with processing? If you think it is a way of making my computer malfunction, for Microsoft’s benefit, then I do not want the update. I also noticed kb2952664 is offerred again as a recommended update. I do not trust it on my machine..
Yet another example of why cumulative updates are bad news for customers, when a software developer can dictate to their customers how they’re allowed to use their own hardware you know it’s time to jump ship.
Yes exactly. And I am also sure they switched to combined update rollups so they could sneak in many of their unwanted updates along with genuine improvements or fixes. It looks like I will have to give up on “quality updates” entirely and use only security updates from now on. If Microsoft try to sneak in more crap like this processor detection to block a CPU through a security update, I will stop updating entirely. Still, I won’t use Windows 10 which is a malicious, hostile piece of crap.
When you notice what M$ did by screwing easy wireless networks management as of Windows 7 in Windows 8 and onwards, you can be sure they are heading to wrong direction.
To be able to manage wireless networks easily in GUI, you are obliged to use third part programs or to stick with command prompt.
In Windows 10, you already need 3 third part programs to restore pre Windows 7 customisation :
– Classic shell starting from Windows 7 onwards
– Wireless network manager starting from Windows 8 onwards
– Windows update minitool starting from Windows 10