Blocking Telemetry in Windows 7 and 8.1
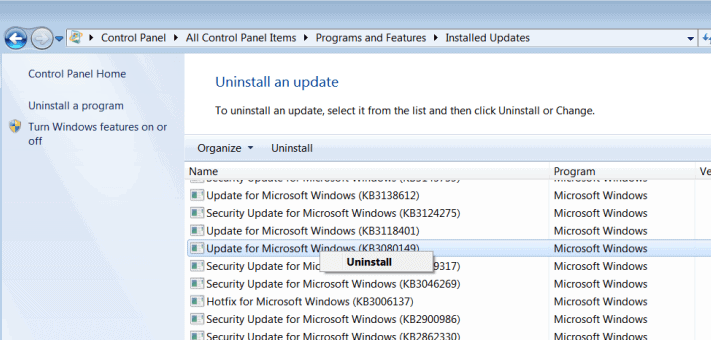
Microsoft pushed patches to devices running Windows 7 and 8.1 in recent time that collect information and transfer data to Microsoft regularly.
One of the main issues that Windows users may have with telemetry is that Microsoft does not reveal what it is collecting, and what is included when telemetry data is transferred to the company.
The following tutorial provides suggestions on limiting Windows data collecting and transferring. There is no guarantee that nothing is collected and/or submitted after making privacy related changes to the operating system, but a guarantee that data collecting is severely limited at the very least.
Information taken from various places around the Internet including this Ask Woody comment, this German forum post, and Günter Born's post.
Make sure you back up important data before you continue.
Update: Eric @ Tweakhound created scripts that you can download and run. It is recommended that you go through the scripts first before you execute them.
Blocking Telemetry in Windows 7 and 8.1

The following Windows updates are related to telemetry and diagnostic data.
- KB971033-- Description of the update for Windows Activation Technologies
- KB2952664 -- Compatibility update for keeping Windows up-to-date in Windows 7
- KB2976978 -- Compatibility update for keeping Windows up-to-date in Windows 8.1 and Windows 8
- KB2990214 -- Update that enables you to upgrade from Windows 7 to a later version of Windows
- KB3021917 -- Update to Windows 7 SP1 for performance improvements
- KB3022345 -- Update for customer experience and diagnostic telemetry
KB3035583-- Update installs Get Windows 10 app in Windows 8.1 and Windows 7 SP1- KB3044374 -- Update that enables you to upgrade from Windows 8.1 to Windows 10
- KB3068708 --Â Update for customer experience and diagnostic telemetry
- KB3075249 -- Update that adds telemetry points to consent.exe in Windows 8.1 and Windows 7
- KB3080149 -- Update for customer experience and diagnostic telemetry
- KB3123862 -- Updated capabilities to upgrade Windows 8.1 and Windows 7
You can remove any of the patches using two methods:
- Tap on the Windows-key, type Windows Update, and hit the Enter-key.
- Select Installed Updates on the window that opens.
- Right-click on updates and select uninstall to remove them from the system.
Second method uses the command line instead:
- Tap on the Windows-key, type cmd.exe, hold down Shift and Ctrl, and hit the Enter-key. This opens an elevated command prompt.
- Use the command wusa /uninstall /kb:3080149 /quiet /norestart to remove updates.
- Replace the number after kb: with the update that you want to remove.
Make sure you hide any update that you have removed, as it will be picked up by Windows again the next time Windows Update checks for update.
The Windows\System32\CompatTel folder
The CompatTel folder is still there after you remove the telemetry updates on the machine. One change that you may notice is that the older Telemetry client, diagtrackrunner.exe is in that folder, and not the newer compattelrunner.exe.
You cannot remove the folder or files directly, as you need ownership first for that.
Turn off the Customer Experience Improvement Program
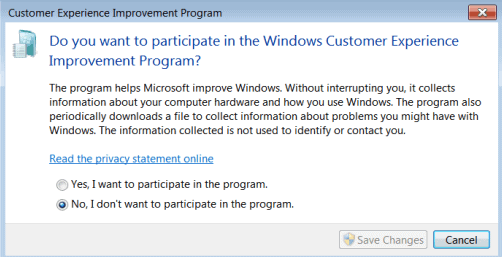
We have posted a tutorial already that explains how to turn off the Customer Experience Improvement Program.
Basically, what you do is click on Start, type customer experience, and select the "change customer experience improvement program settings" result. Select "No, I don't want to participate in the program" when the new settings window opens.
Remove the Telemetry service
Next thing on the list is to remove the Diagnostic Tracking service. It may not exist anymore already, but I suggest you run the commands below just to make sure.
Open an elevated command prompt -- if it is not still open -- and run the following commands:
- sc stop Diagtrack
- sc delete Diagtrack
The first command stops the Diagtrack service, the second deletes it.
Blocking Microsoft Servers
Caution: Some servers and IP addresses may be used by other Windows services. If you notice that some are not working anymore, disable them one by one until you find the culprit that you need to exclude from the blocking.
Note: the following servers cannot be blocked using the hosts file. You need to block them using another means, e.g. router firewall or installed firewall.
- onesettings-hk2.metron.live.com.nsatc.net
- onesettings-bn2.metron.live.com.nsatc.net
- onesettings-cy2.metron.live.com.nsatc.net
- vortex-hk2.metron.live.com.nsatc.net
- vortex-db5.metron.live.com.nsatc.net
Other servers you may want to block:
- 134.170.30.202
- 137.116.81.24
- 204.79.197.200
- 23.218.212.69
- 65.39.117.230
- 65.55.108.23
- a-0001.a-msedge.net
- choice.microsoft.com
- choice.microsoft.com.nsatc.net
- compatexchange.cloudapp.net
- corp.sts.microsoft.com
- corpext.msitadfs.glbdns2.microsoft.com
- cs1.wpc.v0cdn.net
- df.telemetry.microsoft.com
- diagnostics.support.microsoft.com
- fe2.update.microsoft.com.akadns.net
- feedback.microsoft-hohm.com
- feedback.search.microsoft.com
- feedback.windows.com
- i1.services.social.microsoft.com
- i1.services.social.microsoft.com.nsatc.net
- oca.telemetry.microsoft.com
- oca.telemetry.microsoft.com.nsatc.net
- pre.footprintpredict.com
- redir.metaservices.microsoft.com
- reports.wes.df.telemetry.microsoft.com
- services.wes.df.telemetry.microsoft.com
- settings-sandbox.data.microsoft.com
- settings-win.data.microsoft.com
- sls.update.microsoft.com.akadns.net
- sqm.df.telemetry.microsoft.com
- sqm.telemetry.microsoft.com
- sqm.telemetry.microsoft.com.nsatc.net
- statsfe1.ws.microsoft.com
- statsfe2.update.microsoft.com.akadns.net
- statsfe2.ws.microsoft.com
- survey.watson.microsoft.com
- telecommand.telemetry.microsoft.com
- telecommand.telemetry.microsoft.com.nsatc.net
- telemetry.appex.bing.net
- telemetry.appex.bing.net:443
- telemetry.microsoft.com
- telemetry.urs.microsoft.com
- vortex.data.microsoft.com
- vortex-sandbox.data.microsoft.com
- vortex-win.data.microsoft.com
- watson.live.com
- watson.microsoft.com
- watson.ppe.telemetry.microsoft.com
- watson.telemetry.microsoft.com
- watson.telemetry.microsoft.com.nsatc.net
- wes.df.telemetry.microsoft.com
Deleting Scheduled Tasks
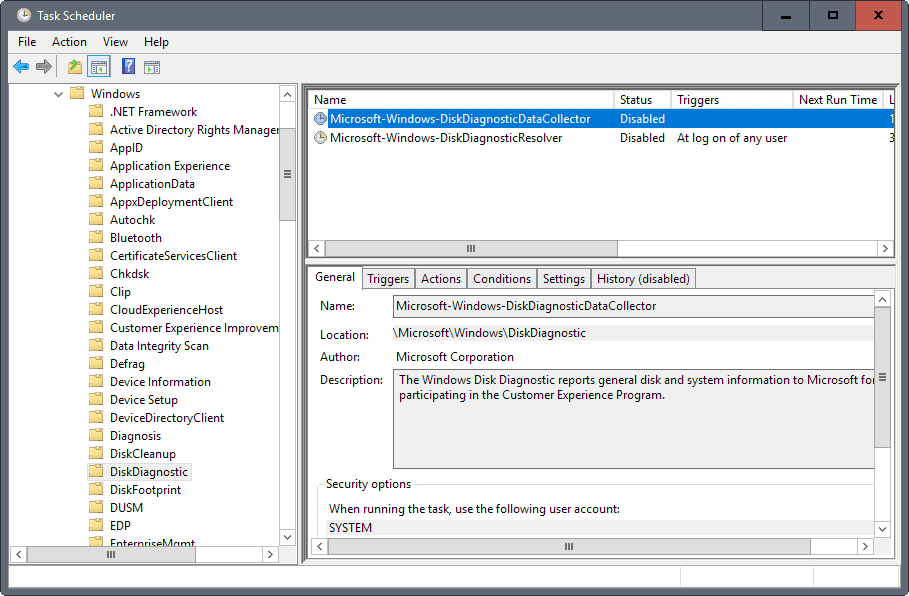
Windows 7 and 8.1 run a lot of tasks that send data to Microsoft.
- Tap on the Windows-key, type Task Scheduler, and hit the Enter-key.
- Navigate to Microsoft > Windows in the task hierarchy, and delete (or disable) the following tasks:
- All tasks with Application Experience.
- All tasks with Autochk.
- All tasks with Customer Experience Improvement Program.
- DiskDiagnosticDataCollector under DiskDiagnostic.
- WinSAT under Maintenance.
- Deactivate all Media Center tasks.
Closing Words
There is always the chance that new updates will add new services or tasks. This is why it is recommended to set Windows Update to inform but not download and install automatically.
Now You: Have anything to add? Let us known in the commands.


















Here’s an updated article about neutralizing telemetry with a batch script updated 2019-12: https://www.askwoody.com/forums/topic/2000012-neutralize-telemetry-sustain-win-7-8-1-monthly-rollup-model/
would be really great if this article could get a 2020 update. Another telemetry “attack” came with the MS Nov. 2019 update, even if you´ve downloaded the “security-only” version.
Is anyone installing the Monthly Quality Rollups? I installed fresh win 7 x64 and updated only important updates (omitting telemetry listed above) I then hid the latest rollup (October). Then WU lists the previous month’s rollup, which i hide, then repeat for the previous rollup.. . after about 10 times doing this individual important security updates start appearing (ones i never saw in the initial 100 plus updates) I wonder if this is a way to update w/o using the rollup?
some comments above say that one should DISABLE things in
Administrative Templates\SYSTEM\Internet Communication Management
But on my Win7 the setting in question says, “Turn off Windows Customer Experience Improvement Program”
This should mean that, if the State is Enabled, then “Turn off” has been enabled = it’s off
while if Disabled = “Turn off” has been disabled = it’s on
That is, DISABLE means “opt-in”!
This could be confusing and you may want to read carefully what Local Group Policy Editor says
Microsoft has a new IP address range, or at least newly discovered to me. I keep a pretty close eye on my connections, and today discovered (with TCP-UDP Endpoint Viewer), that I was connecting to Microsoft again. The Range is 52.96.0.0 – 52.255.255.255
mmm.. looks like the post forgot about the group policy settings. (gpedit.msc)
go to group policy -> computer configuration -> administrative templates -> system -> internet communications.
Then killing most of those too.
I apologize for machine translation.
I delivered lock of the following servers in firewall
onesettings-hk2.metron.live.com.nsatc.net
onesettings-bn2.metron.live.com.nsatc.net
onesettings-cy2.metron.live.com.nsatc.net
vortex-hk2.metron.live.com.nsatc.net
vortex-db5.metron.live.com.nsatc.net
Win 8.1 ceased connection with the Internet stopped
I resolve in firewall – the Internet starts over again working
https://pastebin.com/fD4Y1AUc
¿Is that script safe? ¿Already tested?
Hi Martin,
I’m doing step by step your suggestion and I removed Scheduled Task and Telemetry services.
I checked my system (Win7Sp1-x64) for KB you listed, but there are some I don’t find:
KB2976978 — KB3022345 — KB3035583 — KB3044374 — KB3075249 — KB3123862.
I hope it is not a problem, but can you suggest some reason for this “missing”?
Any help will be welcome.
Hi, Pici
couldnt find many of the telematry entries,how to run command promt,task scheduler was empty and not as shown in image, also , windows somehow deleted some of my important data and softwares, i dont suspect virus, it also tricked me to delete temp folder, what to do?
Beautiful, been doing this for years and years, but one hell of an article too bad there’s no simply patch updated constantly to do these changes.
Those with Pro/Ultimate etc. Windows editions.. Might also wanna check gpedit.msc locate both:
Computer-/User Configuration
Rules for:
Administrative Templates\SYSTEM\Internet Communication Management
Disable everything except maybe for auto update certificates and access to Windows Update (Computer Configuration).
Since there is absolutely nothing none of those services, tasks do that is useful.
I admire the diligence shown here, going to ever increasing lengths to block the Microsoft spy machine.
Realizing that this would be an endless task, I opted out a long time ago as I have better things to do with my life.
I would definitely recommend you spend some of this effort trying out Linux. It’s legally free & does not have a corporate spy machine behind it that attempts to make up for loss of license revenue by selling their own customers private data. In win10 everything you do is reported back by default – not merely the web-sites you surf.
I have absolutely no regrets about my switch.
I accidentally installed KB3133977, and since I have an Asus motherboard, and it killed my boot. I eventually got my computer started up again and uninstalled the update but now my computer still gives me the message, if I turn secure boot back on, as if the update was still installed even though I can see it in my hidden updates. Has anyone else had this problem?
It is nice to have all this information in one site.
Does anybody know if there is a search option within the Windows Important Update List? The only search option is located within the navigation bar. However, it only search apps within the control panel. It will be nice if a Find text option within the UI screen was incorporated to it. I wonder why Microsoft did not include this option?
Without it, it will be hard to find what updates have to be hidden in the list. Specially if you have almost 200 important updates pending in a new Windows 7 Install…
You can uninstall updates from the command line easily, see: https://www.ghacks.net/2015/04/17/how-to-remove-windows-10-upgrade-updates-in-windows-7-and-8/
Hi,
took script from here: https://tweakhound.com/2017/02/11/blocking-windows-7-telemetry/
and I adopted it to the KB list from above:
REM :: BlockGWXetcV6.bat
ECHO OFF
SETLOCAL
REM — uninstall updates
echo uninstalling KB971033
start “title” /b /wait wusa.exe /kb:971033 /uninstall /quiet /norestart
echo done, uninstalling KB2952664
start “title” /b /wait wusa.exe /kb:2952664 /uninstall /quiet /norestart
echo done, uninstalling KB2976978
start “title” /b /wait wusa.exe /kb:2976978 /uninstall /quiet /norestart
echo done, uninstalling KB2990214
start “title” /b /wait wusa.exe /kb:2990214 /uninstall /quiet /norestart
echo done, uninstalling KB3021917
start “title” /b /wait wusa.exe /kb:3021917 /uninstall /quiet /norestart
echo done, uninstalling KB3022345
start “title” /b /wait wusa.exe /kb:3022345 /uninstall /quiet /norestart
echo done, uninstalling KB3044374
start “title” /b /wait wusa.exe /kb:3044374 /uninstall /quiet /norestart
echo done, uninstalling KB3068708
start “title” /b /wait wusa.exe /kb:3068708 /uninstall /quiet /norestart
echo done, uninstalling KB3075249
start “title” /b /wait wusa.exe /kb:3075249 /uninstall /quiet /norestart
echo done, uninstalling KB3080149
start “title” /b /wait wusa.exe /kb:3080149 /uninstall /quiet /norestart
echo done, uninstalling KB3123862
start “title” /b /wait wusa.exe /kb:3123862 /uninstall /quiet /norestart
echo done, finished uninstalling telemetry updates
echo next, block OS upgrades (in case GWX comes back)…
REM — Block OS upgrade
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\GWX /f
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\GWX /v DisableGWX /t REG_DWORD /d 00000001 /f
echo finished…Disabling CEIP…
REM — Disable Customer Experience Improvement Program
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\SQMClient\Windows /v CEIPEnable /t REG_DWORD /d 00000000 /f
—–
And then I also disabled following scheduled tasks: \Microsoft\Windows\Autochk\Proxy, AitAgent, ProgramDataUpdater
And following windows service disabled: Diagnostics Tracking Service (DiagTrack)
The C:\Windows\System32\CompatTel\diagtrackrunner.exe should be removed via uninstall of one certain KB file, otherwise one has to change the file owner (or what I sometimes did in the past: use killbox to force removal on reboot)
This might valid for Win 7 only.
(sorry for in case of double post)
To me it’s still fascinating that Microsoft is trying so hard to force the users into the updates. I guess in the the near future you have to upgrade to Win 10 and its “Windows as a Service” mentality. Just read about it at https://microsoft-windows-10.com/everything-you-need-to-know-windows-as-a-service/ and still not sure if this is the way to go.
What is your biggest concern about the forced updates? I mean, why are you avoid most of them with so much afford?
Thanks for this article. I tend to track what’s running and I know what I install, so I was pretty alarmed when 7 or 8 new services started running this morning, Telemetry being most noticeable.
I appreciate your solutions. Got them under control AND deleted a few additional thx to your Task Manager section. :D
To block MS Servers i strongly suggest WindowsSpyBlocker : https://github.com/crazy-max/WindowsSpyBlocker
So much time and effort being expended by so many people trying to keep Windows secure and private.
The solution is simple. Dual boot Windows and Linux (Mint in my case).
Keep Windows off the Internet (Network adapter disabled) and only use Linux online. I have Windows 7 at SP1 level only and it runs all of my Windows programs perfectly. No need to worry about updates or having to run antivirus, antimalware, etc.
I’m doing this too. I’ve taken my home Win 7 workstation offline entirely. It runs peripherals like scanners, printers and other devices, and still has software that is useful – but it no longer surfs. I built an older Toshiba Tecra M2 with a Mint distro and use this for email and web access. Anything I need to transfer is done by flash drive and the contents are screened by manually updated AV apps. Simple and it works.
Look for more people building function-specific dedicated Linux builds on older systems. Like a Raspberry Pi as a dedicated audio/video streamer. And old hardware is plentiful and cheap. If the initial config is simple, rebuilding it on occasion is simple too.
Hi Guys,
After doing this above tricky block ,Does this update will reappear if Microsoft will again push for update ?
Thanks
Updates will re-appear when Microsoft releases an update version.
Martin, by turning off automatic updates and using WSUS offline and picking the “security only” updates, will that avoid these unwanted KBs from being installed again?
Yes that should prevent the installation.
Thanks martin.. but bad habit of MS.
You’re doing Odin’s work here, son. Thanks a lot für the detailed explanation and helpul article!
Installed KB2952664 again today after having it installed previously.
After it was installed and the system rebooted…
Diagnostic Tracking Service was still disabled (as I had set it)
The Customer Experience Improvement Program setting was still set to No (as I had set it).
No new tasks were added to Task Scheduler, and the tasks that are related to CEIP remained Disabled (as I had set them).
No new processes were started.
To sum up, no changes from before.
So it seems the hypothesis about KB2952664 “snooping” is more science fiction than fact.
Alternatively, insert the Windows 7 SP2 disk, install from scratch, and turn off automatic updates. Sadly, this is notably safer than allowing Microsoft any access to your computer whatsoever any longer.
> Deleting Scheduled Tasks
> …
> 8. Deactivate all Media Center tasks.
What “Media Center” tasks?
I have none, which actually might be good i suppose.
Other than that, awesome guide, did everything else, thanks!
I use Ancile. It’s updated regularly. Read the ghacks article here:
https://www.ghacks.net/2016/09/12/ancile-block-spying-on-windows-7-and-8/
Hello Martin,
Thank you for this excellent overview, and for sharing it with Woody Leonhard’s readers at AskWoody.com — a wonderful example of collegiality (that will hopefully inspire others)!
Regards,
AJ
You might want to check C:\ProgramData\Microsoft\Diagnosis\ETLLogs\AutoLogger\AutoLogger-Diagtrack-Listener.etl
If the ADL is present you can disable it via these registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\WMI\Autologger\AutoLogger-Diagtrack-Listener
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\WMI\Autologger\AutoLogger-Diagtrack-Listener\{DD17FA14-CDA6-7191-9B61-37A28F7A10DA}
‘Modify the Enabled key to 0 (zero) to disable it for both.
Once you’ve done that, you can delete the AutoLogger-Diagtrack-Listener.etl
How to exclude Windows Updates with WSUS Offline Update:
Just follow my tutorial: https://justpaste.it/WSUS_OfflineExcludeUpdates
Enjoy ! 😺
MS says Win7 is outdated – not like Win10. These telemetry updates turn Win7 into spyware – like Win10. They’re just MS’s way of proving its point.
Thanks.
But there are another group of software (indispensable?) that collect too much info from users and require an internet connection: protection software. And this is a paradox too. Privacy goodbye.
PS: only for people who like to read EULA of internet security… :-)
Yeah, it’s hard to find the proper tool that fits all requirements nowadays.
Good grief thats a lot of calling home.I havent used windows for 2 years now as i am a confirmed linux user and it seems microsoft has slowly got worse,
Glad i dumped it with all that crap going on.
The amount of hoops a user needs to go through for any type of security and privacy on Windows is absolutely insane. At some point, users need to ask themselves what keeps them on Windows. I think there needs to be a valid reason why anyone would subject themselves to this kind of behavior in their daily lives.
I use to spend loads of time securing XP, Windows 7. I don’t think I could effectively manage the privacy and security issues built into Wiindows anymore. It’s completely out of control. I had switched to Linux a few years ago but briefly considered switching back to Wiindows 10 but read about the built-in spyware and data-mining when it was released.
I’m not advocating a move to Linux (or other) here. Use what you want. I’m suggesting that Microsoft and others need to be called out on a regular basis on every single tech article, they need to see this issue resolved in the courts. This behavior is beyond insane and it just keeps on getting worse.
@John,
They need to be called on every single tech article, they are once in a while, never on a regular basis, and far from every tech article, indeed. But should it be would remain the fact that non-tech medias never, or hardly never mention these “beyond insane” practices of those worldwide companies dominating the Web. Most users consider the Web and their connected devices as a tool, and they are right, many conceive this tool as a basic TV that you set once and for all and forget to maintain afterwards. Fortunately security and privacy are starting to concern more and more, but the mental scheme is binary, with the good guys one one side and the bad guys on the other. The bad guys are those who infect the Web and all end-users, the good guys include those major companies with insane practices because they communicate a lot on users’ security and privacy, and of course never mention their inquisitive policies and when they do it is to explain that this behavior is required for users’ safety …
Those companies, though private, are more and more perceived as “out of copyright” because they hold the whole system, the Web system anyway, it’s as if they are constitutive of the modern era. In the same way we call a refrigerator a frigidair (in France anyway) when “Frigidair” was the leading company in that sector, in the same way these leading Web and computing companies are now part of our lives in such a way that they are more than, beyond their private status. Was a time here in France when naming “Facebook” on a public media was considered as promoting, advertising. No longer.
So, yes, this presumptuousness must be countered. Not sure if it’s not already too late. Those of us who feel concerned and have the time (and aptitude) to reserve energy for a computer maintenance are a tiny minority, I’m afraid. You can’t help people if they don’t ffeel concerned or if, worse, they don’t care.
I can secure my Windows computer in just a few steps. The thing that takes times is to figure out how, but that only occur a couple times over the life of a computer, namely when the OS is first released or you have to change a key element in your setup such as the firewall.
That said I agree, law will have to get involved to enforce proper opt outs. Special mention to Facebook which is possibly the worst offender both in scale and data type. I rarely see it mentioned here.
@Frank
You write…
Maybe you can enlighten the rest of us and share your knowledge on securing Windows computers “in just a few steps”?
Well Frank, what you do is take a “few steps” to the wall and unplug your computer.
What are those “few steps”?
1. Find a good firewall. Takes time, mostly a one time chore. A good firewall is very thorough and flexible. (I have to change mine due to changes in the firewall market so I can’t give advice, sorry. My current firewall brand has served me well for probably a decade and two OS versions, but it is time to change.)
2. Configure it so it blocks everything. One time chore, takes from a few minutes to an hour depending on firewall UI and your habits and knowledge.
3. Enable select features, like WiFi handshakes and Time sync. One time chore, can take some time unless there exist guides somewhere. Otherwise resources on protocols like good old Wikipedia coupled with firewall logs. If you never did that it’s a chore, but when you know what’s up it’s technically just setting less than 10 rules.
4. Allow non-Microsoft programs like browsers or IMs as needed. It’s extremely fast to do because you don’t make spot-on rules like in 3. You can if you care or are using software from privacy invasive company like Google, but we are talking about protection against Windows’ embedded spying here
5. Update Windows manually using the new update bundles, it should be one single download each month obtained from the browser.
6. Optional: Disable telemetry and other crap if you want to regain some computer resources, but that’s not required since they can’t phone home.
Maybe you can enlighten the rest of us and share your knowledge on securing Windows computers “in just a few steps”?
I’ll never understand the blacklist stance regarding Microsoft programs communicating with the web. Just block everything and use a whitelist instead if you need to allow something.
Programs that can access the internet are mostly browsers or IMs, not Windows. Don’t waste your time building complex blacklists that can never catch it all: Block everything, whitelist what you know is fine when you need it.
Sure, I’ve tried the whitelist approach (block everything by default, then grant access as needed) once. But only for a brief time!
I very soon got fed up with the result: spending half my time with error messages, all kinds of unexpected program failures, and adjusting firewall settings again and again.
So no, I don’t feel this is a sensible solution, unless perhaps you use just a very limited and never-changing selection of software.
I’ve been doing that for at least 10 years without problems. When you install a new program that requires internet, you can just allow it if you like: It’s not Windows shit. You don’t need to setup complex rules if your goal is to block Microsoft, just spend 30 seconds to allow the new program you installed and from then you can use it normally without ever having to deal with its firewall settings :)
Absolutely correct. The ‘block all’ is the only sane way to do any real security. The problem is that Microsoft has historically used DLLs and other support executables to perform certain functions. Lots of these support files are arcanely named. If you kill access to a library because of telemetry, you might also kill access to essential Windows functions – as these libraries are reused by various programs.
You don’t kill access to a library that’s on your own computer, you kill the ability of Windows to send data outside. You can let all the telemetry shit run on your computer if you like, it’s only a computer resource issue if they can never report back to Microsoft.
There’s probably a whole bunch of KB2952664 versions on a telemetry-infected system.. Somewhat cumbersome to get rid of them all:
elevated command prompt enter: wusa /uninstall /kb:2952664 /norestart
elevated command prompt enter: dism /online /get-packages | findstr KB2952664
This pulls up all KB2952664 packages.
To remove them, again from an elevated command prompt enter:
dism /online /remove-package /PackageName:Package_for_KB2952664~31bf3856ad364e35~amd64~~6.1.1.3
This removes version 6.1.1.3 only.
On machines that also have versions 6.1.0.12, 6.1.3.0, 6.1.7.4, 6.1.8.2, etc. etc.
this command must be repeated with the appropriate version numbers.
Once all versions are processed, run: dism /online /get-packages | findstr KB2952664 again,
and if it doesn’t return any packages, KB2952664 is gone
Great! I would add this one too:
KB3184143 – Remove software related to the Windows 10 free upgrade offer
https://support.microsoft.com/en-us/help/3184143/remove-software-related-to-the-windows-10-free-upgrade-offer
If you don’t have any of those installed (or manually removed all of them) then it’s redundant and better to avoid.
Where did this list come from, do you have a source for it? And have you checked to see what you’re actually recommending people block? For example, I know that watson.telemetry.microsoft.com and watson.telemetry.microsoft.com.nsatc.net is used by Windows Defender for virus analysis.
Tell me you don’t actually let Windows Defender lounge around, smoking cigars and drinking martinis within your system do you? It’s sort of like saying, “Hey, I’m going to install this program that’s never ONCE, stopped a single viral, malware, trojan, or anything else that harms people’s computers, because these people who lie through their teeth 24-7-365 told me I should.”
Of course I’m trying to bring light to the matter Tim, but investigate that thing, then shut off, block it, disable it, kill it, smash it with a digital hammer, pour water on the circuitry it’s running through, and chase it all the way out of your yard.
I add a note that this may interfere with other Windows services.
Tom: NirSoft’s IECacheView is excellent. You can delete, (See his site for details), (and I use ccleaner).
One update slipped through the net which I have uninstalled now.
As I have never touched the Windows firewall could someone please tell me how to block the MS servers. Thanks in advance.
Thanks martin for yet another excellent tutorial in how to thwart MS telemetry.
‘MS servers’ is a wide denomination.
MS servers dedicated to tracking are mentioned in the article, perhaps a tougher approach even with,
– WindowsSpyBlocker : https://github.com/crazy-max/WindowsSpyBlocker
– Ancille : https://bitbucket.org/matthewlinton/ancile/
– BlackBird : http://www.getblackbird.net/
– Destroy-Windows-10-Spying – https://github.com/Nummer/Destroy-Windows-10-Spying
I’d advise caution, except for WindowsSpyBlocker, because some settings (block/removable) may be arguable, IMO.
Here I don’t run the scripts and batch processing provided by the above mentioned sites, but rather extract IP ranges and urls then add the former to a personal filters list I add to the PeerBlock application and the latter to a domain blocking blacklist I use with DNSCrypt-Proxy.
Concerning PeerBlock and your question, wybo, if you,
– install the application (free), available at https://code.google.com/archive/p/peerblock/
– add a dedicates Microsoft blocking list available at https://www.iblocklist.com/lists (see ‘Microsoft’ in the list on that page),
then you should have most of Microsoft’s servers blocked, but that means harmless servers as well : only if you’ve decided to ban Microsoft, totally, which is a very personal choice, mine as well need to say. I wouldn’t advise to ban whatever company except dedicated ad/tracking servers. My choice is a blend of efficiency and deep irritation, not at all a calm way of proceeding. But I’ve had it with Microsoft.
@dark, the site/page you mention is interesting and indeed includes Windows (10) Anti-Spy filters, both as HOSTS filters (urls) and as PeerBlock filters (IP ranges).
But the PeerBlock IP Blocklist is dated 8/30/2016, when that list is updated regularly at iblocklist.com …
As for the Hosts version it goes back to 11/22/2016
IPs are more delicate than urls because they may be subject to changes …
There is updated Peerblock Microsoft IP Blocklist list here: https://encrypt-the-planet.com/windows-10-anti-spy-host-file/
@wybo, a 404 on the peerblock link? I get the page correctly. try again or reconsider your DNS server!
OK. Thanks Tom. Although it seems all a tad complicated. I think I can manage that.
PS got a 404 on the peerblock link.
Excellent, Martin. Personally I go even further, but the essentials are all in your article.
Telemetry relates to privacy and another Windows (7 Up or did it start with Vista?) is the infamous Webcache folder which collects the user’s history and is problematic to clean, another Microsoft fantasy.
If you wish to be able, more than to empty that folder but to stop Windows from filling it up in the first place, then have a look at the article which explains how to proceed. Works for Win10 as well as for Win7. I just cannot stand not being able to empty a cache, especially Windows’ …
Disable WebCache : https://www.tenforums.com/general-support/37841-disable-webcachev01-dat.html#post_538631
Works great here. WebCache folder no longer gets whatever. Empty, zero bytes, the end (yours) my friend (because I remain polite) Microsoft.
Beware, what is mentioned in the article includes editing the Registry and as such requires attention. AVOID if you don’t know what you’re doing. If you do know then the method is radically efficient.
I followed these steps to disable WebCache… unfortunately, this causes explorer.exe to crash on every startup.
On the events viewer i can see the following error:
Faulting application name: Explorer.EXE, version: 6.3.9600.17667, time stamp: 0x54c6f7c2
Faulting module name: twinui.dll, version: 6.3.9600.17415, time stamp: 0x54503c45
Exception code: 0x80270249
…etc
So, i’d advice not to do this. Instead, i did moved/symlinked the WebCache folder to a RAMDisk, so it doesn’t mess with my SSD.
(ps: explorer.exe auto resumes itself, so you may don’t notice the crash beyond an increased startup delay)
@diegocr, all I can say is that I’ve experienced no issue myself, here with Win7 64-BIT, that I don’t use Outlook as Albert McCann above. Not sure twinui.dll is in whatever way related to this WebCache, Anyway for anyone such as me who avoids built-in Windows applications, no problem, but otherwise, as Albert and maybe as yourself, it may be likely that Windows does call this WebCache for its own applications. It’s always the same scenario : if you use Windows and a given (Outlook i.e.)/some/all its components out of the box then think twice before tweaking its spaghetti coding, from the registry to the files.
I tried the disabling WebCache things, and that kills the ability of Microsoft Outlook from displaying any web hosted HTML content. :-( Putting the registry entries back, and restarting the task then allows Outlook to properly display HTML emails.
A perfect example of the way Microsoft tightens up everything, linking and building as a spider.
What is the purpose of this Webcache, to serve Microsoft products (as Outlook) or to serve Windows globally?
If Outlook requires that cache then MS should make that cache specific for its products. That’s the core of the company, link as much as they can between what serves the user and what serves them. Pathetic.
There is NO reason for a cache to be out of the user’s control. It’s always possible to clear that Microsoft WebCache manually but it’s a bit problematic and never feasible automatically. Should it have been easy, obvious as it is everywhere else than in MicrosoftLand I wouldn’t have searched to disable that cache in the first place. It’s always been a Microsoft obsession, to control Windows caches, it bothered me and many for years with XP … got worse with Seven, wonder how it’s uncured with Win10 …
Thanks for reporting this internal to Microsoft issue, Albert. Good thing you managed to reverse the process (the how-to mentioned deleting those reg entries). And good thing I added in my previous comment to always be cautious with Registry manipulation.
This looks superb, Martin. Thank you so much!