Disable Microsoft Windows Malicious Software Removal Tool Heartbeat Telemetry
If you have the Microsoft Windows Malicious Software Removal Tool installed on your machine, either by having installed it manually or because it shipped with Windows, you may have noticed already that it is sending out so called Heartbeat Reports after certain scans.
These reports are not linked to any of the major telemetry services or tasks that you may or may not have disabled on your machine.
On Windows 10, the Heartbeat report gets sent out to Microsoft even if you have disabled the Customer Experience Program and the majority of other telemetry related services or tasks, and made sure to set all privacy related settings to maximum privacy.
How to disable Heartbeat Telemetry

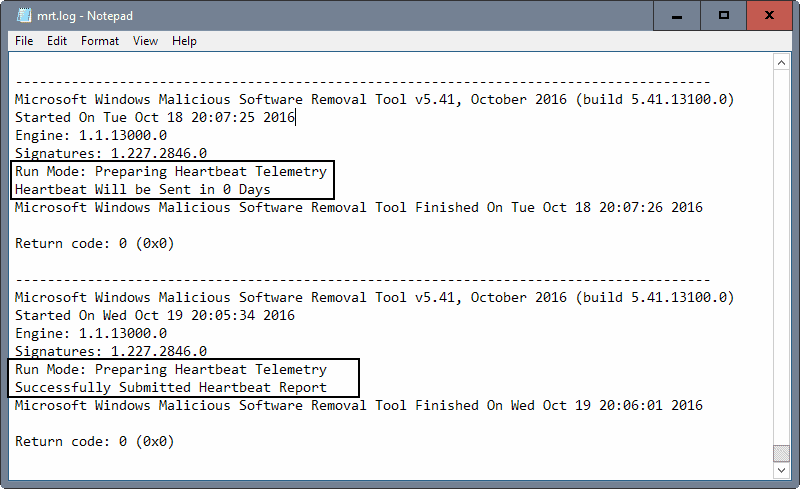
First thing you may want to do is check whether the installed copy of the Windows Malicious Software Removal Toll (MRT) sents Heartbeat telemetry reports.
The easiest way to check that is to load the MRT log. Open File Explorer or Windows Explorer on your Windows machine, and load the following by pasting it in the address bar and hitting the Enter-key: C:\Windows\debug\mrt.log
This opens the MRT log. Scroll down to the last entries and check for Heartbeat Telemetry there. You may also hit F3 to open the search to jump to the first Heartbeat entry in the log.
Heartbeat Telemetry data is not sent out each day according to the log, but only every five or six days. You can verify that in the log as you will find "Heartbeat Will be Sent in x Days" entries there.
Microsoft notes in its privacy statement that the Malicious Software Removal Tool will sent a report to Microsoft with "specific data about malware detected, errors, and other data about your device" but fails to go into details.
We don't know what is sent to Microsoft as part of Heartbeat other than the information that Microsoft revealed in its privacy statement.
Option 1: Registry Key
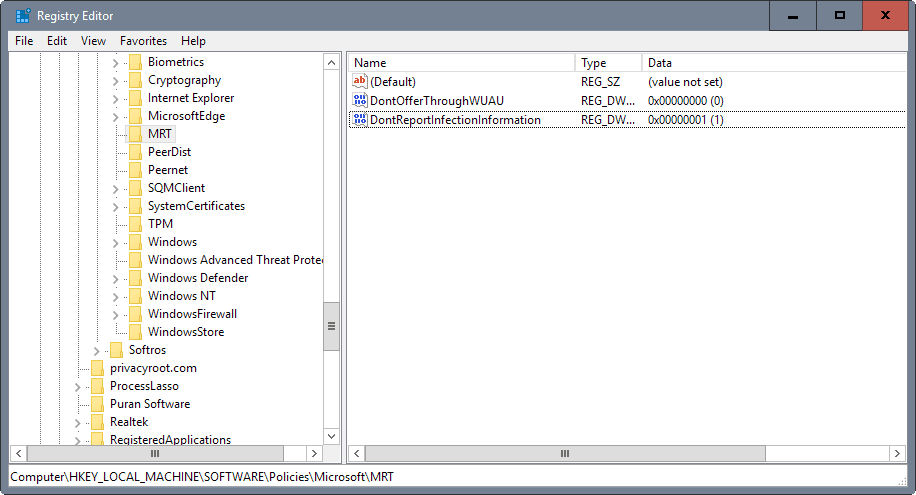
The Knowledgebase support article KB891716, Deployment of the Microsoft Windows Malicious Software Removal Tool in an enterprise environment, lists a Registry key to block the sending of reports of the MRT to Microsoft.
An administrator can choose to disable the infection-reporting component of the tool by adding the following registry key value to computers. If this registry key value is set, the tool will not report infection information back to Microsoft.
Subkey: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT
Entry name: \DontReportInfectionInformation
Type: REG_DWORD
Value data: 1
Note: Since Heartbeat is only triggered when automatic scans are run, it is too early to say if setting the key disables the sending of reports completely. I will monitor the situation and will update the article with my findings later.
- Tap on the Windows-key, type regedit.exe and hit the Enter-key.
- Navigate to the key: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT
- Right-click on MRT and select New > Dword (32-bit) Value from the context menu.
- Name the name Dword DontReportInfectionInformation
- Double-click the newly created Dword and set its value to 1.
Option 2: Disable the MRT Task, or Disable Heartbeat Telemetry
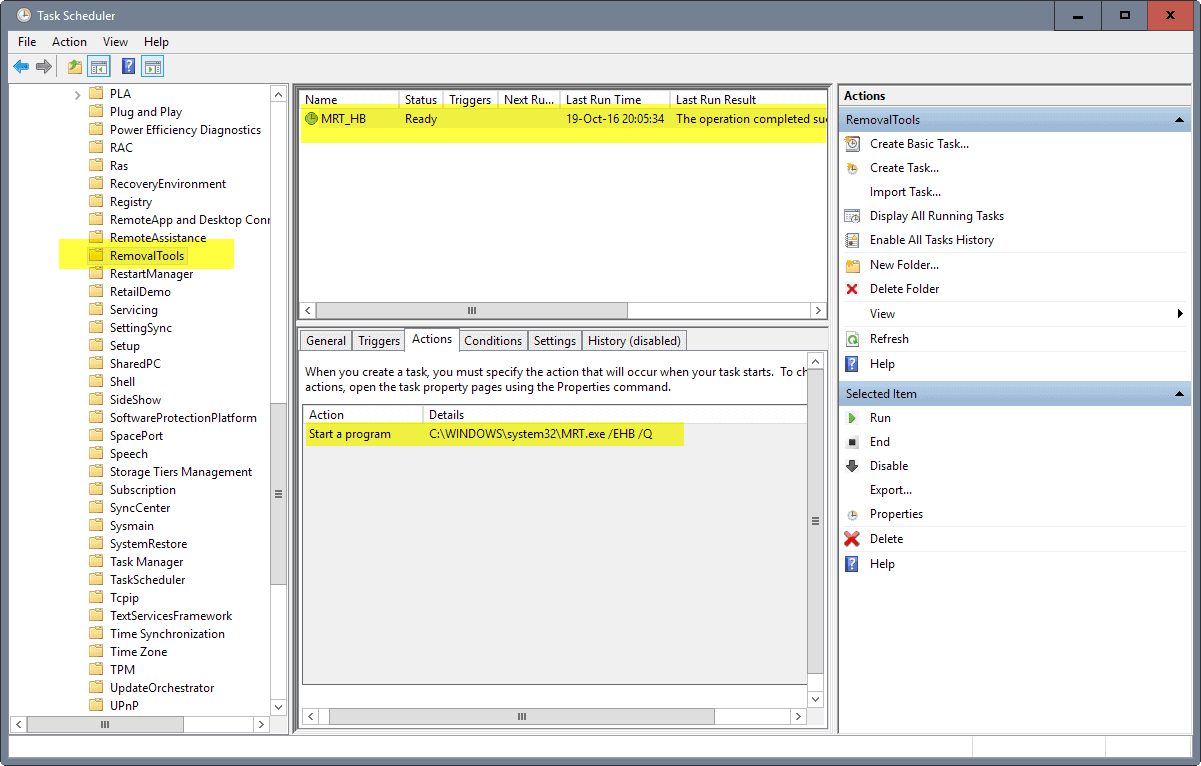
Since MRT is run automatically, it must be triggered somewhere. If you check the Task Scheduler for MRT related tasks, you will eventually find the one task that Windows uses for that.
Note: Disabling the task disables automatic MRT scans on the system. Make sure you have proper antivirus software installed on the device.
- Tap on the Windows-key, type Task Scheduler, and hit the Enter-key.
- Use the sidebar folder structure and go to Task Scheduler Library > Microsoft > Windows > RemovalTools.
- Right-click on MRT_HB and select disable from the context menu.
If you compare the last run time with the Malicious Software Removal Tool log, you will notice that they match. Also, the _HB part is a strong indicator that this is what is triggering the Heartbeat reports.
If you check the command switches used, you will notice the undocumented switch /EHB. You could remove the switch from the command to keep automatic scans without Heartbeat report generation enabled.
I verified that /EHB is indeed the trigger for Heartbeat Telemetry. If you remove it, no Heartbeat reports are created when the scan runs.
You may need to check back regularly though as Windows Updates may replace the custom task with the default one.
Now You: Did the Microsoft Windows Malicious Software Removal Tool send out Heartbeat Telemetry reports on your machine?


















Does anyone know if “TronScript” (this is virus removal tool) disables Heartbeat Telemetry of “Microsoft Windows Malicious Software Removal Tool “…Malwarebytes found two infected registry keys(Potentially Unwanted Modification (PUM) that was modifite..
I want to know If Tronscript changed it(than its okay),
but if not it was a virus right?
Registry path was First:
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\MRT\DONTREPORTINFECTIONINFORMATION
Second path:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT\DONTREPORTINFECTIONINFORMATION
MRT is a malicious program itself. It runs itself without my permission, and I haven’t yet been able to get rid of it. No, I’m not going to meddle with my registry. Microsoft needs to get their heads out of the sand and start doing their job.
Running programs that slow down system startup without permission and not providing security updates for Windows 7 are unacceptable.
“Note: Since Heartbeat is only triggered when automatic scans are run, it is too early to say if setting the key disables the sending of reports completely. I will monitor the situation and will update the article with my findings later.”
Isn’t three years enough monitoring?
Not sure where (all) it has been mentioned, but there’s a -seemingly- GREAT new(ish) tool, for privacy – which works across a number of Windows versions – WPD, https://getwpd.com/
(Please check their README.txt for information on what gets modified!..:))
Does MRT.exe ‘grow’ over time? I noticed it’s now 141MB even though a fresh download is only 56.5MB according to https://www.microsoft.com/en-us/download/malicious-software-removal-tool-details.aspx?id=9905
I have MS Security Home Essentials installed and admit it’s lulled me into taking risks w/downloaded SW where before I wouldn’t have assumed the risk. I ended up on this site due to seeing activity on my proxy posting info to “https://wdcp.microsoft.com/wdcp.svc/bond/submitreport” and was curious what it was.
FWIW, at the same time, my system was getting a bit sluggish w/MsMpEng.exe consuming the full cpu that it was running on (have made sure to limit MS-scanning processes to 1 core (the same core)) to lower impact, but the scheduling in Windows isn’t very good and allows background programs to cause desktop slowdowns even when those BG processes are limited to Idle prio and 1 core. sigh. There have been a few times when I clubbed it (it usually runs a full scan on Sundays, but that 1 scan takes up to a day rather frequently). It was really a drag when it also tried to scan my network drives (something Windows search can’t do…) (which are now on an exception list).
A malicious feature — it refuses to scan-on-demand, any area that you’ve disabled _automatic_ scanning of. Lame — though it means I need to copy material to my Winbox (most of my content is on a Linbox where it can be safely backed up incrementally & daily, unlike on windows).
Have had it detect maybe 2-3 malware infections in SW I downloaded, so I can’t complain much. I used to never try online progs due to paranoia (and refusal to pay “protection” money to anti-vir companies), but it made sense that MS would be best qualified to protect their own OS — and have a vested interest in doing so — its own reputation.
Changing the Task does not disable the MRT run during Windows Updates.
Setting a restriction poilicy via gpmc.msc (Domain) or gpedit.msc (local) works.
Windows Home users will have to do it via registry.
I wonder why my log doesn’t show any tracking info and the registry string is always set to prevent the data sending.
Maybe this is because i disable CEIP ?
There is a way…delete mrt.exe.
Thats what I did
I’m not fond of deleting system files. IMO a smarter move is to consider blocking unwanted applications right from the registry, as described in this article,
How to Block (or Allow) Certain Applications for Users in Windows :
http://www.howtogeek.com/howto/8739/restrict-users-to-run-only-specified-programs-in-windows-7/
Works nicely and allows enable/disable easily.
Just checked my mrt.log and it appears that this started in September with the release of v5.40:
—————————————-
Microsoft Windows Malicious Software Removal Tool v5.40, September 2016 (build 5.40.13000.0)
Started On Wed Sep 21 20:55:27 2016
Engine: 1.1.13000.0
Signatures: 1.227.1155.0
Run Mode: Scan Run From Windows Update
Results Summary:
—————-
No infection found.
Successfully Submitted Heartbeat Report
Microsoft Windows Malicious Software Removal Tool Finished On Wed Sep 21 21:00:28 2016
Return code: 0 (0x0)
—————————————————————————————
The tool seems to then run nightly at random times, according to the log, with Run Mode: Preparing Heartbeat Telemetry, but no status report to say it has been submitted. Haven’t had time to investigate but assume this is the Task Scheduled run with /EHB. The tool only runs for 3 or 4 seconds so I am wondering if this is just a run to ensure that the report is/was delivered, if for some reason it failed on the windows update run. On the two machines that I’ve checked there is no trigger so not sure how this is being rescheduled after the initial run.
Reading through KB891716, there are some other keys that enable checking the tool status:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemovalTools\MRT
more interesting is a sibling key of this one with some subkeys:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemovalTools\MpGears
On our machine these are:
Last Write Time: 21/09/2016 – 21:00
Name: SpyNetReportingLocation
Type: REG_MULTI_SZ
Data: SOAP:https://spynet2.microsoft.com/AntiMalwareServices/2/SpynetReportSrvc.asmx
SOAP:https://spynetalt.microsoft.com/AntiMalwareServices/2/SpynetReportSrvc.asmx
REST:https://spynet2.microsoft.com/spyNet.svc/submitReport
REST:https://spynetalt.microsoft.com/spyNet.svc/submitReport
BOND:https://spynet2.microsoft.com/spyNet.svc/bond/submitreport
BOND:https://spynetalt.microsoft.com/spyNet.svc/bond/submitreport
Name: HeartbeatTrackingIndex
Type: REG_DWORD
Data: 0x6
The registry key creation date seems to correspond with the first execution of mrt.exe v5.40 on this machine.
I chuckled at the urls, but is that humour on MS’s part or a blatant admission of what is occurring on our machines.
If companies feel they need to spy on us then there is little we can do about it, at least they are offering ways to opt-out of these surveillance activities – even if the methods for doing so remind me of an oft-quoted passage regarding a planning application and a leopard.
Just checked a Windows 10 machine and the reporting urls are different, the registry settings above were from Windows 7
Name: SpyNetReportingLocation
Type: REG_MULTI_SZ
Data:
SOAP:https://wdcp.microsoft.com/WdCpSrvc.asmx
SOAP:https://wdcpalt.microsoft.com/WdCpSrvc.asmx
REST:https://wdcp.microsoft.com/wdcp.svc/submitReport
REST:https://wdcpalt.microsoft.com/wdcp.svc/submitReport
BOND:https://wdcp.microsoft.com/wdcp.svc/bond/submitreport
BOND:https://wdcpalt.microsoft.com/wdcp.svc/bond/submitreport
However on my machines the domains resolve to the same ultimate ip address:
spynet2.microsoft.com. 3600 IN CNAME spynet2.microsoft.akadns.net.
spynet2.microsoft.akadns.net. 300 IN CNAME spyneteurope.microsoft.akadns.net.
spyneteurope.microsoft.akadns.net. 300 IN A 191.237.208.126
wdcp.microsoft.com. 3600 IN CNAME wdcp.microsoft.akadns.net.
wdcp.microsoft.akadns.net. 300 IN CNAME wdcpeurope.microsoft.akadns.net.
wdcpeurope.microsoft.akadns.net. 300 IN A 191.237.208.126
Geo ip indicates that ip could be in a data centre in Dublin:
GeoIP Country Edition: IE, Ireland
GeoIP City Edition, Rev 1: IE, 07, Dublin, Dublin, N/A, 53.333099, -6.248900, 0, 0
GeoIP ASNum Edition: AS8075 Microsoft Corporation
Although a whois shows the ip as registered through the Brazilian registry for Microsoft Informatica Ltda so who knows where our data ultimately ends up.
Recently (sept. or oct. 2016) MRT found a malicious file before our antivirus-tool Sophos did.
We only noticed because the user was asked to provide administrive rights than his own to delete it.
Has anybody noticed so far that any kind of information was sent out by the tool which must not leave a computer without consent? Any kind of protective software is interested in knowing what kind of malware is e. g. often found etc.
Heartbeat Telemetry.?
Heartbleed virus.?
Here’s is another trick for stopping some or most of this nonsense. Use the Windows policy “DisallowRun”, here’s a set of registry entries for this:
—–
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“DisallowRun”=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
“1”=”mconduitinstaller.exe”
“2”=”ieLogic.exe”
“3”=”ExPromo.exe”
“4”=”apn stub.exe”
“5”=”askbarsetup.exe”
“6”=”APNSetup.exe”
“7”=”ApnStub.exe”
“8”=”WerFault.exe”
“9”=”MRT.exe”
—–
Note the last two, while I just added MRT.exe, the WerFault.exe telemetry submitter has been there for a while.
Also copy the same settings under these keys:
[HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“DisallowRun”=dword:00000001
[HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
[HKEY_USERS\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“DisallowRun”=dword:00000001
[HKEY_USERS\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
[HKEY_USERS\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“DisallowRun”=dword:00000001
[HKEY_USERS\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
The other EXEs are for various annoyances, like the ASK toolbar. This works like a charm.
Many thanks Albert for letting me discover a Windows feature I had no idea of : the “DisallowRun” Windows policy.
1- Your list includes “4”=”apn stub.exe” and “7”=”ApnStub.exe” : 7 is 4 and 4 is wrong?
2- I searched for this “DisallowRun” and found the following which guided me with further information and concerns Windows 7 : no idea how other OSs handle the feature. System needs to be rebooted for disallowed applications to be effectively blocked.
http://www.howtogeek.com/howto/8739/restrict-users-to-run-only-specified-programs-in-windows-7/
I’ve seen both spellings, the ASK toolbar is included with a bunch of various installers, and the files are sometimes named one way or the other. Even though you might uncheck the unwanted junk, it frequently gets installed anyway, ignoring your choice.
I’ve been using the DisallowRun policy on my 90 year old mother’s computer, that put a stop to the many Citrix and other legit remote control programs that scammers keep having victims download.
I ran MSRT in September and found today that a Heartbeat Report had indeed been generated. I installed no Windows Updates for this month so there is no MSRT to run and no reports generated. I am moving to Linux so this won’t be a problem ( I hope) in the future.
Thanks for the article, Martin.
I just want to bring to your attention two points :
1- Microsoft’s MRT phones home not when run and closed but within an analysis (as far as I can tell).
2- If the updated MRT is installed manually by the user before Windows Update, Windows Update will of course not have to install it but won’t run it as well.
This means that users who wish to carry on with Windows Update but dislike having MRT scan and phone home can do so by checking for the latest MRT version (on Patch Tuesdays or sometimes the day after), download/run the patch (without analysis) and then run Windows Update more comfortably.
Latest version of MRT is always available at https://www.microsoft.com/en-us/safety/pc-security/malware-removal.aspx
I used to proceed this way for gaining the time spent by Windows Update to scan the user’s machine. If I were a Patch Tuesday full rollup user i’d continue the same moreover when this article proves the application is even more talkative than myself :)
Thanks for signaling this, Martin. Double-checking my 8.1 computer for this issue gave a very, VERY interesting result.
It looks like this very month, Microsoft sneakily changed its telemetry server addresses in order to foil users who blocked such addresses in their hosts file.
I have a block list of Microsoft telemetry addresses in my hosts file, and until October 3 this also worked fine to prevent MRT from phoning home. The log for the previous months always was like this:
(quote log)
Run Mode: Preparing Heartbeat Telemetry
Failed to collect/send Heartbeat Send Failure heartbeat. HR = 80072EE7
(end quote)
This recurring 0x80072EE7 error always indicated a failure to connect to the server, which was exactly what I wanted.
But checking today I found that the very last time MRT ran on this system, October 12, the log said “Successfully Submitted Heartbeat Report”. This was a first! Clearly this month Microsoft did switch to some new server address to evade any existing IP blocks. I still need to find out what new telemetry addresses they may be using now.
Anyway, I will stop using MRT. Forever. I never really needed it, so I won’t miss it.
Blocking MRT.exe on the firewall is enough to prevent the transmission.
On Win10 Pro 64-bit, Windows Malicious Software Removal isn’t installed and I don’t have mrt.log.
it IS installed in Windows 10 x64 and stores its log in Windows/Debug folder. The only thing I didn’t find was MRT task in Task Scheduler, but I assume they simply renamed it to mask from user.
I found the same thing on W10 pro 64. No RemovalTools entry at all in task scheduler
Windows 10 64 bits: No RemovalTools in task scheduler but I found mrt.log; last change: Wed Oct 12 2016.
So MRT must be installed even in Windows 10.
Is it opt-in on Win 10 too? It is on Win 7, and ofcourse I did not accept it. I’m tired of Microsoft’s automated stuff, always taking up 25% CPU usage for half an hour each time I used to boot my PC. Both this and MSE. And the only thing that MSE was always finding was Xpadder, a program to map keyboard keys on my X360 gamepad, but nothing more, so I’m better wthout them.
Testing on Windows 7 64-BIT.
1- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT not found
2- Task Scheduler Library > Microsoft > Windows > RemovalTools > MRT_HB not found because I had not only disbled that task but radically removed it (not advised, I was younger then).
3- I had no mrt.log because I’ve set CCleaner to delete unnecessary logs. I’ve just ran mrt v.5.41 (Oct. 2016) for a fast analysis and the new mrt.log states :
“Results Summary:
—————-
No infection found.
Failed to submit clean hearbeat MAPS report: 0x80072EFD”
I must ad that I have a serious anti-Microsoft tracking arsenal in place here. Goof it it does the job.
The key to check for mrt execution status can be found at:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemovalTools\MRT
I had to manually create the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT and subkey DontReportInfectionInformation
Thanks for the info, James Law. Indeed I do have the key you mention, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemovalTools\MRT
For what it’s worth, as far as I’m concerned mrt.exe has been removed (in system32 and syswow64 folders). I won’t use it since it cleans when applicable with no prior user consent. Anyway I never used it. I get to wonder if its primary meaning is not to phone home and I follow on by asking myself what code, what application, software, OS developed by Microsoft is clean in terms of privacy issues.
MS states that the Win malicious software removal tool is NOT a replacement / alternative for dedicated anti-malware and anti-virus software.
I have good anti-malware and anti-virus software installed. Every month, since it first appeared, I have hidden this KB because, for me, it is irrelevant.
Now it is exposed as yet another MS telemetry tool. I sympathize with users like Dave who have found out that it is flawed and not fit for purpose.
Microsoft’s BS security tools deleted all my original xbox softhacking utilities, way back when they were very hard to get. I still don’t think I have them back.
That’s why you back up
You shouldn’t have to backup to protect yourself from your operating system.
I never run Microsoft’s MRT (but I do update it, one never knows), I just did for testing its tracking issue.
May I ask those who’ve run it and had MRT actually find what it considered as malicious, if the user has the option or not to allow MRT to cleanup? If I understand you correctly, Dave, it seems MRT deleted your “original xbox softhacking utilities” presumably without your prior consent. Is this true? If yes, I’ll never run MRT again.
Oh well, Dave, then I’ll never run MRT again. If it had to find and delete files it considers as malicious even should they be not then this is a veto for me. What has been deleted is not always recoverable but the user must have the authority to trigger the destruction button : MRT should report and allow always the user to choose to delete or not, be it MRT as any other application. “False-positive” is a reality.
To resume:
– MRT sends back telemetry data;
– MRT deletes “malicious” files it may have found without the prior consent of the user.
That’s 2 bad points, another two for Microsoft, indisputable winner of all times telemetry & tracking features.
And if I slap the company it’s of course for the same reasons it slaps its users : for their good. Reciprocity is the basis of politeness.
Thanks for this valuable information, Dave.
That’s right Tom. I found out later in the logs, but the files weren’t recoverable. I dunno if the current version still behaves this way.