Firefox blocks weak Diffie-Hellman keys
Mozilla announced on September 30, 2016 that it made the decision to enforce stronger Diffie-Hellman keys in the Firefox web browser.
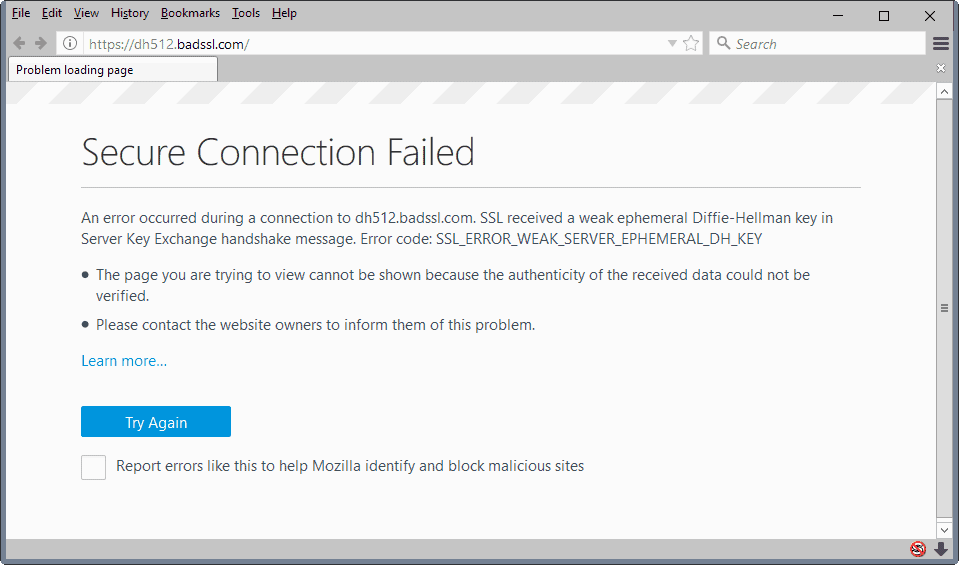
Firefox users who visit websites that use weak -- now less than1023 bits -- will see a connection error message in the web browser instead of the actual site.
The message reads "secure connection failed" and the reason given is the following one:
SSL received a weak ephemeral Diffie-Hellman key in Server Key Exchange handshake message. Error code: SSL_ERROR_WEAK_SERVER_EPHEMERAL_DH_KEY
The page lists a learn more link that leads to the Firefox "what does your connection is not secure mean" support page on Mozilla Support.

The error page itself lists a "try again" button but no option to override the policy and open the actual website.
In case you are wondering, this is how other browser's are handling sites with weak Diffie-Hellman keys:
- Google Chrome, Opera and Vivaldi throw a "this site can't provide a secure connection" error with no override option. Other Chrome or Chromium-based browsers are likely throwing the same error message.
- Pale Moon throws a "secure connection failed" error.
- Microsoft Edge displays "hmm, we can't reach this page" error instead.
- Internet Explorer throws the error "this page can't be displayed.
According to Mozilla, a small number of servers are still configured to use weak keys that are vulnerable to attack.
In response to recent developments attacking Diffie-Hellman key exchange (https://weakdh.org/) and to protect the privacy of Firefox users, we have increased the minimum key size for TLS handshakes using Diffie-Hellman key exchange to 1023 bits. A small number of servers are not configured to use strong enough keys. If a user attempts to connect to such a server, they will encounter the error “ssl_error_weak_server_ephemeral_dh_keyâ€.
The organization mentions the Logjam attack in particular which attacks the TLS protocol.
All major browsers block sites that use weak Diffie-Hellman keys now with no override option. In case you are wondering, Firefox's preference to override weak security certificates is not working either.





















https://bugzilla.mozilla.org/show_bug.cgi?id=1269807
“Remove support for all NPAPI plugins except for Flash, behind a pref. Tests that use the testplugin for now set the pref to keep it working. This will be disabled for ESR 52, but enabled for release 52. In the next cycle, the pref will be removed and this will be hardcoded.”
NPAPI is finally dead, biggest source of crashes and security issues due to buggy insecure plugins is finally gone, hooray.
To be fair, you didn’t have to use NPAPI plugins. I don’t think I use any plugins, because it’s not 2003 anymore.
Interesting. The error message is ridiculous though. How about “This website cannot provide the secure connection that is required.” That makes sense to the average person, and it conveys all the necessary information.
About that message illustrated above that says “Please contact the website owners to inform them of this problem.”
Maybe I can send them a snail mail postal card, since their web site is now unreachable with any known browser.
That is a good point George. You could run a whois and send an email to the administrative or technical contact of the domain: https://who.is/
I did that once and reached a very surprised administrator who had no idea her email was listed on the internet. :)