Find out if Microsoft stores encryption recovery keys in the cloud
A recent The Intercept article reveals that Microsoft is storing device encryption keys in the cloud under certain circumstances automatically.
Device Encryption is a built-in encryption feature that became first available with Microsoft's Windows 8 operating system. The core difference between Device Encryption and Bitlocker is that Bitlocker is configurable while Device Encryption is not.
Furthermore, full Bitlocker functionality is only available in Pro and Enterprise editions of Windows while Device Encryption is available in all.
Device encryption is enabled automatically if the computer has the required encryption chip and if a Microsoft account is used to sign-in to the computer. If that is the case, the encryption key is stored in the cloud automatically. If the computer is not connected to a Windows domain, it is sent to Microsoft, and if it is, will be stored on company servers instead.
Windows users who choose not to create Windows accounts during setup or afterwards, won't have device encryption enabled.
There is no way to prevent Windows from sending the encryption key to the cloud if the computer matches the requirements.
Why keys are backed up in the cloud
You are probably wondering why Microsoft backs up keys in the cloud automatically. The answer to that is convenience, as users can make use of the key backed up in the cloud to regain access to files on the system. This can be the only way if no local backup of the key exists.
Microsoft could however handle this differently. For instance, it could provide users with an option to back up the key locally or in the cloud, something that Apple does for instance.
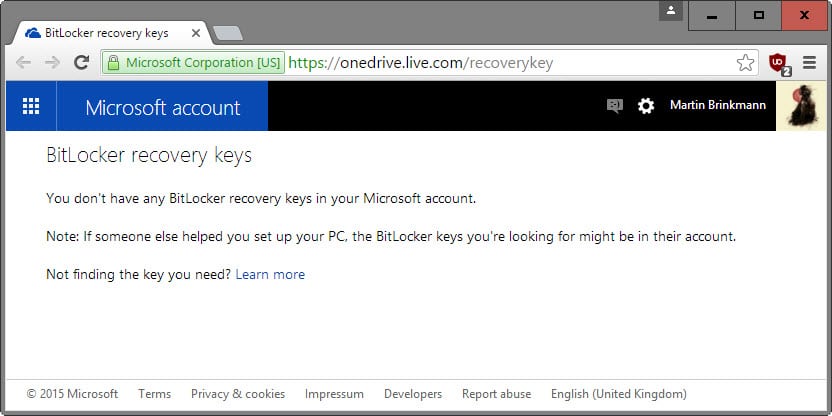
Check up on cloud stored encryption keys

While you cannot prevent Windows from transferring keys to the cloud, you can check using your Microsoft Account to find out if keys are saved in the cloud, and delete them if that is the case.
- Load https://onedrive.live.com/recoverykey in your browser of choice.
- Log in to your Microsoft Account to access the service.
- Microsoft lists all recovery keys stored under that account on the page. If you get "You don't have any BitLocker recovery keys in your Microsoft account" it means that no keys are stored. This is the case for instance if the computer has no encryption chip, or if a local account is used to sign in on the PC.
- Otherwise, you may delete the recovery key on the site. It is suggested to back up the key before you do so.
To be on the safe side
Microsoft noted that the encryption key and backups are deleted when users deleted them on the Recovery Key page.
While that is reassuring, it is suggested to create a new encryption key locally instead and save it locally as well to make sure no one can decrypt data on the drive using the old encryption key.
While local access is needed for that, it is better to be safe than sorry later on.
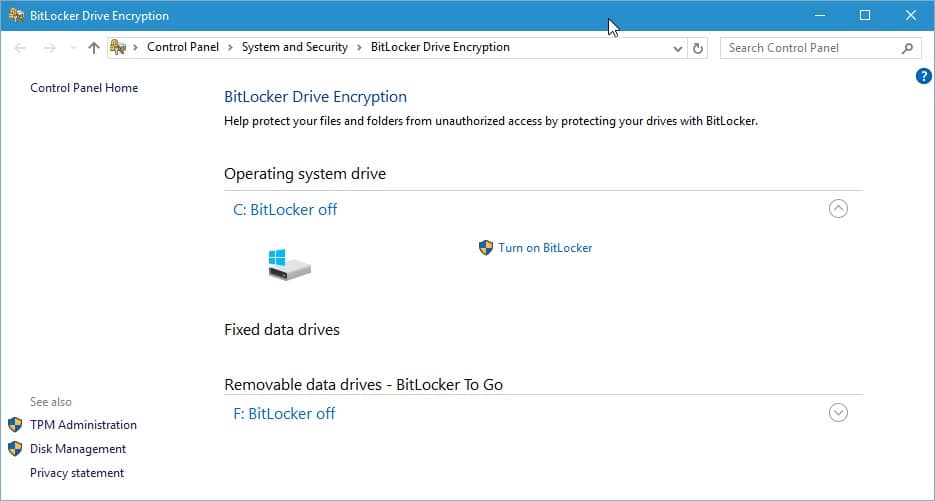
- Tap on the Windows-key, type bitlocker and select the Manage BitLocker result to open the BitLocker Drive Encryption settings.
- Select "Turn off BitLocker" next to the operating system drive. This will decrypt the drive which may take a while depending on its size and performance.
- Once done, select "Turn on BitLocker".
- Windows will prompt you to back up the recovery key. You can select to save it to a file, or to print the recovery key. Don't select Microsoft Account as it will end up in the cloud again if you do.
- Select to encrypt the entire disk including empty space on the next page.
- Select yes when asked to run the BitLocker system check afterwards.
- Reboot your PC.
BitLocker will start to encrypt the drive in the background afterwards. It is suggested to check the Microsoft Account again when the process completes to make sure the new recovery key is not listed there.

















Total Storm in a Teacup, akin to the privacy ‘issues’ in Windows 10. There’s really nothing to see here, other than sensationalist headlines hoping for clicks from The Intercept (and others)>
A total dismissive post from someone with little understanding of the issue, as Jason rightly pointed out it’s that it stores the key on Microsoft servers automatically with no warning or alternative until afterwards.
For a company that’s told everyone they need to build up trust, how they want to put the user in control, and just a few days ago said their all about giving people a choice, the uploading a key to their servers without even telling you isn’t exactly the way to go about it.
There are multiple reasons for a Windows user to be annoyed:
-the cloud backup behaviour is automatic and (if I understood correctly) unannounced.
-the only solutions (given on this page) are (a) a tedious decryption/re-encryption process, or (b) a quick but non-user-friendly command line process.
-plus, frankly, there is a pattern here. Microsoft is trying to do too much thinking for the user, causing a lot of confusion / extra work / undesired consequences for a lot of people.
Anyway, at least this particular issue has a solution.
I think the Intercept article makes more of a meal of this than is the case. If I have understood correctly the issue is with Device Encryption from Windows 8 up, and only if you choose to log in with a Microsoft as opposed to a local account. If you choose to log in with a local account, or enable Bitlocker and do not choose to backup your recovery key to any Microsoft account then you are fine.
I would only be concerned if Microsoft did not make it clear to the user that (with Device Encryption) his recovery key will be backed up to Microsoft’s servers if he logs in with a Microsoft account.
You must signup for a Microsoft account if you want to enable device encryption, without doing that it either wont enable it or knowing Microsoft probably wouldn’t let you continue until you have.
And as i mentioned above this is only an issue now because in the past (8.x) the hardware requirements were optional not mandatory.
I have two MS email accounts. One that friends use to send me jokes. The other required by MS as a security backup. When I hit the link that Martin provided I was told I needed to enable cookies. I enabled cookies and hit the link again. I was instantly faced with a screen that had half of my security email account’s name written out. I was required to enter the full name to access the option. (I do not allow stored cookies)
For that to happen, Microsoft had to identify my computer’s hardware. That means it is possible for MS to track this computer based on a hardware hash. I wondered if Win10’s telemetry was sending such a hash to MS (I’m writing this on a Mac).
Now, if I’m completely misunderstanding this situation feel free to correct and educate me.
Wait up, rather than decrypting the whole drive, why not generate a new recovery key?
From an administrator command prompt:
manage-bde -protectors -disable %systemdrive%
manage-bde -protectors -delete %systemdrive% -type RecoveryPassword
manage-bde -protectors -add %systemdrive% -RecoveryPassword
manage-bde -protectors -enable %systemdrive%
The first command suspends bitlocker (i.e. the data on the drive is still encrypted but the master key is left unprotected). The second deletes the recovery password. The third creates a new one. The final command turns Bitlocker back on.
With this method you’ll need to manually copy that recovery key somewhere safe as it doesn’t force you to do so like the GUI version does.
A nice user friendly option would have been nice don’t you think? Not from you BTW but provided by Microsoft as part of the setup.
OMG, seems everyone forgot that this was implemented in Win8 and now they are making a fuss because Win10 is “hot” topic…
It also seem people saying that aren’t aware that Microsoft changed the hardware requirements needed to gain certification for Windows 10, specifically they made secure boot and TPM, hardware that if detected automatically enables device encryption to mandatory instead of optional.