How to block the insecure RC4 cipher in Firefox and Chrome
Whenever you connect to a secure website using Firefox or any other modern browser, negotiations happen in the background that determine what is being used to encrypt the connection.
RC4 is a stream cipher that is currently supported by most browsers even though it may only be used as a fallback (if other negotiations fail) or for whitelisted sites.
Exploits have come to light in recent time that take advantage of weaknesses in RC4 which allow attackers to run attacks in a reasonable time frame, for instance to decrypt web cookies which often contain authentication information.
Mozilla wanted to remove RC4 from Firefox completely initially in version 38 or 39 of the browser but decided against it based on telemetry data. As it stands right now, RC4 won't be disabled in Firefox 39 or 40.
Tip: you can check if your web browser is vulnerable by visiting this RC4 website. If you see red notifications on the page after the text has been conducted it means that it is vulnerable to attacks.
It needs to be noted that other browsers, Google Chrome for instance, are vulnerable as well. Google is apparently also working on dropping RC4 support completely in Chrome
Disabling RC4 in Firefox
Firefox users can turn off RC4 in the web browser completely. It needs to be noted that some secure sites may fail to work after doing so.
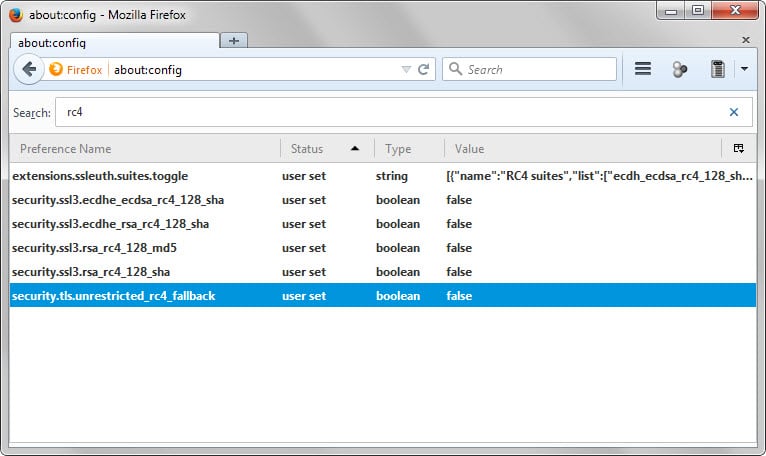
- Type about:config in the browser's address bar and hit enter.
- Confirm you will be careful if you receive a prompt.
- Search for RC4 and double-click on the following preferences to set them to false.
- security.ssl3.ecdhe_ecdsa_rc4_128_sha
- security.ssl3.ecdhe_rsa_rc4_128_sha
- security.ssl3.rsa_rc4_128_md5
- security.ssl3.rsa_rc4_128_sha
Once you have made the changes reload the test page linked above. You should get connection failure messages instead of warnings when you do that.
If you run into issues connecting to secure sites after making the changes you may need to restore support for RC4. To do that repeat the steps above and make sure the values of the preferences are set to true afterwards.
Disabling RC4 in Chrome
The process is complicated in Chrome as you cannot simply switch a couple of preferences in the web browser to disable RC4 in it.
The only valid option is to run Chrome with command line parameters that block RC4. Here is how this is done (instructions for Windows).
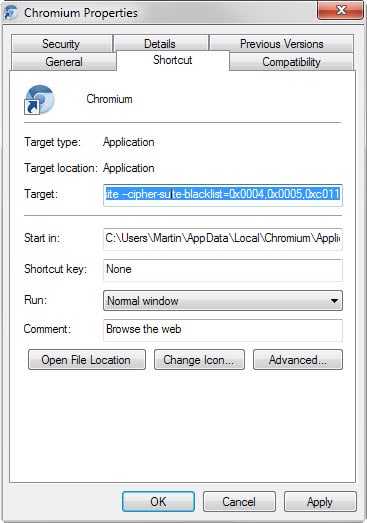
- Right-click on the Chrome shortcut in the taskbar of the operating system, and right-click again on Chrome, and select properties from the context menu that opens up.
- This should open the properties of the executable file.
- Add --cipher-suite-blacklist=0x0004,0x0005,0xc011,0xc007 as a parameter to the end of the Target line. Make sure there is a space in front of the parameter.
- The target line looks like this on my computer after adding the parameter: C:\Users\Martin\AppData\Local\Chromium\Application\chrome.exe --cipher-suite-blacklist=0x0004,0x0005,0xc011,0xc007
- Note: yours will vary based on your username and the version of Chrome you have installed.
The command adds RC4 to the cipher blacklist so that it won't be used by the browser. If you rerun the test, you will notice that it will fail (which is good).

















i use chrome 64bit in windows 10 when i add this –cipher-suite-blacklist=0x0004,0x0005,0xc011,0xc007 and click apply see error, what i do?
Dec 30 2015:
The Stock Browser in Android 5.1.1 also appears to have RC4 (4 Suites) still enabled. Hopefully this gets fixed with the “concertated” Campaign to drop it finally.
Also, the IE11 Browser within Windows 8.1 Mobile has not yet been fixed (it still supports SSLv3, in TLS1 all the known Vulnerability Issues have not yet been fixed/mitigated, including RC4 being usable)
Great info as usual. Did this not to long ago and I also have not had any issues with any websites, at least to this point. ;)
The reason companies keep old encryption is because they have server farms that are setup with hardware that does just one thing (in this case, RC4 acceleration). It’s expensive and time consuming to switch to something else so the rationale is “it’s secure *enough*”. However, if clients and support cases created by users increasingly stack up against it, the switch will accelerate.
Thanks for posting about this.
Just FYI, my Internet Explorer 11 x64 tested as insecure. (I never use it, so I don’t care.) Both my Firefox x86 and Pale Moon x64 installs tested as secure, possibly as a result of actions I took in the wake of the last big insecure protocol scare (a couple of months ago?). I uninstalled Google Chrome some time ago, so I don’t have to bother with it.
I don’t see it mentioned in the article, but I’m running Firefox 41, and RC4 is disabled by default.
@ Hy (unfortunately there was no “Reply”-Button in your comment).
Thanks a lot for your hint to the addon ssleuth, installed it.
I think it gives the possibility to leave the about:config-settings as they are
(all RC4-entries “true”) and set ssleuth to disable RC4 Suites by right-clicking
the adress-bar button, so it should be possible to enable RC4 only when it’s needed.
Thank you, Hy! And many thanks to Martin for the great article.
You’re very welcome! :)
Also big thanks from me as well Hy, SSLeuth is a fine addon for Firefox and i did not know of it before, cheers!
Thanks for this Martin.
Done and dusted.
How to block RC4 in Opera 12.17?
In Opera 12 go to: Settings > Preferences > Advanced > Security > Security Protocols > Details
Look for entries with RC4 in them.
Uncheck.
Reload the test page.
You should be OK now.
I have done exactly what Martin suggests about a month ago ,have not
had any issues with sites ,So Firefox dump this crap
is not needed just unnecessary problems to be !
Thank Martin
Always has great suggestions ..and fixes
I’ve tested on Firefox several ssl sites with the insecure RC4 cipher disabled and no problem up to now. I’m not using EFF’s HTTPS Everywhere add-on but I imagine doing so could maybe lead to connection failures…
Thanks again for the quick info, Martin. Nothing is too quick when security is concerned.
This add on will handle RC4 for you among other things: https://addons.mozilla.org/en-us/firefox/addon/calomel-ssl-validation/
what should I tick in this addon to disable rc4 ?
thank you
ok, thanks Hy
FYI: SSleuth works with the current release of Firefox but not with the current release of Pale Moon. Calomet works with Pale Moon.
Actually, there is nothing specific to tick in the Calomel addon because Calomel cannot be set to disable insecure RC4 cipher suites only.
A much better addon to replace Calomel, and in which you can specifically disable RC4 suites, is SSLeuth: https://addons.mozilla.org/en-us/firefox/addon/ssleuth/
You can also disable RC4 in the addon CipheFox Secure: https://addons.mozilla.org/en-us/firefox/addon/cipherfox-secure/
I did the steps you mentioned, Martin, but I still get the fallback vulnerability.
Some interesting references from the archlinux wiki:
https://wiki.archlinux.org/index.php/Chromium_tweaks#Disable_insecure_RC4_cipher
This is the list of cipher suite I disabled in chromium:
–cipher-suite-blacklist=0x0001,0x0002,0x0004,0x0005,0x0017,0x0018,0xc002,0xc007,0xc00c,0xc011,0xc016,0xff80,0xff81,0xff82,0xff83,0x0033,0x0039,0x0067,0x006b,0x009e
The last five (0x0033,0x0039,0x0067,0x006b,0x009e) are blocked in order to avoid the logjam attack, but I’m sorry now I can’t find the link with references…
In iceweasel/seamonkey I have also these “about:config” entries:
security.ssl.treat_unsafe_negotiation_as_broken;true
security.ssl.require_safe_negotiation;true
security.tls.unrestricted_rc4_fallback; standard boolean false
steht hier bei mir.
Demzufolge müsste ich diesen auf true setzen was dann eventuell wieder auswirkungen hat auf sichere seiten
The way it is configured on your end currently is that RC4 is still enabled on whitelisted sites. If you don’t want that, you need to disable the preferences mentioned in the article.
Bei mir steht
SECURE!
Your browser doesn’t support RC4 by default.
Fallback test below. If you don’t see a red warning, you’re probably safe.
Daraus schliesse ich das es unter Nightly 42 soweit alles Passt ohne das ich -Deaktivieren RC4 in Firefox
gemacht habe
gruss Fips
Fips, this is not the case. If you check about:config, you will notice that RC4 is still enabled but that the preference security.tls.unrestricted_rc4_fallback is set to false now.
The last preference turns off the fallback to RC4 on all sites but sites on a whitelist.
https://hg.mozilla.org/integration/mozilla-inbound/annotate/3e18d65b28c3/security/manager/ssl/src/IntolerantFallbackList.inc#l160