WordPress: Why you may want to disable XML-RPC Support
I recently bought a new website to add to my website investment portfolio, moved it to a server after some initial testing, and have been running it on that server ever since. I noticed a couple of days ago that the site was timing out on page load times. Not always, but it happened from time to time which was cause for concern as I was not that familiar yet with the themes and plugins it used.
The site itself is powered by WordPress, and I started by going through plugin and theme settings to find a feature or setting that I could link to the time outs.
Turns out I could not. I contacted my hoster and they told me that this was caused by a spam attack that was using the XML-RPC (the RPC stands for Remote Procedure Call) feature.
XML-RPC for those who do not know about it is a remote publishing feature of WordPress. You can write your blog posts in third party software such as Windows Live Writer, Qumana or the cross-platform QTM, and publish it on the blog when you are done with it. It may also be used by pingbacks and trackbacks, as well as customized solutions.
Anyway, the solution that the server provider implemented blocked any request to the xmlrpc.php file on the server to return a forbidden message.
<IfModule mod_alias.c>
RedirectMatch 403 /xmlrpc.php
</IfModule>
You can use the following code alternatively:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
Just add this line to the end of your .htaccess file that is in your WordPress root directory to prevent access to the file. It is important that you only do so if xmlrpc is not used for anything.
You can alternatively use a filter to block it using the WordPress config file. To do so open wp-config.php and add
add_filter('xmlrpc_enabled', '__return_false');
after the following line:
require_once(ABSPATH.'wp-settings.php');
Note that doing so will not remove the line
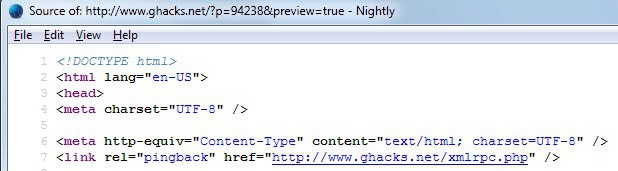
<link rel="pingback" href="https://www.ghacks.net/xmlrpc.php" />
from the page source code. Replace this domain name with yours to check it out. Spammers may still use the information to send spam and pingback to your blog, and WordPress still needs to handle it. That's why it is better to have the server handle this via .htaccess.
The second .htaccess option enables you to whitelist IP addresses that you want to allow access to the file. Simply use the following code to do so:
<Files xmlrpc.php>
Order Deny,Allow
Deny from allAllow from 987.654.321
</Files>
You can add multiple allow from lines here and need to change the bogus IP used in the example to the one that you want to whitelist.
If you want to remove the pingback line in the source code, open the theme header file and remove the line from there. While that removes the line from the source code, spammers may still use the default location of the file to use it.
You find more information about this on Click Nathan and Deluxe Blog Tips.
Advertisement














For WordPress, the odd side is that you can’t use WLR or OLW. Posting from the admin editor is an annoyance really.
Since most bloggers do not use a fixed IP, maybe the solution is some sort of password to access xmlrpc.php.
hello Martin you can also deny the request by 403 Forbidden error too by the URL /xmlrpc.php
example you can try on the plugin here:
https://wordpress.org/plugins/disable-xml-rpc-littlebizzy/
What if you simply rename xmlrpc.php to something else?
Possible as well, but it will be readded when you update I believe.
Wow. You were reading my mind. I was having the same issue the past day or two. I could access my home page, but anything past that I got the “500 internal server” error. I added in your fix, no more issue. Thanks a bunch!