Google Chrome to warn against malicious extension downloads
Google has added several safeguards to the Chrome web browser in recent time to increase the security of the browser in regards to the installation of browser extensions. The developers blocked the option to install Chrome extensions from third party websites last year. This prevents installations by the user but also by automatic means from third party websites, and while there is a way around that, it is a manual way so that it cannot be exploited.
Recently, it introduced a feature to the stable version of Chrome that blocks the silent installation of extensions in the browser. This blocks automatic installations of add-ons by third party software such as security applications or other programs that are running on the system.
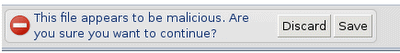
Today, Google announced another change in regards to the security of extensions. It is still possible to download extensions from third party websites so that you can install the extension in the browser by dragging and dropping it into the extensions manager of the browser.
Chrome from this week on will scan extensions that are downloaded to the local system to warn users if they are potentially malicious.
The only explanation that Google provides is that it fill flag binaries as malware if they violate Chrome's standard mechanism for deploying extensions. According to Google, standard deployment mechanisms are through the Chrome Web Store, using inline installations (which reference the Chrome Web Store but run the installer on the site they are triggered on), and through third party software
Google notes that malware in the past tried to get around the new silent installation protection of extensions by misusing Chrome's central management settings which are designed to deploy Chrome in organizations and usually on multi-computer networks.
In doing so, the installed extensions are enabled by default and cannot be uninstalled or disabled by the user from within Chrome. Other variants include binaries that directly manipulate Chrome preferences in order to silently install and enable extensions bundled with these binaries. Our recent measures expand our capabilities to detect and block these types of malware.
Additional security mechanism are always welcome and if the warnings pop only up for malicious extensions and not for all extensions that are hosted on third party websites.
Advertisement
















Blocking doesn’t seem to work.
Just updated Java 7u21 yesterday and let (by mistake) ASK toolbar to be installed.
Uninstalled the toolbar using Portable IObit Uninstaller. Got a pop-up message from
Chrome’s Extensions Update Notifier that ASK toolbar has been installed , would I like to disable ASK.
Had to remove ASK manually.
Chrome Version 27.0.1453.56 beta-m
They said they introduce the feature this week, so it may not be active yet in your version. Also, I’m not sure if they will identify Java as malicious in this scenario.
It was not Java but ASK toolbar extension that was installed :-)