The ultimate guide to securing your Twitter account
Twitter, like any other high profile site on the Internet, is targeted by hackers, scammers, spammers and users who use it to distribute malware or spam.
Security of the Twitter account is of uttermost importance and even if you take all precautions and bomb-proof it, there are still things that may slipped past those defenses.
A simple example is if the Twitter account of a friend gets compromised and then used to spam the followers or distribute malware. You can't protect your account from this, and unless all of your friends are securing their accounts as well, there is always a chance that you may be exposed to these threats.
Still, it is important to secure your account to avoid that it is being misused by malicious users in this way, that third party apps do not record all your moves and sell them to the highest bidder, and that it is not being used to spam your friends on Twitter.
The following guide is a complete guide to Twitter security. I suggest you read it from beginning to end as it is most effective when you do that and make all the necessary changes to your account.
Your Twitter account
The first thing that you need to do is make sure that only you can access your account on Twitter. There are a couple of things that you may want to do to ensure that this is the case.
Use a secure password
While it may be convenient to use a password like princess1 or dallascowboys to sign in to Twitter, it is not very secure. Attackers use dictionary attacks and combine them with often used variations, like adding a 1 to the end or replacing the letter e with a 3, to get into accounts.
It is important to set a secure password on Twitter. There is no definition of secure password on the other hand that is universally accepted. My suggestion would be to use at least 16 characters, at least one letter and one number, and at least one special character in the password.
Make sure you don't use any words found in dictionaries unless you combine them with other words or characters.
It is also important not to reuse passwords so that you can't run into problems if another service on the Internet where you used the password has been compromised.
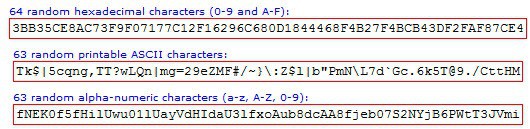
You can use a password generator to generate ultra long random passwords and use a password manager to save them so that you do not have to remember the passwords or write them down (never do that).
You can change the Twitter password on this page. Note that you do need to enter your current password and the new password on the page.
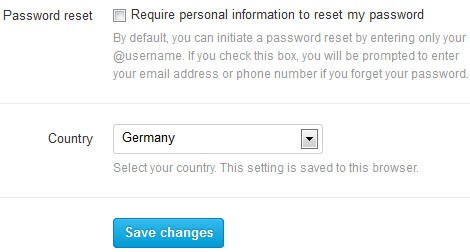
You may also want to check the password reset box on Twitter to make it difficult for third parties to reset the account password.
You can request a password reset on Twitter by simply entering the @username of the account in the login form on the site. If you enable this option, Twitter will prompt for the account's email address or phone number as well which need to be entered before the password reset process is started.
You find that option on the main Account settings page on Twitter under Security. Just check the "require personal information to reset your password" box to add this security option to it.
We suggest you configure login verification on Twitter as well. It is a two-factor authentication option that adds a second layer of protection to your account.
Note that you need a mobile device for that and verify a mobile phone number with Twitter.
The login and phishing
You can still run into traps or issues even if you are using a secure account password. This can for instance be the case when you enter it on a site that you believe is Twitter, when in fact it is not.
Phishing is a permanent threat on the Internet and while it is usually associated with email, it can also happen that you are attacked via advertisement, chats, search engines or notifications.
The best option to protect yourself against phishing is to enter the Twitter web address manually whenever you want to go there, or to use a bookmark instead that you have saved previously.
I'd recommend you check the address anytime you connect to Twitter to make sure it begins with https://www.twitter.com/.
It seems that Twitter is making use of https by default now so that you do not have to enable that option any longer in the settings to use it.
Before you log in on the site, check the web address to make sure you are on the right site.
Change privacy related settings
If you value your privacy, you may want to make a couple of modifications on Twitter to boost it.
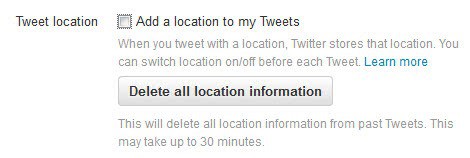
Twitter did add the location to the tweet automatically in the past. It did not take long before software became available that would display the location history of Twitter users using the information.
The data could be abused by third-parties, and burglars could use it to make sure you are not at home. Twitter changed its stance on location-based data in tweets and set the option to disabled by default.
You may want to check nevertheless to make sure that your tweets don't include the information.
- Open Twitter's Privacy and safety page here: https://twitter.com/settings/safety
- Make sure that "Tweet with a location" is not checked under Tweet location.
I suggest you click on "delete location information" if the option was checked to make sure all location-based information is removed.
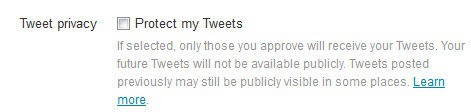
If you are only communicating with a select group of friends, you may want to consider enabling the "Tweet Privacy" option on the same page by checking "protect your tweets".
Private or protected tweets are only visible by approved followers while they are not visible publicly. Note that this does not impact past messages on Twitter.
Other security and privacy options on the page include disabling photo tagging for the account, disabling discoverability options using your email address or phone number, disabling direct messages, or making sure that sensitive content is blocked.
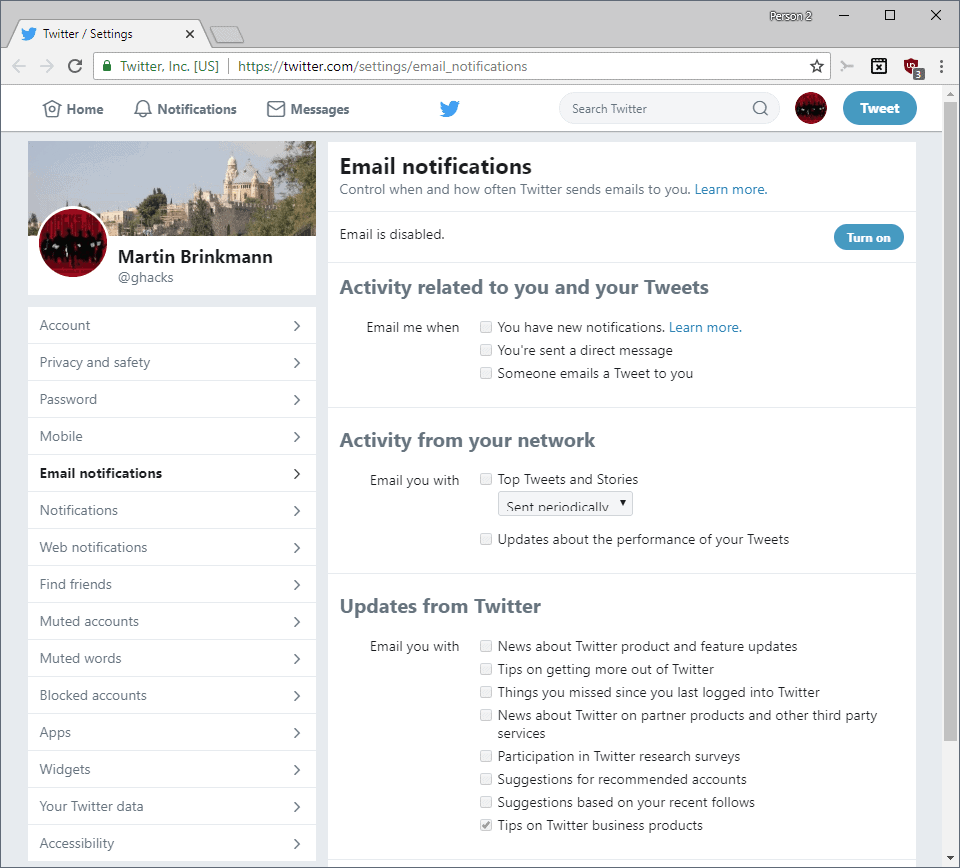
You may also want to check the email notifications page to make changes to some of the notifications and updates that you receive from Twitter periodically.
There are a lot of settings on this page and while some of them may be useful, like receiving information about a new follower or direct message, others may not be as interesting like tips on getting more out of Twitter or news about Twitter and feature updates.
Third party applications
Third party applications can use Twitter for authentication or may require access to your Twitter account if they provide you with functionality.
A desktop Twitter client for instance may need read, write and direct message permissions.
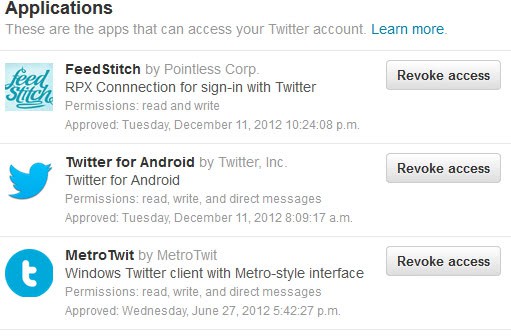
You can check all apps that you have authorized in the past to access your Twitter account on this page:Â https://twitter.com/settings/applications
Each app is listed with its name, company, a short description, the permissions it has and when it was approved.
You can click on the revoke access button next to each application to remove the application from the list of authorized apps.
It is recommended to go through the list and remove all applications that you do not need any longer or have privacy concerns about.
Dealing with messages on Twitter
The majority of messages that you read on Twitter use short link services that do not really reveal the destination of a link. You do not really know where http://goo.gl/6g4XB will redirect you to. You may want to use a service to expand these links before you click on them to know where they point to.
A web service that you can use is Check Short Url. It supports popular URL shortening services but requires you to copy the link and paste it into the web form.
Web Browser tools, features and misc
Here is a small selection of extensions and features that you may want to consider as well.
- Enable Do Not Track in your browser to avoid personalized advertisement.
- Install NoScript in Firefox, the best browser security add-on, or another security extension that blocks third-party connections (see best Firefox add-ons, see best Chrome extensions)
- Make sure your web browser, its extensions and plugins are always up to date. Use Mozilla Plugin Check, Adobe's Flash verifier, the Java version check or a desktop program like Sumo to check plugins and versions.
- Make sure you run an antivirus solution that protects your system in real time, and a firewall that blocks threats and connections. Popular solutions include Avast Antivirus Free or AVG Antivirus Free. The Windows Firewall is not that bad anymore either.
Closing Words
This may seem like a lot but it is not really that complicated to set up, especially since you can use the majority of these best practices on other Internet sites as well. Let me know if you think that the guide missed an important aspect so that I can add it to it.



















Useful article!
I do it the simpletons’ way: I don’t twit nor facebook :)
Nobody needs to know my business. Although I found that I couldn’t stay away from LinkedIn :(
Nice Article, it was really helpful.
Using a password manager and writing a password on paper are different methods to protect against different kind of attacks. I would not dismiss writing a password on paper; for instance if you trust all people in your house, but you are not confident enough that you are not going to have your password manager under attack by a hacker/keylogger/trojan, it is better to have your password written down. I’m not saying that this is your case, but I was just pointing out that password protection methods can vary depending on what kind of attack you are protecting yourself against.