Update Windows Security software to protect against a serious vulnerability
Microsoft published information about a new security vulnerability that affects Windows Defender, Microsoft Security Essentials, and several Enterprise-specific anti-malware solutions.
CVE-2018-0986, Microsoft Malware Protection Engine Remote Code Execution Vulnerability, describes a vulnerability in the Microsoft Malware Protection Engine that attackers could exploit to execute code on the system.
What makes the vulnerability particularly problematic is that it can be triggered by Microsoft security software scanning a specially crafted file. In other words, the attack works without user interaction provided that the file finds its way on to the target system (for instance via a download).

Microsoft lists several scenarios that attackers could exploit. Attackers could use websites to deliver specially crafted files to users, attach them to emails or messaging programs. One of the easiest options that attackers have at their disposal is to attack user systems through specially crafted JavaScript files loaded when a user opens a site in a web browser.
Microsoft anti-malware products are configured to scan files automatically by default. The file the attack is carried out with would be scanned immediately on systems with real-time protection enabled.
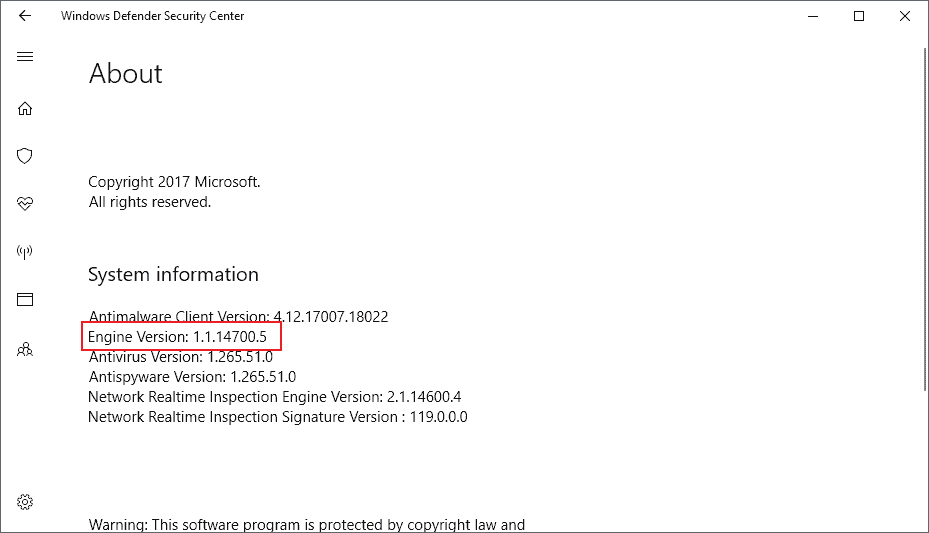
Microsoft released an update for all affected products that corrects the security issue. Windows systems with the engine version 1.1.14700.5 or later are protected from the vulnerability.
You can verify the version on consumer versions of Windows in the following way (thanks Woody)
- Windows 10: Use Windows-I to open the Settings application and go to Update & Security > Windows Defender.
- Windows 8.1: Tap on the Windows-key to open the Start Menu. Type Windows Defender and select the result. Select Help > About in the program window.
- Windows 7: Open the Start Menu with a click. Type Windows Defender and load the result. Select Help > About.
While it is possible to update definitions manually, updates to Windows Defender's malware engine come through Windows Update. You may want to run a manual check for updates if the reported malware engine is lower than the version the patch was introduced in.
- Tap on the Windows-key, type Windows Update, and select the result.
- Click on check for updates and follow the instructions.
An article on Bleeping Computer offers more information about the vulnerability. According to information posted on the site, it was a Google security researcher who discovered the flaw in mpengine.dll. Microsoft rates the bug as critical, the highest severity level as successful exploitation of the vulnerability may grant an attacker full control over the system.
Systems with third-party security software and a disabled Windows Defender or other affected Microsoft security product are not affected by the vulnerability. It is still recommended to update the malware engine as soon as possible to the latest version.


















I managed to manually update the (disabled by av) Windows Defender engine to version 1.1.14700.5 on my Win7 Pro SP1 x64 doing this (not my invention):
Log in as admin to temporarily disable your real time av.
Run: “C:\Program Files\Windows Defender\MSASCui.exe” -Update
(or whatever your path to it is).
When I did this this morning, it was only updated to version .4, but when I did it again tonight it updated to version .5
Good luck
Run command prompt in admin mode and copy and paste this then run. It creates a scheduled task to check updates every hour.
schtasks /create /tn “Defender Definition Update” /sc HOURLY /ru SYSTEM /rl HIGHEST /tr “‘C:\Program Files\Windows Defender\MpCmdRun.exe’ -SignatureUpdate -MMPC”
I run Windows 7 and I’m confused about a discrepancy between what Martin wrote here and what Woody Leonhard wrote at AskWoody.
Per Martin:
“It is still recommended to update the malware engine as soon as possible to the latest version.”
Per Woody:
“If you don’t have [the updated Windows Defender Malware Protection Engine] yet, there’s nothing you can do. Windows Defender updates go through whether you’ve enabled Windows Update or not — they even go through if you’ve turned off the Windows Update service. In theory, you should be receiving the new version today or tomorrow. [ https://www.askwoody.com/2018/is-your-machine-running-the-latest-malware-protection-engine/ ]”
I’m hoping Woody is right, because (like Jonnyredhead) I haven’t seen a method for manually updating, and I’m not seeing a way to pick up Windows Defender *engine* updates in WSUS Offline Update (unless they’re classified as a standard Windows 7 security-only updates).
Mine just updated.
Never mind, I guess. My Windows 7 Windows Defender was an older version when I checked it a couple of hours ago, and it’s up to date now. All *I* did was to manually update Windows Defender definitions (which did not in itself seem to trigger the protection engine update) and to do a WSUS Offline Update run (which ended up installing nothing). I’m *guessing* it really *did* just update itself, even though my Windows Update service is disabled.
Is there a link to manually update windows defender engine for Win7 x64.
Testing
I disabled WD a long time ago using Autoruns.
Malwarebytes takes care of my system security these days.
@TelV:
I use Kaspersky Free as my primary real-time antivirus but I decided to leave Windows Defender running, since (so far as I know) it doesn’t conflict with any other real-time anti-malware packages* and I have to disable Kaspersky from time to time, e.g., to update VirtualBox extension packs. I want something running in background when Kaspersky protection is off, especially in case I forget to turn it back on right away.
*I remember reading a gHacks article saying that something akin to the old EMET protection was coming to Windows 7’s Windows Defender sometime this summer. If and when that happens, I suppose Windows Defender could start conflicting with Malwarebytes Anti-Exploit, like I *believe* EMET did.
I was lucky in that I purchased a lifetime license to Malwarebytes Premium for $23 about three weeks before the offer ended. So now I don’t have to pay anything for it ever again.
At the time though it didn’t have an AV function, but I wasn’t too bothered by that because malware has changed now and its main function is to part you from your money whereas before it was just script kiddies who took peverse pleasure in causing havoc with the OS.
Since version 3.0 though Mbam now includes as AV function and registers itself as the primary antivirus in Windows whereby WD will be terminated anyway.
Everyone cries about windows privacy then uses a Microsoft program that scans every file on their pc?
/eyeroll
Yes, they do….which is why Defender has not been allowed to run on any of my Win10 PCs for many months.
I just don’t get why anyone would use it. Little more than spyware masquerading as…..
I got a large Windows Defender update of about 33MB yesterday. It was a single update since I had received other Windows Defender updates earlier. Most Windows Defender updates I receive are one to two megabytes but some are larger. Large updates make me nervous since I don’t know what they contain and I don’t want Microsoft snooping through my files, although none are illegal.
It ‘s the principle of it.
When I read Woody’s post on his website today, I checked my Windows Defender engine version and it was the updated one.
I think that the large update was the one which updated the engine.
@Mark Hazard can you please elaborate how you got the updates?
Did you make Defender check for updates, or were they installed automatically?
Martin,
Your article needs a small correction, it says CVE-2018-098 in the second sentence, but it should read CVE-2018-0986.
Otherwise, it’s a great article, keep up the great work.
Thanks for the article. Validates my decision to ditch Defender and Security Essentials and surf with JavaScript toggled off.
Thanks a lot for the details and picture !
Martin, it says 3 comments but does not show any of them.
Use the classic version if viewing on mobile. It works great.
Yeah the comments seem to vanish. A lot of articles show comment counts, but don’t show any even with a page refresh, but I’ll come back a half hour later, and see them. I tried Firefox and Chrome. Same thing.
Thanks for the heads-up. Mine is showing updated to the correct version, but I haven’t had a Windows Update since 03/22/2018. Maybe it came in through the cumulative updates on that day?
Sorry, just noticed I have two definition updates today. The first one, about 10 hours ago, I downloaded myself by doing a manual check for updates. Since then MSE received another. The one that included the new engine was: “Definition Update for Microsoft Security Essentials – KB2310138 (Definition 1.265.36.0)”.
If you have “Definition Update for Microsoft Security Essentials – KB2310138 (Definition 1.265.51.0)” which I downloaded today you should get the new engine version. I have Windows Update set to manual, I checked my engine version number and it was the vulnerable one, downloaded the definition update and verified it includes the new engine.
As far as Windows Updates go I still haven’t done the March updates. I have Windows Update set to ‘never check’ but it still pulls the definition updates for MSE on Win7.
I’m not 100% sure but Engine updates may not be listed as individual updates as they may have no KB attached to them. Maybe someone with deeper knowledge can chime in and explain this in more detail.
I did a manual Check for Windows Update about 22:00 EDT 2018-04-03 and got the Defender level you reference. It was not available earlier that day with a manual check. Windows Update never shows Defender Updates in its history. Instead while in the initial Windows Update screen, click on Defender on the left for current Defender levels.
“about” is the correct link for https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-0986 but in words you say CVE-2018-098. It should be 0986.
“Windows Defender updates go through whether you’ve enabled Windows Update or not — they even go through if you’ve turned off the Windows Update service. In theory, you should be receiving the new version today or tomorrow.” according to Woody Leonhard.
In MSE: Open>Help>About.
Thanks Sebas!
Martin, why did you delete my comment? :(
I have not deleted your comment. I see two of your comments on the page, did you write more?
Yes. They reappeared again after sometime. Strange. Even when I refreshed the page, they were not there — so I thought you had deleted them. I see them now with the ‘Classic version’ of your site.
Comments are in a poor state for a little while now…. very odd.
I wonder if it would be wise to put a banner on the page to notify people that there are intermittent issues with the comments, so nobody gets the wrong idea.
But, Martin, where’s the anticipated ending of the article? You know that line: “Now, you… what security software do you use? And, is your MS Security System differs from the version above?” :D
Youpieeee! Mine is engine version 1.1.14700.5.
What a relief! :D