How to block ports in Windows
The following guide walks you through the steps of blocking specific ports on a Windows machine to harden the computer system.
Most Windows users don't come into contact with ports on a regular basis, or at all. While some may encounter ports when they set up a new email address in a desktop mail program, or when standard ports such as 80 or 21 are mentioned in news articles, ports are usually ignored for the most part.
Ports broken down to the core enable communication between a Windows PC and something else, for instance Internet sites or mails servers.
Windows is configured by default to have certain ports open. This is usually done for compatibility purposes to avoid issues when certain services are used.
It is a good idea however to close ports that are not use to harden the system and avoid attacks against these ports. The recent SMB ransomware incident for instance could have been avoided for instance if the port would not be open by default.
Which ports are open anyway?

If you never checked ports on a Windows machine, you may wonder which ports are open on it, and how to find that out.
I suggest you use programs for that, as they offer more details and are more accessible than other means.
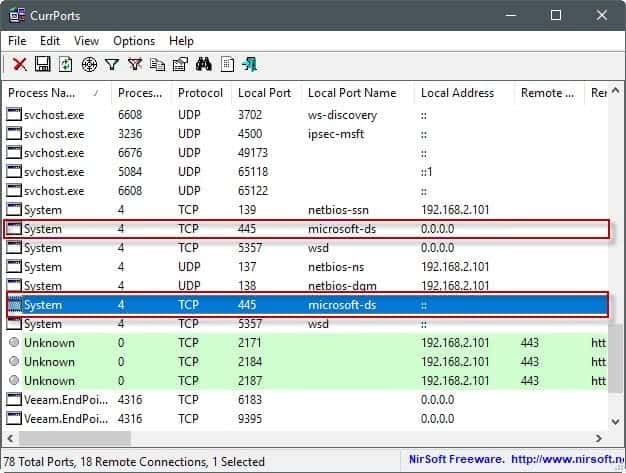
You may use a program like Portscan for that, or, and that is my favorite, Nirsoft's CurrPorts instead (see updated CurrPorts review here).
CurrPorts is a free portable program that you can run right after download. It lists all programs and services in the interface, all Internet connections, and all local ports that are open at that time.
The list of open ports may be useful on its own, but most of the time you may have a hard time deciding whether it is required for functionality, or not. There is also the case where you may need the functionality on a network, but not over the Internet.
You do need to research the ports that you don't know about to make an educated decision about that. One site that you may find useful for that is Steve Gibson's website where you can search for ports and get information on many common ones.
You may also run port checks from the Gibson website directly by clicking on one of the available port scan options there (e.g. common ports, file sharing, or all service ports). You need to concentrate on the ports listed as open in this case.
Blocking ports in Windows
Once you have made the decision to block a port on a Windows machine, you need to find a way to do so. Most personal firewalls, including Windows Firewall, support the blocking of ports. You may also block ports if you have access to the admin interface of a router or modem, as many come with options to do that as well.
The benefit of blocking it in the router is that it is blocked for all devices you use on the router level. So, if you'd block it on the machine level, you'd have to do so for any device you use at that point or in the future.
Blocking ports using Windows Firewall
The process itself is simple, and should not take long to complete:
- Tap on the Windows-key, type Windows Firewall, and select Windows Firewall with Advanced Security from the results.
- Click on Inbound Rules when the firewall window opens.
- Select New Rule from the Actions pane.
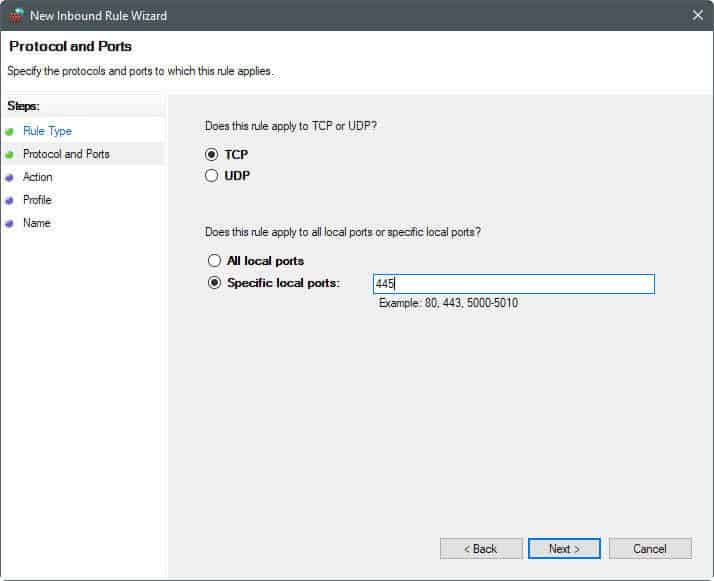
- Select Port from the Rule Type listing.
- Select TCP or UDP, and specify the ports, or a port range (e.g. 445, or 137-139).
- Select block the connection.
- Select when the rule applies (leave default if unsure).
- Add a name, e.g. Port 445, and a description, (e.g. reason for blocking, and date/time).
Note: It can happen that you run into issues after blocking ports on the machine. Apps may not work properly anymore, or you may not be able to connect to certain resources. If that is the case, the port that you disabled in firewall may be needed for that. You can undo the blocking of ports at anytime in the firewall as well.
Repeat the steps for any other port that you want blocked on the Windows PC.
Second note: Programs such as Nirsoft's CurrPorts will still reveal that services or programs are listening on those ports. This does not change when you block ports on Windows. What happens however is that the connection to these services and programs is refused, because connections to the port are blocked by the system.
Closing Words
It is not difficult to block ports on Windows PCs. While you may spend some time researching the open ports before you start blocking them, doing so will pay off in the long run.
Some ISPs have started to block common attack ports on behalf of their users as well to reduce the attack surface. You can run scans on Gibson's website to find out if that is the case for you.
Now You: Do you block ports on Windows? If so which and why?


















Thanks a lot Martin !
Perhaps I have understood it incorrectly, but blocking mentioned ports with a FW is only possible if it’s an external FW, as I have understood the Win OS is still circumventing any SW FW?
Thanks Martin, for another great post.
Maybe a little off-topic, but i’d like to do something a little different : block access to specific IPs that a random app wants to connect to.
Comodo Firewall does it nicely (I have a popup and decide to authorize or not every time there is an external connection). But Comodo has become quite buggy, and sometimes I have no other choice but restart my laptop.
Could anyone suggest a lighter app that does exactly this job ?
Thanks,
DV
I appreciate the effort to write this article, but it really deserves an overview to avoid confusing newbies.
Internet based scanners (like grc Shields Up) will detect open ports on your LAN edge (firewall) router. The only open ports you should see are those that You select in the routers admin setup; example is port forwarding for gaming use. IMHO you should always turn off Universal Plug and Play as a typical (weak and confusing) vendor implementation will make your LAN vulnerable. BTW there are other free Internet based scanners that give you a finer=grained scanning capability – pentest-tools.com for instance.
The other common use case is for mobile use. Laptops should Always have a software firewall enabled. You can scan for open ports using the above tools.
I’m very surprised that Martin didn’t mention the most common port scanner – nmap. It is completely free, open source and cross platform. zenmap is their ‘official’ gui but there are probably others. Use it Only against hosts on your LAN or your ISP may cut you off.
Off-topic note to Martin – adverts on ghacks are running such sloppy, CPU intensive javascript that FF crashed six times while writing this, and I’ve had to reactivate ublock. Any way for you to stop these asshats?
Mike
Another handy tool (free) is CrowdInspect which shows current connections, ports and the option to analyze them with VirusTotal and Team Cymru’s Malware Hash Registry. No installation required.
It’s the bottom tool on the following site: https://www.crowdstrike.com/resources/community-tools/
The program / application “TCPView” from Sysinternals is also a great monitoring tool, as good as Nirsoft’s IMHO. I’ve used both for years.
A small word of caution for those with routers and testing ports via GRC’s “Shields Up” scanner:
Some routers have built-in DDoS (Distributed Denial of Service) attack protection. With DDoS enabled, when you request a (1 to 1024 or 1 to 65656 full) port scan from GRC, the scanning speed can be such that it will trigger this protection mechanism and the WAN connection witt be cut-off. When this happens, the scan doesn’t get very far before this cut-off occurs, thus you might never get to see the totality of which ports are open/closed/stealth. Therefore, to get an accurate scan of all ports you need to temporarily disable DDoS protection in the router settings, and enable the protection once the scan results are displayed on screen.
Temporarily disabling DDoS protection to do the scan does NOT put you at “great risk” since any other protection mechanism (port blocking, IP filtering, etc) in the router and on the computer being scanned are still in effect.
Go to GRC.com Shields UP they will show you what ports are closed,open and stealthed.
What really needs for windows 10 is a whitelist program firewall that will by default block everything both ways except for programs you have whitelisted for internet access. This way no telemetry/spyware/backdoor will work.
Does such program exist?
The http://winhelp2002.mvps.org/ website is an invaluable resource for setting up a hosts file to block–well, anything you wish to, really, Used in conjunction with PortMon and Wireshark, it enables one to regain some degree of ownership of one’s Windows machine.
https://github.com/StevenBlack/hosts
This repository consolidates several reputable hosts files, and merges them into a unified hosts file with duplicates removed. A variety of tailored hosts files are provided.
(It’s so much better)
What is the difference between local adress, 0.0.0.0; ::, ::1, 127.0.0.1, and my local LAN adress?
Can someone in my LAN only access the ports where it says my local LAN adress but not the other four?
Hi Ben,
See: https://www.howtogeek.com/225487/what-is-the-difference-between-127.0.0.1-and-0.0.0.0/
Thanks a lot for this information !
Do you know if Simplewall, that you reviewed a few days ago, can block specific ports ?
I use a router to block any access to ports from outside the network, and a 3rd party firewall to block other kind of threats (i.e. from inside my network, from an unsecured VM, etc.)
Anyone have a list which ports are used for that?
For example i have a NAS and Windows need/ use SMB to connect to it easy in Windows explorer. So i need SMB
Maybe this can help (discovered after my previous post) :
https://support.microsoft.com/en-us/help/3185535/guidelines-for-blocking-specific-firewall-ports-to-prevent-smb-traffic-from-leaving-the-corporate-environment
Also, as mentioned in the article :
https://www.grc.com/port_445.htm
And then choosing another port, i.e. 135, 137, 138, 139 etc …
Thanks
Nirsoft’s CurrPorts, a reference as all Nirsoft’s applications, an every moment companion.
Steve Gibson’s pages, information and probes, Gibson’s desktop applications, another reference, known and called here ever since my first sessions on the Web with XP.
Probing Port 445 and 135 with Gibson’s tester showed “Stealth”. Relief.
Now for SMB. I’d be extra cautious with that. I’ll have to quest for information in order to initiate an educated modification if applicable. I have disabled SMBv1 (only, don’t touch SMBv2!) server and client but haven’t modified any associated port(s) because I lack information regarding SMBv1 and affiliated port(s).
I have to express once again, flattery-free, my gratitude to Martin for always bringing information, relevant information and always at the right time as if he was aware of what the latest concerns of users truly are. A problem or problematic is in the air? Most likely popping in here will show the matter, explained and discussed. gHacks is a reference as well:)
I agree. However, I found an issue when setting up a Windows system foe a blind user.
I had installed Avira antivirus software, and it continually flagged (and quarantined) many of the NirSoft tools, in spite of trying to whitelist them.
Unfortunately, Avira seems opaque to user feedback, so it’s either run in Safe Mode, or uninstall Avira. :-P
Be it Avira, be it Google which at one time would block (within its SafeBrowsing lists) access to Nirsoft’s pages (the developer complained more than once and that’s why I know it, not using Safebrowsing myself). I could even give an example of a perfectly healthy application nevertheless flagged at VirusTotal because, maybe, of its ability to find and remove hidden Registry keys.
Who to trust nowadays? Many among us, the users, far less among the corporations.
Otherwise, my opinion on so called antivirus, anti-malware, “global Internet security” and tutti quanti relies more on those of IT professionals who insist on the predominant value of firewalls than on the very questionable pertinence of those global security “protectors”.
My neighbor uses a free anti-virus, anti-malware, not sure if its Avira, but I know he called me last week because of terrible lags, to what I proposed to run HitmanPro, just to have a look : the result? The computer was infected, with malware cookies, trojans … so his anti-malware, you know, I sort of smile.
Hi martin thanks for the info,
can you write a tutorial on how to unblock torrents ports to have high speeds(when not configured properly)
Now, how to block Microsoft spying and telemetry…
DoNotSpy10 is the world’s first antispy tool for Windows 10. Its straight-forward user interface allows you to manage how Windows 10 respects their privacy.
http://pxc-coding.com/portfolio/donotspy10/
O&O ShutUp10
> Impossible without enterprise/education version.
Those tools he mentioned will block some of it. That’s better than nothing.
Impossible without enterprise/education version.