Windows 10 Limited Periodic Scanning explained
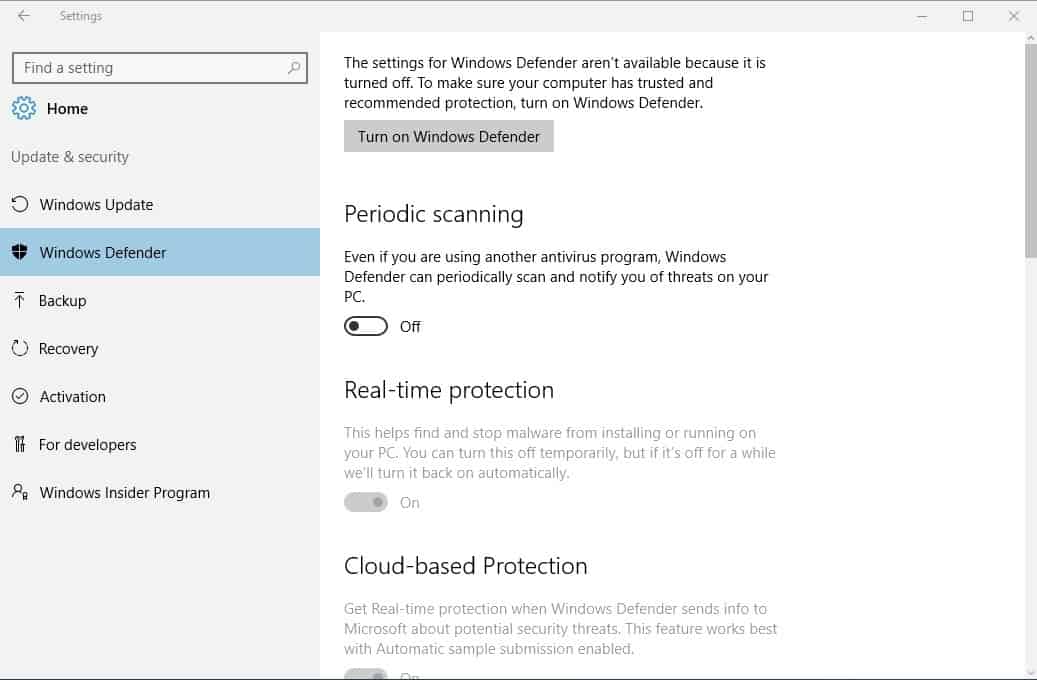
Limited Periodic Scanning is a new feature of Windows 10's Anniversary Update edition that configures Windows Defender to scan the system in intervals even if other antivirus solutions are used primarily.
The main idea behind the feature is to improve system security by using Windows Defender as a second-opinion scanner on Windows 10 devices.
Microsoft Malicious Software Removal Tool scans detect between 1 and 2 million infections on machines each month, and Microsoft notes that some of these happen on machines with third-party antivirus solutions running on them.
Limited Periodic Scanning

Limited Periodic Scanning is an optional feature that is not enabled by default. It becomes available only if Windows 10 detects that another antivirus solution is installed and running, and needs to be enabled by the user or administrator of the device first.
In other words, Periodic Scanning becomes only available if a third-party antivirus software is listed on the Security and Maintenance Control Panel applet of the Windows operating system.
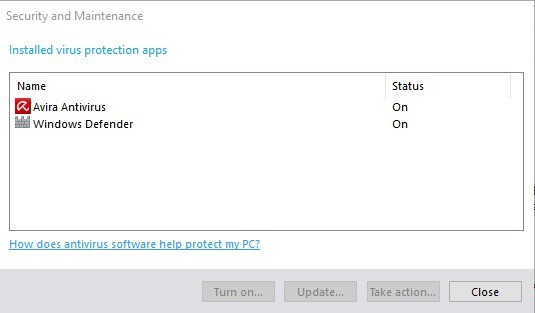
You can verify that in the following way:
- Use the keyboard shortcut Windows-Pause to open the classic Control Panel. If the Pause-key is not available on the connected keyboard, use the shortcut Windows-X instead and select Control Panel on the menu that opens.
- Select System and Security in the next step. You find the link in the Control Panel address bar if you have used Windows-Pause, or listed as an entry if you have used the Windows-X menu.
- Click on the Security and Maintenance link on the page that opens.
- Expand the Security listing on the next page.
- Locate Virus protection afterwards, and click on the view installed antivirus apps link.
- The window that opens lists the recognized antivirus solutions.
Configure Periodic Scanning
Periodic Scanning is a new option in the Settings application of Windows 10. The feature does not appear to be available as a policy currently.
Do the following to configure the new feature:
- Use the keyboard shortcut Windows-I to open the Settings application on the Windows 10 device.
- Select Update & Security when the window opens.
- Select Windows Defender using the left menu on the next screen.
- There you should find the periodic scanning option.
- Switch it from off to on.
To turn periodic scanning off again repeat the process, and switch the option to off in the last step.
The feature uses Automatic Maintenance to determine the best time for a scan and prevent scans during times when the computer is used actively or resources are needed for other processes.
When you enable Windows Defender Periodic Scanning on Windows 10, you will be able to use the user interface and history tab of the program to manage threats even if the application itself is not turned on.
Furthermore, you will get notifications if Windows Defender detected threats during a periodic scan, and may click on those notifications to be taken to the history tab of the program right away.
Closing Words
Periodic Scanning offers frequent second-opinion scans on devices running Windows 10 if another recognized antivirus solution is installed and if the feature is enabled.
This is just one option that you have as you can run third-party security programs as well as second opinion scanners.
To name a few: Trend Micro Anti-Threat Toolkit, Kaspersky AVZ Antiviral Toolkit, or Malwarebytes Anti-Malware.
Now You: do you use Windows Defender?


















defender not showing limited periodic scanning option. how to turn it off?
Windows defender not showing limited periodic scanning option. i want to turn it off.
I wouldn’t trust my PC to Defender/MRT…ever.
Windows 10
I use Bitdefender
My Windows Defender is desactivated and not “reactivable” (grey)
The security panel mentions only Bitdefender
In other machines I saw, WD is activated and not desactivable (grey too)
Do you know anything about it ?
I think for the normal user Defender is enough. I think the rest can be avoid by using the well known tricks, not download or open email attachments and this. It’s normally well known but somehow in 2016 is still seems a huge threat.
Maybe in the school is something wrong, I think they should teach a little bit about social networks, the dangerous about unknown sources and some ‘common’ pc things, it all starts with the knowledge.
I don’t use any antivirus at all, period. They are not only useless, in that they never detect any real threat, but downright harmful and annoying, as they bog down the system and yes, if I, as a matter of rare exception, happen to have a file named “keygen” or something else in a similar vein, they will just block it or otherwise get in my way. Windows defender permanently disabled. I use cation and common sense, and I run files through Virus Total.
How is this different than Windows 7. I have both Windows Defender and ESET. They are both activated. No ill effects.
jimp: Is something else really necessary?
WD uses “definitions” which are hashes of known malware viruses. This means that once a malware has been recognized, an hash (fingerprint) has been created and the malware can be found through WD scans. This is an old way of AV – still useful – that leaves 0-day malware undetected. That means: if a malware has no hash on your latest definitons, WD can’t do anything. Newest AV engines use behavioural analysis of malware code.
CHEF-KOCH: each time a new definitions-update is available Defender anyway scans.
Not useless if the update reports your browsing, your recent opened files and whatnot to Redmond Servers.
I use only Windows Defender and have never had a problem. Is something else really necessary?
Nope. And Periodic Scanning seems like an integration of the Malicious Software Removal Tool and/or Safety Scanner with the Antimalware Service that Defender uses.
https://blogs.technet.microsoft.com/mmpc/2016/05/26/limited-periodic-scanning-in-windows-10-to-provide-additional-malware-protection/
Everything is enabled by default. Nah. Definitely not, just open gpedit.msc and see that most is not set/disabled. The stuff which is enabled, was enabled for every Win OS (okay except the brand new stuff maybe).
I see this option critical, because each time a new definitions-update is available Defender anyway scans. A bit useless imho.
CK, you have heard that ISPs servers fast-track users page-requests when they see “Speedtest.com” et-al, coming in? The users sees the test report 5-MB/sec, but then their actual surfing page requests get directed to the mainstream, 1.2MB/Sec clogged rate.
A “devious” mind could do a similar thing for gpedit.msc when it is launched, show “special,” stuff as “disabled” but only while gpedit.msc is open.
If it’s from msoft and it looks to good to be true…
Sorry I not understand what you want to say, of course the page fingerprint mechanism is widely in usage today, amazon and other popular cdn’s using it. But to compare this with gpedit … it’s a bit strange, I didn’t know that it maybe not shows the real status?! I was always thinking it detects directly stuff from regedit/secpol by loading the entries from there. But if you found something on this, feel free to contact me on GitHub. :)
And if group policy editor was something intended for your average user you’d be getting close to being partially correct, firstly group policy editor isn’t included in the Home edition of Windows, secondly if a setting in group policy editor is not configured then typically that means it’s enabled.
Speaking of GPE, I noticed that in Insider Program you couldn’t for example, disable Start search with it in some builds – chosen settings were ignored. That makes me wonder, what’s the real power of that tool in W10 nowadays.
And that’s why i said group policy editor isn’t included in the Home edition of Windows, I’m fully aware it’s possible to download or add the feature but for your average user it’s not.
I also said not configured typically means it’s enabled as I’m aware that’s not always the case, feel free though to add up all the different group policies defaults and sort them into default states of enabled and disabled so you can find out what’s the typically setting.
Either way i think you’ll find group policy editor is not something intended for your average user.
https://technet.microsoft.com/en-us/library/dd367853.aspx
Gpedit for Home users:
https://www.itechtics.com/enable-gpedit-windows-10-home/
Of course it’s additional and the user needs to do some steps but it’s still possible. This trick is also not new because it exist since Win 7/Vista.
> if a setting in group policy editor is not configured then typically that means it’s enabled.
Nope, a lot of settings are not configured and this really means sometimes it’s not activated, for example most of the network stuff, it’s also depending if you work under domain or workgroup (could be the reason maybe).
“Would you like to enable The One Eye NSA Client?”
No.
*SOMETHING HAPPENED*
“an optional feature that is not enabled by default”
That has to be a first for Windows 10, normally everything’s enabled by default.
The amazing part is that it’s optional.
Even better that you can uninstall Windows Defender.