Public Key Pinning in Firefox 32 to protect against MITM attacks
Public Key Pinning (PKP) is an extension to the HTTP protocol that is in draft status currently over at the Internet Engineering Task Force (IETF).
It allows web services to reduce the number of authorities that can authenticate the domain by instructing clients to only use a specific subset of authorities instead of accepting any root certificate that ships with the browser.
The technique is designed to reduce the chance of man in the middle (MITM) attacks under certain circumstances and protect against rogue certificate authorities.
The security feature works only on the second visit to the site and not on the first as information about certificate authorities that the site accepts need to be submitted to the client during the first visit. This is called trust on first use (TOFU).
This means that it won't help if a rogue certificate is used during the first connection attempt or if a man in the middle attack is happening at that time.
Another issue for site owners is that improper pinning may result in their sites or services becoming invalid.
A pin in this context describes the relationship between a hostname, say a website like Amazon, and a cryptographic identity.
Starting with Firefox 32, Firefox will support Public Key Pinning. Firefox 32 is currently available as a beta version and will be made available to stable users of the browser on September 2, 2014.
Firefox displays the lock icon indicating a secure site as normal if a certificate authority specified by a site the browser is connecting to is known by the browser. Firefox will reject the connection otherwise if that is not the case.
If the latter is the case, a secure connection failed error is displayed in the browser.
It is interesting to note that Firefox will ship with built-in pins just like Google Chrome does. This integrates pinning instructions for select domain names to overcome the trust on first use issue as information are present in the browser from the get go.
Starting with Firefox 32, Firefox will ship with pinning information for Twitter, Mozilla AMO and Mozilla CDN host names. From Firefox 33 on, it will add Google and additional Twitter domains to that list. From Firefox 34 on, the list will be extended with the Firefox accounts domain, TOR, and Dropbox.
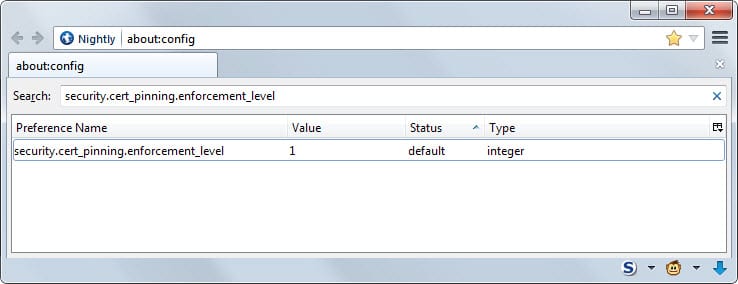
Pinning Preference
Pinning is enabled by default in Firefox 32 and newer versions of the browser. A preference is provided that controls the feature.
security.cert_pinning.enforcement_level
- 0. Pinning disabled
- 1. Allow User MITM (pinning not enforced if the trust anchor is a user inserted CA, default)
- 2. Strict. Pinning is always enforced.
- 3. Enforce test mode.
The default value of the preference is set to 1. This can be changed to 0 to disable pinning or 2 to enable strict pinning.
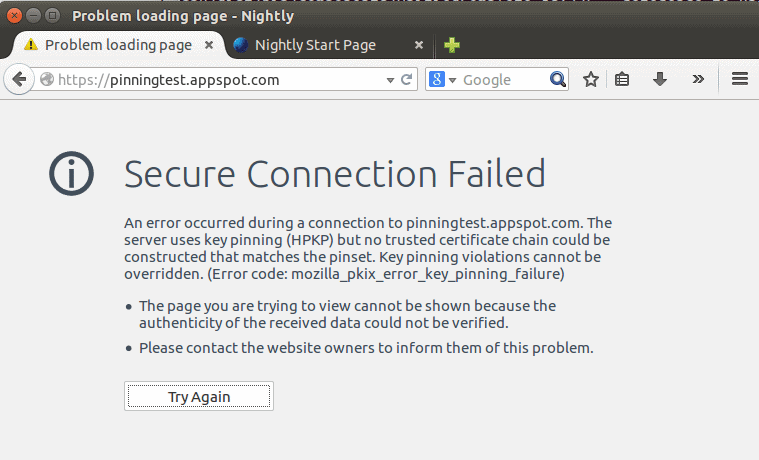




















“Allow User MITM” can be useful if you have a security solution (i.e: antivirus) that scans your HTTPS traffic. In this case, using “2” can break things…
The question that arises is why other websites are packed into the built-in list far later, especially Google, than others?
Also it would be of interest if the list can be edited by the end-users. At least if an end-user has a trusted source for those pins, the list can be used to decrease MITM surface.
mmmm .. Tofu :)