Flash tops the Exploit Kits Chart in 2016 again
If you needed another reason not to use Flash anymore, a new security report by Recorded Future may convince you to consider this at the very least.
The company analyzed 141 exploits kits that were available between November 16, 2015 and November 15, 2016.
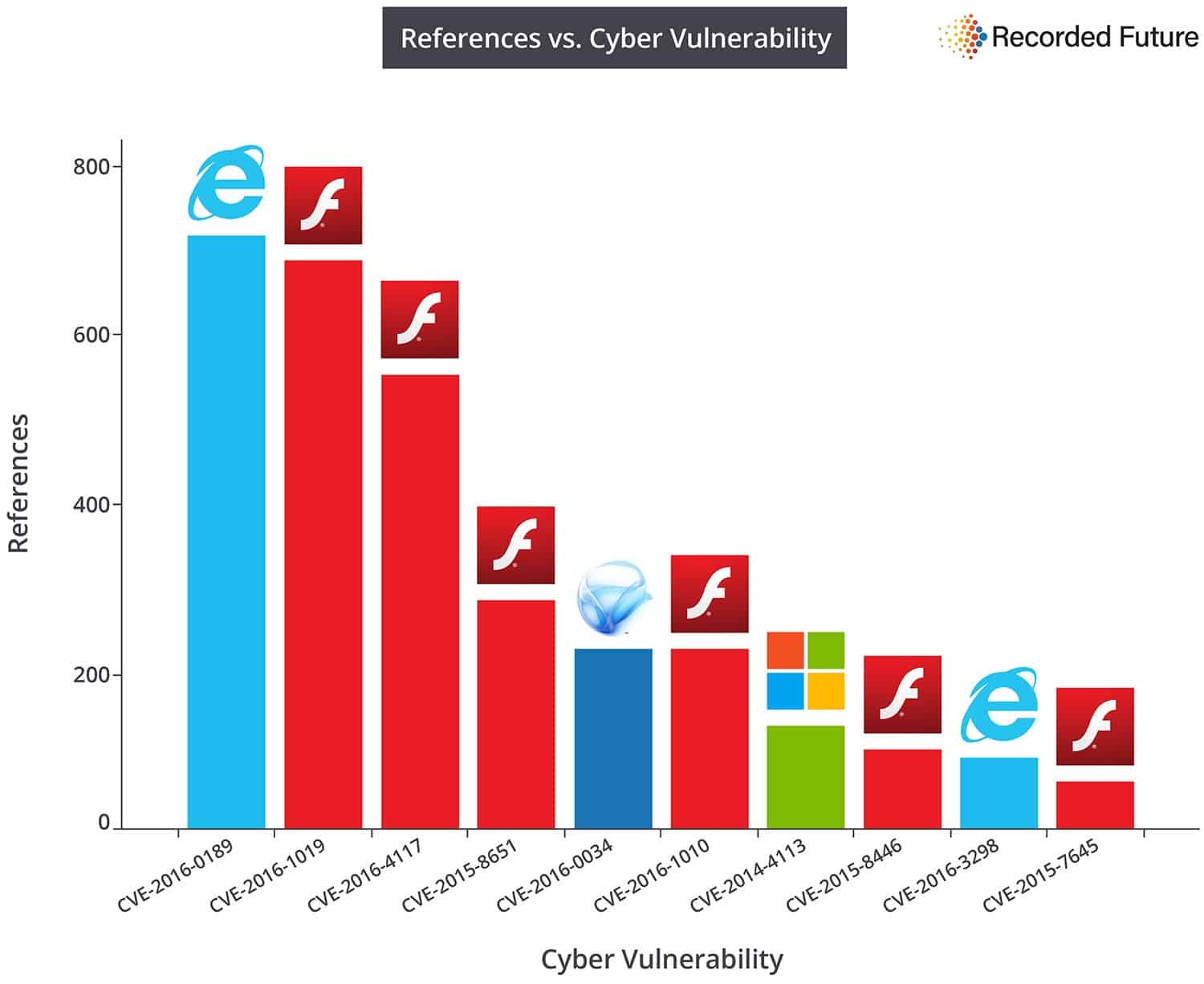
The main takeaway of the research study is that Adobe Flash vulnerabilities made up six of the top ten chart spots.
Flash was not the only software that exploit kits targeted in the past year though. In fact, a vulnerability in Microsoft Internet Explorer tops the chart, followed by three Flash vulnerabilities and then a Microsoft Silverlight vulnerability.
A Windows vulnerability comes in at seven, and another Internet Explorer vulnerability at nine. The remaining places are all filled by Flash vulnerabilities

Flash did better this year than last year. Last year, Flash topped the first eight places of the top ten vulnerabilities list used by exploit kits, with Internet Explorer and Silverlight taking up the last two spots.
As far as the methodology is concerned that Recorded Future used to generate the report: it did not reverse engineer exploit kits or use other forms of direct analysis. Instead, it used meta information available on the Internet to compute the information.
Recorded Future did not reverse engineer any malware mentioned in this analysis and instead performed a meta-analysis of available information from the web. Exploits for dozens of other vulnerabilities are currently employed by EKs and this report’s intent is to highlight top targets of popular exploit kits.
This means that the vulnerabilities are not necessarily graded by severity, or impact on user systems. Instead, the vulnerabilities are graded by references made to them on security sites, forums and such.
This can be easily seen by looking at the vulnerability adoption by exploit kit chart that the company created.
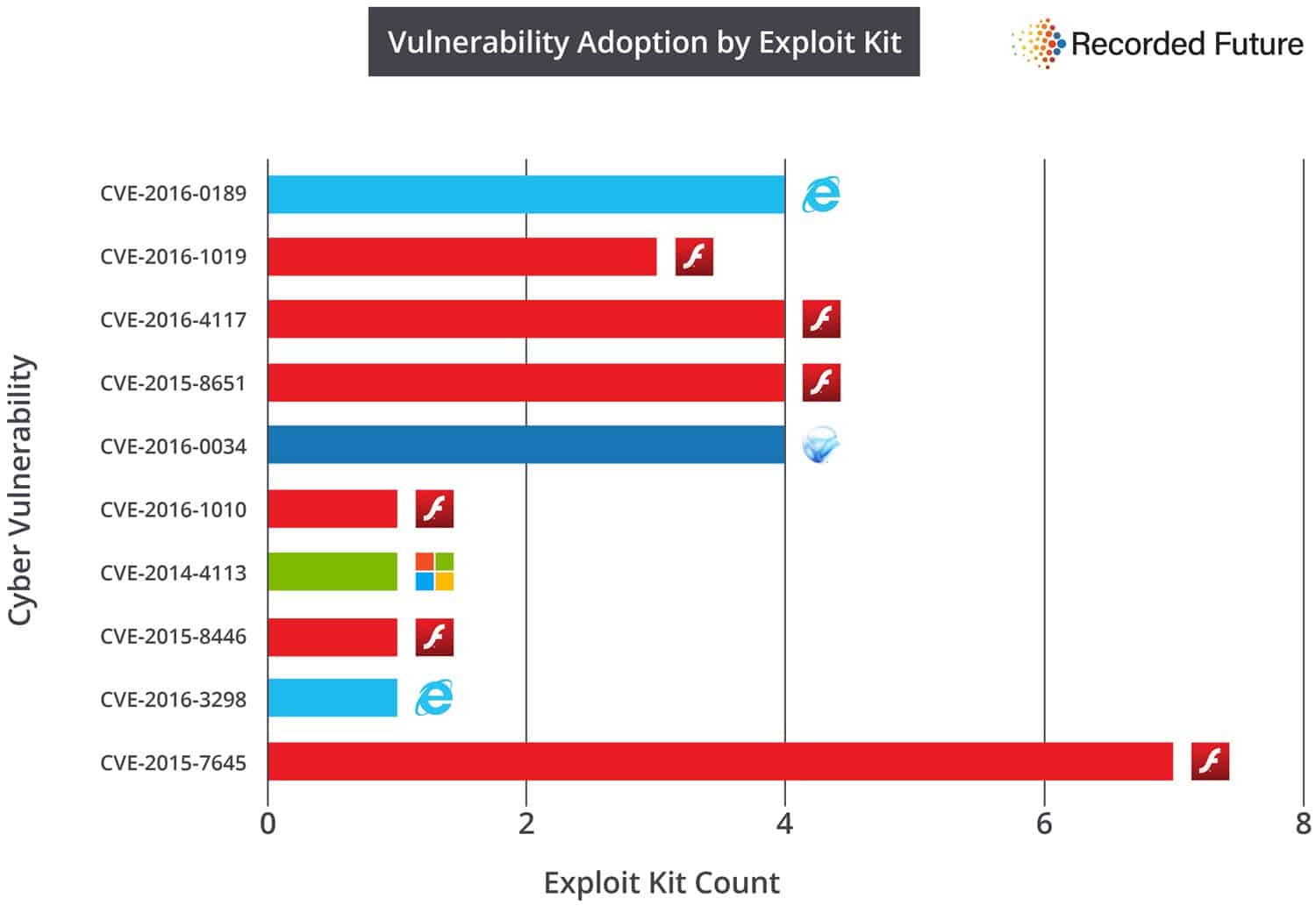
While the first five vulnerabilities listed were all exploited by three or four exploit kits, it was the Flash vulnerability in the tenth spot that was exploited the most (seven times).
The report ends with recommendations. These include the usual: patch your system and software, remove software if it is not required for core business processes, enable click to play, use script blockers, create frequent back ups, and use Chrome if possible.
The top 10 vulnerabilities
CVE-2016-0189 -- The Microsoft JScript 5.8 and VBScript 5.7 and 5.8 engines, as used in Internet Explorer 9 through 11 and other products, allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka "Scripting Engine Memory Corruption Vulnerability
CVE-2016-1019 -- Adobe Flash Player 21.0.0.197 and earlier allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via unspecified vectors, as exploited in the wild in April 2016.
CVE-2016-4117 -- Adobe Flash Player 21.0.0.226 and earlier allows remote attackers to execute arbitrary code via unspecified vectors, as exploited in the wild in May 2016.
CVE-2015-8651 -- Integer overflow in Adobe Flash Player before 18.0.0.324 and 19.x and 20.x before 20.0.0.267 on Windows and OS X and before 11.2.202.559 on Linux, Adobe AIR before 20.0.0.233, Adobe AIR SDK before 20.0.0.233, and Adobe AIR SDK & Compiler before 20.0.0.233 allows attackers to execute arbitrary code via unspecified vectors.
CVE-2016-0034 -- Microsoft Silverlight 5 before 5.1.41212.0 mishandles negative offsets during decoding, which allows remote attackers to execute arbitrary code or cause a denial of service (object-header corruption) via a crafted web site.
CVE-2016-1010 -- Integer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors
CVE-2016-4113 --Unspecified vulnerability in Adobe Flash Player 21.0.0.213 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors
CVE-2015-8446 -- Heap-based buffer overflow in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via an MP3 file with COMM tags that are mishandled during memory allocation
CVE-2016-3298 -- Microsoft Internet Explorer 9 through 11 and the Internet Messaging API in Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allow remote attackers to determine the existence of arbitrary files via a crafted web site.
CVE-2015-7645 -- Adobe Flash Player 18.x through 18.0.0.252 and 19.x through 19.0.0.207 on Windows and OS X and 11.x through 11.2.202.535 on Linux allows remote attackers to execute arbitrary code via a crafted SWF file, as exploited in the wild in October 2015.

















People have been brainwashed. You don’t just magically get hacked just by running a Flash web page. Just block ads and trackers and make Flash click to play and you’re safe.
People and companies as well, then. Click-yo-play is essential but may not be sufficient if the user gets tricked by an appealing video the same way a fish decides to bite a lure. Then it’s too late. I see no brainwashing here, even if elsewhere briefing is a pain, such a pain that we may get to be aware of it even when not applicable. This is not a hoax, a myth, search the Web and you’ll find many trusted, independent experts who all agree : Flash is and remains, together with a handful of applications, the source of the majority of security problems. This is a fact, not brainwashing. Not to mention privacy.
Also privacy wise, you’re unique in the world with JS and you’re unique in the world with Flash. Same shit.
Flash is not a problem if you don’t run it except when you know it’s a central piece to the content you actually came here to see.
Ads and trackers are the problem.
But if you want to focus on tech, JS is the worst offender not because it is less secure but because it’s always on everywhere. If you take one JS page and one Flash app, yes, going the Flash route is easier for the attacker. But it’s tens of thousands of cross-site communicating JS pages against a couple Flash apps these days. So statistically, I don’t trust either one more than I trust the other. Just enable what you need when you need. (Except the web without JS is WAYYYY more impracticable than the web without Flash, so most people can’t block JS, and those who can have to allow it way more often than they do Flash)
I haven’t used Flash in a couple of years. Sadly, being a college student I have found that there are a ton of legacy programs that require flash, especially in education. When this occurs, I do everything in my power to use the institution’s computers rather than my personal computers.
I’ve been staying clear from Flash since January 2015, if a website does not want me to show it’s videos I just close it and never come back, fortunately most use Youtube.
The only site I did not boycott was the BBC, I just have to ignore the “video news”, their radio “I-player” does not need flash anymore, and their streams works on any capable outside player.
Staying clear from Flash, like others from tobacco or alcohol! And I totally agree!
Yet I wouldn’t boycott a site for the sole reason of its stubbornness to handle Flash only; I would be tempted though given the exasperation such sites provoke but I’d consider that the content of such a site is not indexed on its video policy.
But maybe I should boycott, maybe if we all did such sites would start moving their art (“art” encrypted with the middle letter!) and not wait the day no browser will support them any longer.
If I were younger, maybe :)
who is still using Silverlight?
I’m not sure about the validity of this report considering the methodology…
@Tom
I don’t think privacy.resistFingerprinting gives privacy for real at this point, it’s a recent and very rarely enabled pref. Do we know what it does exactly on Firefox 50 ? The question I’m asking myself is whether or not it’s actually detrimental to privacy.
When this feature is ready and properly accessible to normal users it will certainly be great but the question is today.
@ Syl,
Indeed not very much is known of this Firefox setting, privacy.resistFingerprinting
Ghacks mentioned it at https://www.ghacks.net/2016/07/04/tor-privacy-settings-coming-to-firefox/ :
“A core preference is privacy.resistFingerprinting. Originally introduced in Firefox 41, it is the central preference for Tor-related settings. While it covers most Tor settings that are implemented in the Firefox browser, some are available under other preferences.”
This setting was initiated by Tor, and whether or not we “like” Tor, hard to imagine “whether or not it’s actually detrimental to privacy.” to quote your wondering.
But it is true that this setting is not over-documented, to put it mildly.
Also, if I do take into consideration Tor’s contribution to privacy settings in Firefox itself I cannot say that I’m sure all these new settings are pertinent. Not that they’d defeat their purpose — privacy — but that they could appea, maybe, maybe for some of them, inappropriate in consideration of other Firefox settings with which they could — could — pose a compatibility issue.
Hence, this privacy.resistFingerprinting has been here reset to true after I’ve removed Flash but will stay in the scope of my attention (sorry for the wording, this time I was thinking in French!).
That’s why I install click to play per element addon for Firefox and have Chrome click to play in the settings. Also one of the reason I won’t use Edge b/c it only has disable or allow globally with its flash. Still tons of Flash on the web, but you can drastically minimize its usage to necessity and your vulnerability with those settings.
After having removed Adobe’s Flash Player system-wide in August 2015 I re-installed it — only the Firefox plug-in — perhaps two-three weeks ago.
When I noticed that sites, starting with Firefox 50.0, would not recognize Flash as installed when the about:config setting privacy.resistFingerprinting was set to true, I decided to once again remove it, and I believe this time it’ll be for good.
I just couldn’t stand the idea of disabling a Firefox privacy feature — privacy.resistFingerprinting — for the sake of a video player which not only defeats privacy at its core but which moreover is an everlasting security pit as described (and reminded) in this article.
I do not understand that leading sites, France Télévisions (in France, where else?) or the BBC, many other valuable places stick to Adobe’s Flash. Why? All browsers handle HTML5 nowadays, the video is fluid, the toggle to fullscreen is fluid (Flash seems to wake up from the Dead when toggling to full-screen).
Anyway, the article comforts my decision and will remain in standby memory should I be tempted to call back Flash.