How to disable Firefox's Captive Portal test connection on startup
Mozilla's Firefox web browser tests on startup whether the network connection that is used requires a login; this is common when a device is connected to a public hotspot, e.g., when using a hotel's wireless connection.
While that is useful in some cases, it is not something that many Firefox installations require. If you use Firefox at home only, you do not need the check to be performed. It reduces the automatic connections the browser makes and may speed startup just a little bit as well.
Firefox attempts to connect to http://detectportal.firefox.com/success.txt during the test to find out if it can connect to the address. The very same address is also used to test if the active network connection supports IPv6.
Note: you may need to undo the changes if you notice connectivity issues; this should not be the case, but it is easy to undo if something goes wrong.
Disable Firefox's Network Connectivity Tests

- Load about:config in the Firefox address bar to get started.
- Confirm the "Accept the risk and continue" prompt that is displayed. You may also want to uncheck the "warn me when I attempt to access these preferences" to skip the prompt the next time.
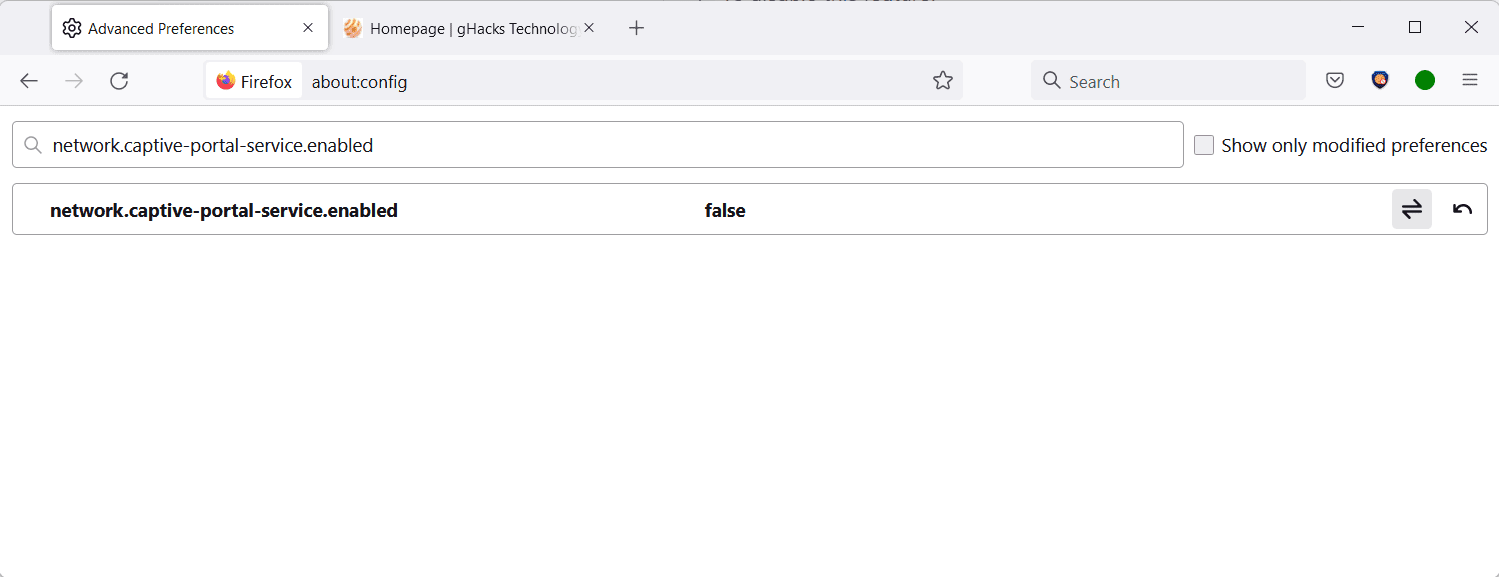
- Search for the preference network.captive-portal-service.enabled using the search field at the top.
- Set the preference to FALSE by clicking on the toggle icon located at the right. To undo the change, repeat the action so that the preference's value is TRUE.
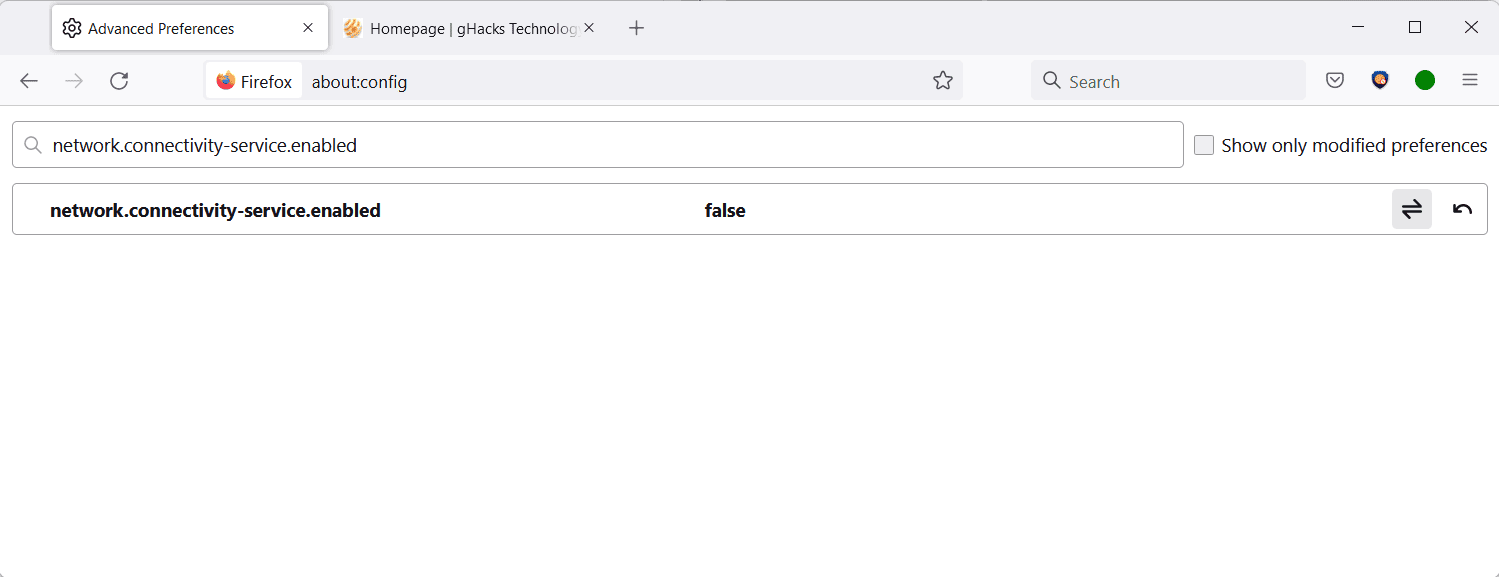
- Search for the preference network.connectivity-service.enabled using the same method as described above.
- Set the preference to FALSE by clicking on the toggle icon. To undo the change, repeat the action so that the value of the preference is set to TRUE again.
The preference network.captive-portal-service.enabled checks if the network connection requires authentication. Firefox users who travel a lot and those connecting to networks that do require authentication may want to keep the preference's default value of TRUE. Everyone else may set it to FALSE without running into any usability or connectivity issues.
The preference network.connectivity-service.enabled determines capabilities of the network connection by connecting to the very same address as network.captive-portal-service.enabled.
The Tor project disabled the functionality in its browser, without any reported issues since the change. The development team noted that Firefox makes this connection whenever the network state changes:
NetworkConnectivityService probes http://detectportal.firefox.com/success.txt?ipv4 and http://detectportal.firefox.com/success.txt?ipv6 whenever network state changes (event network:link-status-changed). We should probably disable this unless it's needed for browser functionality.
Closing Words
Most Firefox users do not need the two preferences when they use the browser. Some users may want to do so for privacy, others to reduce the number of connections the browser makes.
Now You: do you monitor your browser's automatic connections?






















Wow, imagine still dicking around with arkenfox and whatever other ‘hardening’ tips for a browser that’s beyond a joke when it actually comes to privacy while talking up a big game – instead of using one that doesn’t require any of this bullshit to begin with.
Pale Moon with Brave as a backup for the extremely rare site that doesn’t work.
And how many users use pale moon?
Probably even lesser number of users than firefox or tor browser
Use brave for all sites. It is the best combination of privacy, security and convenience
Why are installed extensions able to be queried by external entities anyway? I get screen size and browser/version etc but why should the fact that I have Custom Scrollbars installed be public?
I was suspicious with this “Iron Heart said on April 12, 2022 at 3:04 pm” post, mainly because stating what it states and where it states it seemed inappropriate. Slogans are not in Iron Heart’s rhetoric. You agree or not but one must say he substantially describes his positions.
Probably a kid trying to have fun the way he can.
I always recommend Safari in such case.
lol
My firefox maintains a constant connection to amazonaws. Bad behavior.
I’ve disabled push services.
https://www.reddit.com/r/Ubuntu/comments/bg7a6w/why_firefox_is_always_connected_to_amazonawscom/
Firefox has no comment on the problem.
https://support.mozilla.org/en-US/questions/1364245#answer-1474019
I had no idea that this went on. However, I am relatively unsophisticated using Firefox.
I just use it. I made the changes to Firefox. Thanks for the info, Martin.
What would we do without you?
I shudder to think!
It was at this very site where I’d learnt of the arkenfox user.js — then known as the ghacks user.js — and the web has been so much better for me since!
Yes, I do you monitor my browser’s automatic connections.
network.captive-portal-service.enabled has always been set to false
Moreover I block specific Mozilla links (syntax is that of DNSCrypt-proxy, *URL* means any url containing URL
At Firefox start the only connection to Mozilla here is firefox.settings.services.mozilla.com, and it is rejected with this list :
—
# MOZILLA
*activations.cdn.mozilla*
*aus3.mozilla*
*aus4.mozilla*
*aus5.mozilla*
*broker-live.mozillamessaging*
*content-signature.mozilla*
*content-signature-2.cdn.mozilla*
*crash-stats.mozilla*
*data.mozilla*
*detectportal.firefox*
*discovery.addons.mozilla*
*download.cdn.mozilla*
*error.mozilla*
*experiments.mozilla*
*fhr.cdn.mozilla*
*geo.mozilla*
*getpocket*
*hang-reports.mozilla*
*input.mozilla*
*install.mozilla*
*live.mozillamessaging*
*metrics.mozilla*
*mozgcp*
*normandy.cdn.mozilla*
*ostats.mozilla*
*perf-html.io*
*profiler.firefox.com*
*qsurvey.mozilla*
*report.mozilla*
*reporter.mozilla*
*self-repair.mozilla*
*services.addons.mozilla*
*services.mozilla*
*snippets.cdn.mozilla*
*snippets.mozilla*
*snippets-stats*
*sostats.mozilla*
*stats.mozilla*
*support.live.mozillamessaging*
*tbpl.mozilla*
*telemetry.mozilla*
*telemetry-experiment.cdn.mozilla*
*telemetry-experiment-dev.allizom*
*testpilot.mozillalabs*
*tiles.cdn.mozilla*
*tiles.up.mozillalabs*
*treeherder.mozilla*
*versioncheck-bg.addons.mozilla*
*zlb.phx.mozilla*
—
I’ve always used Firefox but it’s not because you like/love someone that you don’t wish once in a while to have that person shut up. The advantage of a browser is that it’s not emotional, susceptible. Maybe in a few years you’ll hear the browser scream ‘Hey, you, why you make me shut-up, why you forbid me to phone home?” Well, because you happen to be indiscreet.
Just a quick “thank you” to Martin for continuing to cover important Firefox “about:config” issues and others.
Thank you!
Thanks, Martin, for this great article. Really great security (and speed up) setting.
Keep up the good work.
Yes, thanks for posting about this setting, I wasn’t aware of this, disabled it right away now!
I was aware of the gist of the article as common sense skills.
However, given the large number of unspecified users (with varying levels of knowledge and experience), it is a topic that gHacks Tech News should be writing about.
Just to be sure, I double-checked the browser I had been implemented (LibreWolf, Firefox ESR, Firefox Developer Edition, Firefox Nightly, Tor Browser, Pale Moon, and the latest versions of each) on the actual device, and the corresponding entry was “false” of each.
As mentioned in the article, I use my home desktop system only on wired LAN, so the “network connection test” is harmful and unhelpful, and even on my regular mobile (iOS) device, I have it disabled in default (allowing only my home Wi-Fi router).
All that and much, much more is disabled by default when using the arkenfox user.js………
arkenfox, and Firefox, have been outperforming Brave since forever, and still does
– https://privacytests.org/
https://github.com/arkenfox/user.js/wiki/1.1-to-arkenfox-or-not
> Now you can start enjoying some of the Tor Level protections arkenfox has enjoyed since Firefox 52
full first party isolation protection years ahead of anyone else
@Klaas Vaak Jr.
Firefox outperforming Brave? Your own link refutes that. And LibreWolf is basically Firefox + arkenfox (= Tor‘s basic config). And both LibreWolf and Firefox + arkenfox have not enough users to matter. Their FP defenses are ineffective if a script is moderately competent.
Iron Heart at it again. You know sometimes you make really good points but when there is anything close to user.js stuff, you just start saying nonsense.
Stop bringing Tor here and stop highlighting – user.js doesn’t do anything for your IP. No software apart from VPNs and Tor does anything for your IP including Brave browser. Even then there are trust issues with VPNs and some consider Tor to be fundamentally flawed.
Best approach as always on the net is – First stop sharing bucketload of information about you unless it is absolutely necessary, i.e. only on govt. sites which must be shared and on e-commerce sites. Second even if you’re on social media stop being a live vlogger all the time. And third if want you want to use a service and it is legal, then use it.
Comment war is over. Peace.
@Yash
I mean, it’s fine by me if you think that I usually am writing comments that make a point, but suddenly lose my marbles whenever it comes to user.js files, it’s not like I care. The flaw with user.js files are obvious: They are trying to replicate a setup that is genuinely meant for Tor for rapid release versions of Firefox, ignoring the reasons why Tor sticks with ESR AND comes preconfigured:
– One can tell differing major versions of browsers apart via feature detection no matter any user agent fakery. If your browser supports a new web standard, a new API, then I can detect this. A fake user agent does nothing to mitigate this, in fact, if your user agent does not match your browser’s detected capabilities you have done yourself a disservice and you have reduced your privacy, because normally the capabilities would match the detected version. Tor mitigates this by using ESR which only gets a new major version once per year, and background security updates without altering the major version in between. That’s why RFP is effective there. I can detect that you use Firefox 99 + RFP + whatever else your user.js changes via feature detection. This reduces your pool to other people using the same user.js (who have hopefully not changed the config, because otherwise they immediately exit the pool), this leads me to my next point:
– Tor, every single installation, always comes preconfigured, and you are not supposed to change its settings at all. Firefox is being configured by you, in contrast. I can tell that your fingerprint is strangely different from other fingerprints of the same Firefox version. Sure, that won’t draw attention to you at all, and improves your privacy by not standing out. Your crowd of like-minded users is huge as well. /s
– And last but not least, your IP address. I can tell that you are not using Tor because there are actual list of Tor IP address (ranges). Yours is not there? 99% not Tor.
I can tell which major browser version you use via feature detection no matter what your UA says, I can tell that your fingerprint has unexpected values compared to other fingerprints of the same major version, and I can again tell that it’s not Tor (if I didn’t already find out via feature detection, unless you use ESR) via IP address. That is not a working concept at all.
But hey, then again, with my delusions regarding user.js files I am actually in good company, the Tor Project, Whonix lead developer madaidan, and GrapheneOS lead dev Daniel Micay are all not convinced of this concept actually working, so they are delusional as well, meaning I am in good company.
PS: You misunderstood what I said re. my question “Why not go all the way to Tor then?”, I meant that if you are using an inconvenient user.js that tries to replicate Tor and breaks stuff, why don’t you use Tor then? Tor will hardly extend the breakage at this point. And it doesn’t suffer from the IP address leak of ordinary browsers. I see no use case for user.js files replicating Tor at all.
@Iron Heart
Tor comes with ESR release for one simple reason – it reduces workload on every Firefox version update. Much like admins. Nothing to do with browser version coz last time when I checked it – Brave reveals version as well.
Second RFP is more than faking user agent – which it doesn’t do btw. On a same version with RFP on, there are not many ways to differentiate them, and don’t bring IP coz Brave doesn’t do anything for it too. Infact if you’ve even got a glimpse of Arkenfox, there aren’t many prefs which alters FP. And all works like a switch which minimizes number of possible different FPs.
Plus again you mentioned Daniel Micay. You know GrapheneOS is similar to user.js. Both improves security and privacy. Yet still you have to throw mud at Arkenfox. And again what the hell does Tor has anything to do with user.js. Tor disables certain API, user.js doesn’t. Plus there are other pref changes as well.
Maybe you can stop your agenda now.
Peace.
@Yash
> Tor comes with ESR release for one simple reason – it reduces workload on every Firefox version update.
False. They are based on ESR so as to not run into fragmentation of major versions that are detectable as such. Has nothing to do with reducing workload, like, at all.
> Nothing to do with browser version coz last time when I checked it – Brave reveals version as well.
That wasn’t my point at all. 1) Brave does not claim to offer Tor-level privacy protection which comes at the price of web compat and 2) I was talking about your user agent not matching your actual browser version. Only Firefox with RFP on suffers from that, not Tor, and not Brave.
> Second RFP is more than faking user agent
At least try to understand me correctly for once, or are you playing dumb, trying to fool me? Your RFP user agent fakery is an issue because I can detect that you are not actually on the ESR version of Firefox (FF 91 currently), I can thus infer that you must run some user.js because you ain’t Tor. Tor is based on ESR (I can also tell ESR and Tor apart via IP address, but that’s another story).
> and don’t bring IP
Why not? You run a setup that simulates Tor though I can tell via IP range lists of Tor servers that it ain’t Tor.
> Brave doesn’t do anything for it too
It actually has a Tor mode though I don’t recommend it. VPN also fixes this issue. VPN or Tor does not fix your issue of using a browser version other than ESR AND(!) RFP, which puts you into a very small pool of users.
> Infact if you’ve even got a glimpse of Arkenfox, there aren’t many prefs which alters FP.
Perhaps it’s you who should get a glimpse, arkenfox messes with WebGL, IPv6 support, WebRTC, cookie acceptance etc., all outside of RFP, and all fingerprint-altering stuff.
> And all works like a switch which minimizes number of possible different FPs.
I don’t know what you mean. You are within a very small pool of people who run that obscure user.js script on Firefox, and this setup is detectable and much different from how Firefox would normally appear. If you think this makes you non-unique then I can’t help you.
> You know GrapheneOS is similar to user.js.
No it isn’t. It fixes many security issues of Android and strips out Google connections. That is not remotely comparable to anti-fingerprinting measures of browsers.
> Yet still you have to throw mud at Arkenfox.
I seldomly throw mud at things that actually work. I do here, because it doesn’t work. It’s also a pathetic copycat effort on top of that, which makes it worse for me personally. It deserves my disdain.
> And again what the hell does Tor has anything to do with user.js.
Tor Browser Bundle comes preconfigured and has a sizable user base. Your Firefox didn’t come preconfigured, you and a relatively small number of other people configured it according to the instructions of some obscure user.js, meaning you are in a very small pool of users with the resulting fingerprint. Tor doesn’t suffer from the issues you suffer from with your setup, it’s therefore a valid point of comparison. You don’t understand this at all, which is funny and sad at the same time.
> Tor disables certain API, user.js doesn’t.
Both disable various APIs, in case you are unaware. Only in Tor’s case it has a shot at actually working because a sizable user base actually has that preconfigured fingerprint and doesn’t suffer from major version fragmentation every 4 weeks. Also doesn’t suffer from IP leaks though that’s another story.
> Maybe you can stop your agenda now.
If my “agenda” consists of arguing against misguided concepts that don’t work, then so be it.
@Iron Heart
It is clear there is no way this discussion is going to a meaningful place. In your last comment you wrote hell lot of stupid things and then used the word ‘personally’ for most of them.
It’s best you stop ranting about user.js. If not then don’t worry go ahead, write some stupid stuff about Arkenfox.
You’re one of those folks like madaidan who won’t use an adblock coz you know it is not perfect. You’ll throw mud again and again at Arkenfox, and then praise GrapheneOS because it strips out Google connection, although basic functionality of GrapheneOS and user.js is same.
So don’t bother responding and write again by copy pasting one word or one line.
And to really get some good perspective, please read Arkenfox wiki, see many differences with Tor browser.
Peace.
Comparing GrapheneOS to a user.js is very dishonest and shows a lack of understanding of how the project works. The mobile OS provides a lot of privacy/security features (e.g. a hardened app sandbox) beyond what AOSP provides on its own, their team also contributes to the upstream. While a user.js is just a configuration file that can only disable/enable existing Firefox features, and you trust a consensus of anonymous people rather than Daniel Micay, a researcher with a good track record in the privacy space
https://grapheneos.org/features
Well you need a Google Pixel to install GrapheneOS. It strips out Google connections. But then what do you think user.js file does? Samba. It also flips/atleast has good points to change prefs that improves fingerprinting protections. It also strips out telemetry and other various connections. How in the world is this different to what GrapheneOS does?
Plus do you know GrapheneOS is not really an OS, but a UI layer built on top of Android. Same like user.js which is built on core Firefox.
Iron Heart’s points are – a) you can’t use something because it doesn’t have sufficient user base, b) you should not do anything otherwise you’ll stick out from the crowd. Well isn’t that the same thing users do when they use GrapheneOS.
At the end of the day if someone’s going to fire shots at a project which aims to improve privacy and security than what was before, then there is another project which does the same thing. Don’t be a hypocrite!
And last this awful attitude of you’re not supposed to do anything to improve some bits as that may make you more unique is really a s*** point, same like what madaidan makes – you can’t use an adblock coz it doesn’t block everything. Awful defeatist attitude.
>Well you need a Google Pixel to install GrapheneOS. It strips out Google connections. But then what do you think user.js file does? Samba. It also flips/atleast has good points to change prefs that improves fingerprinting protections. It also strips out telemetry and other various connections. How in the world is this different to what GrapheneOS does?
You completely ignored my claims and fingerprinting protections are irrelevant because GrapheneOS is not a browser
>Plus do you know GrapheneOS is not really an OS, but a UI layer built on top of Android. Same like user.js which is built on core Firefox.
It’s a mobile OS and Graphene uses the same UI as AOSP 12, what are you talking about? A user.js is a configuration file, not an interface
>Iron Heart’s points are – a) you can’t use something because it doesn’t have sufficient user base, b) you should not do anything otherwise you’ll stick out from the crowd. Well isn’t that the same thing users do when they use GrapheneOS.
Irrelevant since GrapheneOS is not a browser
>At the end of the day if someone’s going to fire shots at a project which aims to improve privacy and security than what was before, then there is another project which does the same thing. Don’t be a hypocrite!
Never said that and that’s exactly what you’re doing
>And last this awful attitude of you’re not supposed to do anything to improve some bits as that may make you more unique is really a s*** point, same like what madaidan makes – you can’t use an adblock coz it doesn’t block everything. Awful defeatist attitude.
The fact that enumerating badness doesn’t work well is not a “shit point”.
https://www.ranum.com/security/computer_security/editorials/dumb/
You need some technical knowledge about user.js and GrapheneOS.
If you really think fingerprinting is really restricted to browser and nothing can be done about OS, well good for you.
Plus do you know any app installed on GrapheneOS can straightaway notice this is not normal Google Pixel and can relay that information via internet if allowed!
It was fun talking to two people who may think are expert but really have no clue about security, nevermind privacy.
@Dennis: or when using Librewolf (= FF + Arkenfox).
Librewolf is absolutely pointless when it is just firefox with a hardened preferences file.
@computer said no
Even Firefox with an obscure user.js file is pointless when the user.js file is basically Tor‘s config minus the Tor network access. Think about it.
@Iron Heart (Chromium user) is complaining about Firefox and its forks. Yikes… When Google and Microsoft stop directly funding the project, then you can talk. Until then, pipe down.
@:-)
https://en.wikipedia.org/wiki/Mozilla_Corporation#Google
@:-)
What does „Chromium“ have to do with being private or non-private? Chromium is open source, you can modify it in any way you see fit. Some projects like Brave and Bromite modify it to enhance user privacy. Firefox has shit privacy by default:
https://privacytests.org/
It‘s worse than Brave which is Chromium-based. LibreWolf, while checking most boxes, has the issue of having too few users which lowers the effectiveness of its FP defenses against scripts that check for more than just a few items. The only two browsers that have good privacy AND a sizable userbase are Brave and Tor.
Also, „funding“, my dude, Mozilla gets 80%+ of its annual income from Google while Brave is self-sufficient via its opt-in and privacy-preserving ads program (Brave Rewards).
> arkenfox user.js
https://madaidans-insecurities.github.io/browser-tracking.html#configuring-the-browser
https://old.reddit.com/r/privacytoolsIO/comments/glr63n/brave_hardened/fr0to0n/
https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
Also, why not just use Tor at this point? Arkenfox and Tor’s configuration are virtually the same, except Tor has the advantage of not leaking your IP address after all is said and done. Tor also remains on the same major version of Firefox for 1 year – ESR – which means that you are actually within a large pool of users with the same major version and the same fingerprint. Trying to replicate Tor’s setup for a much smaller pool of users (those who use some obscure user.js like arkenfox), and for Firefox major versions that change monthly and can 100% be told apart via feature detection if not by user agent, is a recipe for disaster, and serves no real purpose.
>madaidan
LOL, people still falling for it.
@Frankel
What do you mean? He‘s a leading dev of Whonix. Now tell us about your „expertise“ in comparison.
For starters: https://en.wikipedia.org/wiki/Name-dropping
@Frankel
And? I mean, your point being? I did not just drop their names, I‘ve also linked to their comments where they explicitly say that user.js is BS. You‘ve written two comments so far without making a single tangible point, congrats.
You’ll eventually get tired of it :)
> Arkenfox and Tor’s configuration are virtually the same
Why are you so mad at arkenfox that you have to keep making up lies about it? Constantly repeating lies does not make them true, and pants lives in your head, eating away at you. Why are you so mad at firefox, seek some help
– https://www.ghacks.net/2021/10/21/mozilla-firefox-microsoft-store-version/#comment-4506911
– https://www.ghacks.net/2021/10/21/mozilla-firefox-microsoft-store-version/#comment-4507037
– and comments either side of these
Arkenfox is clearly not trying to be Tor Browser and has very little in common
as written Oct 2021
> There are
> – 437 unique prefs in user.js [tor].js
> – 396 unique prefs in user.js [arkenfox].js
> – 735 combined unique prefs
>
> only 43 out of 735 prefs IN COMMON match – that is less than 6% in common with Tor Browser
* [Editor: removed]
* [Editor: removed, do not attack others by changing their nickname]
> arkenfox also makes recommendations for how the UX should behave
these are excluded, under a section called personal and are commented out
> You also seem to count removed / no longer applicable settings still kisted by arkenfox for documentation purposes
these are excluded in a section called deprecated and are commented out, they currently number a whopping SIX prefs
> Firefox occasionally introduces new settings post-ESR, and arkenfox flips those, oftentimes after they are discussed by Tor in preparation of new ESRs
doesn’t change the stats, even if it was true. arkenfox documents all diffs each release well before tor project. the history is there at github. In fact some changes at tor project are directly from pants, including ones that are not in arkenfox. that’s so weird.
> With the three points above in mind, arkenfox basically 100% replicates Tor
So both projects utilize around 750+ prefs changes and only 6% is set in common. The facts don’t lie.
@„all hail pants“
> so mature of you to resort to name calling and misuse of names, which is against martin’s site policies. please show us on the doll where arkenfox touched you
So mature of you to pick that nick in the first place, it is so narcissist, of course I‘ll mock it. The only reason I don‘t do it again is because I know that Martin doesn‘t like anyone to spilling the beans about „arkenfox“ and will resort to the most flimsy excuses to remove posts critcizing its copycat nature.
I‘ll keep this short and simple, and link to the user.js itself:
https://github.com/arkenfox/user.js/blob/master/user.js
I‘ll refer to the „Index“ in the following: All sections from 0100 (Startup) up to and including 4500 (RFP), with few settings being exceptions or matter of personal preference (not strictly privacy-related), are a carbon copy of Tor‘s config. That‘s also more than your claimed „43 settings“ of course.
> Pants is smart if he checks what Tor Browser thinks and does. Be smart, be like pants. The prefs flipped are all privacy related and created by Mozilla, not Tor Browser, and increase privacy, and most eventually ride the train to stable
Pants would be smart if she actually didn‘t live off the reputation and work of other people, in this case the Tor Project, whitelabeling the Tor config as „arkenfox“. See, I know that „Pants“ (who is totally not identical with „all hail pants“ at all, like, totally, not identical at all) has a non-coding project on GitHub she has built a reputation on, and unless she has actual coding skills (I strongly doubt it until I see evidence to the contrary), her career will be quickly over if this project is exposed as a copycat effort, but that doesn‘t justify her in posting misleading numbers.
You think that I actually care? You know, if I cared, if Pants was really living in my head rent-free as you claim, I would reserve the better part of one afternoon (it doesn‘t take any longer) to go through „arkenfox“, setting by setting, and compare it to current Tor. You and I both know exactly what the result would be. Of course, you could fix this issue easily by adding a disclaimer that you are actually getting most of your config (the meaningful sections at least) from Tor, and give credit to the actual creators. Be smart, be like Pants, and just do that.
* [Editor: removed]
so mature of you to resort to name calling and misuse of names, which is against martin’s site policies. please show us on the doll where arkenfox touched you
read the links
– https://www.ghacks.net/2021/10/21/mozilla-firefox-microsoft-store-version/#comment-4507037
at the time of writing (oct 2021)
There are
– 298 prefs not declared in user.js [tor].js
– 339 prefs not declared in user.js [arkenfox].js
so clearly arkenfox doesn’t have 339/437 tor browser prefs – that’s over 77% “not copied”
and clearly arkenfox has 298/396 prefs which tor browser doesn’t even use – that’s over 75% “not copied” because it’s not there to be “copied”
There are
– 7 prefs with different values but matching state
– 39 prefs with matching values but inactive in user.js [arkenfox].js
– 9 prefs with both mismatching values and states
– 43 matching prefs, both value and state (active/inactive)
– 98 prefs in common
so clearly arkenfox has changed 55/98 of the prefs in common – that’s 56% clearly “not copied”
anyway you slice and dice it, arkenfox is not a tor copy
Pants is smart if he checks what Tor Browser thinks and does. Be smart, be like pants. The prefs flipped are all privacy related and created by Mozilla, not Tor Browser, and increase privacy, and most eventually ride the train to stable
Anyway, it’s very strange how pants adds prefs before Tor Browser even discusses them
* [Editor: removed, no personal attacks]
@Iron Heart
Do you really trust Tor? the government funded supposedly anonymously network that over and over again has been filled by malicious nodes?
Plus it hasn’t changed much from the time the guy from a US university got caught sending threat bombs with it.
Not anonymously, not secured, not safe for the normal user, for the CIA, the NSA and the other many government agencies from many countries wanting to know what ‘their people’ are doing.
Which is funny because it is a terrible thing to use but somehow I guess those agencies protect the pedos, because Tor is used for child pornography and other evil stuff and I haven’t heard much about it. I have heard of some people who have taken down their nodes because they have inspected the content that goes through there and it is all pedo stuff and they don’t want to get in trouble and help promoting that.
But even with that, it doesn’t change how it got funded by Gov agencies, so nobody should trust it.
@MaxKarl
>Do you really trust Tor? the government funded supposedly anonymously network that over and over again has been filled by malicious nodes?
I don’t see how receiving money from the US government and other sponsors compromises anonymity; Tor is a FOSS project entirely developed by a non-profit organization. Their team is also very reactive when it comes to taking down malicious nodes
https://github.com/torproject/tor
>Plus it hasn’t changed much from the time the guy from a US university got caught sending threat bombs with it. Not anonymously, not secured, not safe for the normal user, for the CIA, the NSA and the other many government agencies from many countries wanting to know what ‘their people’ are doing
Tor is not bulletproof and never claimed to be. Eldo Kim wasn’t caught because the network wasn’t anonymous, but because of his bad OPSEC
https://www.nbcnews.com/technology/failing-grade-alleged-harvard-bomb-hoaxer-needed-more-tor-cover-2D11767028
>Which is funny because it is a terrible thing to use but somehow I guess those agencies protect the pedos, because Tor is used for child pornography and other evil stuff and I haven’t heard much about it
When you have a project that has been proven to work well, obviously criminals will use it for bad purposes. But you know what? Tor is used for legitimate things (e.g. censorship circumvention, privacy, protecting communications) and the vast majority of onion services (Twitter, Facebook, BBC, Brave, etc) are completely legal
https://2019.www.torproject.org/about/torusers.html