ShazzleMail aims to re-invent email by making it surveillance-resistant
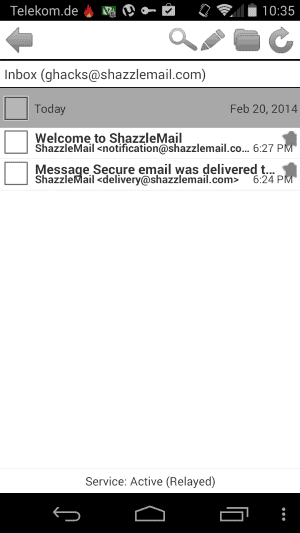
Emails are probably one of the easiest data types that third-parties can monitor. There are plenty of reasons for that, from being stored on third-party servers to the lack of proper encryption. And to top it all, even if emails are encrypted the metadata is usually not.
The creators of ShazzleMail have created a system that they say does away with all current email privacy issues. One of the core differences to standard email solutions is that the email client is also the server.
While that sounds complicated at first, it is not in this case as everything is handled in the background for you. All you need to do is create an email account, or multiple ones, to get started.
This means that every user of ShazzleMail is also operating a server that is being used to send and retrieve emails.
A central registry is being used to provide senders with information about recipients. If the recipient is also a user of ShazzleMail, an encrypted connection is created between the sender's and receiver's device. If the receiving user is not online, the email is not sent until that happens.
This does away with the storing of emails on third-party servers, but does mean that emails are only exchanged if both parties are online at the same time.
If the recipient of the email is not a member of the ShazzleMail network, a url link is sent instead using standard non-secure emails. A click on the link opens an SSL connection between the recipient's computer and the sender's device, so that the information are transmitted via an encrypted channel.
ShazzleMail is available for major app platforms such as Apple's iOS and Google's Android platform, but also as desktop clients for Windows and Macintosh systems.
In addition, it is possible to setup email clients such as Thunderbird once an account has been created. Note that the ShazzleMail client needs to run on the system as well for that to happen, as you won't be able to use the service otherwise.
The team focuses on mobile first and foremost, and there are several reasons for that, but the most important one is that mobile devices -- especially smartphones --Â tend to be online all the time, or the majority of time while PCs or Macs are not usually.
The desktop client is pretty basic but sufficient. The main advantage that it offers over the mail apps is that you can send attachments using it, while that does not seem possible if you are sending emails using the applications.
Lets recap how ShazzleMail differs from traditional email services
- Email is only stored on your devices and on recipient devices, but nowhere else.
- Emails are only transmitted in encrypted form when both sender and recipient are online. And even if the recipient is not using ShazzleMail, a direct connection is ensured.
- There are not any encryption keys that the email provider can pass over to authorities.
Issues
The system is well-thought out but it is too early to tell if it is really secure. A security audit is needed to verify that. I was not able find information about the encryption that the service uses on the services website, or information about the central registry that is being used to link senders to recipients.
The apps are limited in terms of what you can send. While you can add text to emails and basic formatting, you cannot add any file attachments.
With all that said, it is highly advised to be careful when using the service. While that does not mean that you should not use it, it means that you need to be aware of those issues.
Verdict
ShazzleMail is something that I'll be keeping an eye on to see how it evolves over time. A security audit above everything else would certainly help the application's popularity.
Now Read: Postbox email client review
Advertisement














It’s not at all a new concept. The same procedure has been around in chat servers providing encrypted communication. You can send (encrypted) material while both sender and recipient are online.
many thanks for this. You could never say too much to me on the subject of internet privacy. it’s the most pressing concern of our time imho, along with world inequality, both being symptomatic of the same corruption of power.
What a ridiculous name for it!I can’t think of anything worse.Just the name puts me off going near it.
Shazzle:
1. A generic term used to describe the act of expelling liquid from his or her body in a fit of momentary excitement.
2. The act of showing extreme excitement
No ta.
by sharing those definitions, you are propagating the problem. i could have remained in ignorant bliss, but now i can’t unknow. it’s like the time someone told me she hates porridge because of all the mucus in it.
whoops :)
I had to look them up.It’s not even a true word & those defs are from the urban dictionary.Something like Safemail or Armouredmail would be ok but shazzlemail!
“ShazzleMail is something that I’ll be keeping an eye on”
Me too – thanks Martin
Others to keep an eye on include:
– Dark Mail: http://darkmail.info/ | from Silent Circle & Lavabit, among others
– Heml.is: https://heml.is/ | from TPB founder Peter Sunde, among others
– Mail Pile: https://www.mailpile.is/
and I’m sure there are others…
So is the metadata still vulnerable when sending to external services?
It is not, according to the company that operates the service. Read the metadata pdf that is linked on the homepage.