Bitwarden Authenticator now lets you import TOTP tokens from other authenticator apps

Bitwarden Authenticator has added support for exporting and importing Time-based One-Time Passwords (TOTPs) tokens from other apps. The news was shared by a Bitwarden employee on the company's Reddit community.
In case you missed it, Bitwarden Authenticator was launched about a month ago, as a standalone app. Currently, the app allows you to import your 2FA (2-factor authentication) security tokens from Bitwarden Password Manager, Google Authenticator, LastPass, 2FAS, Aegis (for Android), and Raivo (for iOS). Just a reminder, Raivo was sold to a third-party last year, and according to recent reports an update for the app deleted all TOTPs without any prior warning, so you may want to switch to a different authenticator app.
How to import TOTP tokens from other apps to Bitwarden Authenticator
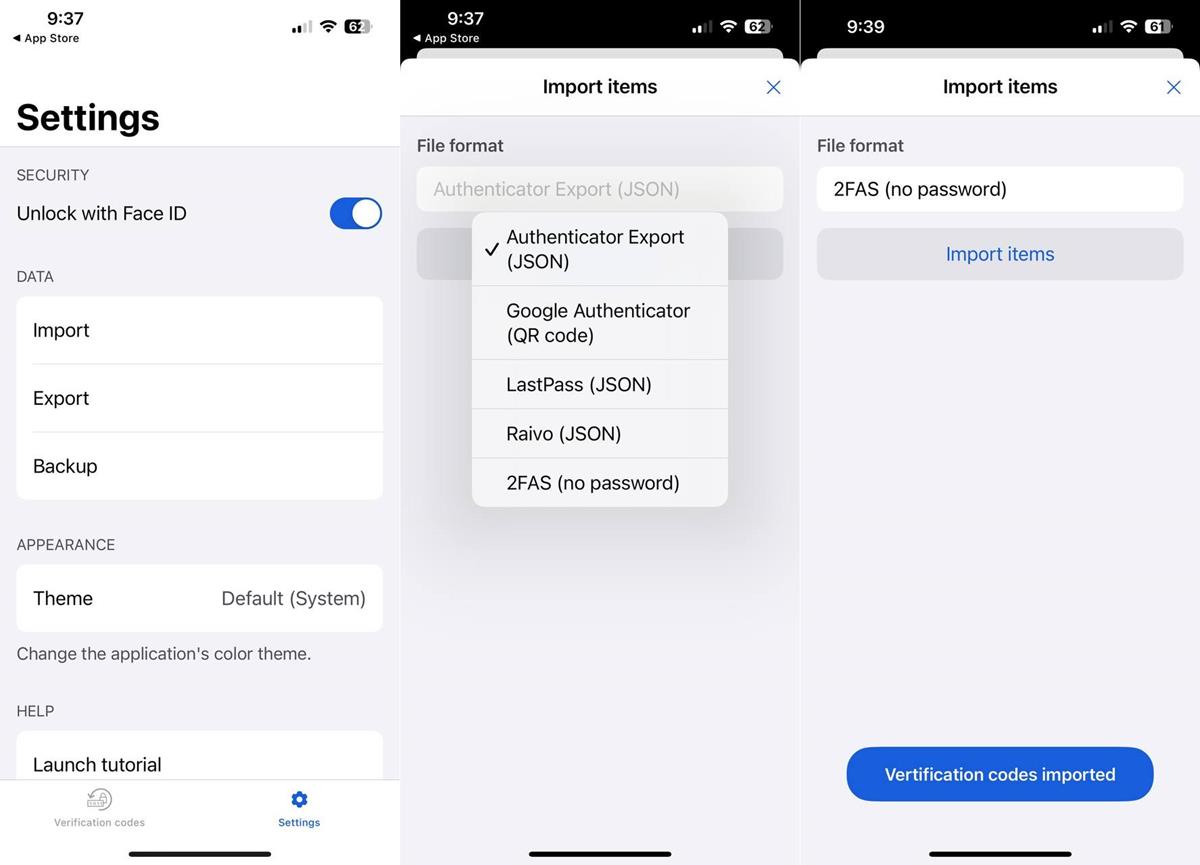
1. Aegis, Raivo, LastPass users will need to export a .JSON file from their app's settings, while 2FAS users will need to get a .2FAS file from the app. Google Authenticator users can use the Transfer accounts section in the app to generate a QR Code, and bring their tokens over to Bitwarden. You can refer to the official guide for more details.
2. Open Bitwarden Authenticator, and tap on the settings tab at the bottom of the screen.
3. Tap on Import.
4. Select the app that you want to import from, and select the file saved on your device.
5. That's it. You should see a message at the bottom of the screen that says "verification codes imported".
Bitwarden Authenticator also allows you to export your tokens to a .JSON file, which you can get from the Settings > Export section. You may use it to save a backup of your credentials, which is important, considering that the app does not sync the data to the cloud. I recommend enabling the "Unlock with Biometrics / Face ID" option in the app's settings to prevent other users from accessing your codes, and protect your online accounts from unauthorized usage.
Note: Some Reddit users reported that Bitwarden fails to import the tokens from 2FAS. But it worked fine for me. I did notice a second update for Bitwarden Authenticator, which may have contained a patch that fixed the bug.
There is no official way to import TOTPs from Microsoft Authenticator or Authy, but it's not Bitwarden's fault. Those apps don't allow the tokens to be exported easily. That said, there is an unofficial method to export your tokens from Authy, you will need to follow this guide on GitHub. I used a similar method to get my security tokens from Authy and imported them to Authy a few years ago.
Personally, I don't want my passwords and TOTP tokens in the same app, which is why I don't use Bitwarden's Password Manager's built-in feature for managing my TOTPs. But I can see why others may prefer to have them in the same place. Some people may want to sync their TOTPs between multiple devices, and it can also be useful if you were switching to a new mobile phone. The new method to import/export the data can help with backing up or moving to new devices easier.
Bitwarden Authenticator is free, open source, and works offline. It is available for iOS and Android devices. You don't need an account to use the app. 2FAS (iOS and Android) and ente Authenticator (iOS and Android) are similar open source authenticator apps, which I can recommend if you don't want to use Bitwarden Authenticator.




















Not sure about this. Basic tenent of IT Security, and security in general, is the Segregated Responsibility Principle.
Never allow a single actor to have the full responsibility and authority to perform sensitive actions, human or machine.
Storing both the TOTP authentication secrets and Passwords within the same vault is more convienent however it isn’t a smart move and defeats the purpose and benefits of having multi-factor in the first place.
Given what I have seen in the wild with code and IT security this isn’t shocking though. Dumbfounded that we still need to instruct developers that string concatenation isn’t acceptable, under any circumstances, to build queries let alone the network configurations and password standards.
The joy of working in a lot-trust society, but that is a rant for another time…
I believe Bitwarden Password Manager and Bitwarden Authenticator are two separate apps. eg: if you are looking at a replacement of Google or Microsoft Authenticator then there is a new kid on the block.
@Cams
Need to verify the implementation details however, based on the image on bitwarden’s own site, it appears that they are storing passwords and TOTP secrets in the same vault.
Ref: https://bitwarden.com/products/business/
If you scroll down to “manage and share passwords in one secure place” section, the screenshot on left shows TOTP code and password together which is concerning. If the vault is breached, so are the TOTP codes.
I think of this in a similar fashion to baseline SSH key management. Big topic however will say that any ssh key should also have a passphrase included to prevent use in the event the key is leaked. It is why ssh-keygen includes the passphrase question during generation. It provides a separate, off system requirement for validation that no passwordless system can match, except possibly security keys ( Yubikey, etc )
The issue applies to TOTP codes, if they are on device they can be breached and this risk goes up if stored within the same encrypted vault. Still better than password only however not what I would consider a step forward for security.
Do you think is safe to keep using Authy nowdays?.
I ended up using Authpass, which uses a KeePass database to store the seeds, and it has much better 2fa OTP support than any of the other KeePass clients. It actually shows the codes when you click on an account, and it’s available on Windows Mac Android iphone Linux.
It supports cloud sync to OneDrive and Google drive and Dropbox, so no app makers can run away with my seeds again!
nope. less update. less contributor. more bug on their client as they said it. more security hole.