3 Options To Analyze Past Computer Usage
Operating systems and applications often save loads and loads of information, often without the user knowing about it. This can have privacy implications, considering that it may be possible to recover files, bookmarks or visited web pages easily if someone gets local access to the PC or access to one of the computer's storage devices.
We have covered the topic before, see Used Hard Drives Still Haven For Identify Theft for instance. We also offered tips and tools on protecting your privacy, for instance by erasing files on unused disk space or what you should do before bringing the PC in for repair.
The majority of users does not really know about this. Most think for instance that deleting files will delete them completely which is not the case. Here is a collection of three different methods and ways to find out more about a previous computer usage.
You can use the information on your own computer, to see if a third party could grab those information from yours as well.
1. Display Deleted Files
Deleted files are not directly deleted by the operating system. Even if you delete them directly or make sure to delete the trashcan as well. Why? Because it is faster to simply delete information about the file, than the file itself. While you won't see the file anymore in your OS, it may still be fully accessible on the hard drive of the computer. Someone with the right set of tools could recover deleted files to get access to what you have been deleting.
Tools for the job:
How to protect yourself:
Wipe the free disk space regularly. This overwrites the free space on the hard drive which makes standard file recovery impossible.
2. The Web Browser History
Web browsers are configured to record the web browsing history. This is done in databases in the program directory most of the time as well a cache that contains pages, images, cookies and other elements of visited websites. It is quite easy to use the cached information to see what sites a user has been visiting in the past and what has been downloaded to the computer.
Tools for the job
- Built-in web browser tools to access the history and cache
- The standard system file browser, e.g. Windows Explorer
- Firefox Cache Viewer
- Google Chrome Cache View
How to protect yourself:
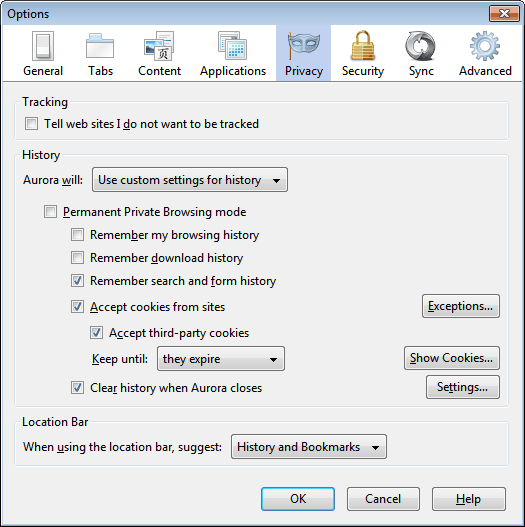
You can configure web browsers to delete the cache regularly, for instance at every exit or every five days. Here is how you would do that in Firefox. Open the Firefox web browser and click on Firefox > Options, or select Tools > Options from the menu. Switch to the Privacy tab
You can either configure Firefox to never remember the browsing history, or use custom settings for the history. This way you could disable the browsing and download history, but keep cookies for your logins.
3. Recent Items
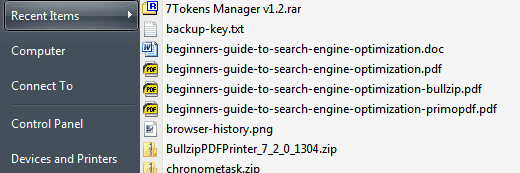
Another area where you might get a lot of information about computer usage is the recent items list. The operating system and multiple third party tools keep tabs on programs or files that have been opened recently. If you have not done anything with the OS or application yet, you may find previously opened files and programs by the system's last user.
Tools for the job
You can access the information right in the application or the operating system. For Windows 7, you could for instance click on the start button and select Recent Items from the Start menu, or right-click an item in the taskbar to see its jumplist entries.
How to protect yourself:
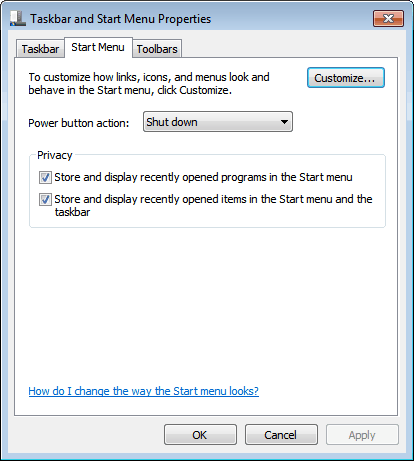
You need to disable recent items either in a control panel of the operating system or in the third party application. For Windows 7, you would simply right-click the start orb and select Properties from the context menu.
Locate Store and display recently opened items in the Start menu and the taskbar to disable that feature.
Closing Words
The three method above are common options to analyze a computer system. Have other suggestions? Let us know in the comments.

















For important data, the best protection is to use encryption software. truecrypt :http://www.truecrypt.org/ is the best choice.
Agree with TrueCrypt.
Thanks Martin for this interesting article.
Paul and his band of loony Grey Hats over at PaulDotCom security weekly go into this and related topics all the time.
Last year they explored this article from their buddy Iron Geek, a frequent guest on the program.
http://www.irongeek.com/i.php?page=security/windows-forensics-registry-and-file-system-spots
Great tip, thanks for posting about it.
ccleaner makes a half decent data mining utility as well when run in analysis mode.
any tool put out by nirsoft for browser analysis
But flash cookies occasionally get overlooked.
http://www.macromedia.com/support/documentation/en/flashplayer/help/settings_manager07.html
the registry is also stores recent items for various programs.
I agree, the Registry contains lots of past and present data.