Deceptive Site Ahead: Google to warn about fake buttons
Google announced yesterday an addition to the company's Safe Browsing technology (Deceptive Site Ahead) that will flag sites with deceptive buttons to users of the company's Chrome web browser and in other programs that make use of Safe Browsing.
Deceptive buttons, either in the form of advertisement displayed on a page or embedded directly on a page by the owner of the site, come in many forms.
These buttons may display actions to download, update, install or play on a site they are displayed on, and are usually accompanied by a notification-type message that makes the action seem important.
Basic examples are actions to install software to play media on a page, or download buttons that don't download the software hosted on the site but unrelated third-party offerings.
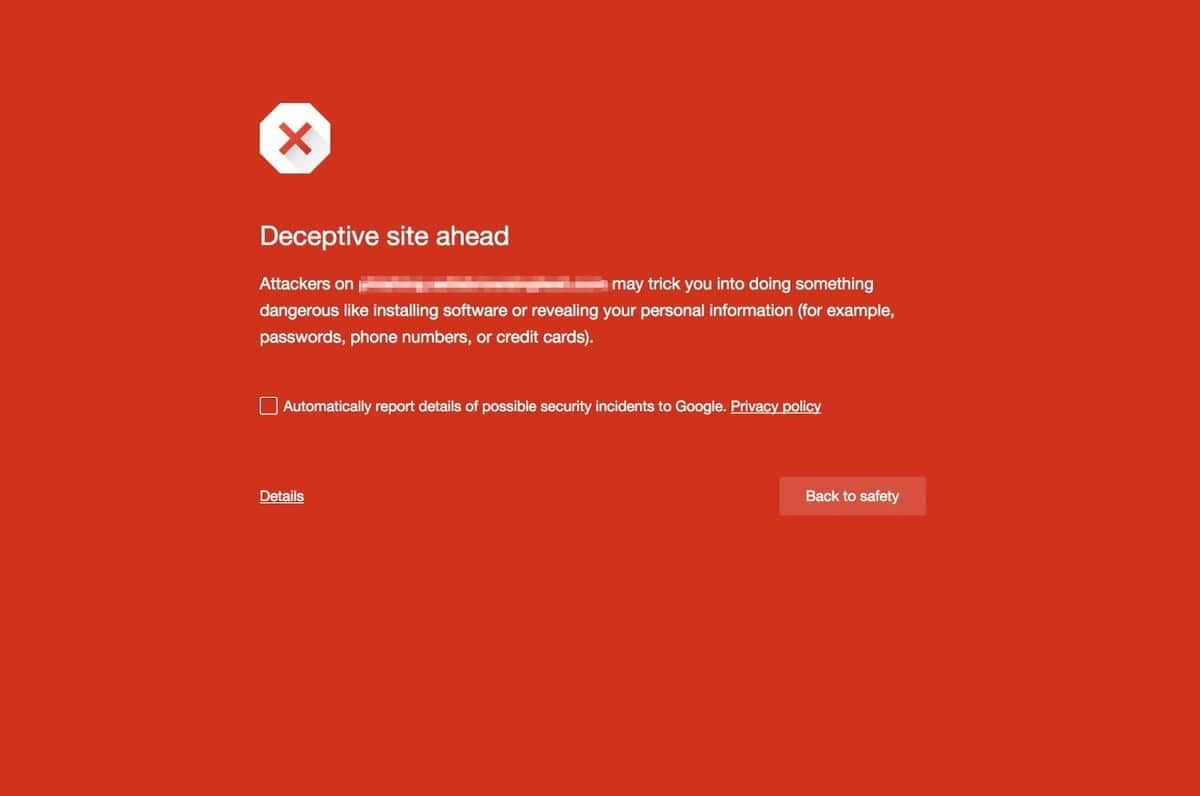
Deceptive Site Ahead
The new "deceptive site ahead" message appears in the Chrome web browser instead of web pages if Google considers the site to be "social engineering" due to the use of content that tries to deceive users who visit it.
The message reads:
Deceptive site ahead.
Attackers on [site url] may trick you into doing something dangerous like installing software or revealing your personal information (for example, passwords, phone numbers, or credit cards).
A click on details displays an option to override the warning and continue to the site.
Google mentions two specific scenarios in which sites may be flagged as deceptive:
- Pretend to act, or look and feel, like a trusted entity — like your own device or browser, or the website itself.
- Try to trick you into doing something you’d only do for a trusted entity — like sharing a password or calling tech support.
While some webmasters use these types of deceptive practices on purpose, others may be affected by it indirectly though advertisement displayed on their sites.
Google has created a support page for webmasters that offers instructions on how to troubleshoot the issue and resolve it so that the "deceptive site ahead" warning notification is removed from the site.
Webmasters whose site's were flagged for containing social engineering content may start the troubleshooting by opening the security issues report on Google Webmaster Tools. There they should find listed information such as sample urls that were flagged.
The actual removal may be problematic, as webmasters need to find the source of the deceptive content and remove it. Afterwards, they need to request a review of the site which Google claims may take between two and three days to complete.

















Google is catching even safe blogs as well. Two of my blogs were caught by this error and we don’t use any other Adcodes other than Google AdSense. There is no chance that we offer bad downloads on our WordPress self hosted blogs.
WordPress can have security problems just like anyone else. For example see
https://wordpress.org/news/2016/05/wordpress-4-5-2/ . I don’t know if this example or other prior WordPress releases could account for your problem.
When in doubt, close the browser itself.
If even that window appears to be tampered, use your system monitor / task manager to kill it.
At any rate, good to see more warnings from the browser. Due to ublock origin, I rarely see this malware.
so there won’t be “install chrome” buttons in google.com?
cool
Ublock seems to hide a lot of fake DL buttons also.
Glad to see Chrome is following Firefox lol – FF has similar security module as well: “Reported Attack Pages”.
Firefox uses Google Safe Browsing.
Although I don’t use Chrome or Google, I am glad that Google is taking the initiative against these deceptive ads. I hope by doing so, other browsers will follow suit. It may not eradicate shady practices like these but any action is a step in the right direction.
This will help a lot of people. One way I try to avoid fake buttons is to right click, and scan with Virustotal. You can install the extension for Virustotal through either the browser’s own site for extensions, or from Virustotal.com directly. It really saves time as you can see the download/link that the button is saying it is, or isn’t, and then the results from about 53 different scans.
Wait, I’m pretty sure I’ve seen adwords ads before that had exactly that behavior.
I would say all of them.
No anti-virus or anti-malware program can protect you from errors of your own making. Google has the resources and the browser to pull this off. Kaspersky doesn’t.
If we’re redirected to a site with two or more generic download links, we ought to have sense enough to just leave. What safe and legitimate site would post multiple, unspecific, essentially identical download links on the same page?
Hate these fake download buttons. Many times I’ve downloaded malware and viruses on my computer because I thought the button was real. Even when I noticed it wasn’t the real program and I canceled the installation process it still installed loads of malware on my computer. This is why I’m doing a complete reinstall of my Windows now. Kaspersky was no help. Pointless software if it doesn’t protect my computer. :/