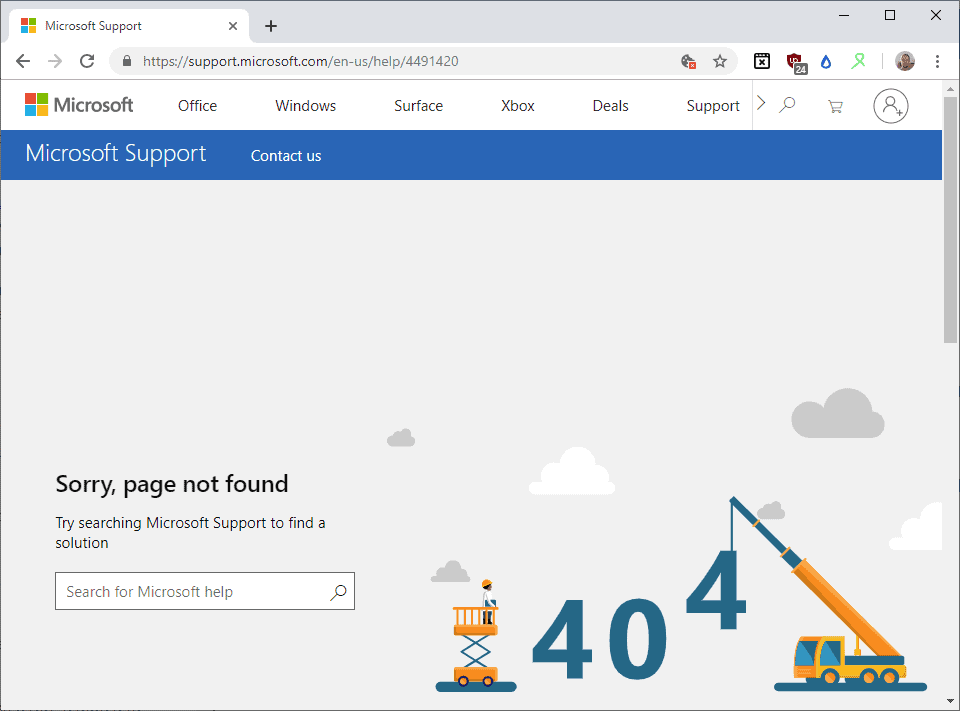
Microsoft: fix security issue with non-security update. Instructions point to non-existent KB page
Can things get any worse than this? Microsoft published a security advisory yesterday -- ADV190005 | Guidance to adjust HTTP/2 SETTINGS frames -- which affects Windows Server running Internet Information Services (IIS).
The security issue could be abused to cause CPU usage to increase to 100% until the malicious HTTP/2 "connections are killed by IIS".
The advisory recommends to administrators that they install the February non-security updates for the version of Windows 10 that is installed on an affected device. Microsoft released cumulative updates for all supported versions of Windows 10 on the February Patch Tuesday that included security updates.
The updates that Microsoft refers to in the advisory were released this week for Windows 10 version 1607 to 1803 (the update for Windows 10 version 1809 is being tested in the Release Preview ring currently) and the related Windows Server versions.
No instructions available

It is not the first time that non-security updates update security related content. The main issue with the approach is that it weakens the already-very-weak distinction between the monthly security and non-security releases.
The approach is far from ideal especially for administrators and users who install security-only patches exclusively on devices.
Update: Microsoft published the support article in the meantime.
What makes this particular security advisory even more problematic is that Microsoft asks customers to review a Knowledge Base article that does not exist.
The security advisory was published yesterday, but the essential support article is not published yet (a day after the release). It is possible that Microsoft made an error when it added the link to the page, but someone would certainly have verified the link before hitting the publish button.
It is unclear whether the installation of the updates fixes the issues or if other steps are required to resolve it completely.
Closing Words
This is not the first time that Microsoft released updates or advisories without publishing their support pages. I published Microsoft, please publish support pages before updates in 2016 to raise awareness for the issue.
Users and administrators may encounter Windows updates and patches without option to find out what they actually do, may introduce issues, or have additional steps or requirements.
Administrators could install the patches and hope for the best in this particular case, or wait until Microsoft publishes the support page. Both options are not very pleasant; the first could mean that important steps to protect the server are not implemented because of missing instructions, the second that attacks could hit the server while the administrator waits for Microsoft to release the support page.
Now You: What would you do and what is your take on this? (via Ask Woody)



















As of today, Woody’s at MS-DEFCON2:
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don’t do it.
Hard to tell if a particular update is the reason or multiple updates, there are a number of blunders mentioned on just the site’s first page!
https://www.askwoody.com/
I haven’t updated my ver1803 in quite a while. Maybe when MS introduces and blows up the 1900 versions, they’ll quit trying to wreck the 1800’s and I’ll update.
Honestly, it seems like MS is managing as though they’re time travelers from the 1800’s or 1900’s!
OK, one more kick at the dead horse. Windows is a dog’s breakfast now and for anyone unfamiliar with the expression, it’s not a compliment. What can you do if you’re not a software expert? Just muddle through with backups and re-installs as required until you switch to a proper OS.
Yes, agree.
Running Win 10 Home/Pro/Ent is like a woman suffering painful menstrual periods every month and extra painful childbirth every year or super painful premature childbirth every 6 months.
The only sane way for home-users to run Win 10 is to run the Ent LTSB/LTSC 2016 or 2019 edition, even if unactivated and/or unupdated = can pause the forced auto-install of security updates for up to 30 days and no forced auto-upgrades for up to 10 years until EOL.
@AnorKnee Merce,
You’ve got a vivid imagination! I’ve never heard of Windows 10 being described in that way before. :D
I think they do it on purpose, so if you want a specific security update it is embedded with other shit you do not want, what that other shit is microsoft only knows, lol.
Microsoft is loaded with incompetent clowns up top. This happens to many large successful organizations eventually. Just look at governments around the globe. I won’t provide examples. There are really too many to mention.
What’s the solution? Trim staff in areas needed the most (to protect the incompetents).
“What would you do and what is your take on this?”
I’m so glad that this isn’t something that I personally have to worry about. But if I did…
Microsoft updates have to be treated with great caution, so I wouldn’t be in a rush to update anything because of this. I’d be more likely to write a monitor program to detect the issue and restart programs as needed. Ultimately, once I’ve seen the updates successfully installed by a lot of other people, I’d move forward with that.
I didn’t get a 404 when clicking the link on the portal site Martin. Instead it loads this article: https://support.microsoft.com/en-us/help/4491420/define-thresholds-on-the-number-of-http-2-settings-parameters-exchange
(But maybe it just came online)
Oh yeah, it just came online. Wonderful..
But HOW to set them is left unsaid. Kinda important to know, I think. Found this guidance:
https://www.reddit.com/r/sysadmin/comments/at61wn/microsoft_publishes_security_alert_on_iis_bug