VeraCrypt 1.20: 64-bit optimization, new home
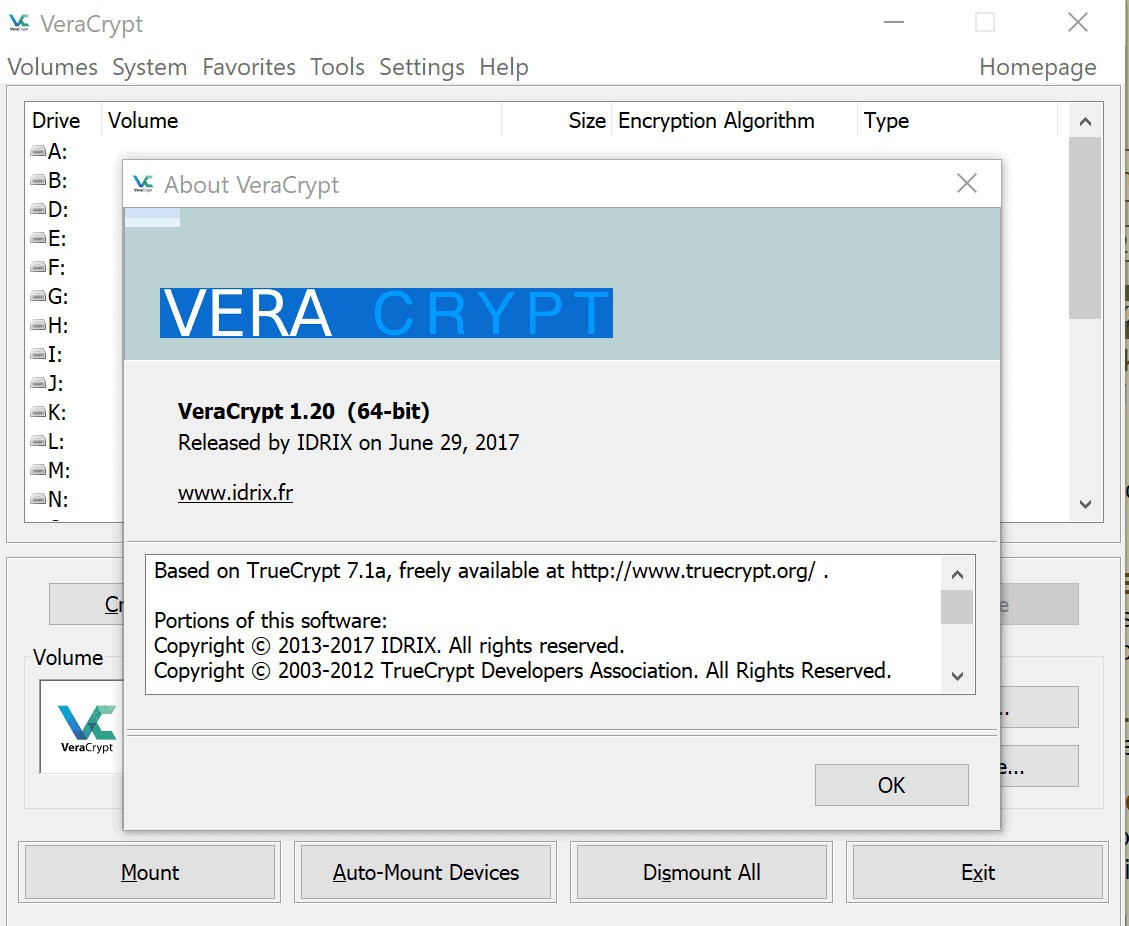
VeraCrypt 1.20 featuring 64-bit optimization, support for Secure Desktop for password entry on Windows, and more, was released on June 29, 2017.
The encryption software was one of the programs that came to life after the developers of the open source encryption software TrueCrypt stopped development under mysterious circumstances.
VeraCrypt is based on TrueCrypt source code, and compatible with encrypted containers and drives as a consequence.
The software is available for Windows, Linux and Mac OS X, and also open source.
VeraCrypt 1.20
The new VeraCrypt 1.20 comes with 64-bit processor optimizations for all supported operating systems. The developers have improved the implementation for Sha-512 and Sha256 which results in a 33% speed increase on 64-bit systems. Additionally, a 64-bit optimized assembly implementation of Twofish and Camelia is included in VeraCrypt 1.20 which makes Camelia 2.5 times faster if AES-NI is supported by the processor, or 30% faster if it is not.
Other major changes for all operating systems include the use of Address Space Layout Randomization (ASLR) for improved security, and the integration of a local HTML user guide instead of a PDF document.
The Windows version of VeryCrypt 1.20 has received quite a few changes of its own on top of that. It supports Secure Desktop for password entry in the new version which isolates the dialog from the rest of the desktop and other processes on the operating system.
The feature is not enabled by default, and VeryCrypt users need to enable it before they can make use of this. This is done under Settings > Preferences > Use Secure Desktop for password entry.
The option is available as a command line parameter as well. Use /secureDesktop yes to enable the feature.
Other major changes on Windows include support for the ReFS file system on Windows 10 when normal volumes are created, and the use of enhanced NX pool under Windows 8 or newer for additional driver security.
The new version fixes some performance regressions as well: the performance impact of checks for disconnected network drives has been reduced, and a high CPU usage case was fixed when mounting favorites.
The handling of EFI systems has been improved on top of all that. Windows users may edit the EFI configuration file manually. The developers fixed a bug in the EFI system description when using the EFI Rescue Disk, and fixed an incorrect warning about Windows not installed on boot time with EFI system encryption.
The changes are smaller in the Mac OS X and Linux versions of the application. The minimum version of Mac OS X has been raised to OS X 10.7 for instance, and both Linux and Mac versions check TrueCryptMode in the password dialog when they are opening containers with the .tc extension.
The project moved away from CodePlex as Microsoft plans to shut the site down this year. The main address of the VeryCrypt project is https://www.veracrypt.fr/ now.
Downloads are provided on CodePlex and SourceForge. The Windows version is not listed right now as a download option, but it can be downloaded from third-party sites such as MajorGeeks.
There was a forum thread on SourceForge about issues with 32-bit versions of VeraCrypt 1.20 on Windows, and it may have been pulled because of that. No confirmation has been given though.
Update: VeraCrypt 1.21 has been released. It fixes the issue of version 1.20.
Now You: which encryption software do you use, and why?




















If secure desktop is a windows thingy, does that mean the option is not present in the Linux version (I can’t find it in Preferences)? Aren’t Keyloggers used to attack Linux users?
The Release Notes for VeraCrypt 1.21 dated 2017-07-09 are at https://www.veracrypt.fr/en/Release%20Notes .
Stable 1.21 is out.
https://veracrypt.codeplex.com/wikipage?title=Downloads#Title
/EndofLife :oP
@ CHEF-KOCH:
Get a life, seriously.
shut up please.
he is right, and me too. crypto party yyyyyyyyyyy ;)
I call you a clown because you did not used any research, VeraCrypt was already audited. Look here: https://ostif.org/the-veracrypt-audit-results/
Seems 1.21 wasn’t final, yesterday (as mentioned) 1.21 RC3 was released. The changelog is here:
https://netix.dl.sourceforge.net/project/veracrypt/VeraCrypt%20Nightly%20Builds/README.TXT
I will continue to use TrueCrypt until an audit comes out saying not to use it under any circumstances. I’ve kept up with the audits and I just don’t trust Veracrypt. Call it a gut feeling, call me a clown, but my gut feelings are usually right. TrueCrypt continues to work for me and that’s all that matters.
1.21 is out.
I have posted this as an update in the article earlier today ;) Glad that they pushed out an update quickly.
I checked with the Veraceypt team and they told me:
“Yes, this file is original one but it was removed few hours after
posting because it should have been called 1.21-RC2 as there are stilll
some issue with some old hardware.
The final 1.21 will be published soon (Just waiting for driver signature
from Microsoft needed for Windows 10) so once the final 1.21 is release
you should update to have the latest code.
Normally filehippo should not have published 1.21 before an official
statement is made. They are too quick and they can create problem in the
future.
I hope they will update 1.21 installer when the final one is released.
Thank you for your message.
By the way, the latest version is 1.21-RC3 and you can get it from
https://sourceforge.net/projects/veracrypt/files/VeraCrypt%20Nightly%20Builds/ “.
Thanks for link. Contrary to your good advice as well as my own common sense, I successfully installed 1.21 from the last filehippo link you posted. The program can be installed as portable with caveats, which I did not do. The installed code says it is from
https://www.idrix.fr/Root/ but they give currently invalid sources to get 1.21 .
I still cannot find 1.21 with a google search, or using all the references in this article. What’s the secret to finding it?
Yes it is a bit of a mystery. You can grab it from here for instance: http://filehippo.com/download_veracrypt/
I would probably wait until the new version is available on one of the official download sites.
Regarding True Crypt, let’s not forget that we still don’t know why the developers called it quits (and we don’t know who the developers are, either). All we know is a third-party audit found some (not terribly important) holes afterwards.
So, assuming the worst (and less likely), that is some three-letter American agency put a gun to the developers’ head and forced them to open an unknown backdoor into it, after which they quit in disgust, True Crypt is still a very acceptable encryption program, depending on your threat model. If you are just protecting your hard drive against nosy guests, or petty thieves that would nick your posessions, the probability they would break your True Crypt volumes’ encryption is practically nil.
If, on the other hand, you need to protect the dealings of a Fortune 500 corporation with Iran, or the Russian GRU might be interested in the contents of your laptop, then it’s probably a bad idea to use True Crypt.
Anyone care to elaborate on Secure Desktop ?
I’m too lazy to Google it and to run into tl;dr article.
Special mode where what you type cannot be captured by keyloggers (like in Windows UAC). Screen goes dark, except for the box where you type your identifiers.
How read/write backward compatible is VC with TC containers? Any drawbacks with VC before taking the jump from TC?
VeryCrypt supports TC volumes, and you may convert these volumes to VeryCrypt’s format as well. Quote: Starting from version 1.0f, VeraCrypt can load TrueCrypt volume. It also offers the possibility to convert TrueCrypt containers and non-system partitions to VeraCrypt format.
A question… VC, Bitlocker, or what for Windows 8.1 FDE under UEFI?
Secure Desktop is nice. Weird it’s not selected by default. Same thing in Kee Pass, by the way : you need to know it’s there, and burrow down a long list of options to find it.
I’m happy to learn about the speed increase, because I did find Vera Crypt significantly slower than True Crypt (also, clunkier). Although it’s supposed to be more secure, which is difficult to beat.
Seems 1.20 has serious bug:
https://sourceforge.net/projects/veracrypt/files/VeraCrypt%20Nightly%20Builds/
https://sourceforge.net/p/veracrypt/discussion/general/thread/4a30f11c/
Yes TrueCrypt has several ‘holes’ which are vulnerabilities. They all require additional workarounds to work but there are present and that’s why the TrueCrypt Developer wrote to not use TrueCrypt.
As an example we had this one:
https://www.ghacks.net/2016/08/18/veracrypt-1-18-fixes-one-truecrypt-vulnerability/
https://www.comtek4u.com/content/2015/04/07/veracrypt-10f-2-update-fixes-truecrypt-audit-vulnerability
Most dramatically fix was that the ‘hidden volumes’ could be revealed which was recently fixed.
So the question is not to use TrueCrypt or not, you have to use VeraCrypt or BitLocker. One benefit on BitLocker would be that you can use VeraCrypt too to create/use mounted containers as ‘key store’ if you not fully trust MS.
The Truecrypt issues are well documented now, so TC is fine to use if those limitations don’t affect the use case.
Just me but given that there’s some reports of ‘rare’ instances where new Skylake & Kabylake have a HT bug,
I’m holding off on pushing my K especially when trying a fresh release of a fairly complex O/S related program.
Haven’t heard yet of an Intel or other patch via Windows 10. Short term fix said to be disable HT. Doing that
sounds awful at first blush but doesn’t usually creative drag on average use. More hit to multi-tasking and high
end media rendering kind of demands. Some bleeding edge, graphic intensive games for twitchers may have
a noticeable hit as HT begins to be used lot in them. Don’t know about that. Biggest issue would seem to be
if hackers exploit in a way that could threaten to crash CPU at random or pay us some bitty coin.
https://www.theregister.co.uk/2017/06/25/intel_skylake_kaby_lake_microcode_bug/
The v. 1.20 is causing BSOD for some users. That’s why in the download page it still v 1.19. See the forums.
Behold. We must hear from Pants first before we have our says.
Well I guess now they need another audit, these are big changes, some are affecting the actual encryption.
Not sure if can trust.
Martin, are you using this personally or prefer TrueCrypt?
I don’t use either, but if I had to choose, I’d pick VeraCrypt.
This is why version 1.20 was removed from sourceforge: https://github.com/veracrypt/VeraCrypt/commit/fe278afb18729fdc7c57a48ed4b2081f3cd64e39
Quote from sourceforge:
“Technical explanation: the 32-bit assembly code for SHA-512 uses an SSSE3 instruction but the C code only checks for SSE2 before calling it. So, on systems without SSS3, the SHA-512 code was crashing because of an illegal instruction.”
A version 1.21 is about to be released which will address recent issues following the release of 1.20.
Oh! So what are you using to encrypt your files?
DiskCryptor. Not sure if I will use it for much longer though as it has not been updated in a while.
VeraCrypt was audited by an independent party last year, and the developers patched the vulnerabilities that were identified. TrueCrypt has not been supported for two or three years now and will contain all the vulnerabilities that VeraCrypt has fixed.
TrueCrypt had holes which are fixed with VeraCrypt.
The question wasn’t directed to you.
Obviously, @Ademas knows that, but would like an expert opinion on whether those “holes” are significant enough to merit not using TrueCrypt.
https://www.veracrypt.fr/code/VeraCrypt/
https://github.com/veracrypt/
https://bitbucket.org/veracrypt/
Works well now with UEFI/GPT!