McAfee Raptor, a real-time behavior detection technology
McAfee just released Raptor, a real-time behavior detection technology that is available as a standalone version for 32-bit and 64-bit versions of the Microsoft Windows operating system.
Apart from being available as a standalone version, McAfee has integrated Raptor into Stinger, a standalone program that detects and remove viruses and other malicious programs from Windows systems.
Update: The standalone version of Raptor is no longer available. You may still use the Stinger application as it includes Raptor. End
If you run Raptor as a standalone version, you will first and foremost notice no change on the system. The program installs itself in C:\Program Files\McAfee\Raptor without installation dialog and runs in the background afterwards. The program folder stores log files and the quarantine as well.
The only indicator that it is running is its system tray icon and the Raptor.exe process that is listed in Windows' Task Manager and other process managers.
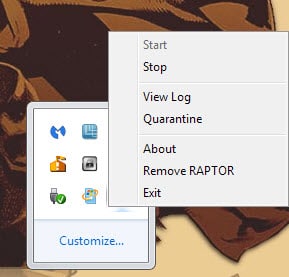
Raptor displays a handful of options when you right-click on its system tray icon. Use it to open the program log, quarantine or to stop it from running on the system.
The difference between exit and remove Raptor is the following: exit terminates Raptor's process for the session while remove blocks it from starting with the operating system on the next boot.
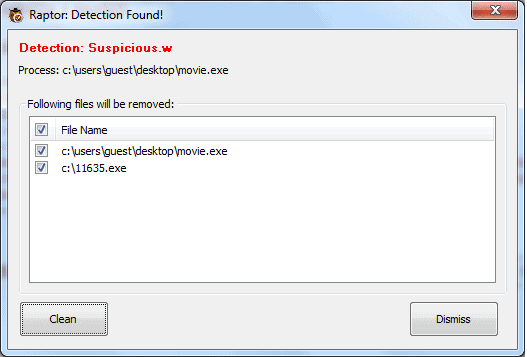
Raptor displays a dialog whenever it detects suspicious file running on the system.
A special version of McAfee's Stinger application, free to download and use as well, ships with Raptor now. You can download it from the official website where it is currently only offered as a 64-bit application.
When you run Stinger for the first time Raptor is installed automatically on the system. From there, it works just like the standalone version of the program.
The homepage reveals information about how Raptor works and what it does.
Stinger now includes Raptor - a real-time behavior detection technology that monitors suspicious activity on an endpoint. Raptor leverages machine learning and automated behavioral based classification in the cloud to detect zero-day malware in real-time.
According to McAfee, Raptor collects and submits system information to McAfee servers. This includes behavioral traces of files (typically a few bits according to the company) and trace information such as file name and path, its process ID, the version of the operating system and a random GUID of the machine.
It is too early to tell how effective Raptor is in preventing malicious 0-day programs from running on systems Raptor is installed on and how it compares to anti-exploit and other behavioral detection tools.



















When it comes to working with machines like I do on the side, you’ll become familiar very fast with McAfee. When I see anything with McAfee it gets removed. There were a few machines I did two years ago were McAfee was the cause of the system locking up. Easy work but long when your waiting on a crappy Laptops. Thanks Marin.
P.S I know what you mean, I’ll drop you a packet on the subject.
“According to McAfee, Raptor collects and submits system information to McAfee servers. This includes behavioral traces of files (typically a few bits according to the company) and trace information such as file name and path, its process ID, the version of the operating system and a random GUID of the machine.”
McAfee’s statements regarding the privacy implications of this structure would be most enlightening. Their FAQ is uninformative. Is there anything you can do, Martin, to chase some information on this?
It would also be of interest to learn how Raptor co-exists with other resident protection, particularly exploit defenses like EMET, Malwarebytes AntiExploit, etc. and more traditional resident anti-virus programs that also include anti-rootkit components. Since it is “behavioral” and “cloud based”, it may be that it will function well next to resident systems. Some assurance or denial would be helpful.
I fired off an email but I would not hold my breath.
While no platform is immune to malware, Windows is (and always will be) the most vulnerable, due to fundamental design flaws which cannot be fully remedied. Take for example this episode where Microsoft denied the existence of a major security hole, then released a patch which only provided a superficial improvement:
Microsoft responded, “Where the paper errs is in claiming that this is a flaw in Windows.”
http://en.wikipedia.org/wiki/Shatter_attack
(Since when are native Windows services and the Win32 API not part of Windows?)
“This research was sparked by comments made by Microsoft VP Jim Allchin who stated, under oath, that there were flaws in Windows so great that they would threaten national security if the Windows source code were to be disclosed.” (meaning: if you want a secure computing platform, do not use Windows.)
“The flaws presented in this paper are, at the time of writing, unfixable. The only reliable solution to these attacks requires functionality that is not present in Windows. When Microsoft saw a copy of this paper, they sent me a response stating clearly that they are aware of these attacks, and do not class them as vulnerabilities.”
-Exploiting design flaws in the Win32 API for privilege escalation
“Microsoft’s response that the desktop is the unit of protection is at best incomplete. There appear to be ways to break that model.”
– Hewlett Packard Laboratories
“Under Windows, there is no practical way to prevent code in the sandbox from calling a system service. In addition, third party software, particularly anti-malware solutions, can create new attack vectors.”
– Chrome developers manual
_________
Windows is slow and bloated enough without the anti-malware overhead, and in many cases this only provides an illusion of security. It is often better to abandon the platform than it is to struggle with the excessive maintenance (and the security holes that will never be patched.)
See also “redirect to SMB” — a back door that Microsoft has inserted into every version of Windows, including the new Windows 10:
“Wallace said the vulnerability would most likely be used in a targeted attack by an advanced threat actor because it requires control over some components of a victim’s network traffic. However, Wallace also noted that an attack could be launched via a malicious ad or through a shared Wi-Fi access point.”
“Redirect to SMB is based on research conducted 18 years ago by Aaron Spangler, and is an extension of a vulnerability that Microsoft promised to patch in 2009, but ultimately did not, only releasing an advisory and workaround method.”
http://searchsecurity.techtarget.com/news/4500244375/Redirect-to-SMB-vulnerability-affects-all-versions-of-Windows
__________
(If machines can learn to recognize behavioural patterns, perhaps a legion of drooling Windows users can learn to do the same.)
X-p
There is only one antivirus worse than Norton, and this is it. I wouldn’t touch any McAfee product with a 10-foot pole.
Lemme guess, you’re a(n) (delusional) AVG/Avast free version fan who thinks….just because the pretty packaging and company behind it seems legit, then it’s all the protection you and everyone around you will ever need. Well it’s not and both Norton’s and McAfee’s use different core engines to do similar jobs and each come up with different results. They aren’t the best but they have been around for a LONG time because they have good products. I wouldn’t trust my system to a freebie scanner with a pole of any size.
I only have seen trouble with McAfee,
Beginning this week a customer came in saying his system almost stopped working what it indeed did.
Turned out McAfee was happily running the harddrive @ 100% from boot for about 20minutes.
After this windows was able to get to desktop to just slow down to a snail again, as McAfee started using harddrive back to 100%.
Removing it in safe-mode solved it quite well, customer was happy of-course mostly because system was faster then when he got it as new including McAfee that came with it.
Have seen this so so so many times, even norton.. Not sure if they are making these virus scanners to act this way, or simply do not pay attention while coding it.
Hello Martin could you write a post like this https://www.ghacks.net/2009/04/21/avg-antivirus-linkscanner/
about the different link scanner addons/exstensions for firefox and chrome?
here are some
https://addons.mozilla.org/de/firefox/addon/trafficlight/
https://addons.mozilla.org/de/firefox/addon/drweb-anti-virus-link-checker/
https://chrome.google.com/webstore/detail/avast-online-security/gomekmidlodglbbmalcneegieacbdmki?utm_source=chrome-ntp-icon
https://chrome.google.com/webstore/detail/drweb-anti-virus-link-che/aleggpabliehgbeagmfhnodcijcmbonb?utm_source=chrome-ntp-icon
Hello Everyone!
I have not used any product from McAfee in years (due to glitches I have encountered in the past) but decided to give the Stinger/Raptor program a go.
WELP! It did NOT go! In fact, it was a Horror Show:
I used the scan briefly but stopped it so that I can see whether or not the programs could be easily removed from my (Windows 7 64-bit) computer system. Initially it could not be deleted the normal way. I had to use both the Everything (Search) software and Unlocker to find and then delete both Stinger and Raptor separately (as these) are in different Program folders:
I found the Stinger folder; then used Unlocker to remove it (It was deleted after Unlocker UNLOCKED said program. I then found the Raptor program after typing in McAfee in Everything (search). The Raptor files were so stubborn (to remove) that the computer needed to be rebooted!
Then this happened: After the reboot I was UN-Able to get an Internet connection! I then did a System Restore which was unsuccessful the first time. I then put the computer system in Recovery Mode and went into System Restore from there. This time said system was restored successfully. I do not know if my inability to get Online (after reboot) was just a coincidence after having removed the Raptor files or what . . . and I do realize that Raptor is currently in Beta. In any case, I won’t be trying any more McAfee products ever again . . . and that’s my Final answer!
i
Wow Mcafee programs sure don’t like your computer. I did not experience any of these issues during tests.
To remove McAfee products they usually have a program to do it because conventional un-installing doesn’t cut it as like a virus it is embedded in the core and oddly enough re-inserts itself when we try to force them off our systems. I do not know of this Raptor B.S. has a removal tool but from what I understand of the main program, the un-install tool removes all traces of their products.
I was a McAfee fan since Windows 2.5 and even up until 2005 but with each version what I noticed was more and more demand for system resources and any system with 4G of RAM or less slowed down to a crawl. Security wise, McAfee’s always found stuff Norton’s never found so I stayed with them for the longest time, but as I said that was up until 2013 when I made the jump over to Norton’s Internet Security Suite when I built myself a Hexcore – 8 Gb RAM, 4 Tb HDD system. I haven’t looked back.
Mainly because two things. First McAfee’s somehow relied on MS Internet Explorer as a shell interface and preferred the latest version at the time. And if it wasn’t updated to the latest version their software did not work. This is the same time I make the full time jump to Firefox. Secondly though we had the option to disable protection for xx amount of time for what ever purposes required, the program itself always had an option to add files/directories to a white list but that option was never available.
The program tab was present, but there was no actual button, or link to add files/directories. I had phone support service from McAfee’s so gave them a call, and their CSR told me certain portions of their programs are being phased out but in the meantime the individual modules have been disabled, not un-installed – simply disabled but still as an active process that wasn’t actually doing anything other than taking up resources.
I made the jump to Norton’s because they do have a way for me to exclude (white list) certain files/directories from any scan and their entire program basically runs from lesser files/resources than McAfee’s does. McAfee’s requires several modules each with several DLL files that ALL load into active processes regardless if the program or module was running or not. That is the memory hog portion of McAfee’s that I hated.
Norton’s is a bit faster and leaner and though like McAfee’s also has a toolbar and add-on/extension for my browsers, Norton’s can be disabled or simply we can choose not to install them. McAfee’s claims to not be installed but I always found it to be running in the background when I didn’t want it to.
Indeed.
This is my 3rd computer in 13 years and McAfee seems to have an issue with my computers!
(Is the ex-founder still on the lam?)
i
Every single time I’ve installed an application from McAfee, I’ve had problems. The system runs much slower, freezes up or crashes. I don’t have this migraine and don’t intend to get it.
After Norton killed PC Tool’s Threatfire, then Raptor will have to do.
I did so enjoy Threatfire.. simple, effective.
David, other behavior-based blockers still exist. I don’t want to recommend any one in particular; I’ll just suggest that you visit wilderssecurity dot com and skim through the discussions there (in the “other anti-malware” subforum).