Scan files for hidden executable contents
Attackers have multiple options when it comes to disguising executable files on a system to trick users into running them.
A common approach is to make use of Windows' option to hide known file types which may make it more difficult for users to identify the type of a file.
There are other options, for instance using the Right to Left Override trick to reverse part of the file name to change the file extension without modifying most of the file name or rename executable file extensions to safe file extensions and run the files manually using system commands.
While antivirus software may spot some of these attempts and block them, it is likely that at least some attempts are not detected right away.
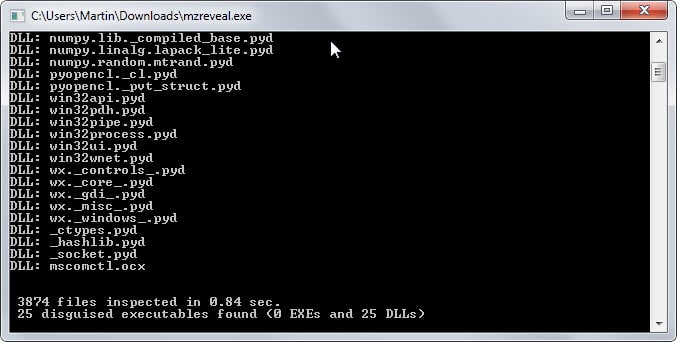
The free program MZReveal scans the root directory and all subdirectories it is placed in automatically for hidden executable file types.
The program is portable and you can run it right from Windows Explorer. It displays a prompt when you execute it asking you to say yes or no to bare filenames.
Once you have made the selection it will scan all files in all directories under that root folder. The scan is very fast, it took less than half a second to go through more than 3000 files for example.
Results are displayed in the prompt but it is closed seconds afterwards which means that you cannot go through them on the screen.
MZRevealer creates a log file in the root directory after the scan that you can load in any text editor to do so.
The log file lists all hidden executable files and their path on the system. Note that the author refers to PE (Portable Executable) files which means that the program won't find .exe files only but also .dll files and several other formats including screensavers or drivers.
The discovery of disguised executable files in the directory is not necessary a bad thing but it makes sense to go through each file, maybe scan it locally or on Virustotal, to make sure it is clean and not malicious in nature.
Verdict
The author announced that the program will receive updates in the near future with additional switches and options.
For now, it is a handy program to have even though you may not run it regularly on your system.
























Can the right to left “feature” be disabled on the OS level in Windows somehow? The ability to have files with *mixed* left to right and right to left strings seem useless. At least I can’t think of any legit use for it. The link Martin provided show that windows command line doesn’t obey the right to left instruction. So could not Windows Explorer, or the whole of Windows, be set to force all letters in left to right format?
Must not be working in Windows 10 Pro Preview? I searched both File Explorer and Everything.exe and still can’t find mzreveal.log.
I found ExeWatch add problems too and got removed from the Portable flash drive along with it getting dumped to a archive folder on the Nas Server.
Thanks for Tutorial Martin
I ran it in C:\ but can’t find the log file. Do you know what the filename and extension is? There isn’t any file you can’t find with everything.exe.
I ran it with admin prividges. The file is MZreveal.log – I too had trouble finding the log. Everywhere easily found it (but in the wrong places, but with the right content). I just left everywhere up with mzreveal.log as my search term – it shows up pretty much instantly. Make sure you haven’t got any filters, diacritics, case applied to the search.
Is this also a problem
under Linux?
This isn’t even exactly a problem under Windows. The kind of Windows user who can also use Linux wouldn’t be susceptible to this kind of tricks in the first place.
You’re mistaking on what I said, and you’re QED-ing me. What you’re expecting people to do is beyond most average joes grandpa and grandma, let alone using “Linux”. The people who could do that is also the same group of people smart enough to not fall into this “danger” while using Windows so the whole point is moot.
Many Linux applications — I want to say “most” but I can’t support that with numbers — are offered through curated, secure repositories. That said, Linux does not use the *.exe file extension to identify executables. Instead, information in the file header signals the OS that a file is to be treated as an executable. (Very oversimplified, but that’s the gist.)
In Linux, the command line can be used to scan for executable files. (Again, that’s oversimplified — “executable” depends on user permissions, for instance, and so you’ll get different results depending on whether the scan is run as root or as non-root user. Yadda, yadda.)
To check the validity of installed software, there is a utility (in the Debian universe) called “debsums” which can scan installed packages and check their meta-information against a master database.
OK .. what;s going on?
If I run it in c:\windows : it lists 4407 line items, 416 are “EXE”
If I run it in c:\windows\system32 : it lists 472 items, 8 are “EXE” (eg format.com, more.com, *.scr [screensavers] )
If I run it in c:\windows\SysWOW64 : it lists both sysWOW64 and system32 items for a combined total of 1403 items of which 24 are “EXE” (and the log file turned up in system32)
I had trouble finding the log files when in the system/syswow directories – not sure if initially I didn’t run it in admin mode – in the end I just left Everything with a search parameter in it so I could see what the heck was going on. I swear I was paying attention – the sysWOW64 dir run stuck the log in system32
Anyway – what the heck am I supposed to do with all that? What directory did you use Martin in that screenshot to get 25 files with zero “EXE”s?