Rootkit Detection Software Codewalker
Most computer users may have heard about rootkits for the first time when the Sony BMG rootkit scandal exploded in the news.
Sony BMG back then added rootkit-like behavior to select commercial music CDs. These installed resident software on Windows machines they were inserted in that shared most characteristics with rootkits.
Side note: World of Warcraft Hackers used the Sony rootkit for hacks.
Rootkits are still not considered a huge threat by many. It is more likely to get infected by a computer virus or trojan than by a rootkit, but rootkits are inherently more dangerous because of how they have been designed.
One core trait of rootkits is that they elude detection by normal security software, or the user running the system.
Codewalker
Codewalker is a rootkit detection software that has been developed by members of the Sysinternals forum.
The current version that has been released today is 0.24b which clearly outlines that the software program is a work in progress. It is a portable software that can be run from local drives or removable devices.
The security program suggests to run a deep scan of the computer system upon startup which takes a few minutes to complete. It is possible to skip the deep scan which will leads directly to the main program interface.
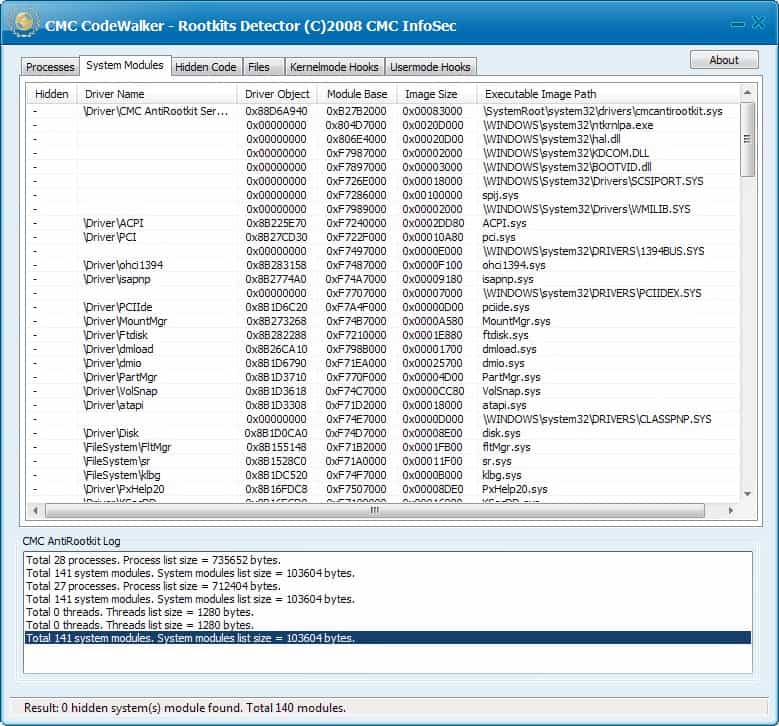
The main interface uses tabs to display various information including system processes, hidden code, kernelmode and usermode hacks which get populated when the system is scanned.
The connected disk drives are displayed on the right side with the option to select some or all of them for a scan. The same scan that was suggested upon program start will then be performed. The results are shown in the various tabs after the scan has finished.
The developer explains his program:
For hidden driver detection, you can test it with some pretty well hidden driver PoC such as phide_ex and many builds of Rustock.B variants. Although you have to use the "Hardcore Scan" method to detect them.
For code hooking detection, the engine walks all the branches of scanned module i.e any execution path of it to detect modification (btw, that's why i call it CodeWalker). IMHO, It can detect code hooking very well especially with rootkits that place abnormal hooks like Rustock.C (FF25 & FF15 - jmp/call dword ptr [abc]) tho there're still some problems with false-positive hooks/modifications.
Codewalker is a viable alternative to already available rootkit detection programs like Gmer or AVG Anti-Rootkit. It is probably be best used in conjunction with these tools.
Update: Please note that CodeWalker has not been updated since 2008. While it may run fine on all recent versions of Windows, it won't be as effective anymore as in the past because of that.






















avg still good here
i download and it find bugs
http://www.brothersoft.com/avg-anti-rootkit-free-60621.html
RootkitRevealer
http://technet.microsoft.com/nl-nl/sysinternals/bb897445(en-us).aspx
AVG Anti Rootkit free is no longer available, so this might be a valuable replacement.