Evidence Collector review
Update: Evidence Collector has been discontinued. It is no longer maintained but the most recent release can still be downloaded from the developer website linked below.
Have you ever asked yourself what law enforcement agencies would find when they analyze your computer?
How their tools look like and what they are scanning and checking for?
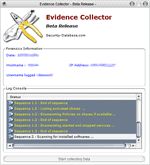
If you answered at least one of the questions with yes you may want to try out Evidence Collector (via Techtrends) which is a forensic computer program. Evidence Collectors main purpose is to help with IT incidents but it can give a solid impression on how such tools work generally.
It's a standalone tool which means it can be run from external devices connected to the computer which is definitely a prerequisite for all forensic tools.
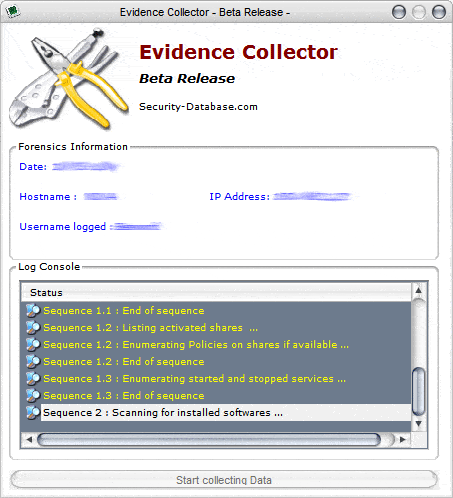
It analyses the user level at startup and displays information like the local IP and hostname. A click on Start Collecting processes 14 sequences, some with subsequences, that collect data and write that data to logfiles in the Evidence Collector directory.
The software did write 25 different log files into the log directory including a list of opened files, installed applications and processes during a trial run.
Evidence Collector concentrates on hardware and software only while law enforcement agencies would definitely scan the computer for files as well, probably using a software like Locate to find information in filenames and contents.
A detailed list of what is analyzed:
- Shares and policies applied on shares
- Started and stopped services
- Installed software
- Installed Hotfixes
- Enumerated Processes
- Events logs
- TCP / UDP mapping endpoints
- Process handles tracking
- List start-up programs
- Suspected modules
- Users policies
- USB history
Note that you need to process the accumulated data using other tools or manually as it does not offer any options in this regard.
Evidence Collector is a free software currently in beta. There is no information on the homepage about compatibility, it ran fine on my Windows XP Service Pack 3 system.
























I’m suprise bye USB.AccessHistory.log, impresive ^^
What you guys are sayin ??
this aint big brother .. this could prevent from any attempt to inject rootkit or any trojan.
This tool acts as master coordinator of many other utitlities.
My school has this sort of thing but it isn’t much use l0l, I either usb boot XP or go in safe mode and terminate it’s service. Although I agree it’s big brother :<
The BIG BROTHER now on your PC.