Hackers targeting air-gapped devices in Eastern Europe with new malware

A concerning cyber threat has emerged in Eastern Europe, where Chinese state-sponsored hackers are employing a new and sophisticated malware to breach air-gapped devices.
These malicious actors, associated with the cyber espionage group APT31, also known as Zirconium, have been conducting a series of stealthy attacks on industrial organizations in the region.
The attacks, first detected by cybersecurity company researchers at Kaspersky in April of the previous year, utilize a multi-stage approach and have raised significant concerns about the security of air-gapped systems.

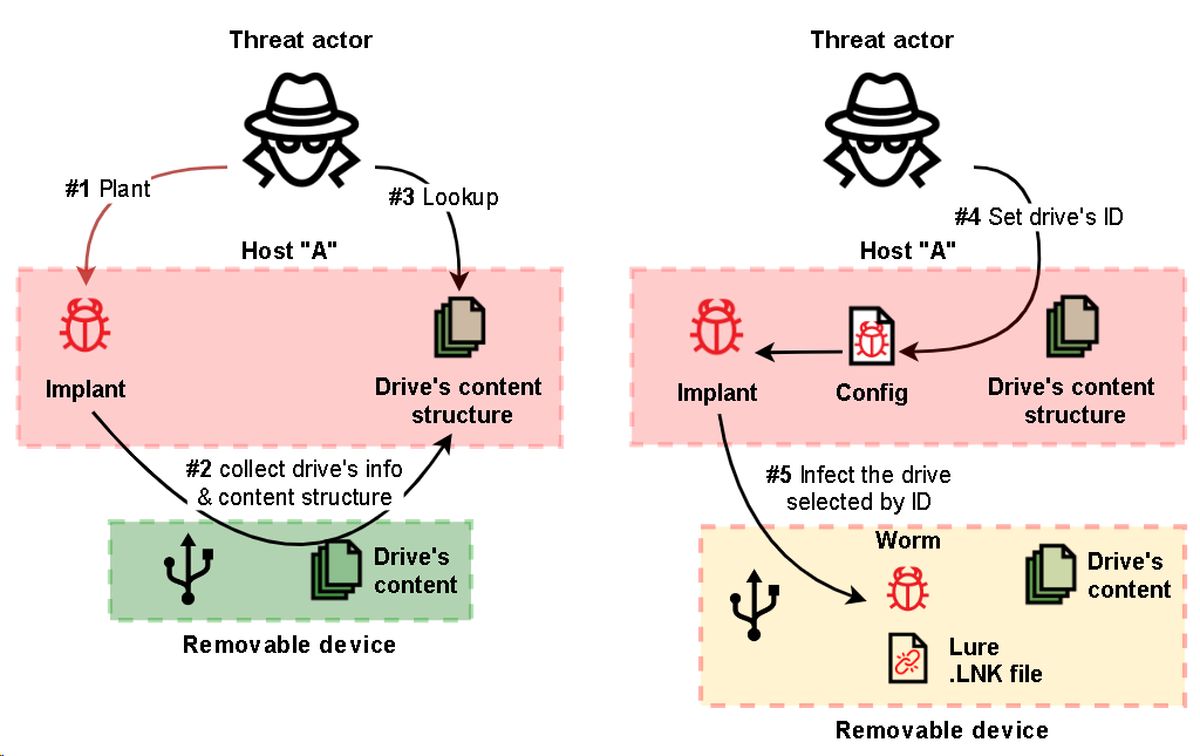
The attack has a three-step approach
During the initial phase of the attack, the hackers deploy at least 15 different implants, belonging to the "FourteenHi" malware family, to infiltrate the targeted systems. These implants are designed to establish resilience and remote access to compromised systems. Simultaneously, they collect valuable data that aids in identifying further opportunities for exploitation.
In the second stage of the attack, APT31 employs specialized malware to specifically target air-gapped systems. Using USB propagation, the hackers infect removable drives and use them as a pathway to breach the isolated networks. This allows the malware to intercept sensitive data stored in air-gapped devices.
The third and final stage of the attack involves the use of implants that can upload the collected data to the hackers' command and control (C2) servers. This data may contain valuable intellectual property, sensitive information, or other critical data stolen from compromised organizations.
Malware is unusually advanced
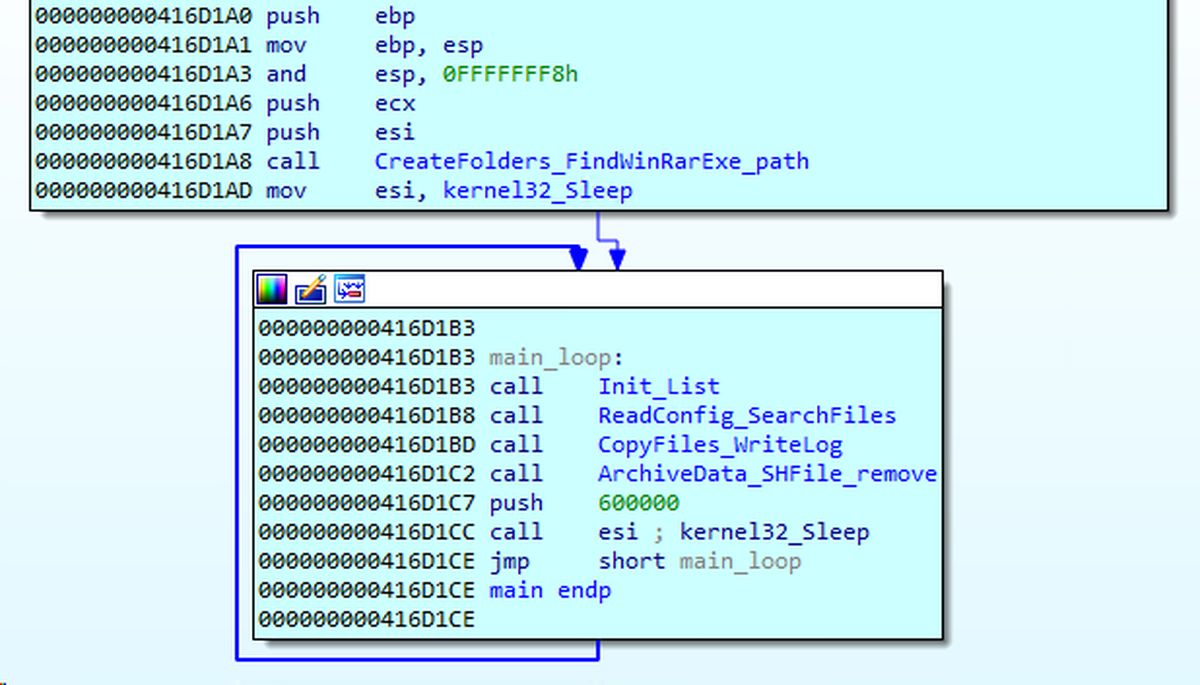
The malware used in the attacks consists of four distinct sections. The first section profiles removable drives attached to the infected system, collecting files, capturing screenshots, and recording window titles. Additionally, it drops additional payloads on the compromised device to ensure further infiltration.
The second section of the malware infects removable drives by copying a legitimate McAfee executable, which is vulnerable to DLL tampering, along with a malicious DLL payload. These are then set as "hidden" in the root directory of the device, and a Lure LNK file triggers the infection when accessed.
In the third section, a script is executed to collect data from the infected device and save the output to the "$RECYCLE.BIN" folder, from where the first module retrieves it.
The fourth section, seen in some attacks, acts as a payload dropper, keylogger, screenshot capture tool, and file stealer.
To avoid detection and analysis, APT31 employed advanced tactics, such as hiding payloads and malicious code in binary data files and the memory of legitimate applications. This made it challenging for traditional security measures to detect and respond to the threat effectively.
Read also: Malware with faked timestamps on the rise to bypass Windows protections.
As the attacks progressed, Kaspersky observed an additional implant used by APT31 to harvest local files from the compromised systems. This implant utilized decryption and payload injection techniques to remain undetected, further demonstrating the group's sophistication in cyber espionage.
Advertisement















– Disable autorun for external media.
– Disable USB ports for removable media on critical systems.
– Train users not to be total dumbasses by sticking in USB drives of unknown origin.
Pick any of these; personally I’d say the first two should be more than enough.