OSArmor monitors and blocks suspicious processes on Windows
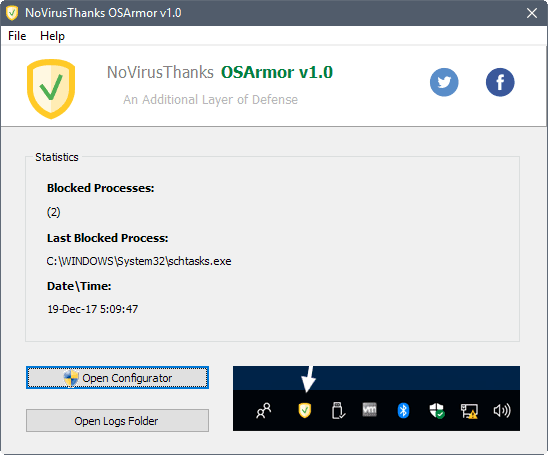
OSArmor is a new security program by NoVirusThanks for Microsoft Windows devices that monitors the system to block suspicious processes or actions on the system.
The security program has basic anti-exploit protection built into it, but it is not comparable to Microsoft EMET or Malwarebytes Anti-Exploit, as its focus is on preventing certain processes from executing in first place or certain activities from being executed.
A basic example is the blocking of processes that have double file extensions, sample.txt.exe to hide their actual type from unsuspecting users.
OSArmor review
OSArmor is compatible with all recent versions of the Microsoft Windows operating system. The application needs to be installed before it can be used. The installer itself is clean, and the program is launched right after installation.
The interface is basic at this point in time. It displays session information about the number of blocked processes, the last blocked process, and the date and time that happened.
You cannot do much other than opening the logs folder or the configuration. First time users may want to open the configuration first as it lists all the security features OSArmor supports.
Most protective options are enabled by default. The list is rather long, here is a short listing of interesting ones:
- Block execution of pif, com and double file extensions.
- Block USB spreading malware.
- Prevent "important" system modifications via bcedit.exe.
- Block direct execution of scripts and exe files from archives.
- Prevent regsrv32 from executing remote scripts and /i: parameter.
- Block processes executed from wscript.exe, cscript.exe, mshta.exe and wmic.exe.
- Block executionpolicy bypass and windowstyle hidden in PowerShell.
- Block remote URL downloads from the command line.
- Block direct execution of JavaScript and VBscript code.
- Limit Windows Screensaver files to Windows folder.
- Block execution of schtasks.exe.
The only options that are not enabled block the execution of unsigned processes from Local AppData, Roaming AppData, CommonAppdata, and Control Panel Applets.
The program comes without help file which makes it a tool for advanced users. It runs silently in the background for the most part and writes any processes that it blocks to daily log files.
The log files are a history of blocked processes, and they are the only option to troubleshoot issues. Logs list date, time and processes, as well as rules that blocked the process from execution.
One of the main shortcomings of OSArmor is that it comes without whitelist. You can only disable a protective feature if you notice that legitimate processes are blocked by the application.
The program needs a whitelist direly, and an interface that lists all blocked processes directly so that you can whitelist certain blocked processes easily.
Closing Words
OSArmor 1.0 is a promising security program for Windows that blocks activity that is often abused by malware and other unwanted software. The lack of control over what gets blocked is the program's main weakness at this point.
An option to display a prompt (allow or deny execution, research online) would be useful, and a whitelist needs to be implemented as well so that false positives can be addressed without having to turn off a feature completely.























OSArmor has a whitelist now though adding to it can still be tricky unless you catch it right at the moment it blocked something. That said it has improved quite a bit at version 1.4.3 now and it is much better than the 1.0 Martin reviewed originally.
OSarmor est la solution qui va combler la limite des antivirus.
Very good and promising…!!!
Thnx
No-Virus-Thanks has many good tools.