Large number of Android VPN apps insecure
Virtual Private Networks (VPN) have evolved from a technology used mostly by businesses to one that is used by more and more home users as well.
Reasons are manifold, but improved privacy and security are certainly two key features that make a growing number of home users use VPN services and apps.
Without going into too much detail; a VPN protects a device's IP address as traffic flows through it instead of directly to the user's system.
Google's Android operating system supports native VPN clients since Android 4.0 released in October 2011 through the Android VPN Service class.
When enabled, VPN applications on Android intercept and take full control of a device's traffic.

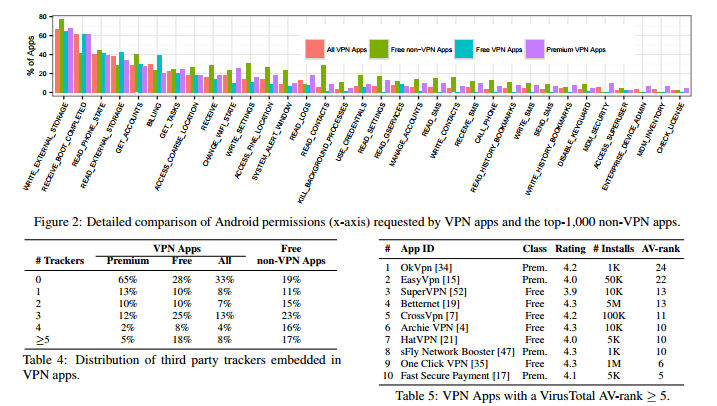
A team of researchers analyzed more than 280 Android VPN applications for privacy and security issues. The results, revealed in a research paper, reveal that many free and premium VPN applications on Android are insecure.
Key findings include
- 67% of Android VPN applications promised to protect user privacy. 75% of those used third-party tracking libraries, and 82% requested permissions to access user information such as text messages.
- 37% of Android VPN applications had more than 500K downloads, and 25% at least a 4-star rating. Over 38% of those applications showed signs of malware on Virustotal.
- 18% of all VPN applications implemented tunneling protocols without encryption.
- 84% of VPN apps do not tunnel IPv6 traffic.
- 66% of VPN apps do not tunnel DNS traffic.
- 18% of VPN applications don't reveal "the entity hosting the terminating VPN server", and 16% of apps may forward traffic using peer-to-peer forwarding.
- 16% of VPN applications deploy non-transparent proxies that modify HTTP traffic, for instance by injecting or removing headers. 2 of those inject JavaScript for advertisement and tracking purposes.
- 4 of the analyzed VPN apps perform TLS interception.
The research paper does not include the full list of tested Android VPN applications, and the issues identified in each of them. That's unfortunate, as it would have helped users make an educated decision on which Android VPN application to install on their device, and to verify that installed VPN apps are not misbehaving.
Some VPN apps are mentioned however. The research paper lists all VPN apps that were flagged as potentially malicious by Virustotal, and apps that have "egress points in residential ISPs".
The researchers suggest that Google needs to rethink the VPN permission model, as the current one is putting users, who are mostly unaware, at risk.
The ability of the BIND_VPN_SERVICE permission to break Android’s sandboxing and the naive perception that most users have about third-party VPN apps suggest that it is urging to re-consider Android’s VPN permission model to increase the control over VPN clients. Our analysis of the user reviews and the ratings for VPN apps suggested that the vast majority of users remain unaware of such practices even when considering relatively popular apps.
Now You: do you use a VPN application on your mobile device?
















I would expect advice and guidance not just article about what we all know, hello Icecastlle where did you go?
The best VPN for Windows and Android is Psiphon by Psiphon Inc. for sure. And it’s even free.
God bless the developers.
I use PrivateInternetAccess.com
It works on PC, Android, Macs and iPhones. It’s about $50-$60 per year for 5 devices. But it utilizes strong encryption and a total lack of advertisements, tracking and storage of your activities. Everything is never stored so it’s never wiped.
I don’t think this survey is made for the usual casual user. At least I get completely lost in it and I believe I am not the only one.
Can someone please answer if F-secure Freedome (I am using it) is recommendable ? Thank you.
VPNs are mainly for public wifi safety and such, the day everybody wanted them to be for more they were going to “abused”. Abused as in the level of trust needed was never going to be fully realized.
I have looked at a few *free* VPN apps on Android and the TOSes have always scared me off. For the last few years, I have used and *paid* for a highly-rated VPN provider that keeps no logs, tons of IP addresses, has great customer support and recently packaged in ad-blocking. I trust them more than I do the Googles, Microsofts and Facebooks of the world.
I say this because the report, which does NOT list the VPN offenders, might be enough to scare off users from using quality VPN services to enhance privacy and related issues. It might be used by our arrogant technological overlords as an excuse to ban VPN apps or tweak their systems to keep these (easy to install) apps from running effectively. It could drive ISPs and governments to use reports like these to enact policies that benefit their surveillance and data-mining programs. It could certainly be used by record and movie labels as additional FUD.
While most of us here understand that this isn’t a negative blanket statement on VPN services, it should always be pointed out (to the uninitiated) that quality VPN providers do exist and are important as one of the many tools available to end-users in their fight against illegal data-mining and surveillance.
So which VPN ist it ? Don’t leave us in the dark – please enlighten us. :)
Is there some type of test I as an individual could use to see if my VPN is working properly? How do I know all actions are going through the VPN? I can check my IP address but that doesn’t tell me if all of my data is going through the VPN.
A DNS leak test comes to mind. There are lots of websites doing this. You could probably also use some network sniffing software to visually confirm that everything leaving your PC is going to the same address. But the bigger question is, What’s going on internally at the VPN itself? There is no 100% certain way to know. You’ve got to collect as much information as you can about the company and then roll the dice.
In the UK, a VPN is a basic requirement for internet usage, since the country’s new Investigatory Powers Bill allows practically any government employee in any division to look up your internet history for the part year. That sounds like an exaggeration, but amazingly it isn’t. Even if you aren’t worried about what the department or employees could do with your data officially, these are humans trusted with this power: hundreds of thousands of them. Any malicious group could easily put their man into one of these departments and retrieve whatever data they want.
Even if you’re not in the UK, there’s no doubt there are sleeper cells from malicious groups in every ISP already. Why wouldn’t there be?
“Why wouldn’t there be?â€
Yeah, sounds like a truly good reason to install DPI, which is 10 times more expensive than normal network equipment already costing a small fortune. Just because why not?
“allows practically any government employee in any division to look up your internet history for the part year”
Do you have a trustable link that confirms this ? They can do so without contacting any judge whatsoever I assume ? I know about this bill but don’t know the details. (Don’t worry I don’t need to be convinced this is bad, it’s just knowledge I wish to validate so I can use it :) )
Thank you Martin for focusing on issues like quality of apps.
This research paper would have been much more useful with a complete set of results for all 280 VPN apps.
Agreed, this would make it more useful.
I don’t get this screenshot and what it really shows. So this is about ipleak? Or really about the app itself. There is a difference, an app can be secure but the service leaks your ip anyway or the app causes this.
I’ve been doing a lot of research on VPN’s recently, and I have to say, this does NOT surprise me. My research is concentrated on fixed location small business models, but has spilled over into the mobile device arena per requests from my client. So, first things first, thanks Martin! This news and the links provided are very timely for me.
I started looking seriously at VPN’s using OpenVPN as my baseline. Y’all need to check out OpenVPN. I went there because the source code is, as you would expect by the name, “open”. There’s a thousand pages of information at the site, and the actual code for OpenVPN is available, and put together by a group of experts. I studied it all and gained a boatload of knowledge.
My plan was to use OpenVPN as a baseline, and then dig as much as I could into other commercial products and find the perfect fit for my client, and hopefully other clients down the road. After almost two months, I keep coming back to OpenVPN. They’ve thought of everything over there. I also like their payment plan for a private tunnel. It’s set up by data usage. They’ll give you 200mb for free, so you can create an account and play with the private tunnel. After that, for US $20 you can buy 100Gb (total data usage – up/down) and install on unlimited devices or for US $30 you can get unlimited data for 10 devices for a year. OK, I’m done plugging OpenVPN (Yes, OpenVPN is available for android. No, I don’t know if it was part of the review.)
There’s far more to a VPN than how many servers they have, how fast the connections are, or what encryption is used. These are all valid points of concern, but as the Android debacle shows, getting to the meat of the API and actually seeing what the tunnel is doing with your traffic is paramount. After investing many hours educating myself all I can tell you is look deeper than the marketing plan for your VPN. Ask technical questions. Bottom line: I actually don’t know who to trust. I’m probably going to recommend OpenVPN to my client, and see if I can negotiate a yearly deal with them for slightly more than 10 devices, or just buy two of the unlimited plans. At least at OpenVPN you can see the code and talk to technical people directly.
Lastly, as far as whether or not you need a VPN, this is the question my client originally came to me with. Seems like a general consensus among most tech journalists is that “yes, you do”, or at the very least, “yes, maybe not today, but certainly tomorrow”… I’m still not convinced that’s true. There are real security benefits to be had, but there is also a cost and performance trade-off. Plus, it’s another layer of software that must be installed and updated/maintained. I don’t know about you, but in my area a lot of small businesses are looking to consolidate their IT. Simple is better. In the case of a VPN, when a user complains “The internet is down” it’s yet another item to check (ISP, router, client device NIC, client device browser, VPN…)
Funny thing is, I was just thinking the other day that fixed locations, doing nothing nefarious on the internet, would probably be better off shopping for the best ISP rather than the best VPN… Whereas mobile users, dropping into unknown hot-spots all the time, well they could certainly use the added security of a properly setup and protected tunnel… Especially for sensitive business information/exchange.
And now we have this: Android VPN’s are crap!
Regards,
Mr. Joey
Just to clarify (something you probably already know but that is not clear from your post): OpenVPN is a client, not a VPN service. The VPN service you’re talking about is PrivateTunnel, a spinoff of the OpenVPN project. One does not need to have a PrivateTunnel account to use the OpenVPN client.
And yes, OpenVPN is fantastic. I use the Android version to handle my third party VPN service (Mullvad). It’s a good way to go.
“Funny thing is, I was just thinking the other day that fixed locations, doing nothing nefarious on the internet, would probably be better off shopping for the best ISP rather than the best VPN…”
Exactly. That’s why I don’t use VPN, also knowing that most suck and it’s a chore to find the right one. I’ll use Tor in some cases and my ISP for the rest. That ISP is way good and trustable enough and provides a decent amount of dynamic IP ranges, with IP address renewable at will. Of course by law it does store data for a year and will let law enforcement check in as mandated by yada yada you get it.
But some people don’t have a trustable ISP near them. Or just as bad, are stuck with a fixed IP.
ProtonMail said that they were looking into creating an actually secure and private VPN service though, and that is interesting. I may start using a VPN if it is theirs.
The proliferation of VPN providers and the eagerness with which they are ready to give their products for almost free in recent times already had made me suspecting them, so I never use a VPN.
Also, being used to surf over Ixquick, I never actually felt any need for a VPN. Only sometimes I use their Proxy links to access websites that are blocked by ‘authorities’, and that works.
In fact, I wonder what differences there are between them and VPNs, I guess it’s just an other name for the same, with VPN sounding more like ‘you definitely need to buy my app if you want to feel safe’ , no?
Btw, I recently read that China is making its use formally illegal these days, with serious penalties, and guesses are that the government here (in Thailand) might soon follow their example.
Correction : their use, VPN,s
It’s crazy how many people just download apps without considering the data these apps will gain access to and the potential repercussions of their actions to install the app. God knows the huge amount of sensitive data that’s is being transferred to corporations.
Finally someone looked into the whole array of half cooked so called VPN applications available. Even paid version rather rarely prevent DNS leakage. What is worse, majority claim to be VPN but in fact they just use alternative DNS, no encryption and tunnelling. Been using VPN for quite sometime and realized that most of even “premium services” are not even close to what they claim to provide.
The best VPN for Windows (aside from Tor) and Android is Psiphon by Psiphon Inc. for sure. And it’s even free.
God bless the developers.
free? THE BEST?!! ha!
i am a network administrator and IT Security Consultant. Do not be quick to call the free stuff the best. Its usually the least secure. and because it is free, they are offering it to you bundled with ads, apps and trackers that dont always follow your requests to privacy.
my personal suggestion of a GREAT vpn that is not hosted in the us. is not owned by a us or an EU country… is
VPNTUNNEL.COM for 35$/yr you can have unlimited bandwidth and 5 concurrent devices on at the same time.
They also even support OPENVPN …