Firefox Add-on YouTube Unblocker blocked by Mozilla
Mozilla banned the popular Firefox add-on YouTube Unblocker yesterday after it was confirmed that it tampers with Firefox security preferences, and downloads and installs an unrelated add-on from an unofficial website.
The add-on, used to unblock YouTube videos that are blocked in certain countries by redirecting access through proxy servers in countries where the video is available, has hundreds of thousands of users.
The bug report on Bugzilla offers details on the add-on's wrong doings. It disables Firefox security preferences using user.js manipulations, among them the blocklist feature and add-on signature enforcement, and downloads another add-on afterwards, named Adblock Converter, which it hides from the browser's Add-on Manager.
Please note that the downloaded extension may use different names, so make sure you check for any add-on listed in the Add-ons Manager that you have not installed.
Looking at the code of the add-on "YouTube Unblocker", I found the responsible code in the file [email protected]\resources\unblocker-api\lib\utils.js following line 138. The function updateConfigFile() downloads files from a web server and places them onto the hard drive of the user.
In the case of the attached response.json it is a user.js and a malicious add-on. Both are a clear violation of the add-on guidelines.
Firefox users who have the add-on installed in the browser should consider the following course of action immediately:
- Removal of the YouTube Unblocker add-on if that has not been done already by Mozilla through the browser's blocklist feature.
- Removal of the adblock converter extension using Firefox's Safe Mode. This can be started by holding down the Shift-key on the keyboard before Firefox is launched.
- Opening the profile folder to delete any traces of YouTube Unblocker or Adblock Converter, especially any folder starting with youtubeunblocker
- Starting Firefox, opening about:config and resetting the following Firefox preferences by searching for them, right-clicking on them and selecting reset from the context menu:
- xpinstall.signatures.required
- extensions.blocklist.enabled
- extensions.blocklist.url
- extensions.blocklist.detailsURL
- extensions.blocklist.itemURL
Firefox users who want to be on the safe side should consider resetting the browser instead. This can also be done by holding down the Shift-key on the keyboard during start of the browser.
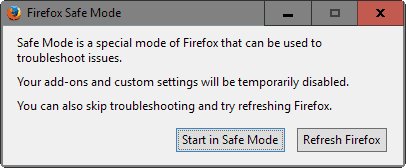
Select Refresh Firefox this time to reset the browser. Please note that this will remove installed add-ons, themes, and reset preferences and other customization, but will keep bookmarks, passwords, the browsing history and open windows and tabs among other things.
The add-on is no longer listed on Mozilla's official Add-ons repository (AMO). (via Sören Hentzschel)
















How do you remove Adblock Converter – simply look in about:addons while in safe mode? I can’t see it there.
this is what i want to know too, they say it hides from the addon menu but they say to look there still. . .
other than searching .xpi for add-ons you didn’t install, searching for Unblocker and adblock convert. anything else i should look for? also you should add, that you should delete the user.js file because even if you change the about:config settings the user.js will just overwrite it on restart.
I’ve been a month late to this and malwarebytes found a Crapton of youtube unblocker stuff and saw the addon gone in firefox. i used Control+C and found nothing about adblock converter. am i fine?
Has anyone written a Greasemonkey script that works around GEMA?
https://addons.mozilla.org/en-US/firefox/addon/proxtube/
The purpose of this add-on is to bypass Google’s a.ssinine and arrogant blocking of videos I used to be able to see, most likely because it will interfere with their “youtube red” atrocity. So just how much did Google pay Mozilla to blacklist it?
Did you read the article?
Hmm… setting user.js to read-only might be a good idea.
Is it a day ending in y? Must be time for news of another Mozilla Coch-Up.
Seriously, what’s the ratio of bad news to good with Mozilla the last 3 years or so? It’s utterly distressing.
For step 4 (Starting Firefox, opening about:config and resetting the following Firefox preferences by searching for them, right-clicking on them and selecting reset from the context menu:) “reset” is grayed out, so i’m unable to do this.
Also, I had the same extension installed to google chrome, is there a similar list of things to do for it?
Google’s extension system is different from Mozilla’s. I’d remove the extension from the browser, but that is probably all there is to do.
What about the add-on it downloads? What does it do? I’m surprised that’s not mentioned.
What I find odd is that the article does not mention what the ‘rogue’ Adblock Converter does. I suppose it’s unethical to have it installed in the background and hidden, but is it actually malicious? The article skips over this and rushes to instuct everyone to quickly uninstall everything. Why should we? I personally never used the addon, but if I did, I would have done so for a reason and would be loathe to remove something that I might have found useful.
Bug report was updated.
@trek100
http://mozhelp.dynvpn.de/guide/youtube-download-bookmarklet
German site, but there’s also a video guide.
From somewhere else I’ve got a custom search engine, which redirects videos through proxfree.com. This may not be as comfortable as an addon, but the good part is that a webbased service cannot install stuff on your computer.
Can you share the “simple bookmarklet”
with us?
(so we can inspect it and maybe try to use it, if it’s safe…).
Thanks!
You don’t need an addon to unblock youtube videos. It’s enough to have a simple bookmarklet which redirects the youtube URL to one of several websites which can unblock it.
Did it really do all the bad things? No. All News chatter only the notice someone unknown (Google employee?) writes in the system. Did it disturb an maybe upcoming business model by YouTube? Yes. Is it anticipatory obedience? Yes. German users need this Addon, cause YouTube is unable finding an agreement with GEMA. You should be angry about this incident. It disempowered your will and decision. We should be thankful? You are kidding, right?
Well Ole, the code is there and the addon changed the mentioned preferences in the config so yeah, no need to defend this.
And there are still plenty of addons out there that do the same thing for german users, i changed back to ProxTube again and it works flawless.
Yes it did bad things. It installed a second malicious addon, it disabled the extension signing check, it disabled updates…
So yes, you are kidding….
what a shame
the code is very obvious
how this got approved
if I’m not wrong I saw this addon in AMO from a long time
it take all this time to got revealed
I’m wondering about the real number of the undiscovered malicious addons in AMO?
can you throw in more details please
how many Ppl got infected
from how long the malicious code exist
There is a lot more, last month I was looking for a new translator add-on I found at least 4 addons using external code to track the user and inject code and advertisement when browsing, 3 addons were from China one from Russia.
The “best part” 2 of those addons had the SAME base code the biggest difference was the name.
Every-time I install a “suspicious” addon I browse quickly the code it’s EZ to do and save lot of trouble.
What is the most suprising is that that those addons are signed and were reviewed (by who?) I’m not a programmer and if I was able to understand the code I was expecting Mozarella reviewer to catch them especially when those reviewer make hell of the life of “good developers” by asking for non-sense and took months before an simple addon is approved.
Can you share the addon names
with us?
(so we can all stay away from them…!).
thks!
Did it slip through the AMO Review Process?? Did it get approved with this code included?
I really liked that addon! Is there a way how I can still use it?
Jacob, keep watching for a clean replacement from a different extension author. Among the 100,000+ users, certainly someone will whip up a replacement.
So the purpose of extension signing is…?
> So the purpose of extension signing is…?
The downloaded config file disables the extension signing requirement. That’s the reason why it’s good that the preference to disable the extension signing requirement will be removed in Firefox 46.
THis addon was signed, wasn’t it?
Also it did more damage than just disabling signing-enforcement.
Yeah, great to remove options because of some random Malware. Mozilla creates a walled garden since they want to be in control of what a user is able to install. In former times Mozilla was successful with the opposite.
PS: This was Script-kiddie level, I could easily have done the same.
money?
Security-theater.
The user.js it’s downloading is hilarious.
=====
user_pref(“xpinstall.signatures.required”, false);
user_pref(“extensions.blocklist.enabled”, false);
user_pref(“extensions.blocklist.url”, “https://www.google.com”);
user_pref(“extensions.blocklist.detailsURL”, “https://www.google.com”);
user_pref(“extensions.blocklist.itemURL”, “https://www.google.com”);
user_pref(“extensions.update.url”, “https://www.google.com”);
user_pref(“extensions.update.background.url”, “https://www.google.com”);
user_pref(“toolkit.telemetry.archive.enabled”, false);
user_pref(“toolkit.telemetry.enabled”, false);
user_pref(“toolkit.telemetry.server”, “https://www.google.com”);
user_pref(“datareporting.healthreport.uploadEnabled”, false);
=====
Script-kiddie style.
EDIT:
I’m more about the working directory-traversal in there:
“”local”: “/data/config.json/../../../../user.js”,”
Scary.
if affected users are doing a manual clean-up they should clear the user.js file out of their profile folder as well
Strange what’s next blocking Zenmate because it also acts like/Proxy/VPN. Makes less sense, same like Google anti-adblocking banning on stores, blocking them but allowing adblocking within the browser itself.
if being caught spreading malware isn’t enough, what would be your threshold of taking action against an addon then?