World's Top 200 Common Passwords continue to be incredibly weak

Weak passwords continue to be a problem on today's Internet. It seems that many users continue to pick weak passwords that were weak 20 years ago and continue to be the weakest of the weak. It is probably part convenience and part not-knowing-better that play a role here.
NordPass has released its six annual password report of the top 200 most common passwords. The company has analyzed a 2.5 terabyte database that it "extracted from various publicly available sources".
Note: It is likely that NordPass could not crack the entire list of passwords. With that said, if one of your passwords is found on such a list, you better change it immediately to something more secure.
The top 10 of all countries looks like this:
- 123456
- 123456789
- 12345678
- password
- qwerty123
- qwerty1
- 111111
- 12345
- secret
- 123123
You can check out individual lists of 44 countries or the same for corporate passwords, which NordPass lists in a separate list.
All of the non-corporate passwords that make up the top 10 are cracked in less than one second according to NordPass. The other 190 passwords use a similar scheme and most are also cracked in less than a second. While numbers and qwerty dominate, there are also single words and even some passwords that are more complex on the list.
Related Content:
You find tag12wsx in position 30. It was found more than 90,000 times according to NordPass. Other examples include 111222tianya, found more than 44,000 times, and chesse, which was found more than 23,000 times.
If you take a closer look at the passwords, you may notice the absence of symbols. While there are one or two passwords with an @-symbol, some with !, and g:czechout, which takes the longest to crack on the entire list, there is almost no symbol used in the entire list.
The second interesting takeaway is that there are barely any uppercase letters. The first uppercase letter ins found in Password, which is at position 26. The next is Qwerty123 at position 36 and Qwerty123! at position 46.
To sum it up:
- The most common passwords use lowercase letters and numbers only for the most part.
- Symbols and uppercase letters are nearly absent in the entire listing.
NordPass' findings:
- The password 123456 is still the world's worst password.
- Corporate passwords and non-corporate passwords are not that different in terms of security.
- There seems to be no improvement when compared to six years ago.
The list highlights a problem, but it is not yours
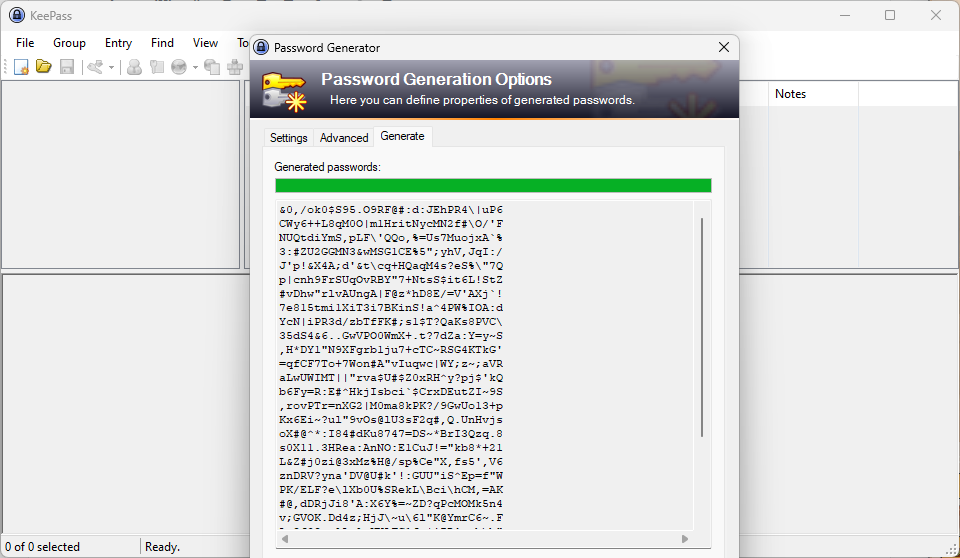
NordPass suggests that users can improve their password security by using a password manager. That is the main takeaway from all weak password listings.
Unless you are really good at remembering strong unique passwords, password managers are the best option. There are plenty of free alternatives.
There is KeePass, which continues to be my personal favorite app, and also BitWarden, which is also excellent and open source. It depends on your personal usage scenarios.
The main benefit of a password manager is that it generates and stores as many strong unique passwords as you require. BitWarden is a little bit easier to use if you need syncing, but both support this in one form or another.
Good news is that you may start right away, if you have not done so already. Most regulars here on Ghacks are probably using a password manager or multiple managers already. It takes a few minutes to download a password manager and install it. Many support imports from browsers and several other apps. You may need some time to change weak to secure passwords, but the heavy lifting is done by the password manager.
Passkeys, an upcoming standard that replaces passwords with keys that are stored on the user's devices, won't replace passwords anytime soon. Adoption is picking up pace, but it is still slow. Many Internet services, systems, or apps do not support the standard yet. Many Internet users may find it too complex of a system to use, at least in the coming years.
What is your take on this analysis? Do you use weak passwords sometimes, or do you use highly secure passwords even for throwaway accounts? Feel free to leave a comment down below.

















IT people I have asked wave this off due to:
1) Log in limits
2) Brute force attack reduction, like in Keepass.
3) The top 10 popular ones are BS, clickbait.
It is true, though, given there are autists with extremely long passwords, that do almost nothing more for security. There’s too many ways around very long passes, if you are a such an important target.
hey, if you type in your pw, it will show as stars
********* see!
hunter2
doesnt look like stars to me
*******
thats what I see
oh, really?
Absolutely
you can go hunter2 my hunter2-ing hunter2
haha, does that look funny to you?
lol, yes. See, when YOU type hunter2, it shows to us as *******
thats neat, I didnt know IRC did that
yep, no matter how many times you type hunter2, it will show to us as *******
awesome!
wait, how do you know my pw?
er, I just copy pasted YOUR ******’s and it appears to YOU as hunter2 cause its your pw
oh, ok.
— A copy of the original bash.org chat transcript
First thing I ask before sharing a private email address is the fellow’s or the gal’s management of passwords : if the answer corroborates what is described in this article, that is a total unawareness of the vital importance of passwords, I don’t handle one of my private emails but rather an alias email address that I can easily block/remove.
Mentalities regarding passwords haven’t changed over six years as it seems, which doesn’t surprise me at all given a majority of users (majority IMO, no stats) are not interested, not motivated or blind when it comes to the imperative of behaving with at least a bare minimum of precautions. Networks are like highways : not only your own life is at risk, but as well those of others. One’s device get infiltrated can mean all data it includes of relatives may be at risk as well.
Here, since always minus perhaps a year or so : all passwords are pseudo-randomly created with 32 characters, upper/mower/symbols. Of course password managers keep and deliver them when needed. It’s so damn easy.
Remember the song “Girls just wanna have fun”? Well, not only girls as it seems. Many, too many, far too many of us seem to have hedonism as the philosophical basis of our lives : enjoy, consume, laugh and forget what responsibility is and means.
most passwords are unnecessary annoyances
sites for recipes, books, news etc have no real need for a security clearance
weak passwords are just fine
the weaker the better
https://bugmenot.com/
Do you have the box the PC came in?
They do not provide much in the way of sources, so that makes it hard to evaluate.
Those kind of “releases” they may have looked into would be ripe with duplicates (same stolen data, in multiple DBs that are not deduped).
Then there is of course their own VPN business, where they can get access to the *unsalted* version of their customers passwords and more easily run a large dictionary and permutation attack on, to work out the real password behind the stored hashvalue.
In any case it makes me take many of the numbers for repeatedly used passwords with a teaspoon of salt.
They are apparently going by the ones that are cracked or leaked by other means (malware loggers and credential stealers). The socalled darknet pw databases are ripe with duplicates, as in same stolen data submitted multiple times, amplifying the count for passwords that statistically have no business being repeated as much they are reporting, except of course that they are the ones that were broken (easily).
Skewed input –> skewed output.
But it makes for more dramatic article… and of course they are trying to sell the idea of THEM handling your passwords with Nordpass (scroll down the page and the selfplug is obvious), so they put some extra scary “you are too stupid to handle your own passwords” out there.
It is one of those “let us generate them for you” (nightmare!) and sync it across devices (=they get a copy of your key database, another nightmare). You have to pay for sync, but you know what I mean, it is going to be sitting somewhere being analyzed and leaked in a big hack one day.
Going to hold back bit here, since I do not know how protected that file is, even against themselves reading its true contents. BUT! There is also a lot of metadata tried to each password, like what site it is for and used with what username/email. There has to be, so it can know when and how to autofill for you, and for you to manage your list. All of which can be sensitive and give attackers a lot to work with.
Lets take a few obvious examples, your home banking or maybe you use a (crypto)trading site or do sports betting, or your icloud password. Just knowing that you have those, and what site you are using and the username, helps criminals a lot. So just encrypting the passwords and not the whole thing, is not enough.
Which should also serve to remind you about what info you are giving away, when you use ‘log in with…’ (google/facebook and all that). And all those other password-less logins that are being pushed around the net, like MS account, with scares about how bad people are at picking password and reusing simples ones. They all want to hold your keys and log in on your behalf – so it is no longer your key, you only have the one to the big ‘log in with’ site or a “PIN” to your device that hold credentials to do that too, without you ever having the actual password.
I honestly encourage you to do some research on the dangers of ‘autofill’ and do a article on that some day. Never let your browser (or app), nor most plugings, autofill, because it can be fooled to fill in stuff when it should not. Most of them don’t even do cert-pinning of your credentials (matching a https site + a specific cert + your credentials).
So while a change of cert (and/or site) could be used to prevent malicious tricks from grabbing your login from autofill it is not a technique that I have seen advertised yet. Probably because it is extra work and people would get aggravated with all those shortlived ‘lets encrypt’ certs prompting them to doublecheck that the request is genuine.
Which, to continue this trail, all browsers have an abysmal interface for and trust way too many “foreign” CAs, not that people even begin to have a clue about which CA to trust in any case.
I mean, would YOU trust a unusual url like ‘http://o.pki.goog/s/we1/hNE’ ? Which is the OCSP url for the cert for ghacks. You wouldn’t, right? Could be anything and means nothing to most.
And without a sweaty amount of extra research how can you know it really is googles CA and not some jerks pretending to be them to fool you. The situation for users is abysmal.
And it is being kept that way to make you give up.
So, doesn’t it seem strange to you that so many of the passwords are all lowercase letters or numbers when almost no modern website allows that? The list includes a lot of passwords that probably came from very old data breaches, so it’s interesting, but it’s not a list of current common passwords. The Status Line blog recently did a write-up looking more into the list. It’s an interesting list, but not really up-to-date.