Intel Firmware updates for Memory Mapped I/O security vulnerabilities
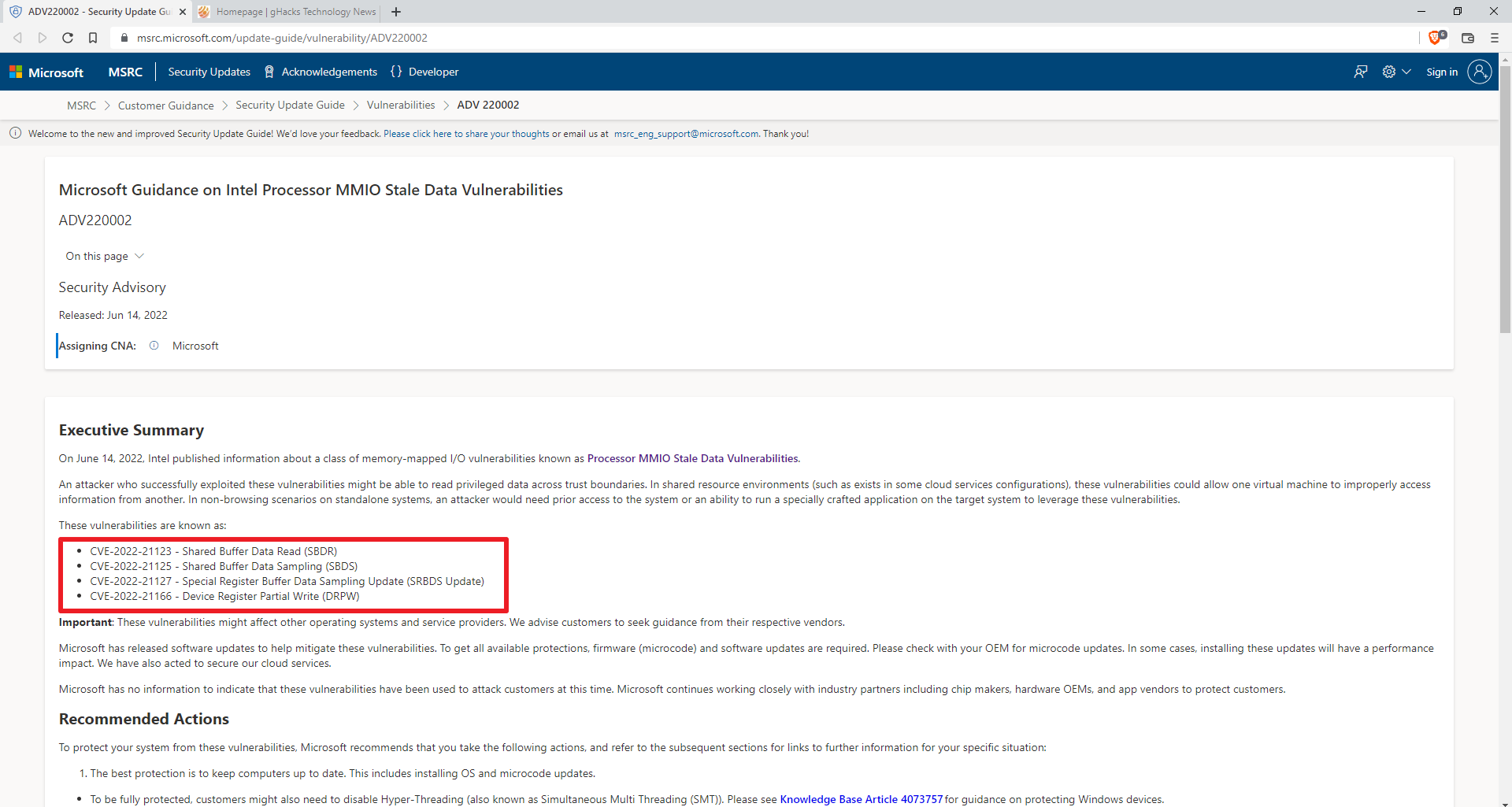
Intel released new firmware updates to address Memory Mapped I/O security vulnerabilities. Intel and Microsoft published advisories this week to inform system administrators about the issues.

Microsoft customers may visit the Adv220002 support page, Microsoft Guidance on Intel Processor MMIO Stale Data Vulnerabilities, for information. Intel published a support page on the company's Security Center website.
The following four vulnerabilities affect certain Intel processors:
- CVE-2022-21123 - Shared Buffer Data Read (SBDR)? -- "Incomplete cleanup of multi-core shared buffers for some Intel Processors may allow an authenticated user to potentially enable information disclosure via local access"
- CVE-2022-21125 - Shared Buffer Data Sampling (SBDS) -- "Incomplete cleanup of microarchitectural fill buffers on some Intel Processors may allow an authenticated user to potentially enable information disclosure via local access"
- CVE-2022-21127 - Special Register Buffer Data Sampling Update (SRBDS Update) -- "Incomplete cleanup in specific special register read operations for some Intel Processors may allow an authenticated user to potentially enable information disclosure via local access"
- CVE-2022-21166 - Device Register Partial Write (DRPW) -- ": Incomplete cleanup in specific special register write operations for some Intel® Processors may allow an authenticated user to potentially enable information disclosure via local access"
The list of affected Intel processors is available here. It includes Intel 7th generation to 12th generation processors, Intel Atom processors, Intel Pentium Gold series processors, and Intel Celeron processors.
Intel published microcode updates, which administrators may install on affected systems to protect the devices. The company recommends that users update to the latest version provided by the system manufacturer.
Microsoft confirmed the issue and provided a description of a potential attack:
An attacker who successfully exploited these vulnerabilities might be able to read privileged data across trust boundaries. In shared resource environments (such as exists in some cloud services configurations), these vulnerabilities could allow one virtual machine to improperly access information from another. In non-browsing scenarios on standalone systems, an attacker would need prior access to the system or an ability to run a specially crafted application on the target system to leverage these vulnerabilities.
Windows client customers need to install the microcode update and software updates. Microsoft has not released the updates via Windows Update at the time of writing. German computer site WinFuture notes that Microsoft will release the updates soon.















Whenever mentioning a security vulnerability in browsers, processors, etc. it would be much better if you could include a simple table of ticks and crosses that includes all major providers and whether they are impacted, at the top of the article.
Apparently, if your processor is pre-2018 Intel won’t fix it.
Good news.
It’s indeed the case that the SpeculationControl script only shows the functionalities which are supported by the CPU and whether they are vulnerable or not. Not supported ones are not displayed and therefore they cannot be affected by the newly described vulnerabilities.
https://github.com/Microsoft/SpeculationControl
Or maybe the functionalities are just not supported in earlier CPU architectures and therefore they are not vulnerable to these attacks.
Tried it out on Windows 10 21H2 and an Intel i7-2860QM cpu (Sandy Bridge). The result said the system was not affected.
But I don’t know if this is really right so far… hope so.
Hi folks
For beginners, it’s sometimes confusing how to check their systems for the mentioned vulnerabilities in the described article. Therefore, here a little guide how to do that with manual method.
Firstly, download the two PowerShell scripts 1.0.16 (SpeculationControl.psd1 & SpeculationControl.psm1) under „FileList“ and save both of them in a folder, e.g. X:\ADV
You can find them here:
https://www.powershellgallery.com/packages/SpeculationControl/1.0.16
After that, run PowerShell and go to the above created folder. In this example X:\ADV
Then run following commands:
– Set-ExecutionPolicy RemoteSigned -Scope Currentuser (confirm with YES)
– Import-Module SpeculationControl.psd1
– Get-SpeculationControlSettings (here you see whether and if so which vulnerabilities exist on your systems)
– Set-ExecutionPolicy Restricted -Scope Currentuser (confirm with YES)
Lastly, leave PowerShell again. That’s even all.
Best wishes
Uwe
@Albert Maurice
For the time being, unfortunately yes.
Why do I have to wade through a very confusing table to check if my processor is impacted ??
Intel is unable to write a small utility to tell me if I need to do anything ??
https://www.intel.com/content/www/us/en/developer/topic-technology/software-security-guidance/processors-affected-consolidated-product-cpu-model.html
I got a Intel firmware update for Ubuntu 20.04 today.
I got an Intel microcode update for Ubuntu 22.04 around two weeks ago.
“… via local access” x4
Person standing at the computer can pick it up and walk away with it.
“Just put a cable lock on it.”
Lockpicking Lawer enters chat..
>In non-browsing scenarios on standalone systems, an attacker would need prior access to the system or an ability to run a specially crafted application on the target system to leverage these vulnerabilities.
Which is not difficult nly requires determined and skilled nefarious perpetrators, and while known exploits maybe patched in smaller time frames these days, that’s only 1% or less of all vulnerabilities that are not made public or that haven’t been discovered yet.
We can blame corporations of which their developers are under strict timelines in order to push crap out the door thats not properly sanitized in some cases. Writing secure code is not something that one can do in certain working environments.