uBlock Origin for Firefox addresses new first-party tracking method
The latest version of the content blocker uBlock Origin for the Mozilla Firefox web browser includes a new feature to detect a new first-party tracking method that some sites have started to use recently.
The issue was first reported ten days ago by user Aeris on the project's official GitHub page. Some sites started to use canonical name records (CNAMEs) to bypass filters used in content blockers. First-party resources, e.g. a subdomain, are not blocked usuall unless they are known to only serve advertisement.
The main issue from a content blocking perspective is that identification and detection is difficult. The extensions would have to uncloak alias hostnames in order to provide the user with information and the ability to do something about it.
Raymond Hill, the developer of uBlock Origin, found a way to address the new first-party tracking method in Mozilla Firefox.
Side-note: Why only Firefox? Because Mozilla has created DNS APIs that may be used to expose the CNAME while Google has not. For now, it is not possible to protect against this form of tracking in Google Chrome. Hill writes "Best to assume it can't be fixed on Chromium if it does not support the proper API".

Firefox users who upgrade to the latest version of uBlock Origin, may notice a new permission request (Access IP address and hostname information). This is required to unlock access to the DNS API in the browser extension.
Note: The version is currently available as a beta version. It may take some time before it becomes available to stable users (version 1.24 required)
Firefox users who run the extension need to do the following to set things up properly on their end:
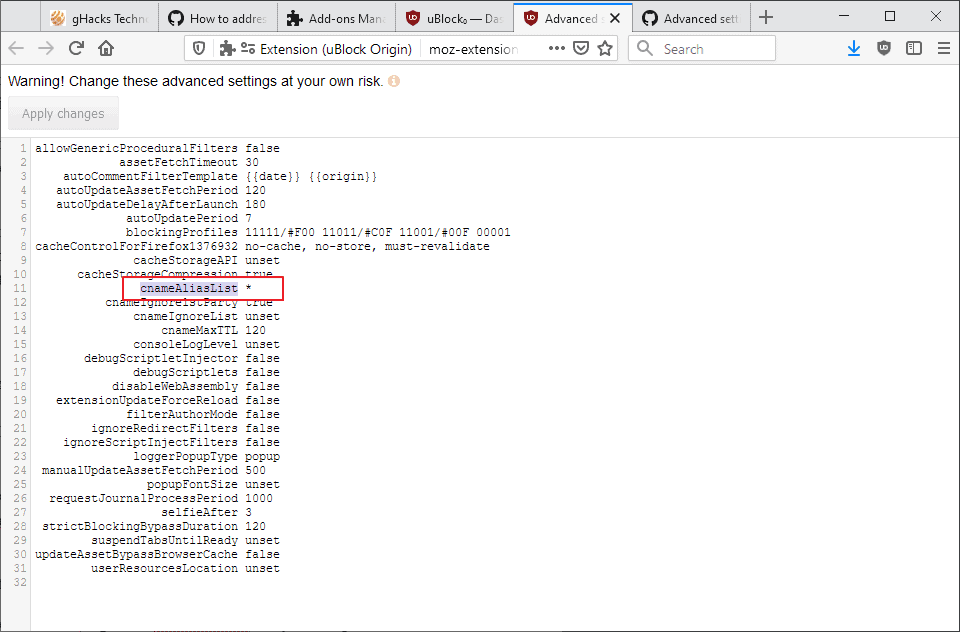
- Open the Settings of the extension, e.g. from about:addons or by clicking on the dashboard icon in the uBlock Origin interface.
- Check the "I am an advanced user" box on the first page that opens.
- Activate the settings icon next to the option to open the advanced settings.
- Change the value of the parameter cnameAliasList to *.
The change runs the actual hostnames through the filtering that uBlock Origin applies again. The log highlights these in blue.
Network requests for which the actual hostname differs from the original hostname will be replayed through uBO's filtering engine using the actual hostname. [..] Regardless, uBO is now equipped to deal with 3rd-party disguised as 1st-party as far as Firefox's browser.dns allows it.
The setting of the wildcard means that the process is done for any hostname that differs; this works but it means that a certain number of network requests are processed twice by uBlock Origin.
The next step is for me to pick a cogent way for filter list maintainers to be able to tell uBO to uncloak specific hostnames, as doing this by default for all hostnames is not a good idea -- as this could cause a huge amount of network requests to be evaluated twice with no benefit for basic users (default settings/lists) while having to incur a pointless overhead -- for example when it concerned CDNs which are often aliased to the site using them.
Hill wants to switch to using a maintained list of known offenders that uBlock Origin (UMatrix will support this as well) will process while leaving any other hostname untouched.
Closing Words
Firefox users may change the configuration to make sure that they are protected against this new form of tracking. Chromium users cannot because the browser's APIs for extensions does not have the capabilities at the time of writing.
















Hello Tom Hawack.
I’m sorry for such a long time without answer. My bad – options for uncloacking CNAME are available in uBO v1.25.0 not in v1.24.3 mentioned in my previous post.
Thanks for an opinion about anti-trackers list. I will use ‘firstparty-only-trackers-hosts’ list, because – for example – ‘firstparty-only-trackers’ list contains only domain names (uBO filters use ‘@@||example.com’ or ‘||example.com’ etc.) and I don’t know if it’s okay.
Thanks, best regards.
Hello. It seems, that option/s to block ‘1st-party’ tracking will be available in v1.24.3 release (see GitHub etc.)
I have one question: do you think, that using ‘https://hostfiles.frogeye.fr/’ website (to import for example ‘firstparty-only-trackers-hosts.txt’ list) is okay? I mean from a security point of view and so on.
This list is mentioned by ‘die in LA’ user (posted on November 20, 2019).
Thanks and Merry Christmas!
@Anonymous,
Glad to know that uBO would handle 1st-party tracking in v1.24.3. At this time indeed (v.1.24.2) its ‘Advanced Settings’ stil doesn’t include the awaited ‘cnameAliasList’.
Concerning Frogeye’s anti-trackers list, there are several of which some specific to 1st-party trackers:
Frogeye hostsfiles at https://hostfiles.frogeye.fr/
All lists offered as hosts and domain format.
Which one to choose?
Frogeye’s Fiirst-party trackers – Readme :
https://git.frogeye.fr/geoffrey/eulaurarien/src/branch/master/dist/README.md#whats-a-first-party-tracker
Personally I use ‘Frogeye First-party only trackers’ (https://hostfiles.frogeye.fr/firstparty-only-trackers-hosts.txt) given I already have an army so to say of anti-tracking blocking lists :=)
It’s all up to one’s context. Do read above mentioned ‘Frogeye’s Fiirst-party trackers – Readme’, it’s clear and well explained.
“Someone jumps the gun” miles wrong. Why are people proud of doing this all over again, this is part of the C-Library, “Socket()” and is “ub4 gethostid(char *)” – learn the book first. This is part of “SVID” and the standard TCP/IP that Microsoft never implemented. But it is fully available on Linux and OSX by using the C/C++ programming languages. But my experience is that we rewrote this, typically to make the lookup faster and avoid queries to the DNS and say query “/etc/hosts” only. It is simply to separate whatever MS has caused problems by not making the specific to Firefox, to what applies to Firefox on Windows.
To everyone else, it is simply to make a line in “/etc/hosts” “192.168.255.255 spammers fraud” and append all the sites you seek to block to this line and some other IP address that is a dead end.
This is fully described in the “Sockets()” part of Unix System V Interface Documentation” – “SVID” which is the basis for “Linux” and Unix BSD that is used in OSX. This standard is not implemented by Windows. There are a number of attempts to patch up the missing functions on Windows.
@Canuto: I didn’t understand what you wrote because obviously you are professional. Can you answer my question about uBlock Origin rules?
I have this kind of settings when I am blocking all third party:
* * 3p block
* * 3p-frame block
* * 3p-script block
Are default noop settings then useless or can I keep them?
behind-the-scene * 3p noop
behind-the-scene * 3p-frame noop
behind-the-scene * 3p-script noop
I’ve read the following on the Lifehacker website: “uBlock Origin’s expanded CNAME blocking capabilities for Firefox are in beta right now, but will soon be available in Firefox once the add-on’s version 1.24.1 drops.”
Martin, perhaps you jumped the gun a little.
I’ve checked the about tab in uBlock’s settings after updating to the newest dev beta build. It still shows 1.23.0 and not 1.24.1b3. The cnameAliasList entry isn’t showing up either. Is Firefox not updating my addon for some reason?
@DaddioSidno: I wondered same thing. Usually, nowadays with webextensions, it is no need to restart Firefox but this time extension does not finnish updating withouth restarting. Waterfox informed clearly to restart browser.
@DaddioSidno, restart Firefox and it will get updated.
canonical name records (CNAMEs) should be banned.
Based on my experiences, I have to disagree with much of what you’ve said.
The most obvious case is with Amazon. For example, if I’m browsing tech sites about Bluetooth speakers in a regular Firefox window, then use my standard keystroke (on my Mac) of Command-Shift-Delete, Firefox brings up it’s “clear” dialog (preset to my usual options). Then by simply hitting the Enter key (which activates the default “Clear Now” button), Firefox clears Cookies, Cache, Offline Website Data, and a couple of other things.
If I then I go to Amazon (in the same Firefox session, possibly even the same tab), Amazon doesn’t seem to know what I’ve been doing recently, which is good.
However, if I’d been browsing those same tech sites/Bluetooth speakers in a Firefox Private Window, then typing Command-Shift-Delete does _nothing_ : it doesn’t bring up the “clear” window or anything else. If I then go on to Amazon (in the same Private Window), Amazon immediately bombards me with Bluetooth-speaker options. Obviously they’re cross-site tracking my previous browsing somehow — and in spite of my running uBlock Origin with extra anti-tracking filters, and in spite of my having turned on the anti-fingerprinting options in Firefox.
I’ve experienced this over and over again: Amazon tracks me when I’ve been Private browsing other sites. (This is before I recently implemented Firefox Containers; perhaps that will change this behavior, not sure yet.)
You said: “Clearing cookies and other persistent storage/identifiers at the end of the private browsing session, one of the main features of private browsing, is good against remote and local spying, not just local.” I’m having trouble understanding what you mean: Firefox doesn’t even give me the option to clear _anything_ at the end of a Private browsing session. Perhaps by “session” you mean actually quitting and relaunching Firefox? Or are you talking about something Firefox is supposedly doing automatically in the background?
I’ve experienced this same issue (although less egregiously) with other websites too, not just Amazon. So I have to conclude that Private windows are helping other sites track me. How? I’m not sure… but fingerprinting my configuration — just as I said before — seems like the most likely reason, unless someone has another explanation. But in any event I know what I’m seeing.
@Jonas said on November 21, 2019 at 11:18 pm:
Below, there are commentaries:
Permission request messages for Firefox extensions | Mozilla Support
https://support.mozilla.org/en-US/kb/permission-request-messages-firefox-extensions
Protect your privacy | Firefox Help
https://support.mozilla.org/en-US/products/firefox/protect-your-privacy
I will check that out. Thanks for your help!
Thanks much to Martin and to Raymond Hill for helping us all stay a little more private and secure!
Martin, perhaps you could remind us (post the configuration instructions again) when uBO 1.24 actually ships.
Slightly off-topic, but speaking of tracking: I’ve noticed over and over again that it’s _much_ easier for sites to track you if you’re browsing in a “Private Window”. This is counterintuitive — it sounds like it would be just the opposite — but Firefox’s “Private Window” only refers to _local_ privacy on your own machine — that is, keeping URLs you visit out of your History list. It actually makes browsing online _less_ private, I assume because it makes it easier for websites to fingerprint your configuration.
“Firefox’s “Private Window†only refers to _local_ privacy on your own machine”
It’s not that simple, for example there were times when the trackers blocker of Firefox could only be enabled in private browsing, and when DNT was sent by default only in private browsing, those are mainly against remote spying, not local spying. Clearing cookies and other persistent storage/identifiers at the end of the private browsing session, one of the main features of private browsing, is good against remote and local spying, not just local. But things like URL history cleaning and keeping storage in memory instead of on disk are indeed mainly against local spying (although there are always some hacks for sites to attempt to access browsing history). So it’s a mixture of local and remote privacy, and private browsing does definitely make browsing online more private.
The fingerprinting issue you’re talking about is maybe that sites can find ways to detect that you are using private browsing, but calling this “easier to fingerprint your configuration” is a stretch, the cross-session privacy benefits weight much more than this “fingerprinting” issue. The more significant issue with private browsing detection is when sites try to punish you for using it, the usual arms race between blockers and advertisers, but it’s only directly a privacy issue insofar as sites manage to detect if you are or not using private browsing, it’s not like the plethora of unique identifiers they can attempt to extract with other mechanisms graciously provided by your browser.
My main problem with private browsing is that session storage, including session tracking cookies, is hidden to the user while still present. It is probably a side effect of the storage being only in memory, possibly not a bad intention from Mozilla this time, but then it is a very bad reason and hard to excuse that this was not fixed after all these years (questionable priorities against certain privacy bugs start becoming closer to bad intentions here). More than an advanced user has been mislead to think that those session tracking cookies were not even in their computer.
This is why instead of permanent private browsing I just configured the browser to clear everything automatically every time at the end of the session, this has almost all the benefits of private browsing without the problem above, I can control what session cookies I let in or not.
Can they use HTTP Alternative Services the same way as CNAME to disguise third-parties as first-party ? I’ve been wondering about that since this was implemented.
https://tools.ietf.org/html/rfc7838
If they do, could ublock origin do anything against it ?
Yes I did.
Great, but is not possible auto updated?
“Someone made a script that generate a list of first party domain to block. It seems to crawl websites and extract all requests and compare domains with regex of known first party tracker.”
https://news.ycombinator.com/item?id=21584119
https://git.frogeye.fr/geoffrey/eulaurarien
https://hostfiles.frogeye.fr/firstparty-only-trackers-hosts.txt
@die in LA, nice find!
There’s also, from the same maintainer,
‘Frogeye First-party trackers host list’ at https://hostfiles.frogeye.fr/firstparty-trackers-hosts.txt
which includes the firstparty-only-trackers-hosts.txt you mention plus an extra-layer :=)
P.S. I’d prefer to die in Verona!
Slightly off topic, but is there a way for uMatrix to block YouTube ads? I know uBlock does it, but I don’t want another extension just for the occasional YouTube ad.
Not likely. uMatrix blocking is based on domains. YT serves movies and ads from same domain. If you block ads, you also block movies.
Thanks gorhill!
I will wait for uBlock Origin v. 1.24 stable.
Firefox FTW (again), Goolag again omitting APIs that can help preserve user privacy.
Firefox >>>>>>>>>>>>>Chrome, Blink Edge, Opera, Vivaldi, Brave, etc.
I can’t wait to see how the Goolag shills spin (lie about) this.
Apparently Firefox added this in version 60, while Chrome, Edge and Opera have no support for it.
https://developer.mozilla.org/en-US/docs/Mozilla/Add-ons/WebExtensions/API/dns/resolve
However I suppose that extensions could already do that until Firefox 57, and that this addition just restored this little part of the useful extension abilities that they had removed themselves when enforcing the Google webextension system in Firefox 57. A lot is still missing (ublock origin’s inline script blocking by CSP is unreliable for example), much of which will never come back, and more is being removed these times, like the remote code ability used by translation extensions.
What is Goolag? If you can’t wait to see lies then you must be more patient.
There are workarounds for Chrome in the form of filters but a proper solution to address this abuse will not exist until Chrome devs decide to implement DNS WebExt. API like Firefox devs did.
I installed the latest beta version, but still this parameter cnameAliasList is not listed.
@Sebas, did you perform a clean install of the beta?
You have to uninstall the extension and freshly add it via the Beta from GitHub. Then it will be available.
Thanks Martin, long live to Firefox (and Raymond Hill) of course. :-)
Yeah, it’s amazing that Mozilla with all their Google deal provided resources refused to provide a decent adblocker by default to the masses, but that a single person without a profit motive and not even taking donations was able to provide and maintain the code for one. Thank you Raymond Hill !
Yeah, @happysurf, both doing a fantastic job, as others, as we all when we share our findings for a better Web! :=) Those who actually innovate, create deserve a special thanks, Raymond Hill to start with, who’s never rude nor excited, only efficient. I evoke rudeness because knowing what he knows, having the talent he has, many — myself included — would join to counter-measures dedicated exasperated words towards those who initiate, develop, propagate all these tracking and advertisement issues which are the very purpose of committed honest and talented developers all in a better Web life for us, users.
I agree Tom!
Thanks.
You need the latest beta version for it. You probably have to uninstall the addon, before you install the latest version from GitHub:
https://github.com/gorhill/uBlock/releases
I had to do it exactly like written.
P.S.: Never regretted to switch back to Firefox again.
Never regretted switching back to Firefox either.
It treats me with respect which is something the other big guys are sorely lacking.
For now I could never imagine going back to chromium.
Indeed this new uBO feature is now available only on version 1.24.1b1 available on the uBO’s releases GitHub page.
1- It’s beta, one may prefer to wait for the release on AMO;
2- As noted by gorhill (uBO’s developer) and quoted in this article,
“The next step is for me to pick a cogent way for filter list maintainers to be able to tell uBO to uncloak specific hostnames, as doing this by default for all hostnames is not a good idea — as this could cause a huge amount of network requests to be evaluated twice with no benefit for basic users (default settings/lists) while having to incur a pointless overhead — for example when it concerned CDNs which are often aliased to the site using them.”
At this time, on the 1.24.1b1 release we do have cnameAliasList set to * by default and for the time being, with the increase of network requests this implies. We’ll need those new dedicated cNameAliasList filter lists, another extra work for in perspective for maintainers.
“When the going gets tough, the tough get going” : we’ll make it again against the rudeness of advertisers.
Firefox has the required DNS APIs to do so, not Chrome indeed.
I have updated the post to reflect this!
Thanks Martin!
Now I starting to wait with main (Great working) ublock 1.23 upto Ublock 1.24 is launched.
Maybe I do get this upgrade in my shoe from the Dutch St. Nicholas with his soot wipe helper or else from Santa Claus, because I have been a sweet little guy all year round. :-)
I was already wondering why ublock origin installed in Brave does block nothing anymore on youtube and others, while it always did. And a lot less on Firefox as well. Brave shields still do block a lot.
Thanks for the info Martin, very valuable.
Thanks Martin, For sharing this.
I have however problmes configuring it.
I configured unto now main ublock according you article Integrate Nano Defender with uBlock Origin to block Anti-Adblocker”
But when I look at the picture above you have the possibility already presented to you there that I don’t have them presented to me:
Your list: CnameAlialist
Your list: Cnamignorelistparty.true
Main list goes
cacheStorageCompression true
Noting here
Nothing here
consoleLogLevel unset
debugScriptletInjector false
debugScriptlets fals
Etc etc.
What can i do to make it happen?
It appears to be only in 1.24.1 Beta version for the moment.
https://github.com/gorhill/uBlock/commit/3a564c199260a857f3d78d5f12b8c3f1aa85b865
I tried to add those values to 1.23,
cnameAliasList *
cnameIgnoreList unset
cnameIgnore1stParty true
cnameMaxTTL 120
but as soon as I clicked the “Apply changes” button the new values disappeared.
Further it tells: The webext API `dns` is available in Firefox 60+ only.
Have to wait for an update as they aren’t up yet while I am typing this post.
As noted by user ‘MickyFoley’ hereafter,
“You need the latest beta version for it. You probably have to uninstall the addon, before you install the latest version from GitHub”
Which means don’t overwrite your installed uBO from AMO with that beta from GitHub,
– Backup your uBO settings,
– Uninstall uBO (AMO stable)
– Install uBO (GitHub beta)
– Restore your backedup settings.
Personally I’d advise to wait for uBO updated stable on AMO, unless you know what you’re doing of course.