HTTPZ is an advanced HTTP connection upgrader for Firefox
Most sites on today's Internet support HTTPS and are configured to use HTTPS when a user connects to the site without specifying a protocol (e.g. only typing ghacks.net in the address bar and not https://www.ghacks.net/).
Web browsers, with a few notable exceptions such as Tor Browser, don't try to upgrade connections from HTTP to HTTPS automatically. If you click on a HTTP link in an old article, probably published before the migration to HTTPS began, you may end up loading the resource using HTTP; this won't happen if the site migrated to HTTPS fully, but will happen if it has not migrated at all or supports both HTTP and HTTPS.
Extensions like HTTPS Everywhere upgrade connection requests automatically if the site is in a database of sites that support HTTPS. Search engine DuckDuckGo launched a new feature called Smarter Encryption in its applications and extensions recently that upgrades connections to HTTPS automatically based on search engine data.
HTTPZ for Firefox
HTTPZ is a Firefox extension that upgrades HTTP connections as well. It does not rely on a database of sites that support HTTPS though; the extension tries to upgrade the connection to HTTPS automatically and will revert back to HTTP if the HTTPS connection throws an error.
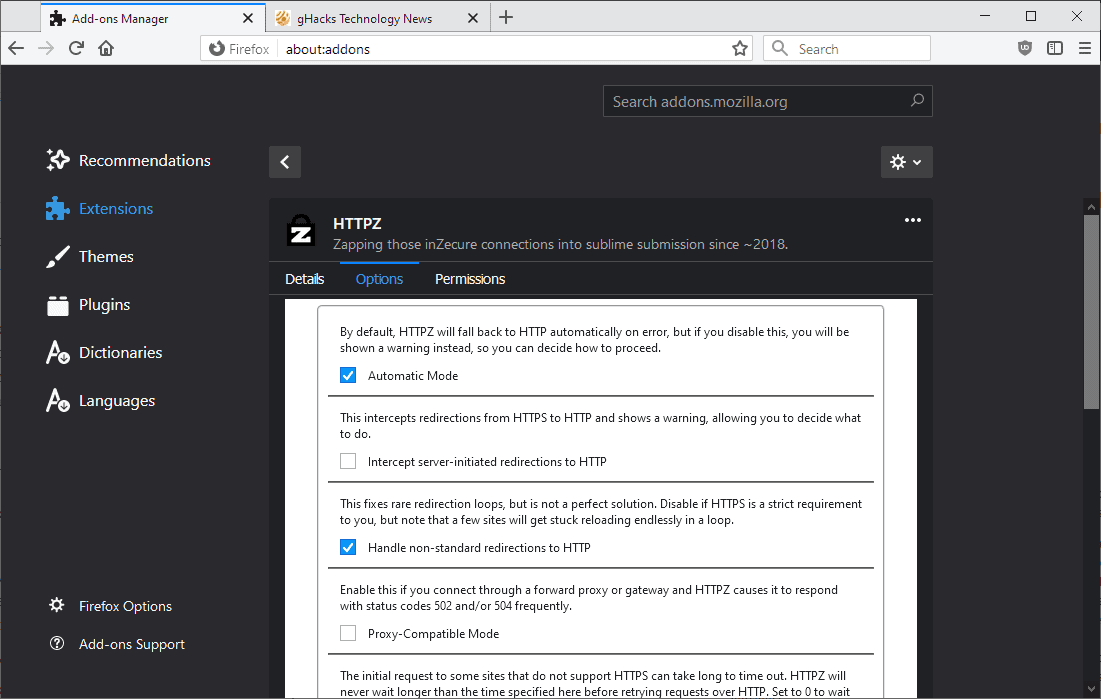
One of the great strengths of HTTPZ is the extension's rich feature set. You may want to check the options that it provides right after installation to adjust them according to your needs.
Here is a quick overview of what is provided:
- Disable fallback mode to HTTP if the HTTPS upgrade does not work.
- Show a warning if a site redirects from HTTPS to HTTP.
- Enable proxy-compatible mode.
- Set a timeout for HTTPS connection attempts (default: wait for browser to act).
- Disable a cache that remembers successful HTTPS upgrades.
- Configure ignore behavior for sites that don't support HTTPs (default 7 days).
- Whitelist hostnames that should be ignored by the extension.
You find import and export options in the settings as well; useful to export settings and import then into other Firefox profiles.
HTTPZ has two limitations currently. The main one limits upgrades to the site that is accessed by the user, e.g. through links. The extension does not attempt to upgrade sub-resources, e.g. elements loaded by a HTTPS site.
The second issue is purely cosmetic; If an upgrade to HTTPS fails, Firefox wants to display an error message that describes what happened. HTTPZ does not wait for the error message to load but will retry the request using HTTP (which you can disable in the settings).
Closing Words
HTTPZ is a powerful extension for Firefox that upgrades HTTP site requests to HTTPS automatically. It features a whitelist and ignore list, and options to make rules more or less tight.
One downside is that it ignores sub-resources which may lead to mixed content warnings in Firefox.
Now You: how do you handle sites that still use HTTP?


























*** Caution incompatibility in Firefox with Bitdefender. I was fixed uninstalling httpz
[url=http://pix.toile-libre.org/?img=1576001476.png][img]http://pix.toile-libre.org/upload/thumb/1576001476.png[/img][/url]
@nerdiness over 9k:
Touché. It would seem *your* nerdiness k-level is higher than *my* nerdiness k-level. ;-)
I installed HTTPZ in Firefox and Tor Browser only yesterday, so it’s still very early days for me. And since I don’t use those browsers all that often, it may take me a while to acquire first-hand experience with its pros and cons.
One thing I *did* do right away was to change the HTTPS-timeout from 0 (= until the browser gives up) to 10 seconds, because at least one of the sites I tried took FOREVER to load (or rather to *not* load) at the default 0 setting. I don’t *require* strict HTTPS compliance for most of my browsing. I just want to use HTTPS when it *is* available but is not enforced on the server side.
HTTPS is so widely implemented by default these days that, at least for me, this is a problem that no longer needs a solution. I used HTTPS Everywhere in the past, but stopped a couple of years ago as it was getting rare to run into HTTP sites.
Out of curiosity I installed HTTPZ for a couple of days, but found its warnings to be more of an annoyance than a benefit, and it’s been uninstalled.
Brave browser is made by google…
Martin, I saw two errors in the article:
Where it starts with “Note that it is designed to do so only for non-manual HTTP sites.”, actually, it’s the opposite. The addon tries to upgrade those too. The ones it ignores are when you manually type “https://”, and apparently if you have another extension or something that can redirect to https before HTTPZ does, it ignores those too. This has to do with security.
The other error is where it says “Disable a cache that remembers successful HTTPS upgrades to speed up future connections.” The addon actually explains that it is a security measure. I don’t know if it speeds up or slows down anything but I personally couldn’t tell the difference so far.
@Anonymous:
Leaving the cache enabled would create a partial local record of sites visited — a record that (like the ones created by adblocker and scriptblocker customizations) would not get zapped if/when you clear your browser history. I’d call that more of a “privacy” concern than a “security” concern, but whatever. I’m guessing that *disabling* the cache would probably make HTTPZ “Tor Browser compliant.”
If that’s not a serious issue, whether in ordinary Firefox or in Tor Browser — some people use Tor Browser primarily to minimize tracking and profiling, not to hide every last item in their local browsing history — leaving it enabled would indeed make future connections to cached sites faster, and not “hammer” cached sites with superfluous connection requests, which is always good netizenship. The difference in speed probably isn’t significant most of the time, but every site appreciates less hammering.
@Peterc
I’m pretty sure that’s not how HTTPZ works. It triggers “superfluous requests” only when sites do not support HTTPS, because it always tries to connect securely first, and it only makes an insecure retry over HTTP once it has determined that the server does not support HTTPS.
As far as I know, the HTTPS “cache” feature is not really a cache at all in the conventional sense. It is merely a list of domains the addon builds automatically as you browse secure sites, and it uses it to keep track of the sites that support HTTPS, so it can avoid retrying requests to those sites over HTTP if attempting to connect to them over HTTPS ever happens to fail in the future. That is a security measure against SSL-stripping attacks that is clearly inspired on HTTP Strict Transport Security (HSTS), but the addon also offers an alternative to that in the form of a “manual” mode of redirection that redirects any given site to HTTP only after asking the user and warning them of the potential risks.
HTTPZ is pretty well thought out overall (in my opinion), but it can be a bit hard to understand at first, and it seems a bit rough around the edges here and there. Surely a sign of early days of development.
You are right, thanks!
HTTPS Everywhere = 1,67 MB;
Smart HTTPS = 124.99 KB;
HTTPZ= 21.52 KB.
Huh… guess it really is fat-free.
How is this different to Smart HTTPS, which seemed to have been doing the same thing for a long time?
@Martin Brinkmann:
Concerning Tor Browser, does the browser *itself* now enforce use of HTTPS where available? I ask because my Tor Browser profile includes HTTPS Everywhere, and I’m pretty sure it either came with my original Tor Browser install or got added by a Tor Browser update/upgrade somewhere along the way. Is HTTPS Everywhere no longer useful or necessary in current Tor Browser?
Following up on my previous post, if Tor Browser *does* still in fact rely on HTTPS Everywhere for enforcing HTTPS, it’s all the more unfortunate that there’s no WebExtensions version of HTTPS Finder.
@Martin Brinkmann:
Thanks, Martin. I gather that, like Tor Browser, HTTPS Everywhere is the Electronic Frontier Foundation’s baby, which might be one reason they’re sticking with it. They control what it does.
And on second thought, creating user rules for sites not in HTTPS Everywhere’s database creates a durable local record in your profile of at least *some* of the sites you’ve visited, so I’m guessing the EFF would *not* endorse using a WebExtensions version of HTTPS Finder, even if one existed. I suppose building a local whitelist for alternative extensions like HTTPS by default and HTTPZ would do the same thing, so the EFF would probably disapprove of doing that, as well.
Tor Browser’s implementation is based on HTTPS Everywhere.I’m not aware of plans to change that.
Tor is not the only other choice. The Brave browser does this by default as well.
DISCLAIMER: My primary browser is Pale Moon and I haven’t yet tried HTTPS Finder in Google Chrome or Waterfox Classic, nor have I tried Smart HTTPS, HTTPS by default, or HTTPZ in modern Firefox.
HTTPS Everywhere supports user-created rules for sites that aren’t in HTTPS Everywhere’s database. (If you’ve ever installed HTTPS Everywhere in your current user profile, look inside it and you should find a subfolder named HTTPSEverywhereUserRules.) But no one wants to have to write rules manually, so there was/is also an extension called HTTPS Finder. HTTPS Finder detects sites that support HTTPS but don’t enforce it and offers to make a site-specific HTTPS Everywhere user rule *for* you (MUCH easier). Currently, there seems to be a version of HTTPS Finder for Google Chrome and, on Github, for legacy Firefox (=Waterfox Classic?), but *not* for modern Firefox. For modern Firefox, I have seen Smart HTTPS, HTTPS by default, and now HTTPZ suggested as substitutes for the HTTPS Everywhere + HTTPS Finder pairing.
In Pale Moon, the HTTPS Everywhere fork is named HTTPS Always and the HTTPS Finder fork is named HTTPS Inquirer. (The profile subfolder for user rules is named HTTPSAlwaysUserRules.) HTTPS Inquirer is only just out of beta, but it seems to get the job done, at least for the sites *I’ve* used it to make rules for. (As disclaimed above, I can’t yet speak to how well the original HTTPS Finder works in Waterfox Classic or to how well its Chrome version works in Google Chrome. I *do* find it a little odd that there isn’t a WebExtensions version.)
the developer of HTTPZ is a talented and super-great guy and i love his dynamic approach to upgrading http connections verses the EFF’s static approach which i personally think is a really poor solution
one possible downfall with HTTPZ is that i don’t think it can upgrade 3rd party connections, so if example.com pulls resources from http://example-2.com, the latter isn’t upgraded
please correct me if i’m wrong, but i know this was an issue in the past
Smart HTTPS addon do this for ages, even for Chrome. What’s the difference? https://addons.mozilla.org/firefox/addon/smart-https-revived/
Whatever, it’s another alternative to the popular and suspect HTTPS Everywhere.
suspect?
@Anonymous:
Suspect = limited/incomplete by design? (If a site isn’t in HTTPS Everywhere’s default database and isn’t targeted by a user-created rule, HTTPS Everywhere doesn’t try to upgrade HTTP connections to that site to HTTPS.)
sounds very similar to
https://addons.mozilla.org/en-US/firefox/addon/smart-https-revived/
I just roll with it unless a financial transaction is involved. I’m not paranoid enough to be worrying about every site I visit.
HTTPS Everywhere already have this: Encrypt All Sites Eligible (EASE)
Good to have options though.
Also check the other addons by claustromaniac, it’s a good kitty.
https://addons.mozilla.org/firefox/user/13341776/
After having been a user of ‘HTTPS Everywhere’ for many years I’ve made the switch to HTTPZ just a few days ago. Of course the advantage over the former is that it won’t miss secured sites which wouldn’t be in a database, no database means a lite add-on. On the other hand, as noted by claustromaniac, the developer of HTTPZ on the extension’s AMO page,
“Unlike HTTPS Everywhere, this extension does not take care of sub-requests triggered from HTTP-only sites. For now, it outright ignores those requests, because using the same approach with those (retrying on error) is very complicated and has significant drawbacks.”
Still worth it nevertheless IMO. The number of HTTP-only sites is decreasing. Of course those remaining which perform calls to 3rd-party sites via http won’t have those calls secured (when applicable) as with ‘HTTPS Everywhere’. This is far less a concern when connections to 3rd-party sites are leveraged by a filtering extension such as ‘uBlock Origin’.
HTTPZ has been improved lately, running excellently up to now, though I had to test with sites I know as being accessible via HTTP (only or not) given finding an HTTP-only site, say from Search engines results, is less and less frequent.
HTTPZ is the best in its category IMO, other alternatives to ‘HTTPS Everywhere (not many) are far less performant.