KB4100480 out-of-band security update for Windows 7 and Server 2008 R2
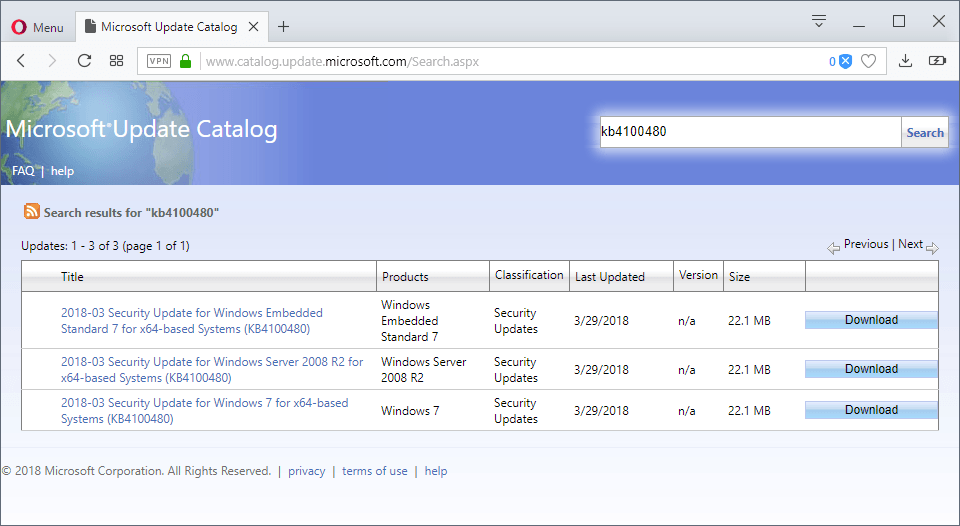
KB4100480 is an out-of-band security update for the Microsoft operating systems Windows 7 and Windows Server 2008 R2 that "addresses an elevation of privilege vulnerability in the Windows kernel in the 64-Bit (x64) version of Windows".
The vulnerability is documented under CVE-2018-1038, Windows Kernel Elevation of Privilege Vulnerability on Microsoft's Security TechCenter website.
KB4100480 for Windows 7 and Windows Server 2008 R2

Successful exploitation of the vulnerability gives an attacker full control over the system. Microsoft notes, however, that the issue requires local access to an unpatched computer system.
An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application to take control of an affected system.
The update addresses the vulnerability by correcting how the Windows kernel handles objects in memory.
The update patches a security issue discovered earlier this month by security researcher Ulf Frisk who documented it on a GitHub page. The researcher discovered that Microsoft's Meltdown patch, CVE-2017-5754, released on the January 2018 Microsoft patch day, changed the user/supervisor permission bit to user which made the page tables "available to user mode code in every process" whereas they should only be accessible by the kernel on Windows machines.
The support page for KB4100480 lists all updates that Microsoft released that caused the issue on systems running 64-bit versions of Windows 7 or Windows Server 2008 R2. Basically, any update released on January 3, 2018 or later is affected.
The update is available from Windows Update and Windows Server Update Service, and also as a standalone download from Microsoft's Update Catalog.
Microsoft did not mention whether the new update fixes any of the known issues introduced in previous updates.
Now You: How do you handle Windows updates these days?


















Yeppers Miss sophie, I dont even use
malwarebytes, but am still running Spybot 1.
Also Using Ublock’O that i update once a week.
(Cloud OFF) if there were any viruses my limiter/port sniffer would show the culprit.
Most of that Antivirus stuff is malware itself.
It’s quite laughable when people say “I haven’t had a virus in years, and don’t use AV”. If they don’t use AV how do they know that their computers aren’t infected ?
@Stefan – Its not laughable at all. How about scanning (as I do) with Malwarebytes, or vetting everything that’s installed (before) its installed?
In this scenario, MBam is not working in the background, and using no resources. Its just on demand. Period scans give a good indicator that all is well, as well as everything being run (before installation) on Virustotal, and other scanners.
Then how about HOSTS? UBO with many filters, a lot hand crafted….blocking scripts, and keeping bad stuff well away?
How about using DNS providers like Quad9 and ComodoSecure, protecting our PCs at the DNS level?
You clearly don’t know very much, if you find all this laughable. And yes, I have not had a virus for years, and my PC is seriously clean and looked after.
I don’t even have Windows Defender. And if I had an issue, I have clones of my SSD going back months. I suggest you educate yourself.
Question was: How do you handle Windows updates these days?
I always end up here (from Google) to find information about KBxxxxxxx updates and then decide. I’ll install this one, seems legit and you can normally uninstall it afterwards if it gets too nosy.
Martin, Thank you for this explanation and summary. The update just pushed its way into my Windows 7 64bit Pro and I do not see any effects.
This flag that the Microsoft patch coder forgot to flip back from test mode to non-test mode happened way back in January. That means three months went by and no one on the windows update team noticed. An outsider caught it – how come?
‘No known issues’ with KB4100480. Now what does that really mean? .
Considering 44% (est.) of online Windows users are on W7 (and probably the majority are 64bit), that is close to half of Microsoft’s customers, which is in the billions. Not to mention that 89% are in the enterprise.
KB4100480 is checked and being sent out via windows update. The process by which unknowns become known?
not seeing it in wsus yet, thought I would may take few more hours
edit: and as I typed that I synced wsus and there it was LOL
man…timing is everything
I have not any anti virus and my thinking is to take the new anti virus and reduce the risk on my computer. you have a new versions to fit my computer …..?.so u have a perfect version so send a link for me…and plz don’t be a ignore mine comment……
So is this patch going to actually patch something this time or will it further degrade Win7 and Win7 only, in an effort to prevent another XP and force people into Win10 by security coersion?
KB4100480 fixes the vulnerabnility introduced by KB4056897 or KB4056894 on 64 bit Windows 7. It’s a nasty vulnerabilty. I’ve checked, it does fix it. KB4100480 is a small patch so unlikely to mess up other stuff.
I’m not taking anymore risks, as soon as I install Winodws 7 I disable the update service completely and remove all installed updates, until it becomes barebones SP1 and then I just install all the VC++ Runtimes, DirectX and .NET.
@Weilan – I’m with you totally. I don’t agree with the comment by SecOps. ‘True’ security is within ‘US’, and the many multifarious ways that we can protect ourselves, as long as we are in the know.
I haven’t had a virus in years, and don’t use AV or any Windows updates. Like you, I have Win7 very bare-bones, everything stopped….just as it was from the retail box. However, it is running in a VM, which certainly helps.
Totally get you, and agree. My view is….and has been for a long time, that Windows updates create a situation where the risk of having them is far far greater than the perceived risk of a virus. Yet many people just don’t seem to get that for some reason.
@Sophie, that’s because some people still believe the “newer is always better” slogan. I believed that back around 2009 when Windows 7 was just releasing and it was great from the first days, as for Windows 8 and Windows 10, they have been a disaster since day one and still are. That’s when I stopped believing that “newer is always better”.
@Weilan – again, I very much agree. Many people really do believe that newer is better. I for one, don’t. That’s not to say that I don’t have lots of software that is up to date. But on SO many occasions, I see “improvements” that are nothing of the sort – and I revert back.
As a result, I keep archives of all old software, and can generally always roll back. OR, I never update something in the first place.
A very good example of poor changes……just off the top of my head, is Microsoft’s Outlook.com. Sure, that’s Webmail, and not something that we “install” as such. But boy have they degraded it!! They fiddle and fiddle, and things that used to work really well, are just bust…..in the name of progress.
Newer is very often not better…. that’s for sure.
That is extremely insecure.
@SecOps I haven’t had a virus in about 8 years without using any antivirus or installing updates. Common sense is the best antivirus, but it can’t be bought with money.
Too early to tell; Make sure you have a backup before you install the patch. I’d wait before installation unless it is critical because others may have access to the system.
Hmm i don’t see this update available in Windows update, same with Monthly roll up updates for March, I’m started to think that registry hack to enable updates if you don’t have antivirus isn’t working anymore, otherwise i can’t explain the absent of updates for this month (Win7 32bit no AV)
You don’t see it because you have a 32 bit OS. This is for 64 bit systems.
As far as the wider question of how I handle updates; I’m at the point I may stop updating. Since Oct. of 2016 I’ve done security only updates. As I only have one machine with Windows 7 (never went to 10) that I surf on, I think I’ll just lock it down-block web access- and just switch to Mint for web activity.