Check If Your DNS Is Vulnerable
Humans are not good with numbers. At least not many are. That's why the DNS, the Domain Name System, is in place. It translates the addresses that we enter in the browser to IP addresses that the computer understands.
A DNS lookup of google.com would result in the IP 72.14.207.99 (among others) and you can type in that IP or the name and both will take you to Google.
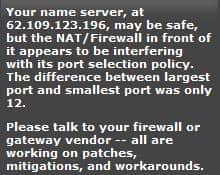
Those look ups are handled by dns servers and recently a serious vulnerability has been discovered that made it possible to manipulate those queries. This could be used to send users to a different location which could open the door for serious phishing incidents. Just think about the possibility to fake eBay or Amazon and send visitors to those fake sites even if they type in the real address.
Doxpara Research, run by security researcher Dan Kaminsky, created a script that is checking if the DNS server that you are currently using is vulnerable to the attack. This is done by pressing a button on their website. I tested the script in Firefox and Internet Explorer and both look ups worked fine.
One solution if the DNS server is found to be vulnerable would be to switch to the Open DNS system. David Bradley, an active reader of my website, covered the topic as well on his Significant Figures website.
Is your DNS server still vulnerable? Let me know!
Update: It appears that the script to test for the vulnerability is no longer available. Considering that it was discovered in 2008, it is unlikely that DNS servers are still vulnerable. You can check out the article on CERT which provides information about the vulnerability (Multiple DNS implementations vulnerable to cache poisoning).
Still, if you want to be on the safe side, you may want to consider switching from using your Internet providers DNS servers to third-party DNS providers such as Open DNS.
Advertisement















I use OpenDNS, and I checked, and I’m secure. I had checked a couple of days ago, before I switched to OpenDNS, and I was unsafe. :)
I’m definitely safe ;-)
Thanks for the citation!
db