Windows Update KB4078130 deactivates Spectre Patch
Microsoft released the Windows Update KB4078130 yesterday. It disables the mitigation against Spectre, Variant 2 on all supported versions of the company's Windows operating system when installed.
Microsoft released updates for Windows on the January 2018 Patch Day to mitigate Spectre and Meltdown vulnerabilities disclosed earlier. The company stopped the distribution of these updates to select AMD devices shortly after initial deployment because it caused blue screen of death crashes on Windows 7 machines with AMD hardware.
Intel acknowledged "higher than expected reboots and other unpredictable behavior" and recommended to customers on January 22nd that customers "stop deploying the current microcode version on impacted processors."
RedHat reverted patches on January 21st already.
KB4078130 deactivates Spectre Patch
KB4078130 is not offered through Windows Update. The update is available on the Microsoft Update Catalog website. Users and admins need to download it manually to install it on affected systems.
The update is available for all supported versions of Windows -- client and server. It has a size of 24 Kilobytes.
Microsoft recommends that the patch is only applied to systems on which unexpected reboots or other issues are noticed after installation of the January 2018 security updates.
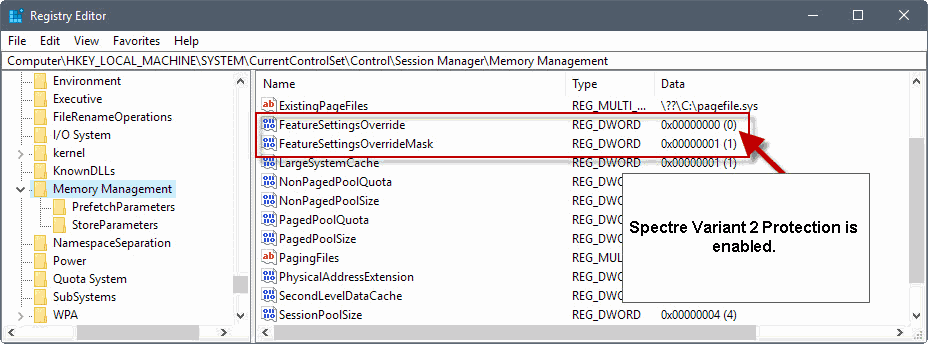
Registry
The update is not the only option that admins have to deactivate the patch. Admins may change values in the Windows Registry directly to activate or deactivate the patch. Microsoft highlights how that is done on this Support page.
Tip: We have uploaded batch scripts to our server which you can download and run to enable or disable the Spectre Variant 2 protection. Download the file with a click on the following link: (Download Removed)
You may use InSpectre by Gibson to disable the protection as well.
To disable Spectre Variant 2:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 1 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 1 /f
To enable Spectre Variant 2:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 1 /f
Closing Words
Disabling the protection should resolve unexpected reboot and other issues caused by the Spectre Variant 2 patch. It is not necessary to install the updates on systems that run without any of these issues after update installation. (via Born and Deskmodder)
Related articles
- Check Linux for Spectre or Meltdown vulnerability
- Find out if your browser is vulnerable to Spectre attacks
- Find out if your Windows PC is affected by Meltdown/Spectre vulnerabilities
- How to find and install BIOS updates on your computer
- Linus Torvalds calls Intel’s Spectre/Meltdown patches utter garbage





















Ref: Windows Patch KB4078130
Having Right Clicked and ‘run’ the Windows ‘Out of Band’ .exe Patch (then re-booted) – there was no sign of it in Windows Update History (nor in the Updates Uninstall Log).
Neither I nor a Microsoft Support Agent (who remotely accessed by PC for well over 30 Minutes looking for it) could find the bleeping thing.
So…now have no idea if it’s in and working, or if it never actually installed.
The Microsoft Support Agent looked in the Registry, but he did not appear aware of ‘what’ he was looking for in there.
Is there a quick search for any new Registry Keys that the Patch might have deployed, that would confirm the Patch ‘did’ install? (I’m a not sure how to ‘safely’ search the Registry).
Reluctant to (once again) try running the .exe file from the Microsoft Catalog, in case my Computer explodes or something.
Thanks in advance for any Comments / thoughts (Have a great Weekend)
According to the Microsoft Reference : “… This update covers Windows 7 (SP1), Windows 8.1, and all versions of Windows 10, for client and server. “.
So that to the contrary of the Microsoft Reference subtitle and of the content of this article, this should not concern W2K8 R2 and W2K12 R2, but only W7, W8 and W10 (also when used as a Server).
Microsoft Reference : https://support.microsoft.com/en-us/help/4078130/update-to-disable-mitigation-against-spectre-variant-2
According to the Microsoft reference : “This update covers Windows 7 (SP1), Windows 8.1, and all versions of Windows 10, for client and server.”
W2K8 R2 and W2K12 R2 seem not to be covered by this (KB4078130).
Reference : https://support.microsoft.com/en-us/help/4078130/update-to-disable-mitigation-against-spectre-variant-2
AskWoody writes………………………… :
So, the proverbial bottom line: Should you be concerned?
Short answer, no. In particular, if you’ve followed my recommendations and avoided this entire Meltdown/Spectre upgrading debacle — haven’t installed any of this month’s patches, haven’t installed the latest BIOS/UEFI microcode — there’s nothing in KB 4078130 that’s of interest.
On the other hand, if you have installed your vendor’s microcode update, and you’ve installed the January Windows patches (one or more of the gazillion on offer), and you’re having problems — your machine stops unexpectedly, or performance hit the bottom of a molasses sludge pit — then installing KB 4078130 may help. Or maybe not.
There are 2 ways to patch for the Spectre 2 bug, the IBRS and IBPB features(= need OS kernel and CPU updates) and/or Google’s Retpoline software feature(= only need OS kernel updates).
… Retpoline also results in minimal performance hit on CPUs but requires extra work to recompile stuffs in the OS.
… IBRS and IBPB results in significant performance hit on CPUs, especially for Cloud servers(= about -30%).
Linux is moving towards implementing the Retpoline method, eg Linus Torvald/kerneldotorg’s Linux kernel 4.15 has Retpoline built-in = may not need the Linux kernel and CPU microcode updates for IBRS and IBPB.
… AFAIK, Windows is not moving towards the Retpoline method, ie still sticking with the IBRS/IBPB method.
Raspberry Pi is not vulnerable to meltdown nor spectre.
raspberrypi.org/blog/why-raspberry-pi-isnt-vulnerable-to-spectre-or-meltdown/
so a flip of the registry setting can disable the “protection” ?! that’s not very promising. What is to stop a virus to to do the same?
@Martin, thanks for the registry changes. InSpectre refuses to change anything even when run as administrator. The appropriate button remains disabled on my AMD PC.
Staying out of it altogether on my unpatched Win7s and my good ol’ patched XP.
Which are the patches that slow down the PC exactly?
And can those be disabled via registry?
When that nasty update for 1709 came out, this PC was fine. My AMD machine was not fine. It kept trying to install it and failed (always at 25%). The overhead on the PC was unbearable. To make matters worse, the Win 8 Video driver I had been forced to use for my old NVIDIA video chip was replaced by a lousy MS version. I rolled it back to a full HD backup from July 29 2017. SInce then it has updated itself. All is well … until the next fiasco.
If you download version 6 of Inspectre you now actually get version 6a. FWIW.
Wasn’t there an “Inspectre Gadget”? ……….oh wait….that must have been Inspector Gadget. Silly me!
An amazingly pertinent confusion, Sophie! Both from now on will remind me of one another. Unfortunately the funny one is 30 years old and the sordid one is a new-born rascal :=)
Hello Tom………….grinning from ear to ear now, having read your reply!!
Shame we can’t insert a little picture of the rascal — here, in the body of these messages!
Was that really thirty years ago? Best hurry and get my walking stick!!!!
@Sophie, when I describe Inspectre as a little rascal I mean Spectre of course (I had in mind “Spectre In(side”)) and not Gibson’s InSpectre diagnostic tool…
‘Inspector Gadget’, the cartoon, is at least 30 years old. Recalls me Sunday afternoons in Amsterdam where my girlfriend (then) and I would eat good little things between two laughs about dear Inspector on TV :=) Nice times! No tapenade there, rather haring with onions, lol.
@Tom – Yes……and I quickly realised that the rascal in question was not the original protagonist!
But guess what Tom………I did not dare to (E)dit my comment……here on Ghacks…..because we all know what happens to edited comments…… don’t we!!!!
Tapenade……..Onions…..Inspector Gadget……….. there clearly are no areas that Ghacks commentaries cannot venture into! Hurrah to that!
So yes…..of course, the rascal is the latter, and I soon realised my error, but could do nothing to correct it.
I think it’s safe to say, wait for March or April’s “Patch Tuesday” if you want to update your Windows PC, regardless of version. I honestly don’t believe they’ll get it right on 13.02.2018 either.
I’m running Win7 and Server2016, both updated to December 2017, with no issues whatsoever. No reason to complicate things.
While we’re at it, leave your BIOS alone. If your machine works, don’t break it.
>”While we’re at it, leave your BIOS alone. If your machine works, don’t break it.”
I’ve always updated to the latest version of the BIOS and never had any problems. It’s when I didn’t update, I had the problems, especially on a new computer that’s getting all the kinks worked out of it.
Based upon my experience, typically new BIOS updates only go on for a year or so, anyway. Beyond that, they figure your machine doesn’t need it anymore or it’s too old, out of warranty and not worth bothering with anymore.
>>While we’re at it, leave your BIOS alone. If your machine works, don’t break it.
Spot on. Never rush these things….look and see what’s happening…. BIOS updating is a scary place for almost anyone, and the more the device “matters”, the more the worry. Twas always so, even way back when.
Personally, I’m sceptical about Microsoft having suddenly nailed this. Just have a look at Reddit/Win10 and you’ll see a glimpse of the real world, rather than the spin.
And hard to have any real guarantees about new CPUs being “clean”. For one thing….how long will that take, and how will it be certified?
Remember, as at this writing, no active exploits in the wild. My advice? Cover all your bases in a myriad of ways (there are so many things you can do in mitigation), and then relax…..have a nice frothy coffee! :)
I won’t be touching my BIOS in a million years. I’m reasonably comfortable with settings offered, and even then I don’t like changing them, nevermind flashing them.
> And hard to have any real guarantees about new CPUs being “cleanâ€. For one thing….how long will that take, and how will it be certified?
Indeed. To put a complex process in simple words, what’s up with the manufacturing of CPUs? They are acknowledged as holding the flaws we know and yet continue to be built, sold, assembled? What’s the route plan if any for new, “clean”, free of Meltdown/Spectre processors? Or is it that nothing will be done on the hardware itself, only soft-patches at the horizon? If I buy a new computer tomorrow will it be an infected one? What’s the idea of CPUs’ future?
Hello Tom, yes….absolutely. Just look at the car emissions scandals, and the obfuscation, and the “drip drip” of information from certain manufacturers, with regard to what devices they did or didn’t fit to their motor vehicles, to influence the output of emissions, as certified and recorded.
The point is, with big business, and sometimes Billions, not even Millions of $$$ – you can only ultimately look after yourself and your own security.
A little sticker one day….like the ones that used to say “Made for XP” but that says “Groovy CPU inside, we promise!” ….will never be quite enough to satisfy the curious. (Like us!)
I certainly won’t update the BIOS. The patches mentioned here and there nearly drove me mad last time I read about them because I was facing what I felt as out of my knowledge, control. Too risky. Even pros practice and advise extreme caution when it comes to manipulating the BIOS, I’ve read that over and over since 20 years.
I simply skip these crappy updates on my win8.1, leaving it “unsecured” but saving me from performance issues.
I haven’t installed any updates on my Windows 7 SP1. It has all the VC++ and .NET packages installed, but no updates.
Saving from performance issues… and from patches’ issues.
I won’t buy a new computing device before I have the guarantee it has a “Clean-CPU Inside” and I wonder how long it will take for getting such re-thought, re-built processors.
Yes, the “cure” is nearly always worse than the original issue.
The only fair thing to do at this point is for Intel and AMD to give everyone affected a new fixed cpu, but we all know that won’t happen. Let the shit show continue.
Just buy their next gen 9/10 CPU at 2x the price.
They don’t have a new, fixed CPU to give. It will take a fair bit of time to spin up new silicon.
That would mean replacing all CPUs sold in the past 20 years. Hardly possible for any company, don’t you think?
Sure…better to have billions of people and companies do it even though it wasn’t their fault.